Found in Environments Protected by: Mimecast
Author: Olwen Brangan
Cofense Phishing Defense Center
The Cofense Phishing Defense Center discovered a multi-stage phishing campaign targeting customers from Xneelo, a South African web hosting provider who supports over 500,000 customers. Xneelo provides customers with two options of control panels to manage accounts: the Xneelo control panel and the older KonsoleH control panel. In this four-stage attack, threat actors attempted to obtain login details for the Xneelo control panel and Webmail credentials through a fake KonsoleH login page, as well as credit card information and SMS two-factor authentication (2FA) codes.
Stage 1 – Xneelo Credentials
Initially, the user is presented with an email as shown in Figure 1. Aspects of the email appear genuine: the spoofed email contains the Xneelo logo and Xneelo's address and phone number. However, there are indicators at this stage which raise suspicion about the validity of this email. Of note is the generic greeting "Hello", a tactic often used by threat actors, but not particularly unusual by itself.
Another red flag is the sense of urgency portrayed in the email. The user is strongly encouraged to click on the ‘Pay Now’ button. Failure to do so could result in the termination of services and deletion of hard drive content, leading to a full loss of data as they do not keep backups. This message is enforced using language such as "Please settle your account to avoid suspension of your service", "deactivate" and "immediate" in bold. Note the payment due date is prior to the date of issue, implying an overdue payment, further enticing the email recipient to act quickly, although the requested amount due is R0.00.

Figure 1 - Email Body
In Figure 1, the “Pay Now” button redirects the user to hXXps://postingbank[.]wpengine[.]com/sudd/ where the fake Xneelo login page is located (Figure 2).
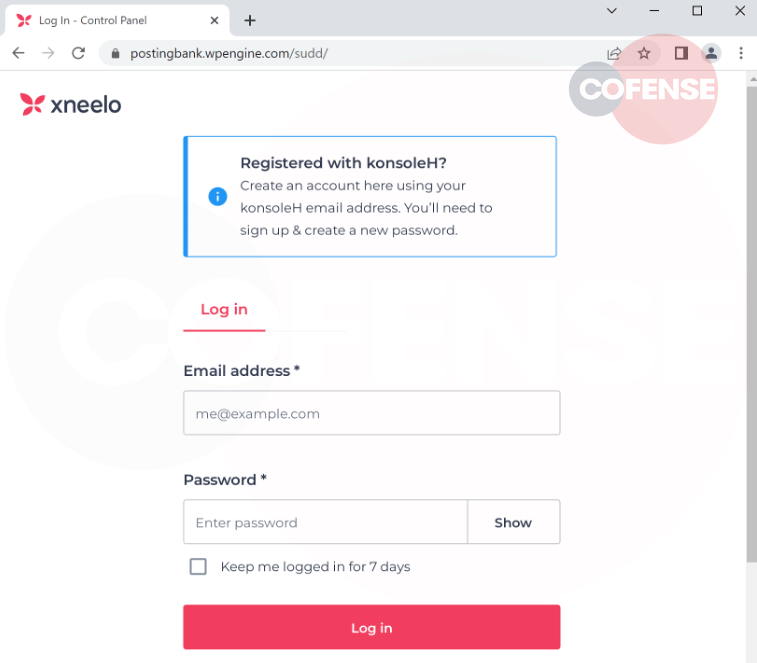
Figure 2 - Fake Xneelo login page
This login page presents a message about signing up, however the 'Sign Up' button is not available. Logging onto Xneelo's real website (https://xneelo.co.za/) shows a similar page with the actual 'Sign up' button beside the 'Log in' button. Omission of buttons or other details are red flags this email and page are suspicious. Spelling errors such as “Pyament” instead of Payment in Figure 3 are also red flags.
Stage 2: Credit Card Data
Once the user enters their Xneelo login credentials, a page requesting credit card information is presented (Figures 3 and 4).
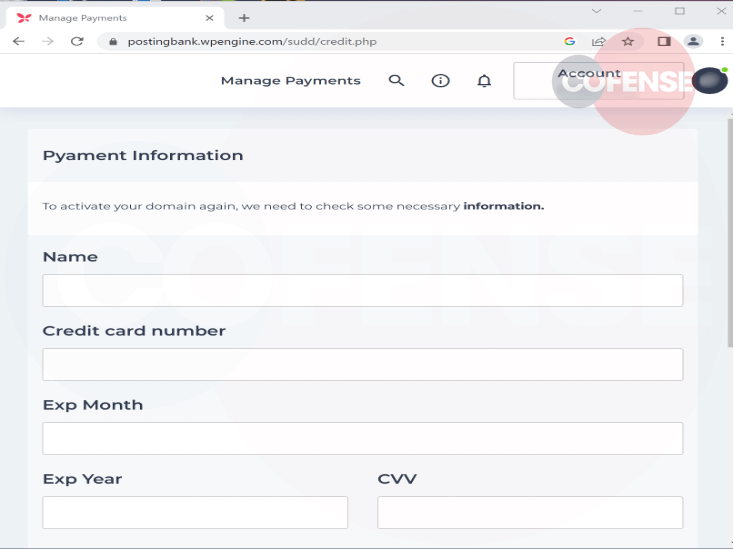
Figure 3 - Credit Card Information
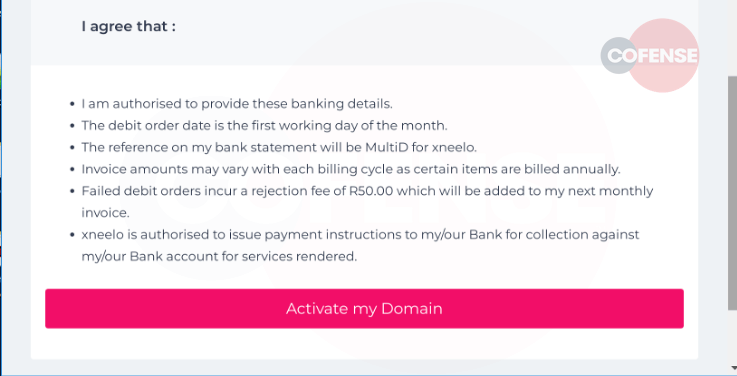
Figure 4 - User Agreement
To appear genuine, a consent list is included containing information from the real Xneelo website: the debit order date is the first working day of each month, the reference used on customers bank statements is MultiD and Xneelo does charge a fee of R50.00 for failed debit orders.
Stage 3: SMS
Having provided the malicious actors with login credentials and credit card information, users then are asked for an SMS code to verify their identity and click the 'Activate my Domain’ button shown in Figure 5.
Phishing for 2FA codes is common. Threat actors use the stolen credentials to interact with the real website and prompt it to send such SMS codes to users. Once users input the code into to the phishing website, threat actors can use it to successfully log in as the users.
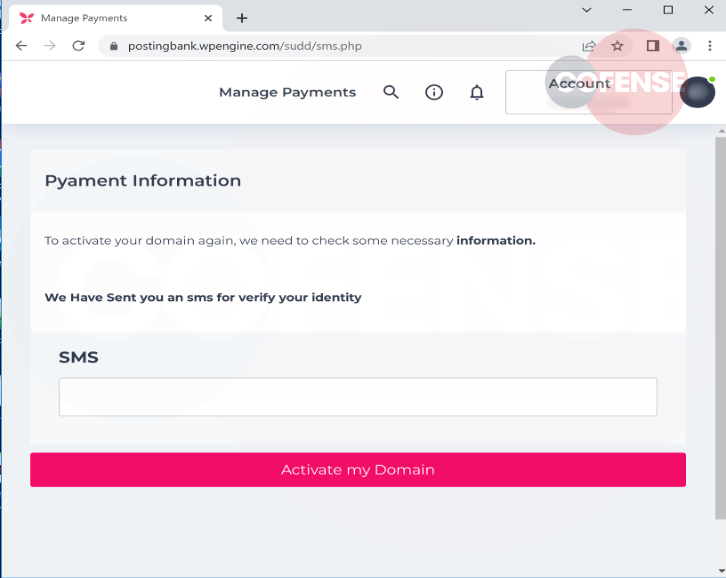
Figure 5 - SMS
Stage 4: Webmail Credentials
The fourth and final stage of this phishing campaign occurs when the user is directed to a webpage which spoofs the real KonsoleH webmail page (Figure 6).
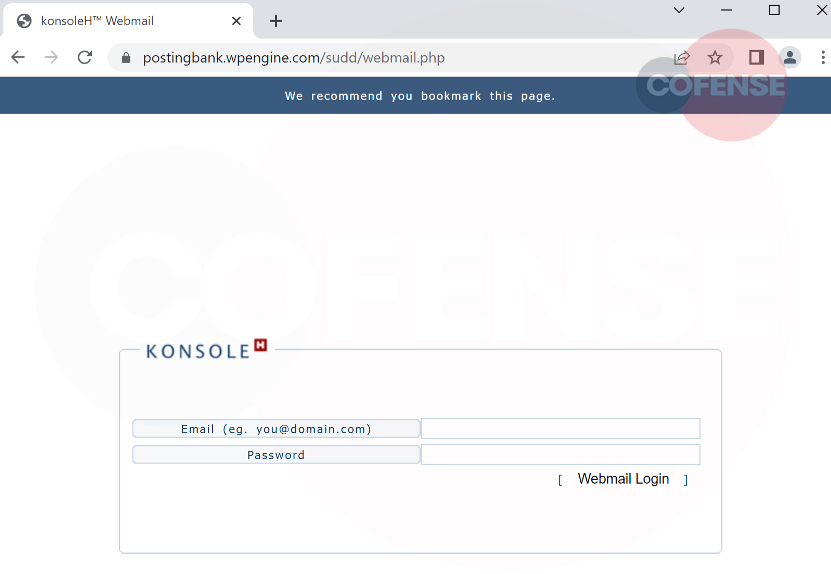
Figure 6 - KonsoleH Webmail Login
Once the user enters an email address and password, and clicks the 'Webmail Login' button, the malicious actors will obtain the users credentials. Access to webmail allows malicious actors to do a variety of tasks including importing or exporting email contacts, access emails that are on the mail server, set up an auto responder using the manage mailbox option, access emails from any computer with an internet connection and create new accounts.
Indicators of Compromise:
| Indicators of Compromise | IP |
|---|---|
| hXXps://postingbank[.]wpengine[.]com/sudd/ | 34.173.203.221 |