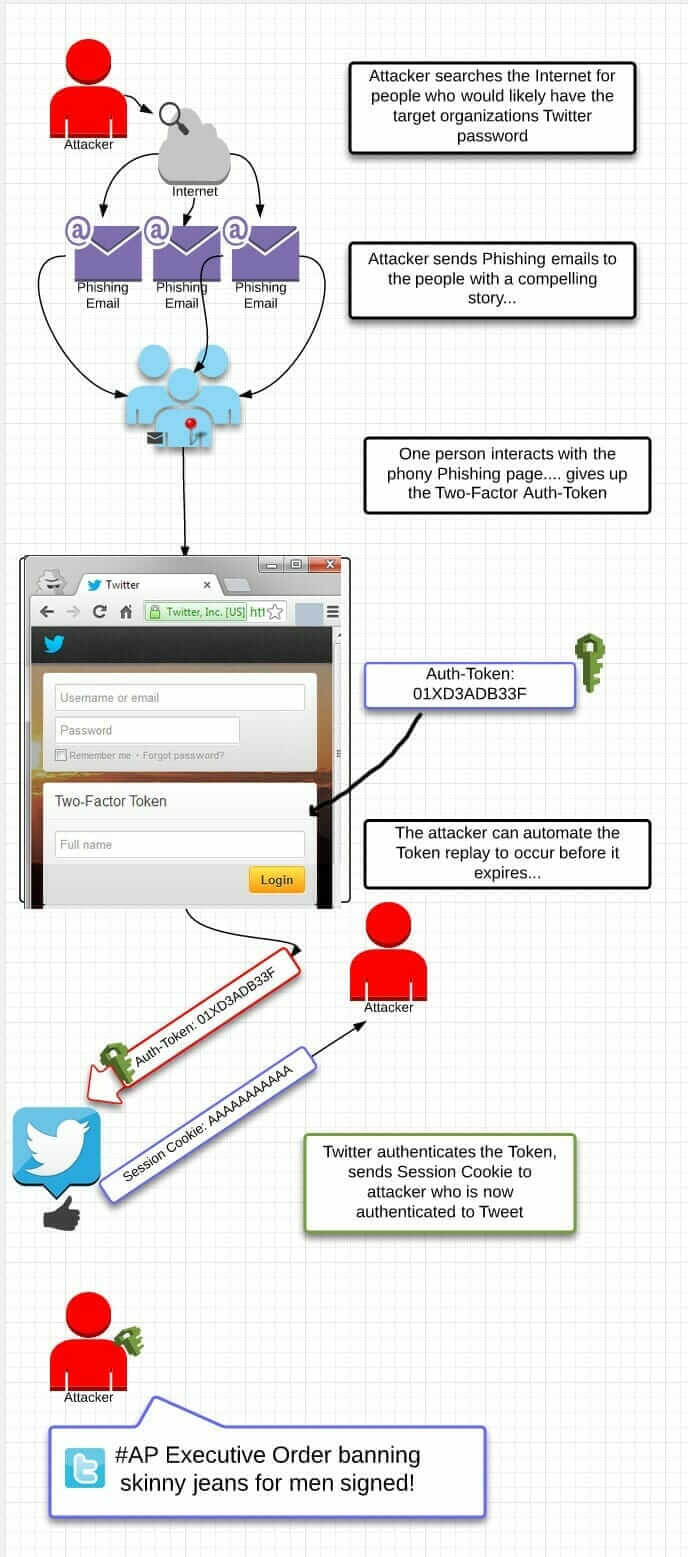
If a user is tricked into revealing login credentials to a false landing page, 2-factor authentication will only limit the time the hacker has access to the account. Attackers would need to collect the 2nd factor of authentication, but the underlying tactics would remain the same. Even if a session cookie expires every few hours (which for Twitter would be days – not hours or minutes), then the attackers would still be able to cause the kind of mayhem we saw today. As we saw, it only took minutes for a tweet to make stock trading algorithms go bonkers. The following graphic provides a visual of the process a hacker would follow to get past 2-factor authentication (note that this isn’t how the AP was hacked, it’s how a hacker would attack Twitter if it had 2-factor authentication):
- Stop Threats
BEC amounts to $500 billion-plus annually in losses. Ensure your business is protected.
Protect your user’s credentials and avoid a widespread, malicious attack.
With malware attacks on the rise, protect your business from all angles.
This latest tactic is only just beginning. Here’s how to get ahead of this threat.
Phishing is the #1 attack vector for ransomware attacks. Stop phishing attacks in their tracks.
Smishing is just all around us. Make sure your employees know how to stay safe.
Voice-phishing is on currently on the rise. See how Cofense stops vishing attacks with our SAT solution.
- Solutions
Phishing Security Awareness Training
Train your employees to defend against advanced email threats.
Email Threat Detection & Response
Automatically stop attacks that bypass your secure email gateway.
Phishing Intelligence Trends Review
- Clients
Businesses from all industries rely on Cofense to safeguard their teams.
Global organizations trust Cofense to protect their most critical assets.
- Resources
Check out our resource library of solution content, whitepapers, videos and more.
Come see us at a local event or join us at an upcoming webinar.
Contact us to get the most out of your Cofense solutions.
See why the Cofense Intelligent Email Security suite stands out against the competition
Stay current on cybersecurity trends, market insights and Cofense news.
See the real threats that are currently evading your Secure Email Gateway (SEG).
Protect your organization with our deep analysis into the current threat landscape and emerging trends.
Trusted partner to some of the best technology brands in the world.
- About
Cofense sees & stops email threats missed by standard security measures.
See the latest articles, press releases and more in our news center.
It’s an honor to be recognized in the cybersecurity market. Check out our recent awards.
Grow your business, drive new revenue streams, and improve your competitive posture through our Partner Program.
We’re looking for passionate people to join us in our mission to stop all email security threats for organizations around the globe.
Get to know our management team.
- Get a Demo