In a recent wave of phishing attacks, cybercriminals managed to bypass secure email gateways (SEGs) from both Proofpoint and Abnormal Security to deliver emails that employed Microsoft-spoofing and artificial notifications into victims’ inboxes. These emails contained embedded URLs that led unsuspecting users to fake login pages designed to harvest credentials. Fortunately, the emails were identified, analyzed, and quarantined by the Cofense Phishing Defense Center (PDC) within minutes. This serves as a stark reminder of the evolving tactics of cybercriminals and the need for multi-layered defense strategies.
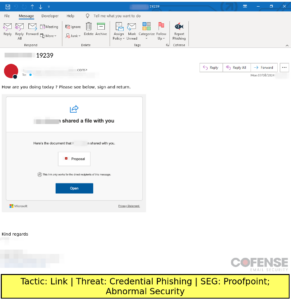
How Did They Do It?
These attackers used several tactics to outsmart traditional security measures:
- Email Spoofing: By mimicking trusted domains such as Microsoft, the phishing emails appeared legitimate to both end users and the SEG.
- Legitimate Embedded Domains: The domain of the URL embedded in the email was app[.]box[.]com which is widely regarded as being legitimate. The threat actors were able to take advantage of the fact that many SEGs and other solutions automatically consider trusted domains to be not worth scanning and thus disregard important information.
- Share File-Themed Messaging: Some emails were designed to appear as urgent document requests or shared files, leveraging familiar file-sharing services like Dropbox to trick users into clicking malicious links or downloading dangerous attachments.
- Timely Notifications: Another tactic involved the use of fake notifications, such as password reset alerts or account activity reports, purporting to be from a trusted entity. These notifications played on users’ fears and urgency, prompting them to click on malicious links or provide sensitive information hastily.
How Cofense Caught it
While Proofpoint and Abnormal Security missed these phishing emails, Cofense’s Phishing Defense Center detected and stopped the attack. Here’s how:
- Human-Led Phishing Defense: Cofense leverages human intelligence derived from our global network of over 35 million trained employees to identify threats. Security awareness training and user-reported phishing emails play crucial roles in our defense strategy. Looping in the human element helps Cofense spot things like “trusted” domains that SEGs miss.
- Automated Threat Analysis: Cofense’s automated systems analyze reported emails and URLs in real-time, identifying malicious patterns and stopping attacks in their tracks.
Cofense’s success in this scenario underscores the importance of a multi-faceted approach to cybersecurity. Through the integration of human intelligence, comprehensive training programs, and a robust rapid-response platform, we can identify and neutralize threats in real-time. While Proofpoint and Abnormal SEGs rely largely on artificial intelligence, Cofense ties in the human element, closing the gap and identifying more risks in your email security.
Conclusion
The incident serves as a critical reminder for cybersecurity professionals to continually reassess and upgrade their security strategies. While automated defenses are indispensable, incorporating human intelligence and maintaining a proactive stance on threat awareness is equally important.
Interested in learning more about how Cofense can enhance your cybersecurity posture? Contact us today!
The Cofense® names and logos, as well as any other Cofense product or service names or logos displayed herein are registered trademarks or trademarks of Cofense Inc.