By: Madalynn Carr, Cofense Intelligence
Threat actors constantly evolve with new mechanisms to bypass multiple secure email gateways (SEGs). A specific mechanism to evade detection is using online documents, such as Adobe, DocuSign, Dropbox, Canva, and Zoho. These services are often used internally and externally by companies, making the domains a trusted source when it comes to SEG automation. Some of these services will even email the recipient of the document directly, allowing threat actors to put little effort into their campaigns.
These document websites took up 8.8% of all credential phishing campaigns in 2024, showing the growing significance of this method. Among campaigns utilizing these online document sites, 79% of all sightings containing these domains were credential phishing.
Figure 1 shows the percentages of these online documents being used throughout all credential phishing in 2024. These are all trusted domains, as they are commonly used both by the public and with internal documents at companies.
Therefore, many SEGs automatically allow these links to enter user email inboxes. This report will look over all of 2024 and will compare the abuse of different online document websites.
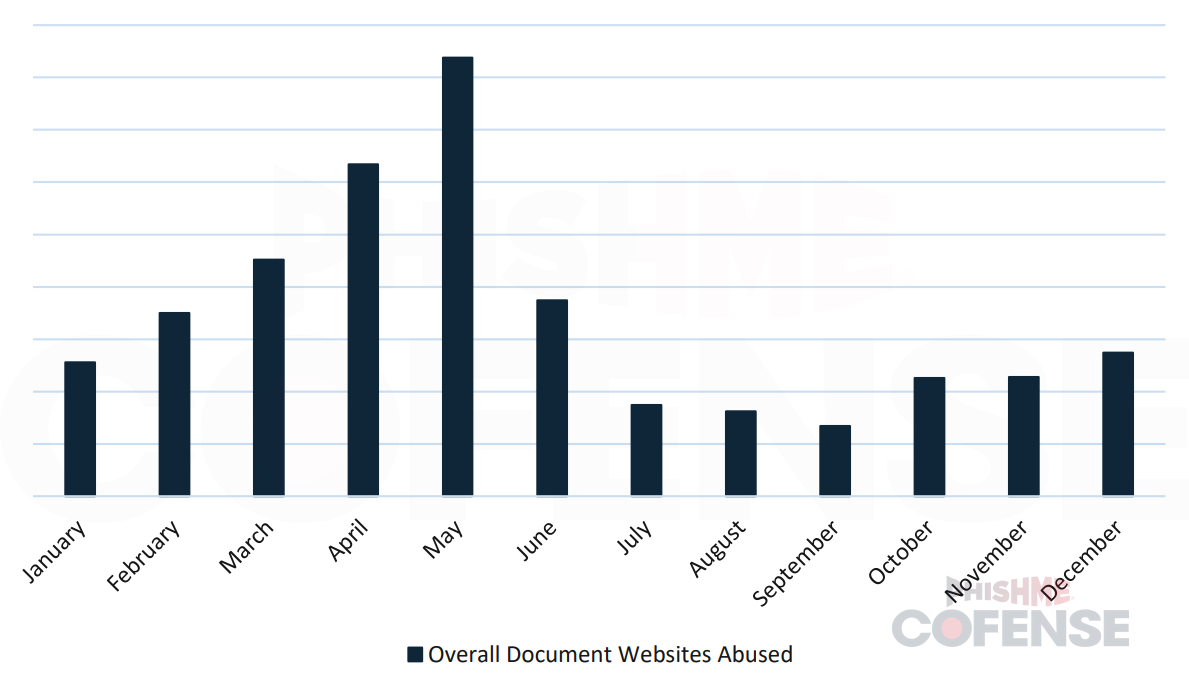
Figure 1: Usage of Online Documents in 2024.
Most Common Document files
The most common online document hosting services during this period are DocuSign, Google Documents, Adobe, Canva, Dropbox, and Zoho. This is determined via the domains used in campaigns, specifically docusign[.]net, docs[.]google[.]com and drive[.]google[.]com, adobe[.]com, sharepoint[.]com, canva[.]com, dropbox[.]com, and zoho[.]com, respectively. Figure 2 below shows the top 6 online document hosting platforms and how commonly each of these companies is abused.
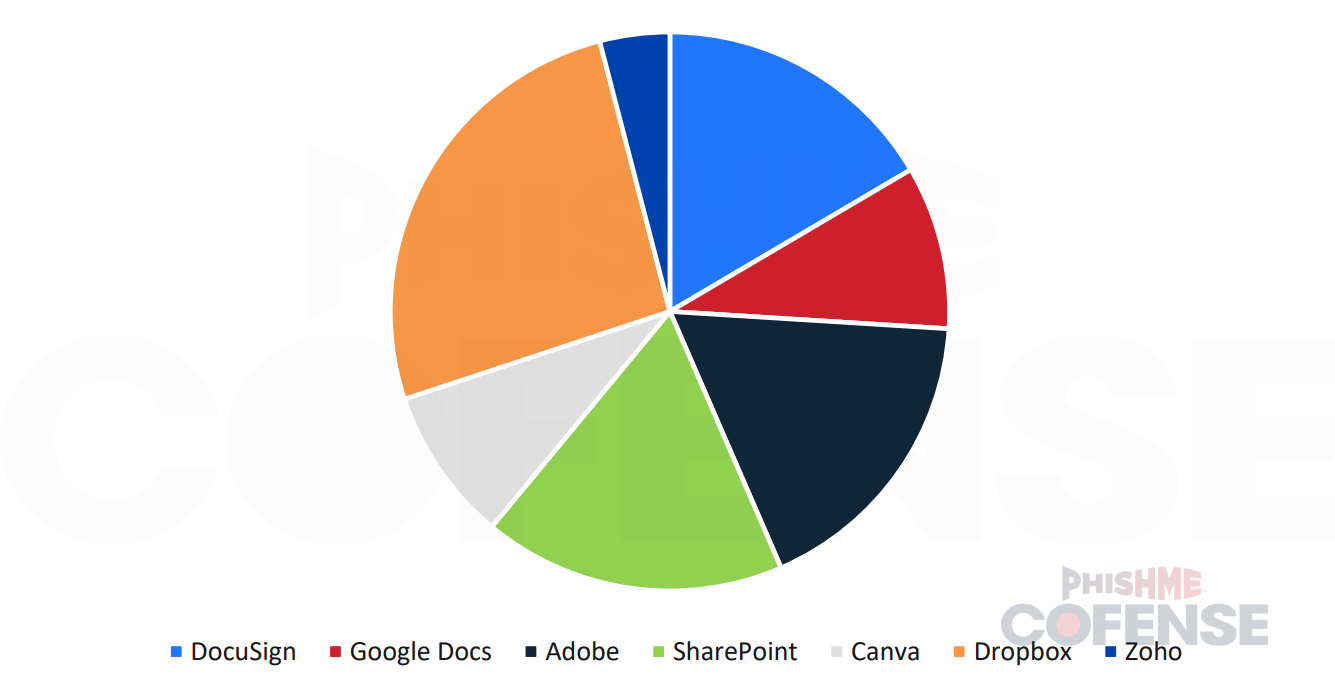
Figure 2: Pie chart showing the distribution of the most popular online document hosting services abused in 2024.
DocuSign
DocuSign is not only commonly spoofed in the credential phishing landscape but also commonly abused by threat actors. During 2024, DocuSign took up just over 16% of all online document hosting services being abused. DocuSign is also one of the more common domains to be seen using a QR code within the document, with this domain taking up 6% of all credential phishing links containing a QR code.
This is likely due to DocuSign being a popular document sharing service and the common usage by human resources (HR) specifically, making SEGs automatically trust the domain. DocuSign does attempt to remove these campaigns; however, DocuSign has functionality that can help aid threat actors.
One example of this is the ability for DocuSign links to expire after clicking once, which would then send another DocuSign link to the original recipient and prevent post-incident analysis by incident responders or security operations center (SOC) analysts.
On top of this, when a document is shared to a user, DocuSign will email the user, which can make it more difficult for SEGs to block emails. An example of an email abusing DocuSign can be seen in Figure 3.
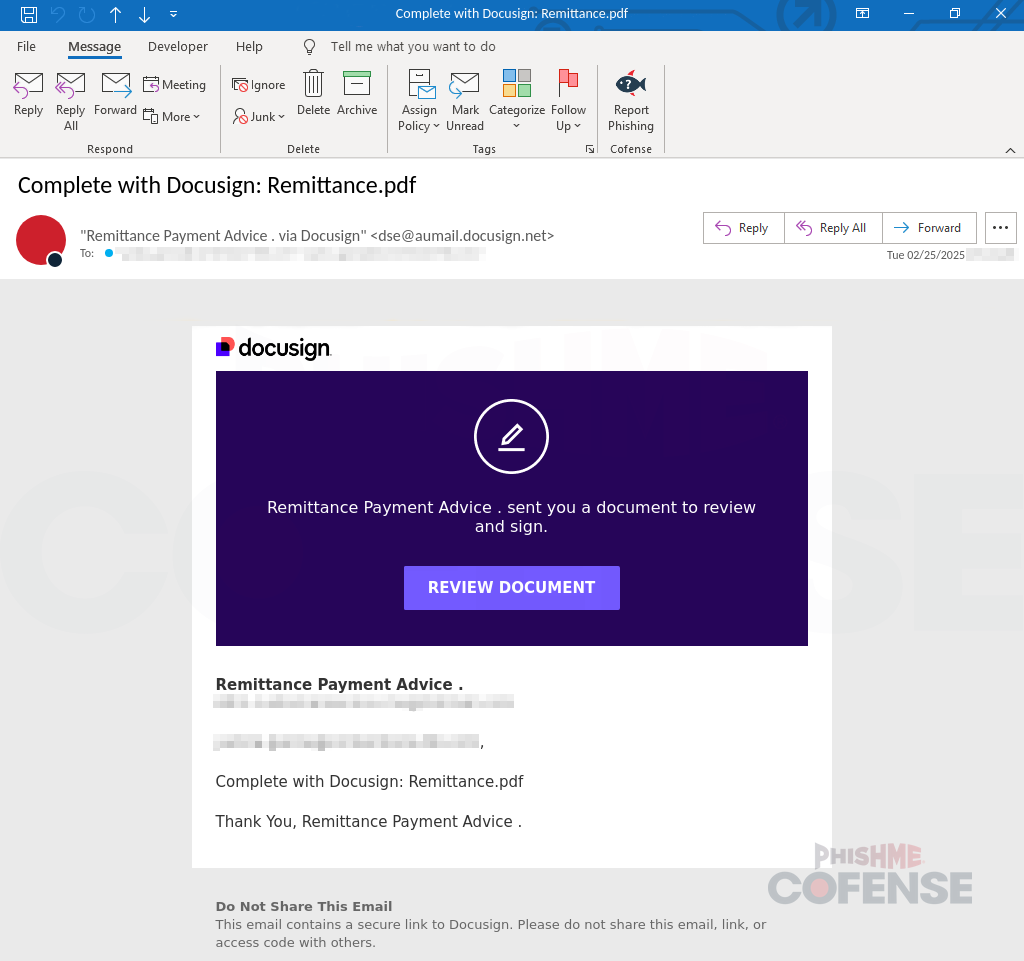
Figure 3: Example of a DocuSign credential phishing campaign.
Google Docs
Google is one of the most popular internet domains, offering multiple file hosting services, such as Google Documents, Google Drive, and Google Sheets. However, threat actors have taken advantage of the blind trust many SEGs have with Google, sending Google Documents to users in an attempt to direct them to credential phishing pages.
Google Document links only take up 11% of all online document hosting services being abused in 2024; however, it is important to also point out that Google Docs is more often seen as a way to deliver malware via an embedded link. Google does attempt to take these accounts down; however, the document typically stays online for some time unless it is specifically reported by a user.
On top of this issue, threat actors can share Google Document files through Google, making it more difficult for SEGs to block the email address since it is well-known.
Adobe
Adobe has been a staple brand on the internet for decades, and therefore, many people trust the Adobe domain. Adobe allows PDF hosting, which is what threat actors focus on to gain not only the user’s trust but also the SEG’s trust. Adobe is just slightly more popular than DocuSign, being used for just over 17% of all online document hosting services abused in 2024.
Adobe does make attempts in taking down these PDFs; however, due to the extreme traffic Adobe has due to its popularity, PDF takedowns can take days, with oftentimes the credential phishing site being taken down before the initial Adobe link.
SharePoint
Due to the extreme popularity of Microsoft services and products in work environments and at home, SharePoint is an extremely popular option for threat actors. Since products such as SharePoint are very common in work environments, most SEGs will allow these emails to enter user inboxes.
Many threat actors will even impersonate a coworker or another company to lure users to click the SharePoint link which leads to the malicious phishing domain. SharePoint contributed 17% of all credential phishing using online document hosting services in 2024. Although Microsoft does attempt to take these accounts down, the landing page after SharePoint is often taken down before the actual Microsoft account.
Canva
Canva, although not as common of a name compared to those previously mentioned, is another popular PDF hosting site. The unique aspect of Canva is that digital media can be displayed in several formats, such as social media graphics, documents, and PowerPoints, to list a few.
However, Canva is slightly less popular among threat actors at just under 9% of all online document hosting services abused in 2024. However, Canva has been quick with PDF takedowns when malicious content is reported.
Dropbox
Dropbox is one of the most popular file-hosting websites, causing threat actors to attempt to abuse the website. Dropbox is used by both individuals as well as companies, therefore, SEGs often do not block these links. Dropbox was the most popular online document hosting service abused in 2024, being 25.5% of all abused online document-hosting services.
Although Dropbox does attempt to take down malicious files, due to the extreme popularity of Dropbox and the large amount of content requiring review, this can take days.
Zoho
Zoho, although the least popular in this list, is still an extremely popular file-hosting website. Barely taking up 4% of all online document hosting services abused in 2024, Zoho is still prevalent in certain regions. Zoho specifically saw a major spike in December 2024, containing nearly 33% of all Zoho abuse in 2024. This high amount of abuse has been witnessed to continue into early 2025.
This could likely be due to threat actors sharing notes regarding which legitimate websites pass through SEGs, and since Zoho is not a common file-hosting site compared to the previously mentioned, many threat actors may not have thought about using Zoho until recently. Zoho has also been previously criticized in the past regarding credential phishing takedowns, with the public complaining about how long it takes for Zoho to take down these campaigns.