By Don Santos, Matthew Dortch & Adam Martin, Cofense Phishing Defense Center
Introduction
Ransomware has long been a staple among threat actors, and the attacks often garner large media coverage. Ransomwares such as WannaCry and NotPetya dominated both the cyber news and broader reporting landscape for months on end. With this came a huge push within every industry to both raise awareness and train their employees to practice due diligence when interacting with unknown email senders. As users have become more advanced in their understanding, threat actors have developed more sophisticated delivery methods. Email lures, sender spoofing, and impersonation of legitimate software vendors have become popular methods of increasing ransomware delivery efficacy. The Cofense Phishing Defense Center (PDC) team has recently uncovered and investigated a compromised sender account acting as a delivery vector for LeeMe Ransomware.
The PDC team found this sample notable for its use of the SAP branding, a fake GUI to appear legitimate, and a Portuguese ransom note, while having Italian comments in its scripts. LeeMe ransomware is also notable for its apparent lack of ties to any established threat groups, use of randomized file extensions rather than a consistent one, and AES-256 encryption method. The relatively low ransom amount (0.46900 BTC/ 105,000 US dollars) suggests a widespread campaign as opposed to high-value individual targets. This investigation will explore both the delivery and execution of the ransomware, along with tips to avoid a similar compromise in the future.
MALWARE DELIVERY & INSTALLATION:
Figure 1: Email Body
Emails from this campaign purport to have a “New SAP Ariba tool”, with buzz words like AI peppered throughout the email body. An embedded link in the email leads to an anonymous file sharing platform that purports to have an archive download for the tool, which needs to be decrypted via a password given in the email body. This tactic of password protecting file archives is often done to evade automated sandbox detection. The email concludes with a polite, appreciative message aimed at fostering trust and projecting helpfulness, as depicted in Figure 1. This type of non-threatening, cordial greeting is not something that would raise alarm bells of a ransomware attack.
Figure 2: Ransomware Download Site
After visiting the link given in the email, the user is taken to a GoFile download page. Gofile is a file sharing website that allows free file uploads without requiring a user account. Figure 2 displays the seemingly authentic "SAP_Ariba_QuoteBuilder_v2.zip" file ready for download. The file is zipped and password protected, a common way to avoid detection from anti-virus software that could block the download.
Figure 3: Instructions text file
Upon download and extraction, there is an instructions text file and an executable. The instructions walk the victim through how to run the executable, still holding the SAP Ariba Quote Builder ruse. It cleverly explains to the user how to disable Windows real-time threat detection if running the program fails. This aims to reassure the victim that while the program is 100% safe, it can sometimes get blocked due to its “advanced technology”. This provides a double pronged method of both increasing trust and disabling of the native protective software.
Figure 4: Fake Installation Screen
After the file has been executed, a dummy installation GUI with SAP Ariba branding will be displayed, as illustrated in Figure 4. This deceives the user into thinking that their new automation tool is installing, while in the background the ransomware is running and encrypting files.
Figure 5: Lock Screen Script with Ransom Note
The ransom note, depicted in Figure 5, is displayed by the lock_screen.py script. Like most ransom notes, it gives instruction of the Bitcoin ransom demand and the wallet to which payments are to be sent. The note also includes the threat actor’s ProtonMail email address for contact purposes.
RANSOMWARE CAPABILITY:
The main purpose of ransomware malware is to encrypt victim’s files, rendering them unusable until a ransom is paid by the victim. This presents a major problem for potential victims, as the encrypted files could be crucial for day-to-day business. This malware achieves this through the file lock_screen_crypto.py. Figure 6 shows a code snippet that defines the target files and location for encryption. This malware sample contains a pre-defined list of target files that are searched by file extension across all available drives. This way, the threat actor can encrypt as many important user files as possible while ensuring that Windows system files are not encrypted, rendering the system completely unusable.
LeeMe Target file extensions: |
.txt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .pdf, .jpg, .jpeg, .png, .gif, .bmp, .csv, .sql, .mdb, .accdb, .dbf, .bak, .zip, .rar, .7z, .tar, .gz, .psd, .ai, .cdr, .dwg, .mp3, .mp4, .avi, .mkv, .eml, .msg, .ost, .pst |
Figure 6: Ransomware Encryption Routine
After parsing through the list and targeted drives, it proceeds to lock the files found using an AES-256 encryption method. Figure 7 illustrates a comparison between an encrypted word file and an original copy. It is evident that files are rendered unusable by the victim after encryption. With the long list of file types it encrypts, there is a high probability that a victim can lose access to important files or documents if they do not have backups in place.
Figure 7: Sample Ransomware Encrypted File
KEYLOGGER & EXFILTRATION CAPABILITY:
This ransomware goes above and beyond by also having a built-in keylogger and credential stealer. To achieve keylogging, LeeMe uses the pynput library and creates a keyboard listener. This listener can be triggered when the user types something from a list of “SENSITIVE_TRIGGERS” as shown in Figure 8.
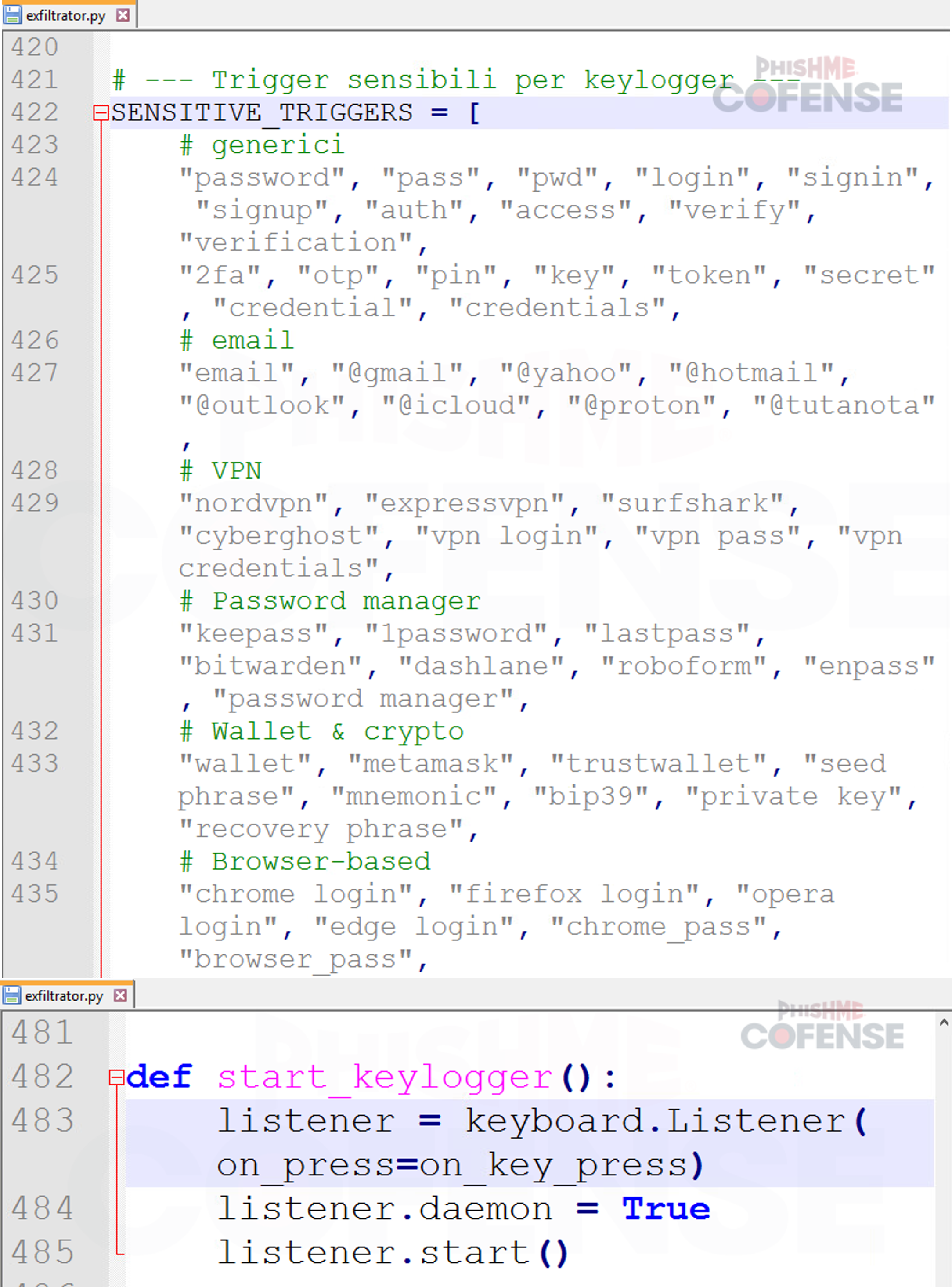 Figure 8: Trigger for Keylogger
Figure 8: Trigger for Keylogger
Additionally, Figures 9 and 10 depict how the ransomware scans the files on the machine and runs them against a predefined list of keywords including: password, passkey, credit card, bank account, and many others that could produce sensitive data. The files are zipped and are uploaded to Gofile or sent to the threat actor via Telegram.
Figure 9: Scanning for Important Files
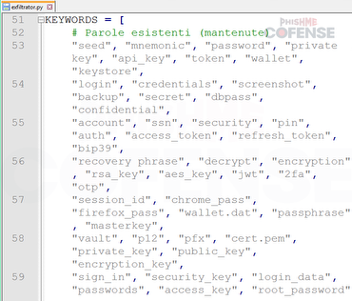 Figure 10: Keywords searched in files
Figure 10: Keywords searched in files
This ransomware sample also has other functions found within the files that it drops. Below are some of the capabilities we found:
- Create autorun entries and scheduled tasks for persistence
- Bypass Windows Defender and blocks Task Manager
- Create copies of itself with a random name under certain system folders
- Setup an SSH and WINRM server for remote access capability
- Prevents malware file deletion and process termination
As usual, the main motivation of this ransomware attack is for financial gain. A quick search on cryptocurrency websites will show us how much the threat actor’s BTC wallet has, giving us an idea of how much was paid by victims. This is illustrated in Figure 11, stating the number of transactions and current balance that this Bitcoin address has.
Figure 11: Ransomware Bitcoin Wallet Transaction History
CONCLUSION:
Ransomware is indeed a destructive force that can cripple organizations, ruin reputations, and cause massive financial burden. Although LeeMe’s ransom amount is relatively small compared to some of the other players, its exfiltration capabilities to steal passwords, credit card numbers, and personal data can lead to further damage, even after a ransom has been paid. This investigation is a reminder of all the potential dangers that threaten untrained users. Users must always be alert and cautious of emails offering unknown tools, and to check with their IT department before downloading anything. The Cofense Managed Phishing Detection and Response (MPDR) Platform can quickly identify and analyze threats that arrive in your inbox, giving your organization a better defense against evolving email threats and malware campaigns like this. Schedule a demo with our team of experts today to learn more.
Indicators of Compromise |
File Name: SAP_Ariba_QuoteBuilder_v2.exe MD5: 5661bf7b82b2e14941756ac46f18cda0 SHA256: 73b4143d5f21833206018bdea6e75f774b1e8fbd6f918be8854ec76a60626b00 File Size: 54,270,995 BYTES |
File Name: lock_screen_utils.py MD5: ae92a4f5727b182154319110b4dd8f19 SHA256: 2fbc97966627b369a2257bff303d724a68cd9149f6cecf40482cb2204cff297e File Size: 6,450 BYTES |
File Name: lock_screen_ui.py MD5: 701bdfcb866443744108bbfa085b9e38 SHA256: fe4aab878ab89f0248e638aa3b8cb08a4cae41706f1d2e6657f975ee29e31347 File Size: 13,902 BYTES |
File Name: lock_screen_generated.py MD5: c53a53d0a922db2d7a7343a0db8a584e SHA256: cfb60c99be2856082b31174d96a327cc40743e0030290dfe81c03537de278085 File Size: 32,757 BYTES |
File Name: lock_screen_crypto.py MD5: 83c089d214612984076dbb17a99c6da7 SHA256: f64cc1340872f843ee51874ad01b648c336ba937db39fb7b3ad80818cf65293f File Size: 4,693 BYTES |
File Name: lock_screen_anti_forensics.py MD5: 6462459e38c4e99a205e8826c48aee03 SHA256: 3fc4abfbda37af8313286b97adf1ae714c91de7528a37a17cc4e6bd35e434c3b File Size: 10,242 BYTES |
File Name: lock_screen.py MD5: a77139ae6eaea697135c38627fcb8d16 SHA256: be1f87f016ebe447ac8bef1ae58d3b11a7d17eec40b49b83e3772abcbf9ea3b1 File Size: 33,228 BYTES |
File Name: exfiltrator.py MD5: c10c4b3d550d05daceefa7d61f5d34fb SHA256: e04bc3ce9f4dc5f105ca7729239127a2380a7e04297b571d7f71c8acbd75d0b8 File Size: 25,655 BYTES |
Indicators of Compromise | IP |
hxxps://gofile[.]io/d/HeFOIx | 149[.]154[.]167[.]220 |
hxxps://api[.]telegram[.]org/bot7912337443:AAFV0_EwrtipOPA3OeLhBo30A1J7EdqStzs/sendMessage | 160[.]202[.]167[.]55 |
All third-party trademarks referenced by Cofense whether in logo form, name form, product form, or otherwise, remain the property of their respective holders, and the use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding the circumvention of end-point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog, are registered trademarks or trademarks of Cofense Inc.