Author: Tonia Dudley
In our 2022 Annual State of Phishing Report, we observed the Business Email Compromise (BEC) threat category inch up from 6% to 7% of overall threats, with the Healthcare sector still leading the way at 16%. With increased attention and speculation around BEC, otherwise known as CEO fraud, Cofense CTO & Co-Founder, Aaron Higbee, BEC specialist and Principal Threat Advisor, Ronnie Tokazowski, and myself sat down to go in-depth on our findings and insights around this threat.
One of the highlights from this webinar was a new tactic we recently observed at Cofense related to direct deposits. As you can see from the message below, this threat actor leverages what many companies use as a best practice, utilizing self-service to update direct deposit information, making this tactic more effective.
 This is just one of many samples highlighted in the webinar. Below is a brief list of takeaways and topics discussed. You can hear the entire discussion on demand, plus register for additional annual report webinars on topics such as Secure Email Gateways and Ransomware.
This is just one of many samples highlighted in the webinar. Below is a brief list of takeaways and topics discussed. You can hear the entire discussion on demand, plus register for additional annual report webinars on topics such as Secure Email Gateways and Ransomware.
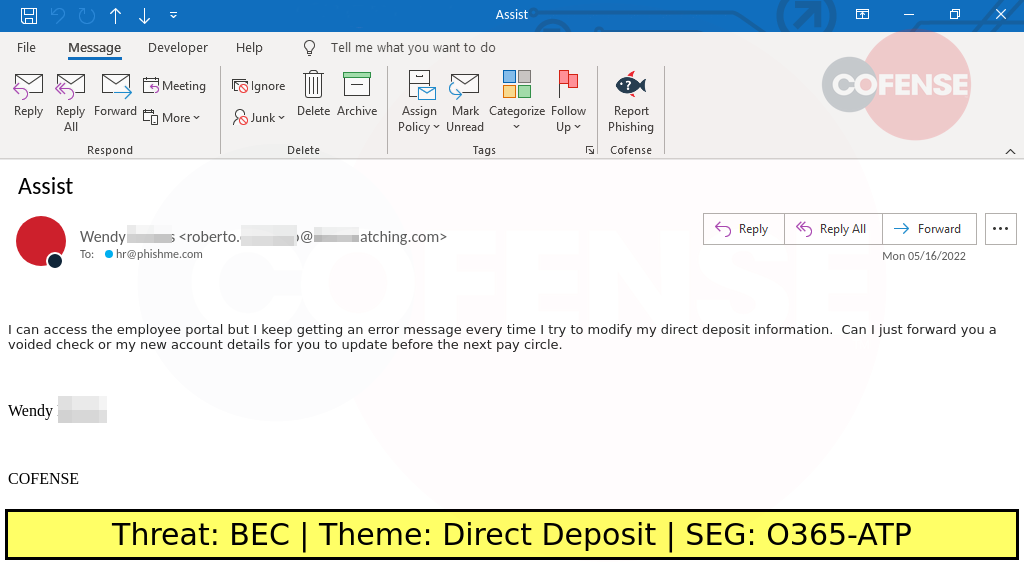 This is just one of many samples highlighted in the webinar. Below is a brief list of takeaways and topics discussed. You can hear the entire discussion on demand, plus register for additional annual report webinars on topics such as Secure Email Gateways and Ransomware.
This is just one of many samples highlighted in the webinar. Below is a brief list of takeaways and topics discussed. You can hear the entire discussion on demand, plus register for additional annual report webinars on topics such as Secure Email Gateways and Ransomware.
Key Takeaway #1 – Evolution of the Threat
In late 2015, Cofense first wrote about BEC as we ourselves observed our CFO received a spoofed email from our CEO, Rohyt Belani, asking for a wire transfer. As we continue to follow the tactics related to this threat, as with any other threat, threat actors have constantly adjusted their templates to minimize the detection of the secure email gateway (SEG) and spam filters. Many of the conversational starter emails are quite vague and take 2-3 follow emails to lure the recipient to execute the desired task (i.e. purchase gift cards).Key Takeaway #2 – Top BEC Threats for Enterprise
We dig a bit deeper into each of these topics on the webinar, but these are the top themes we have observed related to BEC.- Invoice Fraud – this isn’t surprising as we continue to observe this is a top theme for threat actors to gain access to one of their top objectives – MONEY.
- Thread Hijacking – nothing adds more creditability for a recipient to interact with a threat actor than an email chain that appears as three threads deep into a conversation.
- Gift Cards – while this threat tends to be small in currency, it tends to cost the employee directly as they’re unable to get reimbursed for this inadvertent purchase. Threat actors tend to make their request for gift card brand based on the exchange rate on the bitcoin marketplace.
- Direct Deposit – also known as payroll diversion, where the threat actor attempts to redirect your paycheck to their bank account instead of yours.
Key Takeaway #3 – Ways to mitigate against BEC
We closed out the webinar with a few quick actions you can take to help protect your organization against this threat.- Education. While we promote the optimal way to train your employees against phishing threats is phishing simulation campaigns, this threat is a bit more difficult to train using this methodology. When it comes to BEC, use your security awareness newsletters to include this topic, as well as real email images observed by your organization. By sharing a real email, it makes the threat real to your users.
- CEO Messaging. Ensure that your users understand that your executive team isn’t going to ask them to get gift cards to award clients or their family members. Be sure to include this in your New Hire Orientation (NEO) onboarding as this group of your employees are likely to be as familiar with your business practices or executive team.
- Implement and Enforce business process changes. When it comes to BEC, victims of these threats are all linked back to a breakdown in business controls to prevent large amounts of cash to be sent out of the organization.


