Author: Max Gannon, Intelligence Team
XWorm Remote Access Trojan (RAT) is one of the more commonly seen RATs, along with the well-known Async RAT, Remcos RAT, and jRAT. However, XWorm RAT is significantly more advanced than most other commonly seen RATs. It was originally a Malware as a Service (MaaS) which had tiered functionality based on the subscription rate. Higher subscription tiers enabled the RAT to perform additional actions on top of basic RAT functionality, such as performing DDoS attacks, stealing additional information, and unlocking various other functionalities. “Cracked” or stolen versions have since been released in many different locations, including GitHub, making it unlikely that most threat actors currently using XWorm RAT are paying for it. XWorm RAT has been seen in various contexts ranging from basic campaigns crafted by inexperienced threat actors to advanced campaigns utilizing complex secure email gateway (SEG) bypass methods to deliver multiple RATs.
Key Points
- XWorm RAT has been seen in use by multiple APT groups including TA 558, NullBuldge, and UAC-0184.
- As an advanced RAT, XWorm RAT is capable of a large number of actions including acting as ransomware and uploading additional files.
- XWorm RAT was seen delivered alongside other malware families 78% of the time.
History
The first posts selling XWorm RAT as a MaaS appeared in July 2022. It slowly became more common, and Cofense first observed this malware in significant volumes in December 2022. Publicly available free versions of XWorm RAT appeared quickly, with the first fully featured one being posted on GitHub in September 2022. From there, it grew increasingly common and is typically seen in significant spikes toward the end of the year.
Notable Uses by APT Groups
XWorm RAT has been freely available and widely used by threat actors of varying skill levels. It has been seen in use by several APT groups who were likely attempting to disguise their actions by using a tool commonly associated with minimally skilled threat actors. At the time of this report, XWorm RAT has been associated with the following groups:
- NullBuldge
- TA 558
- UAC-0184
Capabilities
As illustrated in Figures 1 and 2, XWorm RAT has a vast array of capabilities including the ability to perform DDoS, spread via USB, replace cryptocurrency addresses in clipboards with the threat actor’s own address to reroute transactions, act as basic ransomware, upload additional files, and perform Hidden Virtual Network Computing (HVNC). It also has more advanced anti-analysis and anti-sandbox features built in. Given that XWorm RAT has shell commands enabled, the threat actor controlling it can also manually direct the RAT to do almost anything that is not already part of the built-in commands. The only area where XWorm RAT falls short is in its method of propagation. While it is capable of spreading via USB, it lacks the capability to spread laterally within a network without extensive direction from its C2.
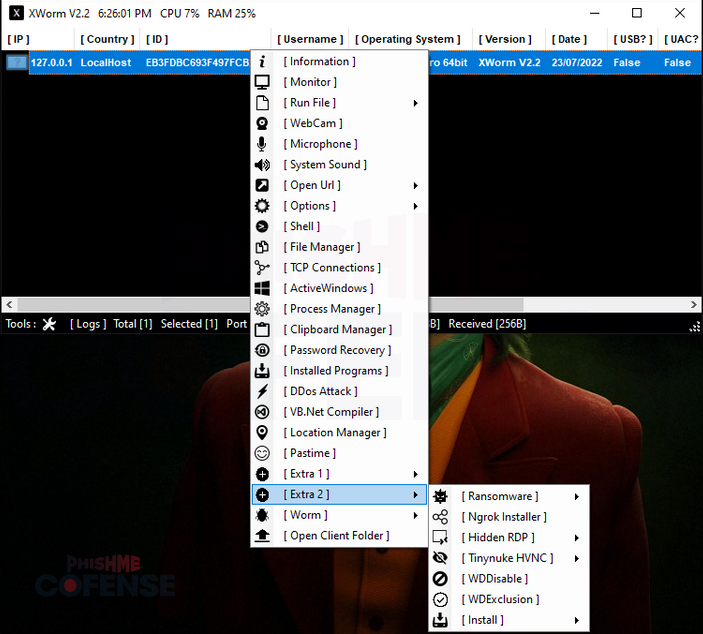
Figure 1: Capabilities displayed in the XWorm RAT controller.
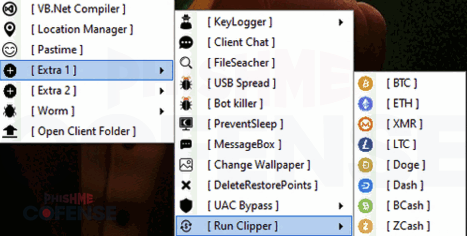
Figure 2: Additional capabilities displayed in the XWorm RAT controller.
In The Wild
XWorm RAT appears in a large variety of campaigns in the wild. Some of the campaigns used advanced TTPs, while others made use of time-tested SEG bypass strategies such as using password-protected archives and legitimate files, both of which were seen in about 17% of the campaigns delivering XWorm RAT that Cofense observed. More advanced campaigns using tactics such as steganography using images with embedded DLLs, like the one shown in Figure 3, were seen in only 11% of campaigns.

Figure 3: Image with embedded DLL extracted via steganography.
Additionally, the most advanced campaigns seen delivering XWorm RAT used links embedded in emails to redirect to pages such as the one shown in Figure 4. This web page copied a PowerShell command to the clipboard without user input and then encouraged users to execute the command. This allows threat actors to deliver malware directly to the victim’s computer and bypass any protection measures that browsers may have against downloading malware. This technique is commonly known as ClickFix. Although this only occurred in 4% of the campaigns delivering XWorm RAT, it is notable for the fact that this technique was seen almost twice as frequently with XWorm RAT as compared to any other malware family.
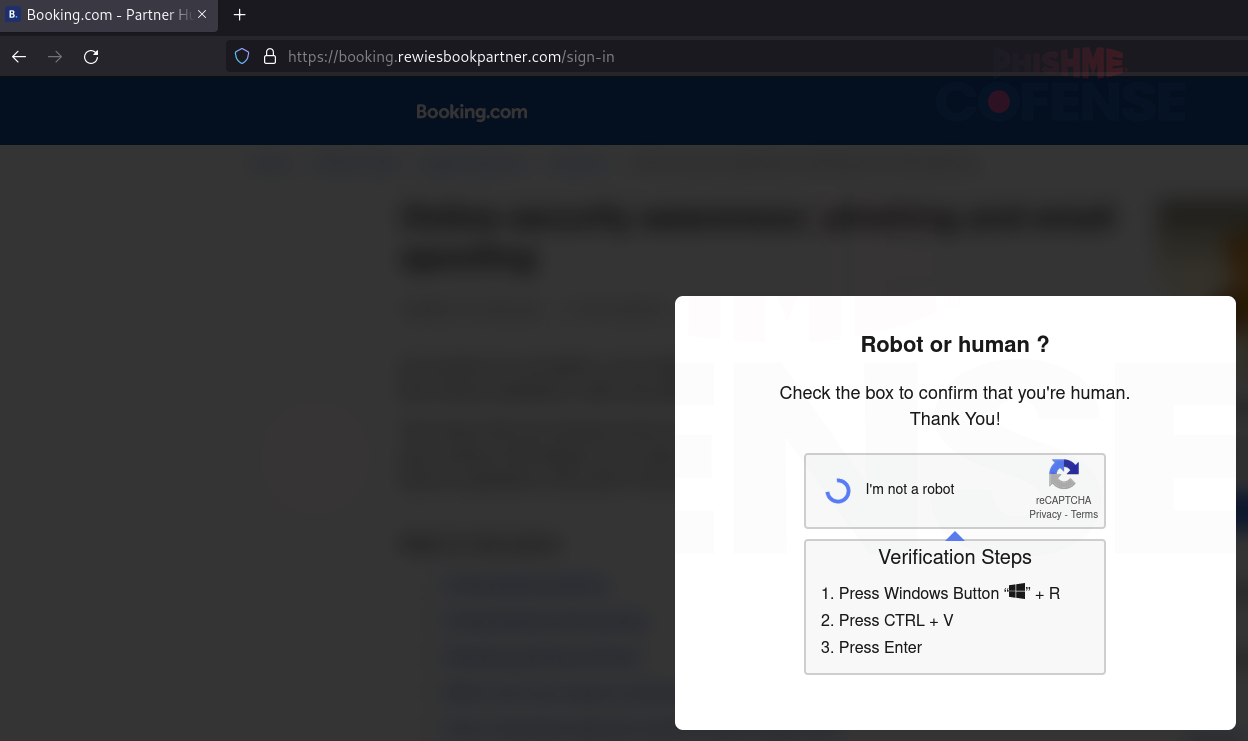
Figure 4: Verification page that copies malicious code to the victim's clipboard, a technique known as ClickFix.
Delivery Mechanisms
XWorm RAT has been delivered by 22 different mechanisms since its first appearance. These range from the most common Batch script, which was responsible for 18% of all XWorm RAT campaigns, to the least common Windows Registry, SVG, NSIS, and Office Macro. Unique campaigns such as the ones using the Windows Registry and SVG delivery mechanisms account for only 2% of all campaigns but are likely some of the best at SEG and EDR bypass as they use unusual methods that most SEGs and EDR are not prepared for.
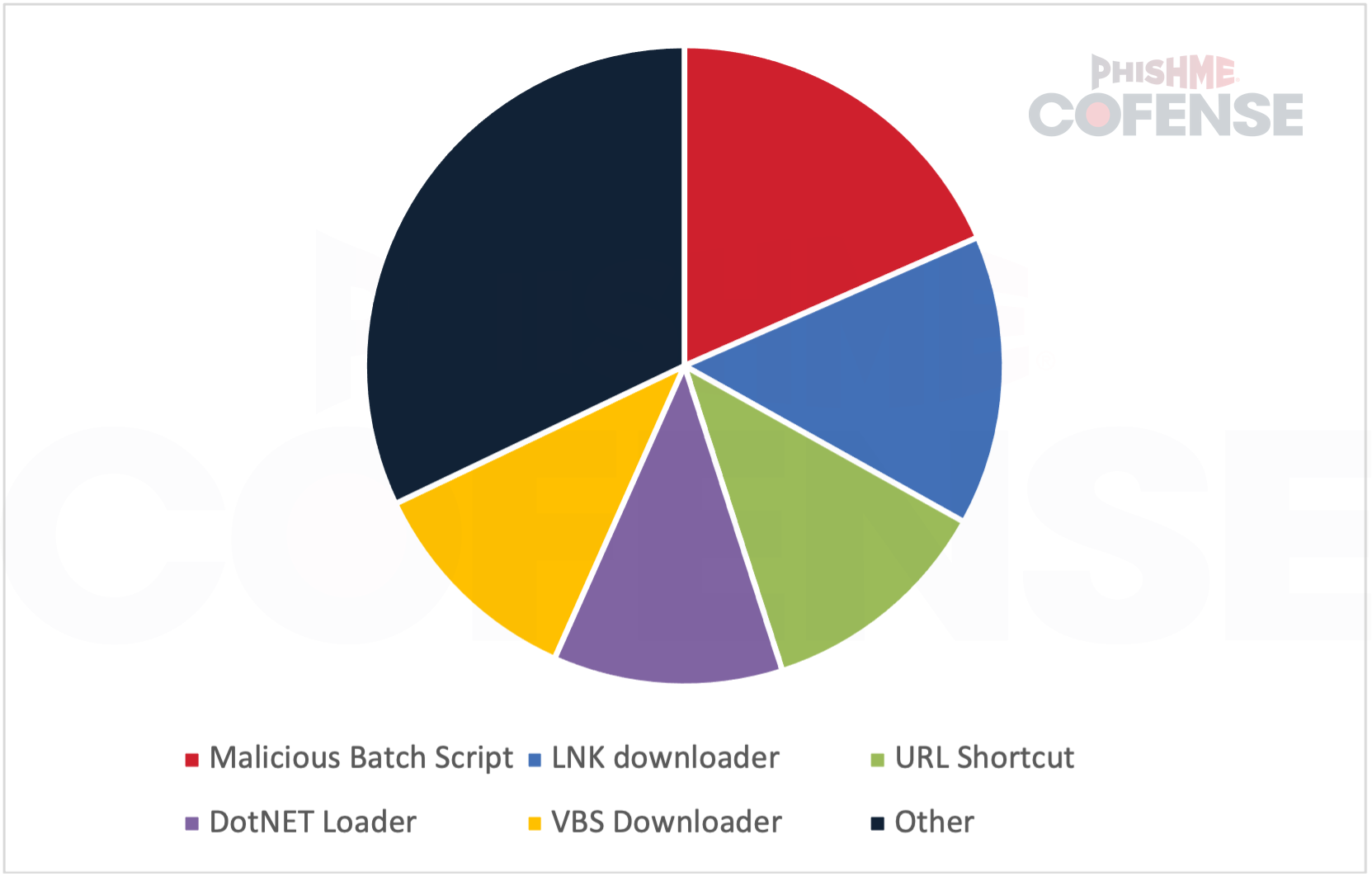
Figure 5: Top 5 most commonly seen delivery mechanisms.
Language
As seen in Figure 6, English, at 58%, was by far the most commonly seen language on email campaigns delivering XWorm RAT. However, English typically accounts for the language of 91% of all campaigns delivering malware. In that context, Spanish and German accounting for 32% combined is very unusual. The majority of the Spanish language campaigns delivering XWorm RAT delivered only XWorm RAT by itself and either directly delivered the executable or made use of a Batch Script. Out of all the languages, Spanish language campaigns were most frequently seen with a password-protected archive with a surprisingly high 81% of campaigns making use of a password-protected archive which was typically downloaded from an embedded link. German language campaigns were typically the most advanced with a whopping 94% of them using an LNK downloader that links to a WebDAV server via File Explorer. This unusual tactic may be used to obfuscate the threat actors’ actions as WebDAV requests from File Explorer may not be logged the same as HTTP requests from other executables. The last major language trend was that Italian language campaigns all delivered XWorm RAT along with several other RATs such as Venom RAT and DcRAT.
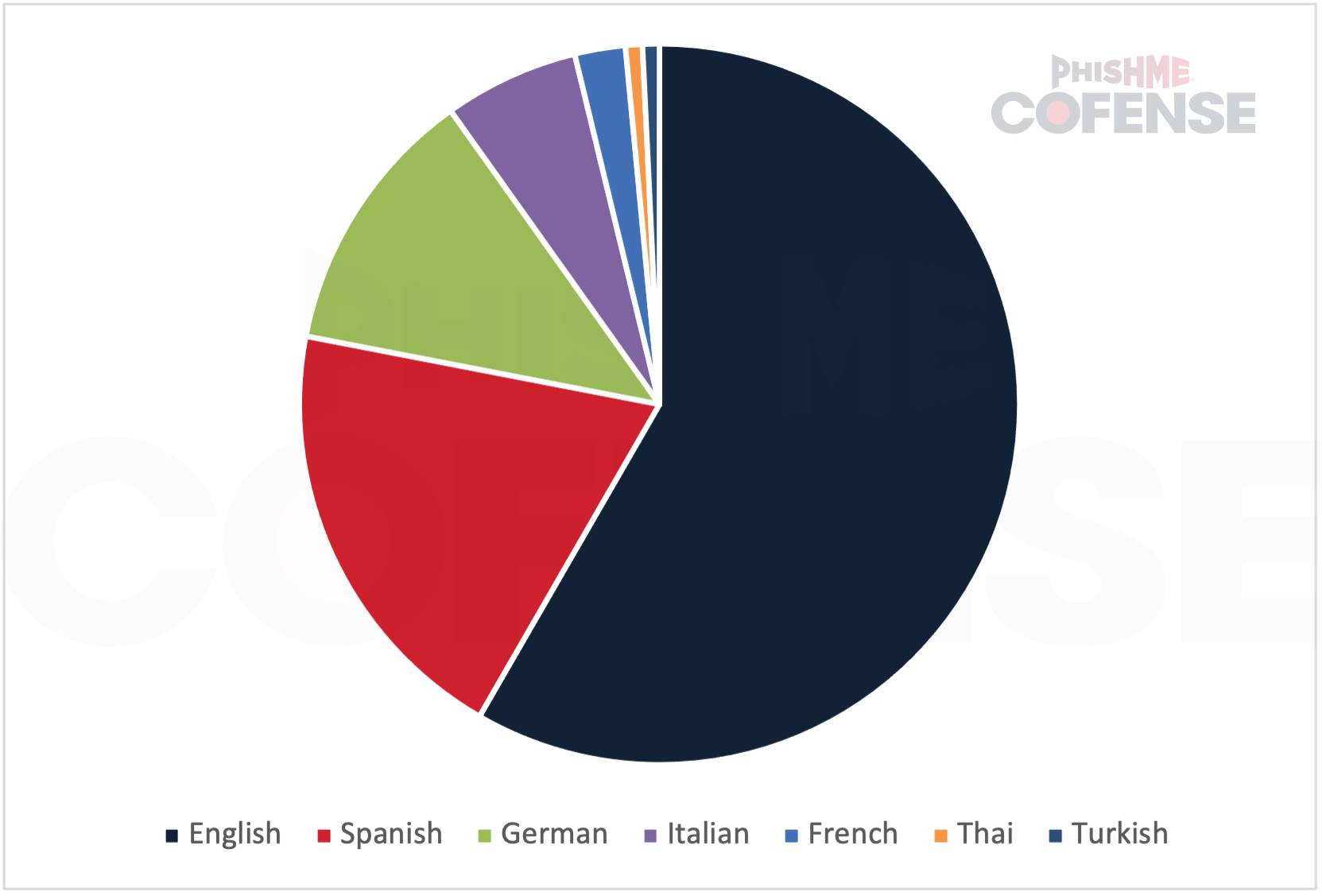
Figure 6: Breakdown of the most commonly seen languages of campaigns used to deliver XWorm RAT.
Common Accomplices
XWorm RAT was seen delivered alongside other malware families 78% of the time. This is unusual as most malware families are delivered by themselves. What is more unusual is that out of the 20 malware families seen delivered with XWorm RAT, more than 60% of them qualify as RATs, which have significant overlap in their capabilities with XWorm RAT. This makes it likely that XWorm RAT being delivered in bundles is either because the bundle is part of a pre-built package or “kit” that threat actors can use or the threat actor delivering the malware is different from the threat actor operating XWorm RAT and is more concerned with installs than detections.
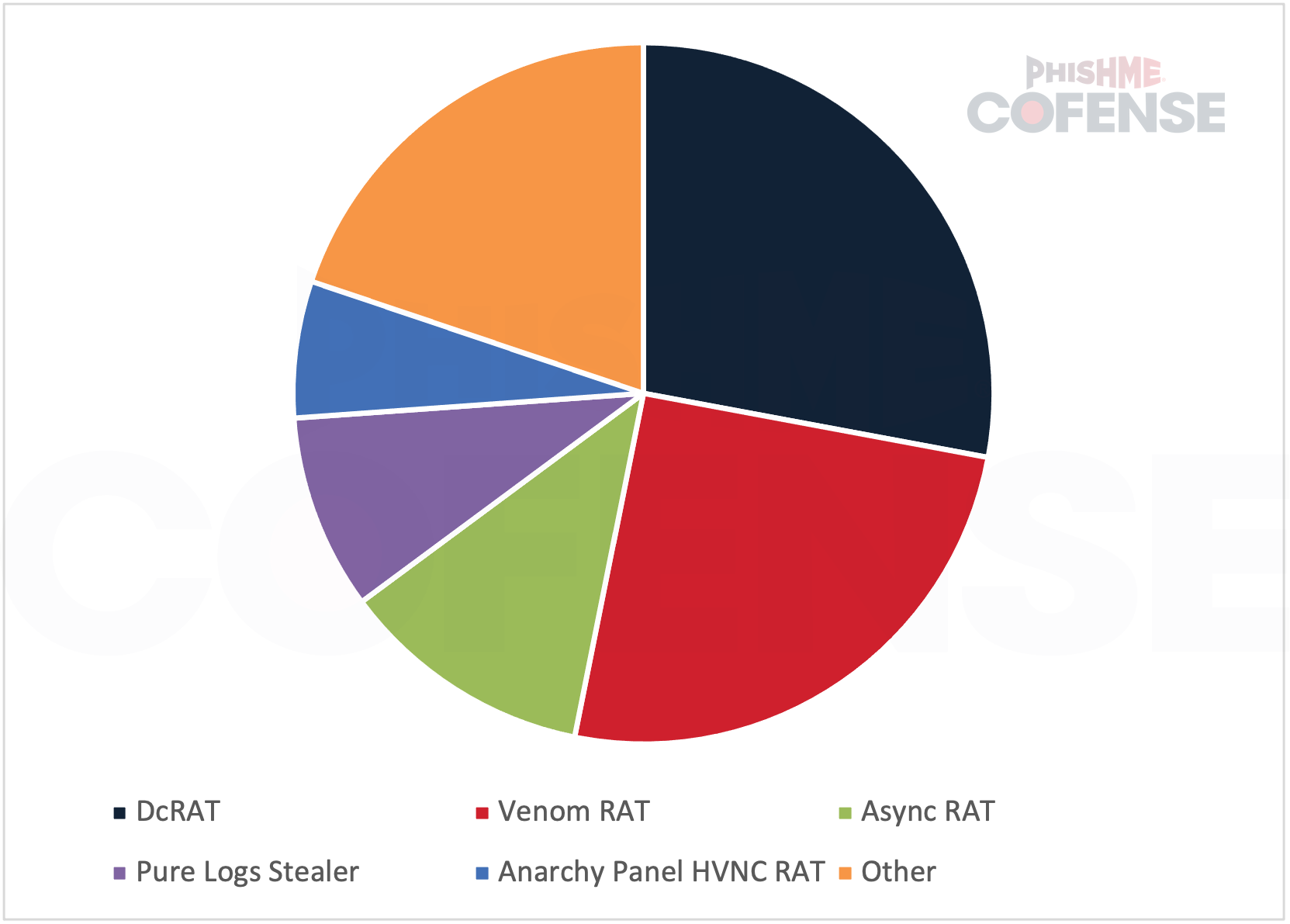
Figure 7: Top 5 additional malware families frequently seen delivered alongside XWorm RAT.
Behavior
Like most malware, XWorm RAT will attempt to enable a persistence mechanism shortly after it is installed. The default methods are dropping a file in the startup directory, creating a scheduled task, and using a registry key. Once persistence is enabled, the RAT will attempt to reach out to its C2 via a direct TCP connection. The C2 is typically a dynamic DNS domain but is sometimes an IP address. The port used is not consistent other than being a non-standard port. XWorm RAT does not use any consistent registry key entries or file locations. While XWorm RAT network traffic does look similar across multiple infections due to length, it can also vary enough that identification based on network traffic alone is not as easy as some other RATs which include an identifying string in their TCP communications. However, XWorm RAT behavior is predictable enough that most sandboxes are capable of extracting configuration information from memory.