Found in Environments Protected By: Microsoft, FireEye
By Naresh Edara, Cofense Phishing Defense Center
The Cofense Phishing Defense Center (PDC) has observed a highly spoofed phishing email campaign imitating the Australian Tax Office (ATO) and MyGov website, trying to harvest MyGov login credentials. The PDC has observed these campaigns during Tax times, and randomly, in guise of an account verification, or fraud prevention alerts. ATO phishing attempts are not uncommon within the APAC region and have been frequenting Australian clients for some time. These campaigns attempt to create a sense of familiarity/trust along with scare tactics to try and influence the victims to engage with the email.
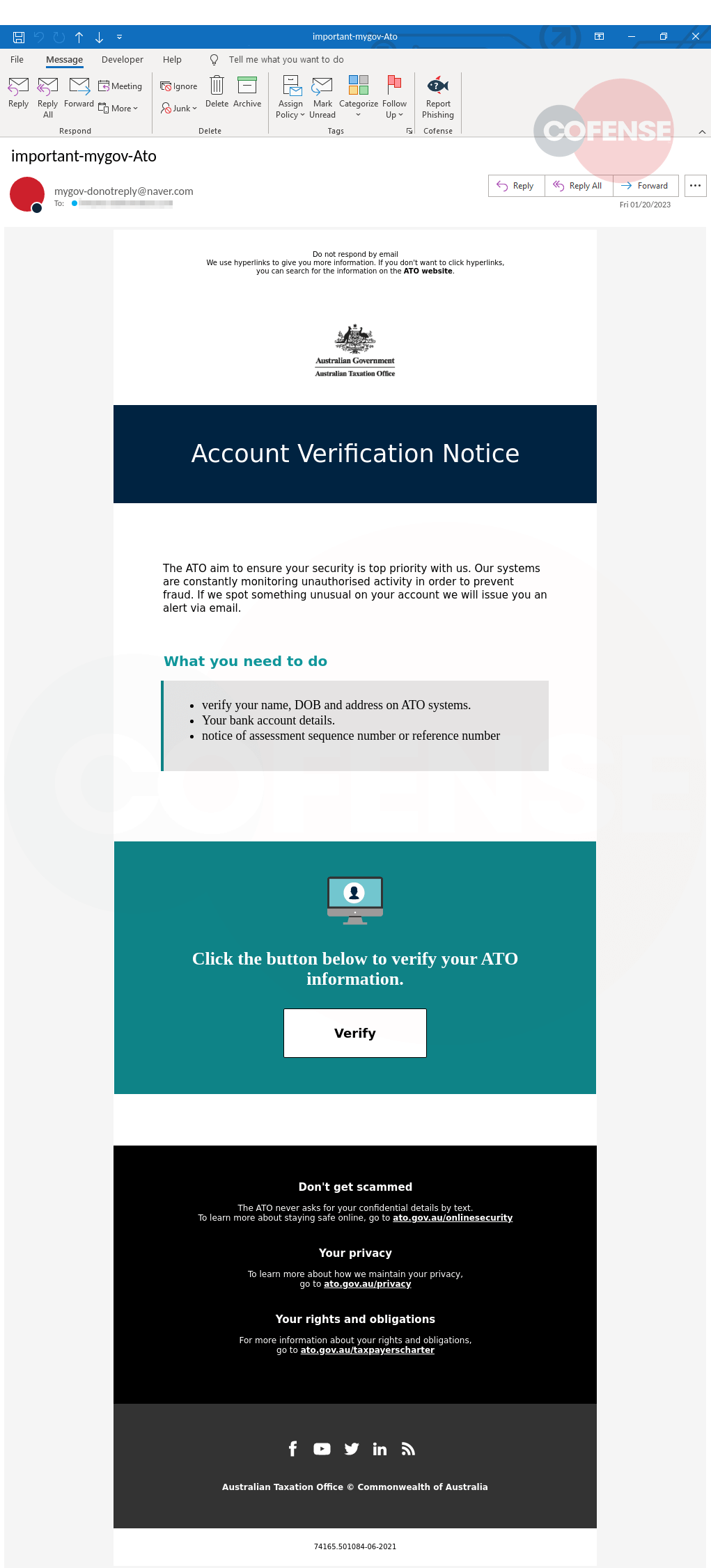
Figure 1: Email Body
The email body is designed with legitimate Australian government logos and branding to create familiarity & trust so recipients to click on the phishing link and enter their MyGov login credentials. The threat actor has spoofed the from address to look like it’s coming from ATO. They are attempting to assure the recipient’s security by pretending to monitor for unauthorized activity and requiring the user to verify their account due to unusual activity. If these tricks work in the threat actor’s favor, the target will click the white button labeled “Verify.”
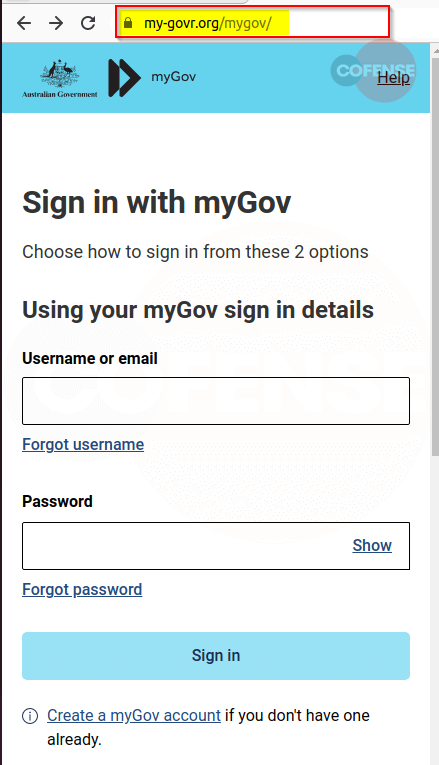
Figure 2: Phishing Page
The phishing page is an exact replica of the legitimate MyGov login page for ATO. Further utilizing Australian Government and MyGov logos yet again, the URLs linked to the logos and hyperlinked text even take you to the official MyGov page. Possibly another tactic to convince the victim that the page is legitimate. However, the domain name of the website is a slight give away. Due to its close resemblance and use of possible typo-squatting of the legitimate site, many users may fall prey to this phish and enter their credentials.
This campaign illustrates how automated systems fail to outperform humans, and the network effect of people as sensors, spotting and reporting suspicious email. It shows how threat actors are trying to leverage familiarity and trust along with scare tactics to get users to verify their account, while in fact they are attempting to harvest credentials with these tactics. With Cofense Managed Phishing and Defense, provided through our Phishing Defense Center (PDC), enterprises benefit from our complete view of real phishing threats. In five years, no customer using Cofense PDC has experienced a breach resulting from a phishing attack.
| Indicators of Compromise | IP |
| my-govr[.]org/mygov/ | 206.189.157.71 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.