The Cofense Phishing Defense Center (PDC) employs threat analysts to analyze emails on behalf of enterprise customers across the globe, in various industries, with users reporting suspicious emails hitting their inboxes. To help keep up with evolving tactics and top ongoing malware threats affecting customers, we’ve created a breakdown of the top five malware families we have observed across our customers over the past thirty days.
Top Malware Families in February:
1. Ursnif
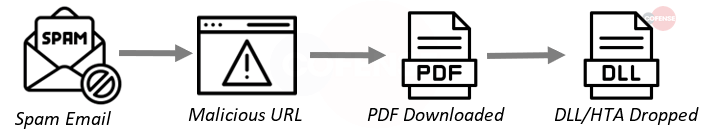
Ursnif is a multi-purpose trojan that is primarily used to harvest banking credentials. Delivery methods can range from VBS downloaders to Excel files that utilize OfficeMacros to download DLLs. One primary objective is to conduct man-in-the-browser attacks by loading itself into legitimate windows processes.
- Subject: Many of the Ursnif samples delivered this month were made to look like communications from the government agency ‘Companies house’.
- Attachment: Most Ursnif were delivered using a URL instead of an attachment.
- Behavior: Victim is tricked into opening a PDF, delivered via a URL embedded in the email, where a DLL and set of instructions in the .hta filetype are sent over.
- Brand: Legal // Companies House
- Infection Chain:
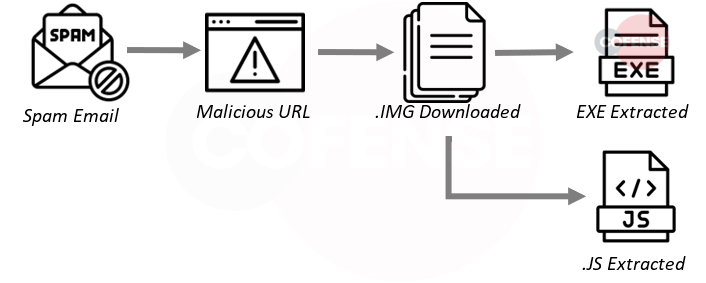
2. QakBot
QakBot is a modular banking trojan with worm-like features that enable its propagation across a network. Once installed, it will use a man-in-the-browser technique to harvest credentials. The campaigns delivering QakBot re-use legitimate emails to deliver zip files containing the malicious word document.
- Subject: The deliveries of QakBot this month are using replies/Fwd to previous emails to make them seem more legitimate. Because of this, the subjects are varied.
- Attachment: QakBot was primarily delivered using URLs this month.
- Behavior: URL downloads a .img file containing a large number of various files that make the malware work. Each file contains a section of the functionality.
- Brand: Re: // FWD: // Etc.
- Infection Chain:
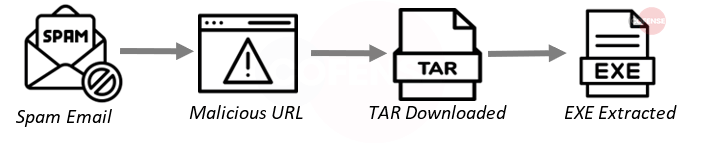
3. Agent Tesla
This keylogger is known for checking browser activity to steal banking information and will send the data through various methods. The most recent variants will use SMTP, Telegram, and mail servers under the control of the threat actor.
- Subject: Subjects delivering Agent Tesla this month were mostly made to appear as purchase inquiries and asked the user to give them their best price and click a link. The language used was varied.
- Attachment: Agent Tesla was delivered this month using a Malicious URL instead of an attachment.
- Behavior: URL delivers an .tar archive containing an exe which, when launched, will run in the background and act as a keylogger.
- Brand: Inquiries // Purchasing Director
- Infection Chain:
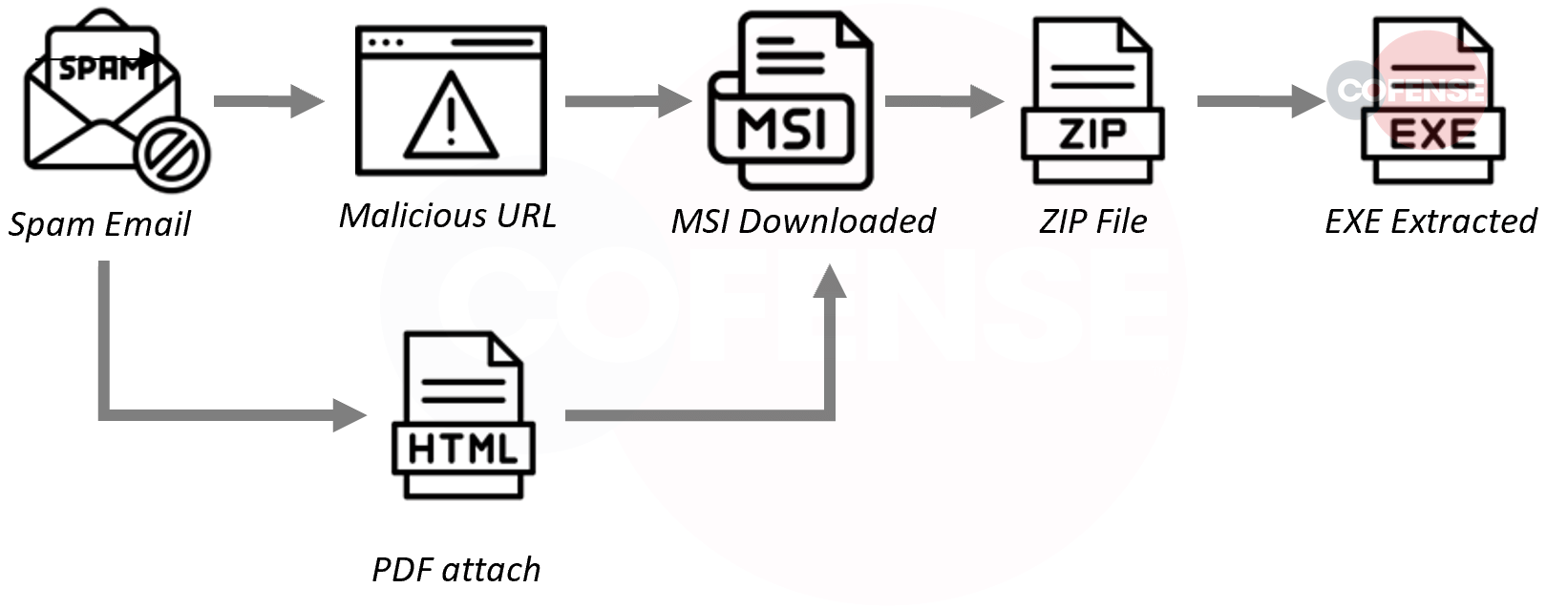
4. Mekotio
This trojan targets Spanish speaking users and will download its payload using various methods. After infection, it will download a ZIP file which contains JS, DLL, and an AHK file. The JS will use AutoHotKey (AHK) to run the DLL which is the main Mekotio payload. A new variant of Mekotio is utilizing a DLL side-loading technique where DLLs related to legitimate applications are run, which then load in Mekotio.
- Subject: Subjects were predominantly made to look like Spanish invoices.
- Attachment: Mekotio is delivered mainly as a URL instead of an attachment.
- Behavior: URL delivers an MSI which, when clicked, will pull the stage 2 .exe.
- Brand: Fractur // Spanish
- Infection Chain:
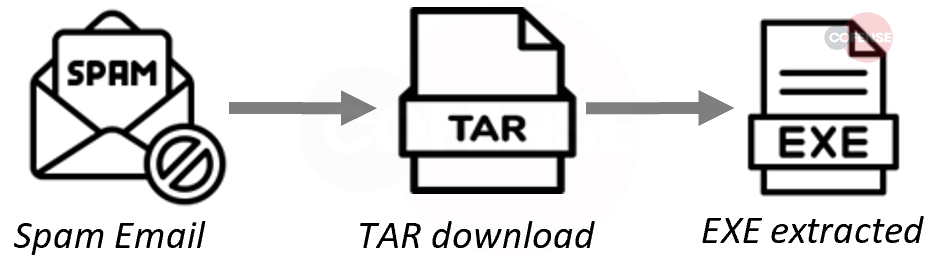
5. Remcos
Remcos was originally a remote desktop connection tool that has since been repurposed as a remote access trojan capable of taking control of a user's system. Its chief capabilities include key logging, information stealing, and audio/visual monitoring.
- Subject: Remcos was delivered as a fake invoice for a payment. Typically, the emails were delivered in Spanish, however some were delivered in other languages as well.
- Attachment: Remcos was delivered using Google docs URLs instead of attached malware.
- Behavior: Once the archive (either .tar or .rar) is downloaded and the contained .exe is executed, it waits in processes while reachine out to C2 for further instruction.
- Brand: Fractur // Invoices // Google Docs
- Infection Chain:
Summary
This month we observed the return of QakBot and a large increase in the delivery of Ursnif. Of note, we have seen a decrease in the overall prevalence of banking trojans such as Banload and it has fallen off the top list for now. The Cofense Phishing Defense Center (PDC) will continue to watch these threats as they evolve and deal with situations as they arise. All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results. The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.