Author: James Hickey, Director Sales Engineering
This should come as no surprise, but email is the #1 attack vector used by cybercriminals. Do you know why? Because it works. Unsuspecting users are tricked every day into clicking malicious emails that make it to their inbox.
As a Google customer, you benefit from their security measures, like the Google email security controls which act as a secure email gateway (SEG) to stop threats. Google claims that “Gmail's cutting-edge AI defenses block more than 99.9% of spam, phishing attempts and malware.” But, like all technology solutions in use independently at the perimeter, it’s not perfect at stopping evolving new threats and still lets threats through to user inboxes.
How do we know?
Because every day our Phishing Defense Centre (PDC) sees thousands of threats that have bypassed SEG technology into our customer environments, several of which are Gmail clients. Luckily, Gmail customers have access to one-click threat reporting and our PDC team to provide a turnkey, managed service to analyse and remediate email threats before they pose a problem.
So, what sort of threats get through? And more importantly, what can you do about it?
Despite Google’s Use of Their Own AI, the Gmail Email Security Controls Cannot Filter Many of Today’s New, Advanced Threats
Cybercriminals are constantly evolving their tactics to stay ahead of security measures. With a continuously changing threat landscape, it’s difficult for Google to stay up-to-date on new types of cyber-attacks. Put simply, even AI models will not spot certain threats if they have not been trained and educated on the latest tactics being used. Threat actors know this and they exploit it.
As a perfect example, the use of malicious QR codes in emails is on the rise, with an average month-to-month increase of 270%, according to Cofense Intelligence. These email attacks make it past all types of SEGs because these gateways are not able to scan the image for the embedded malicious link. Let’s look at a real, redacted example found in a Gmail environment.
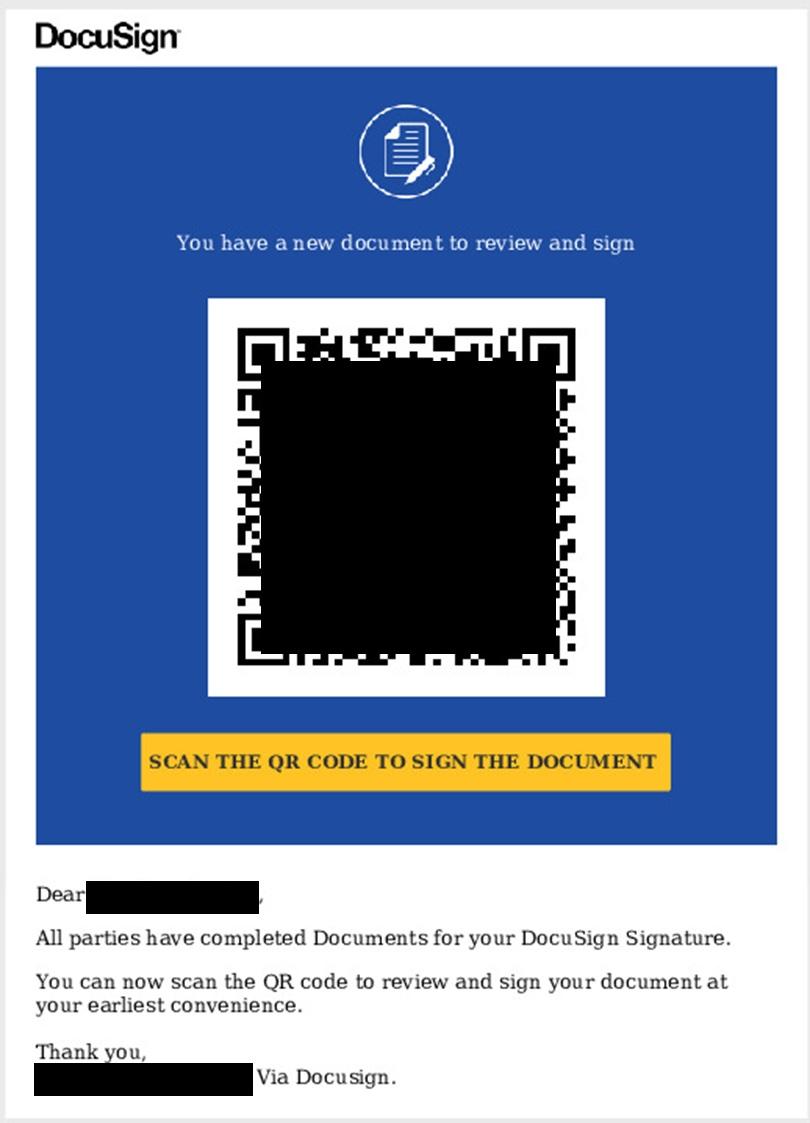
In this case, the threat actor is sending a Docusign document, accessed via a QR code to the user. If the user scans this with their phone, they are immediately taken out of your corporate, secure desktop environment to their unsecured personal device, at which point the threat actor can have them do almost anything.
Social Engineering Attacks
Threat actors are also using social engineering tactics with threats like smishing (SMS text-based phishing) and vishing (voicemail-based phishing) to target employees. Both threats bypass the Gmail email security controls easily, as they often don’t conform to the way the AI model has been trained, and as a result put your company at risk for a costly breach.
Let’s look at a great (redacted) example of this type of attack, again found in a Gmail environment:
Note also, the email message that came along with this supposed invoice below.
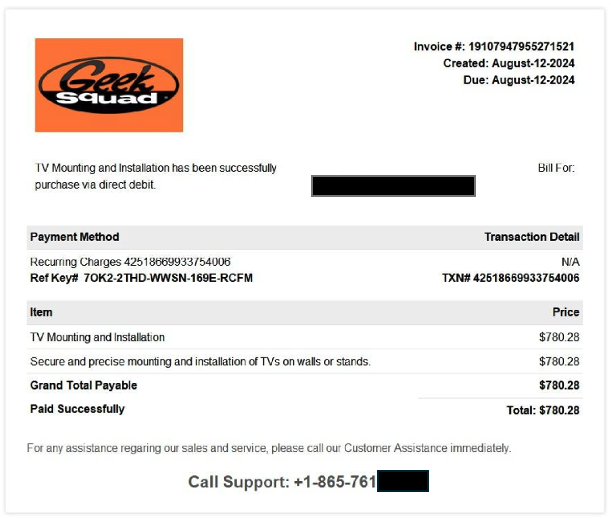
In this example, the user in a US corporation is being sent a Geek Squad invoice for $780. Geek Squad is an often-abused brand and in this case, notice there are no links or attachments to click on. There is simply a phone number at the bottom for the user to call. The user, falling for this attack, might worry they are being wrongly billed and call the number to check, at which point, they are outside of corporate security controls and on the phone with a motivated threat actor. Eighty-five percent of vishing attacks start with the user receiving an email like this with a motivating factor (fear, urgency, etc.) to get them to dial a number.
Complex, Multi-Stage Credential Phishing Attacks
SEGs, including Google’s email security controls, cannot deal with complex, multi-stage phishing attacks. Let’s look at a recent redacted example, found in a Gmail environment, to see why that is.
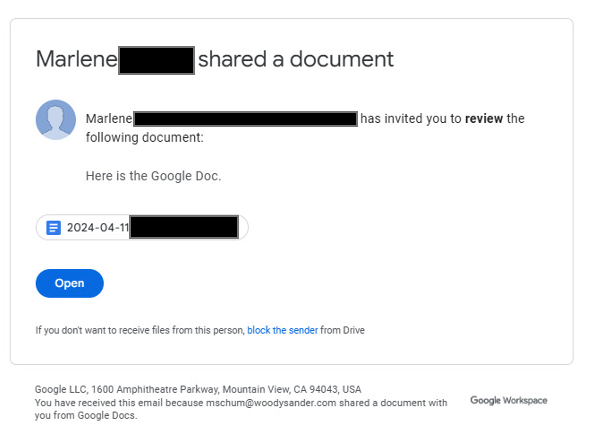
In this example, an already compromised internal mailbox is being used to send a malicious Google Doc link. The malicious document was sent internally from the compromised mailbox, so the Google email security controls were never going to detect it anyway. However, even it had come though the perimeter, let’s look and see what chance Gmail’s email security controls would have had in stopping this threat.
First, the above sharing request was sent as an image to evade detection. In this way, threat actors avoid any kind of text analysis done by the technology. In a Google Workspace environment, you might well be expecting to receive a Google Doc from one of your colleagues, so clicking on “Open” would be a common experience. However, in this case, that link would take you to a link at smore.com, a popular newsletter creation website being used to host the document:
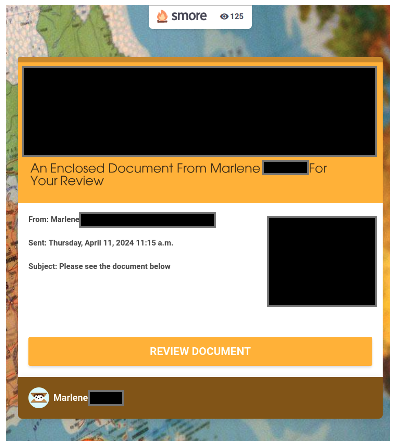
The user receives a note specifically tailored to them asking to review the document. It’s obvious this threat actor had been doing reconnaissance on this environment using the compromised credentials and knew that “Marlene” was likely to be someone sending documents to this user. (Real names and corporate logos used by the threat actor have been redacted.)
If you click on the “Review Document” button, you are redirected to an address at 307b.educdn.net, which then automatically follows a further redirect to a docsend.com address as summarised below:

At the time of analysis, the threat actor had already removed the final element of the threat chain, (as is often the case, the “time-to-live” of an attack is very short), but this could have included malicious content, such as a fake login page, or malware that could infect or compromise the user’s device. Most likely, there was some sort of form asking for the user’s details or credentials so these can also be compromised.
These complex series of redirects are common in advanced credential phishing attacks and, it’s clear to see, any SEG, whether AI-powered or not, is not going to have a chance in detecting the threat in these cases because its buried so deeply behind numerous links.
It’s an unfortunate reality but relying on Google email security controls alone cannot provide adequate email security protection.
So, What Do You Need to Do?
To combat today’s cyber threats, you must use a multi-layered security approach. Enhancing your Gmail email security with additional security measures including security awareness training and threat detection and response can help detect more advanced threats and reduce the risk of a breach.
Security Awareness Training (SAT)
Employees need to be aware of the various types of security threats out there and learn how to not only identify them, but also report them. Cofense PhishMe, the industry’s first SAT platform, offers award-winning training to millions of global users, including real-life email threat simulations, world-class training modules and one-click threat reporting capabilities. Our Gmail “Direct Delivery” capability enables Cofense PhishMe operators to ensure that scenario emails are delivered directly to the Gmail inboxes of scenario recipients.
This feature prevents your organisation’s gateway filters and ‘allow listing’ from inadvertently handling PhishMe scenario emails as spam and, by way of the Google API, delivers scenario emails directly to recipients' Gmail inboxes.
Threat Reporting & Detection
Along with training, you also need an additional layer of threat detection to reduce the risk of a successful email security attack. Cofense’s Reporter button, which allows users to report threats with a single click, is available for use in Gmail environments and is delivered “Browser Independent” as a Google add-on, not just as a Chrome Extension, so users can report suspicious emails when reading their emails in their favourite browser.
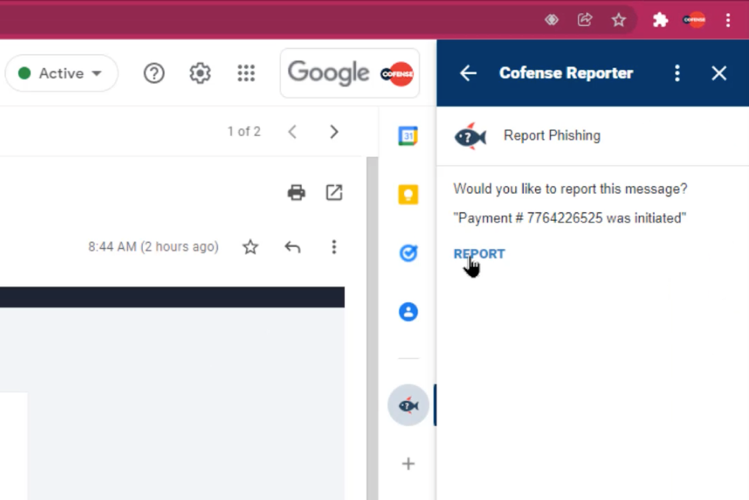
Once reported, Cofense Triage can ingest thousands of user-reported phishing threats, analyse every single one of them, and then automatically remove them from networks across the globe. All of these are missed by SEGs that are used as a first line of defence. When a reported threat is analysed and identified as malicious, the IOC’s can be identified and this “human-vetted” intelligence is shared across organisations and allows them to take additional defensive measures where required.
So, while Google’s email security has its place in the hierarchy of security controls, on its own, it’s not enough.
Only Cofense sees what all SEGs miss.
We stop those threats and keep our global customer base secure. To learn more about Cofense’s world-class SAT and PDR solutions, please visit www.cofense.com so we can answer any questions you have.