Found in environments protected by: Microsoft EOP
By Elmer Hernandez, Cofense Phishing Defense Center
The Phishing Defence Center (PDC) has observed malicious html attachments intended to carry out Browser-in-the-Browser (BitB) attacks.
What are BitB Attacks?
BitB attacks can deceive users by displaying what appears to be a legitimate separate pop-up login window. This window contains a spoofed URL bar with an identical-looking domain name from a trusted authentication provider. BitB attacks can be effective because they abuse modern Single-Sign-On (SSO) mentality and user trust in the URL bar. It is a stark reminder of how resourceful attackers can be in their attempts to compromise user credentials.
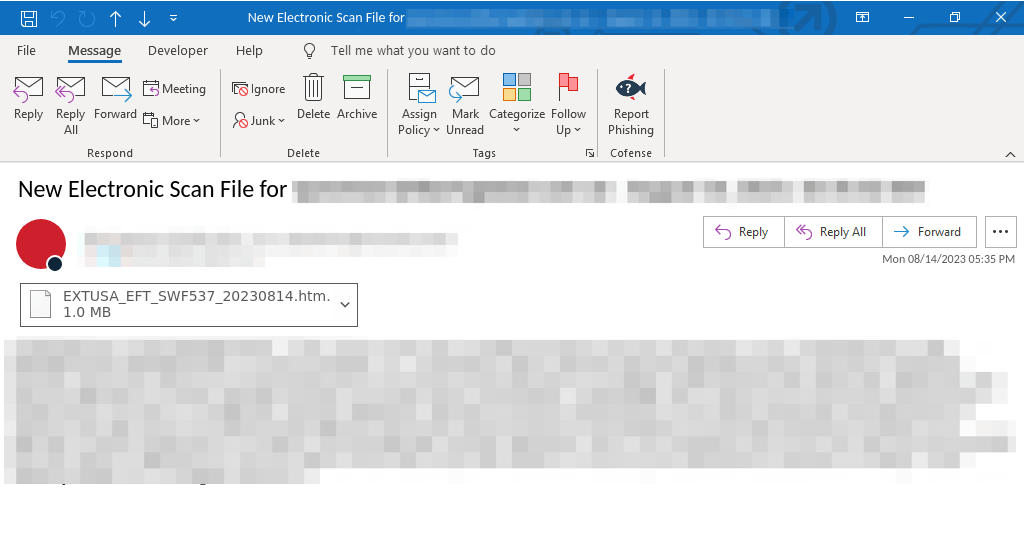
Figure 1 – Email
Figure 1 shows an example email seen by the PDC. The email contains no body, it only makes mention of a new electronic scan file for the user and includes the malicious html attachment. The attachment’s name could potentially refer to a payment, EFT may stand for an Electronic Funds Transfer, while SWF may make reference to the SWIFT payment system. The numbers at the end mark the date in a yyyy/mm/dd format.
Phishing Page
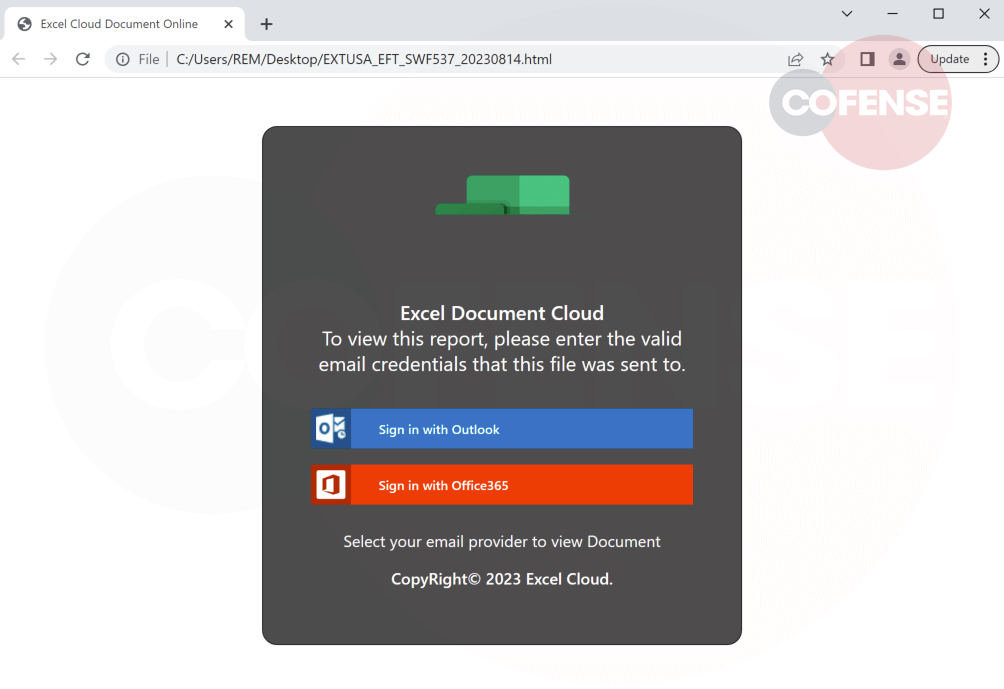
Opening the file will present the user with a subpar phishing page (figure 2). The page has an incomplete excel logo and lacks a background, it asks the user to provide the Outlook or O365 credentials from the account the file was sent to in order to view it.
Figure 2 – Phish Page
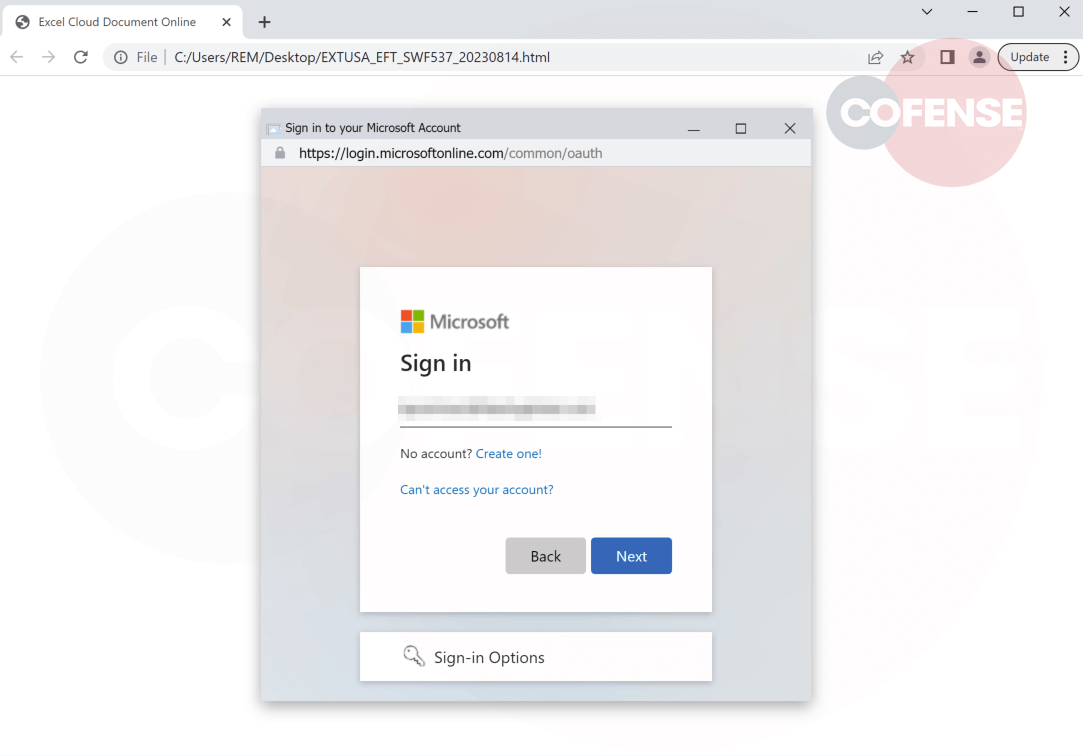
Clicking on either option will open a pop-up to provide the credentials (figure 3). In a world of SSO, users are familiar with pop-up windows used to authenticate with providers like Microsoft or Google in order to access an array of third-party services. BitB takes advantage of this SSO mentality.
Figure 3 – Pop-up Window
The most observant of users might realise that the Microsoft logo is missing next to the window title, and that “Sign into your Microsoft Account” is not the usual message displayed on the real Microsoft site, the correct one being “Sign into your account”. But this might be a big ask for the average user, who instead will likely look at the URL for any irregularities. After all, phishing education often stresses the importance of inspecting URL bars to ensure users do not find themselves on a dangerous spoofed site. Users are told to check the characters and spelling of the domain name as well as the presence of the familiar HTTPS padlock. Looking back at figure 3, we can see that the padlock is present and that the spelling of the Microsoft login domain is correct, this may lead users to ignore any other suspicious features and to wrongly confirm the window as legitimate.
BitB Template
The pop-up window is of course fake, attackers created it using a template by a security researcher known as “mr. d0x” who first wrote about BitB attacks last year.
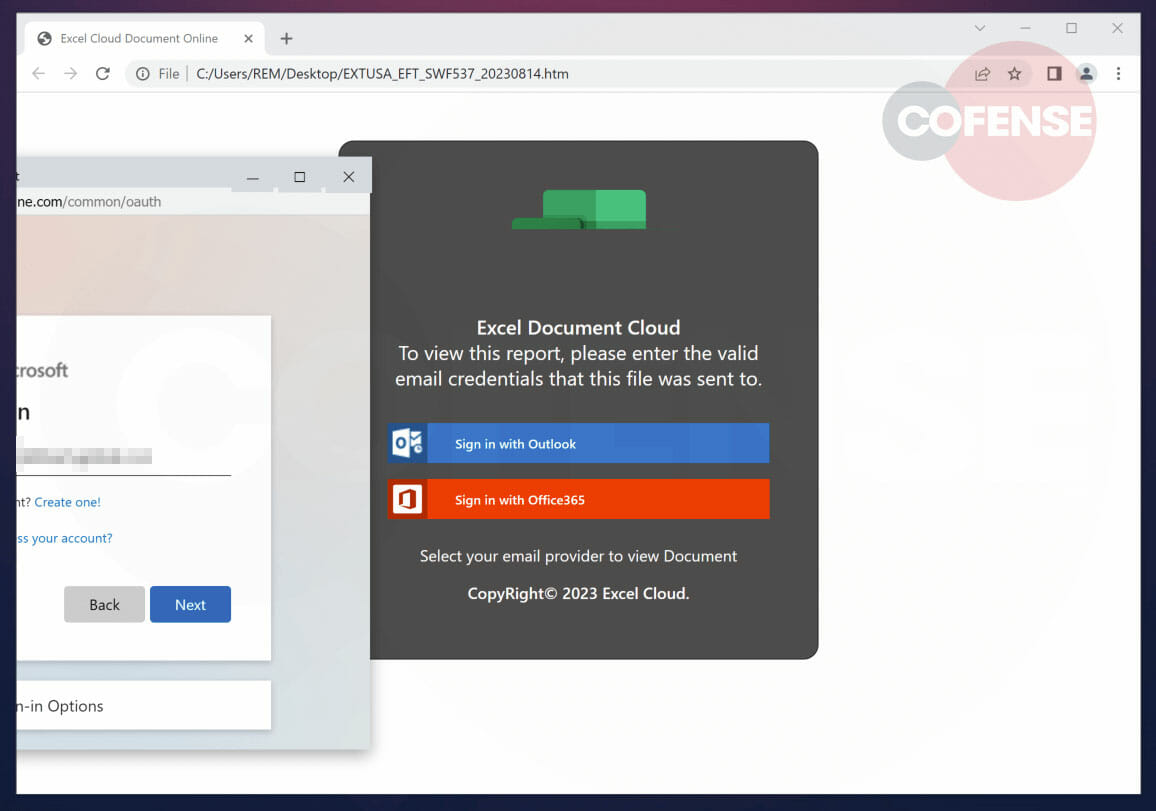
The pop-up is not independent, it exists exclusively within its parent window. To see this, we can try dragging it outside of the original window: a real pop-up window can be moved anywhere on the screen. However, figure 4 shows this is not the case, indicating it is fake.
Figure 4 – Unable to Drag the Window
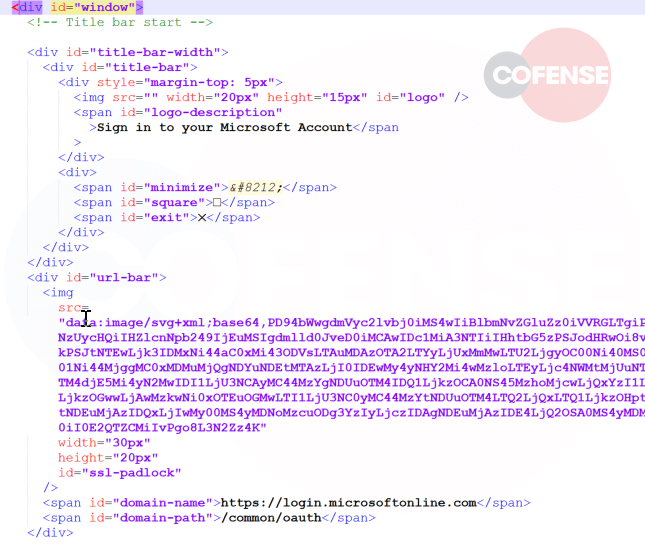
As for the URL bar, it cannot be interacted with because it is an image. Figure 5 shows the html file of mr. d0x’s BitB template.
Figure 6 – mr. d0x BitB Template
You can see attackers did not provide a source for the image with id “logo”, resulting in the lack of a logo at the top of the window. A <span> element adds the fake window title. The padlock in the URL bar is a base64 inline image, once more we see the fake domain and path added in the bottom <span> elements. The functionality of the pop-up is provided through some additional JavaScript.
The template offers high customizability for attackers, with the right stylistic elements it can become an effective technique to impersonate any brand and steal any set of credentials. While a BitB attack relies on a convincing pop-up window, this pop-up will always come from a bogus source whether a file or a phishing site. Users must remain vigilant and pay heed to any initial red flags.
| Indicators of Compromise URL | IP |
|---|---|
| hxxps://oferte[.]bavariamobility[.]ro/auth/mail[.]php | 52.57.233.78 |