By: Max Gannon
Domains hosting malware fall into roughly 3 categories: created, compromised, and abused. Created domains are domains created by a threat actor before a phishing campaign and are used in that campaign to deliver malware. Compromised domains are domains that have had some portion of their resources compromised and used to host malware.
Abused domains are legitimate service, such as Google Docs, which are being abused to deliver malware. It is important for both network defenders and everyday users to understand the differences, how often each is seen, and to know what to look out for. Although the categories are consistent with those seen in credential phishing, the ratios and the makeup of the domains are different.
For example, only 6% of all compromised and created domains used in email-embedded URLs to deliver malware directly or via a redirect from January to May 2023 made use of subdomains. However, as described in our Strategic Analysis Tailored Subdomains in Credential Phishing Campaigns, in 2022 over 69% of the credential phishing campaigns used subdomains.
Key Points
- Created domains are typically used by more advanced threat actors, are not highly effective at bypassing Secure Email Gateways (SEGs) and are highly effective at tricking victims. They made up 11% of the embedded URLs delivering malware seen in 2023 to date.
- Compromised domains are used by threat actors of moderate to advanced skill levels, are moderately effective at bypassing SEGs, and are moderately effective at tricking victims. They made up 53% of the embedded URLs delivering malware seen in 2023 to date.
- Abused domains are used by threat actors of any skill level, are highly effective at bypassing SEGs, and are highly effective at tricking victims. They made up 37% of the embedded URLs delivering malware seen in 2023 to date.
Email-Embedded Malware Campaign Domains: Created, Compromised, or Abused
Threat actors can choose to deliver malware via URLs embedded in emails or via a direct attachment.
Attachments are often the most straightforward and simplest delivery route for threat actors to set up, but they are much more easily detected by SEGs, as well as by trained and vigilant recipients.
Embedded URLs, on the other hand, can improve a phishing email’s chances of reaching inboxes, in a variety of ways. If a threat actor chooses to use a URL instead of a direct attachment, they have a few choices.
Each of the three categories (Abused, Compromised, Created) has different tradeoffs that affect both the threat actor’s choice and the network defenders’ ability to detect and defend. The following sections will break down some statistics, what network defenders and reporters should look for, and some of the potential reasons that threat actors might choose each option.
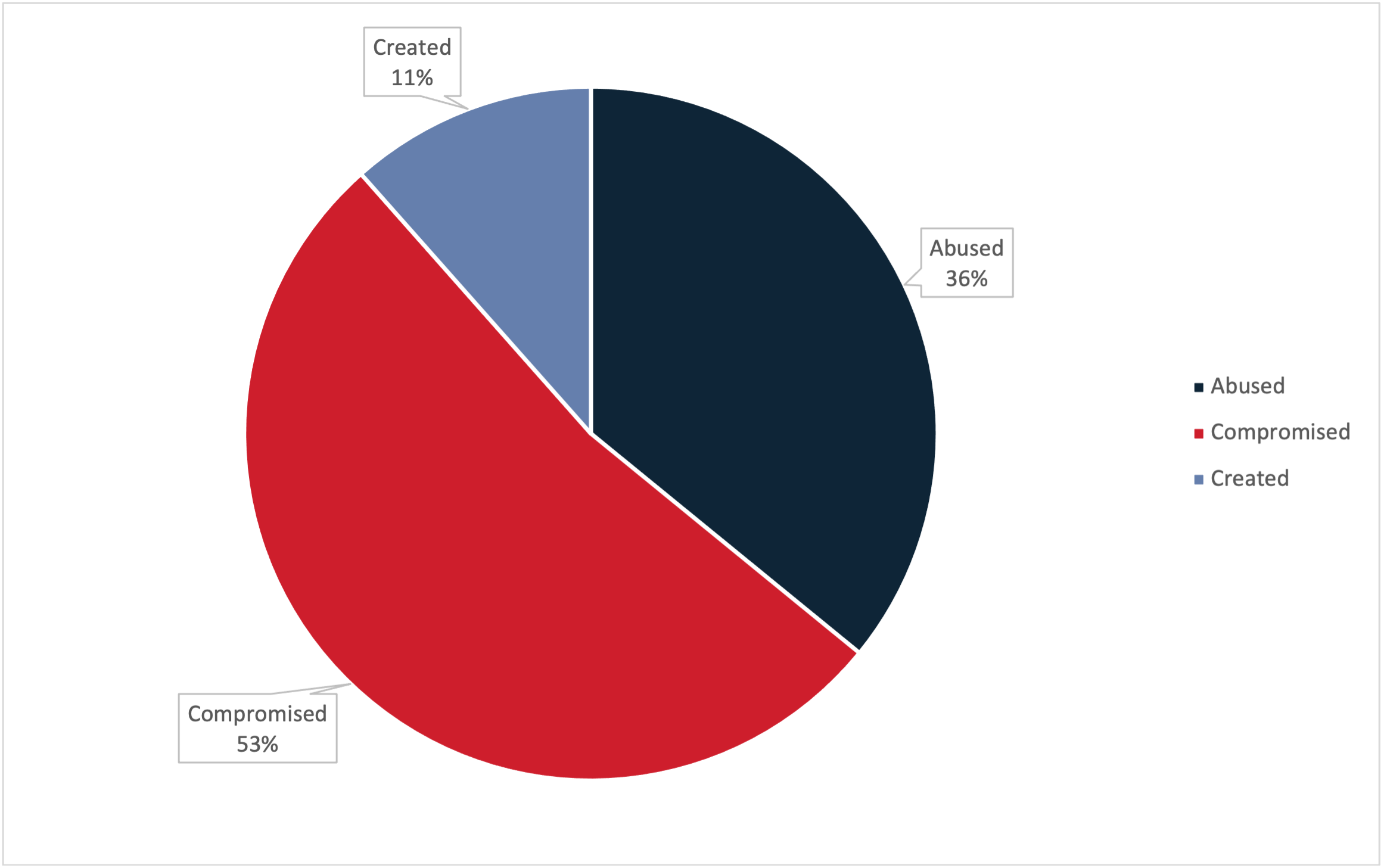
Figure 1: Percent share of domain types for the first five months of 2023.
Created Domains
Created domains are domains created by a threat actor for the express purpose of hosting or pointing to malware and are often part of more advanced campaigns. These campaigns are advanced in the sense that their narratives are well developed and consistent, the email is more carefully designed to trick recipients, and they typically deliver malware that is more complex, such as Ursnif or Gh0st RAT. Threat actors also benefit from creating domains for malware campaigns because they are typically able to keep their payloads available for much longer than with an abused domain.
One major downside for threat actors using domains that they have created for malware campaigns is that SEGs may block domains based on either the creation date or lack of a reputation score.
Accordingly, threat actors must engage in extra planning and effort in order to create domains well in advance of their use and to establish a non-malicious reputation. Even when they do, the domain may only be usable for a short time in a single campaign before it is detected and reported by the security community.
Another major downside for threat actors is that creating domains can be costly and time consuming based on the Top Level Domain (TLD). Domains at some TLDs are cheaper, or potentially free, and easier to purchase, but are less likely to make it through a SEG than a more well-known (and thus more expensive) TLD.
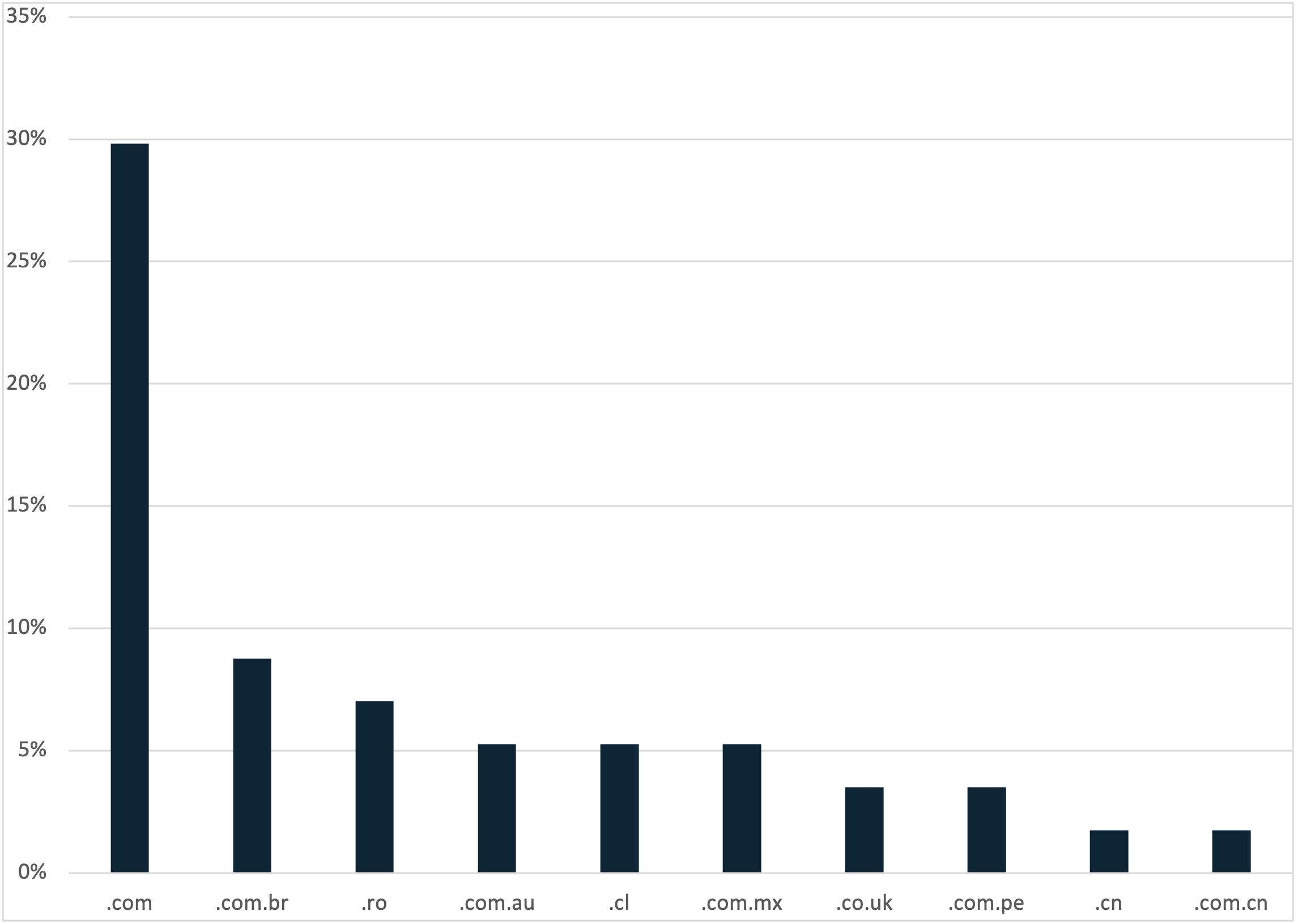
Figure 2: Percentage share of TLDs seen in threat-actor-created domains.
In short, when embedded directly in an email, domains created by threat actors are generally harder for recipients to detect, but easier for automated security solutions to detect. For these reasons, only a small percentage of email-embedded URLs contain domains created by threat actors.
Threat-actor-created domains can be more useful at later stages of the attack, after redirecting a potential victim through abused and compromised domains, but we do not detail that usage in this report.
- Time to live of malware payloads: Long
- SEG bypass: Bypasses few SEGs
- Ease of use: Easy
- Domain Cost: High
- Campaign complexity and sophistication: High complexity and sophisticated
- Percentage of campaigns of this type seen in 2023: 11%
- Most common malware family deliver by this type of domain 2023: Gh0st RAT
Example Malware Campaign: Gh0st RAT
Campaigns with embedded threat actor created domains are often among the more complex and often deliver some of the most sophisticated malware. As shown in Figure 3, the email is carefully crafted to look legitimate, using the recipient’s name and company, a created domain that roughly translates to “Cloud invoice”, and the created domain uses the .cn TLD that matches with the email language.
This campaign delivered Gh0st RAT, which is a publicly available RAT that is simple in its base form but is easy to customize and can be turned into something sophisticated.
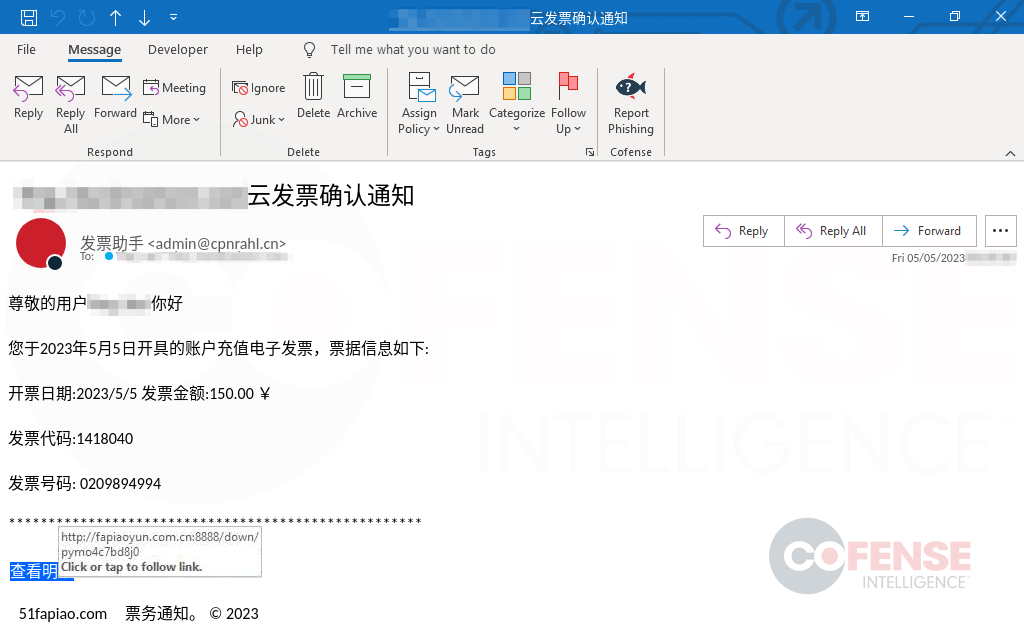
Figure 3: Phishing campaign utilizing a custom created domain to host Gh0st RAT.
Compromised Domains
Compromised domains are legitimate domains that are used in malware campaigns after having been compromised by the threat actor in some way, such as via a vulnerable web application. This does not necessarily mean that a threat actor is able to modify DNS records for the domain, but it can allow them unrestricted control of the content on that domain.
This category includes subdomains of a compromised domain, although compromised subdomains are rarely seen delivering malware.
Compromised domains are enticing to threat actors for several reasons:
- they typically have a history and reputation score that domains created by threat actors lack
- they don’t have the hosting costs associated with a threat-actor-owned domain
- they provide an extra layer of anonymity
- the owners of compromised domains are less likely to perform security scans on hosted files
However, they generally require more effort than an abused domain since the threat actor must first either compromise the domain themselves or buy access from a broker.
- Time to live of malware payloads: Moderate
- SEG bypass: Bypasses many SEGs
- Ease of use: Moderate
- Cost: Moderate
- Campaign complexity and sophistication: Moderate to High
- Percentage of campaigns of this type seen in 2023: 53%
- Most common malware family deliver by this type of domain 2023: NetSupport RAT
Example Malware Campaign: NetSupport RAT
Often, a campaign will use multiple different compromised domains, but all of them will redirect to download malware from the same final location, which is often either another compromised domain or a domain created and owned by the threat actor. This is especially true of NetSupport RAT, shown in Figure 4, which frequently has eight or more unique compromised domains that all redirect to download the malware from a single compromised domain.
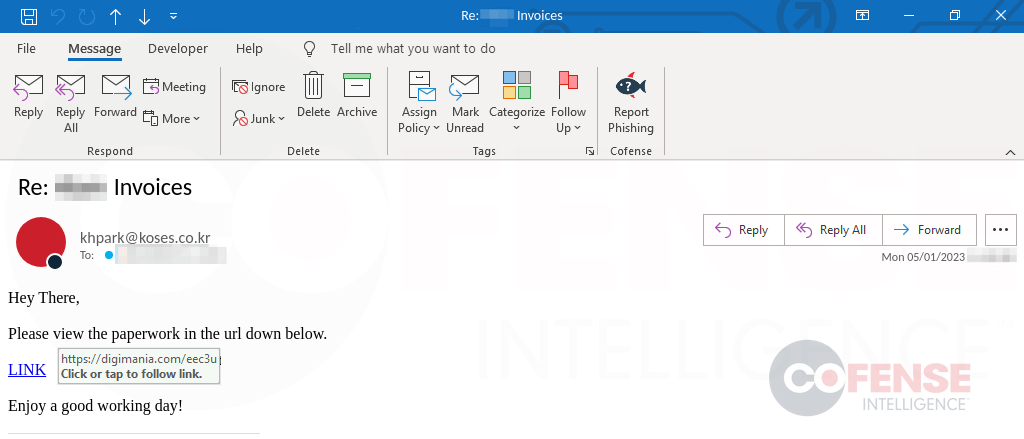
Figure 4: Phishing campaign utilizing a compromised domain to host NetSupport RAT.
Abused Domains
Embedded URLs containing abused domains in malware campaigns consist largely of file sharing sites, such as Google Docs and Microsoft OneDrive (which are used to temporarily host malware), or sites that allow redirection (which are used to direct the victim to malware). Threat actors taking advantage of file-sharing domains are often able to do so with greater ease than setting up a custom domain to host malware or purchasing or compromising an existing domain to host their malware.
Of the three categories, abused domains are most likely to be trusted by SEGs. The downside for threat actors is that most file hosting services will not keep malicious files for very long. This could be because of an inherent time limit or due to how long it takes the service to detect that the hosted file is malware.
Notably, Google domains accounted for 16% of all Abused, Compromised, and Created domains hosting malware available for download from a link embedded in an email. The complexity of emails using abused domains to host malware ranges from the simplest to some of the more complex.
That said, the majority of them are as straightforward as the one seen in Figure 5. Of all abused domains seen in 2023, Google made up 43%, Mediafire made up 14% and OneDrive made up only 8%.
- Time to live of malware payloads: Short
- SEG bypass: Bypasses many SEGs
- Ease of use: Easy to use
- Cost: Low
- Campaign complexity and sophistication: Moderate to High
- Percentage of campaigns of this type seen in 2023: 37%
- Most common malware family deliver by this type of domain 2023: Remcos RAT
Example Malware Campaign: Remcos RAT
Out of all the Google URLs seen hosting malware, over 79% were hosting Remcos RAT files. These files are typically executables over 1GB in size, contained in password protected smaller archives. By making the files artificially large the threat actors prevent Google from scanning them.
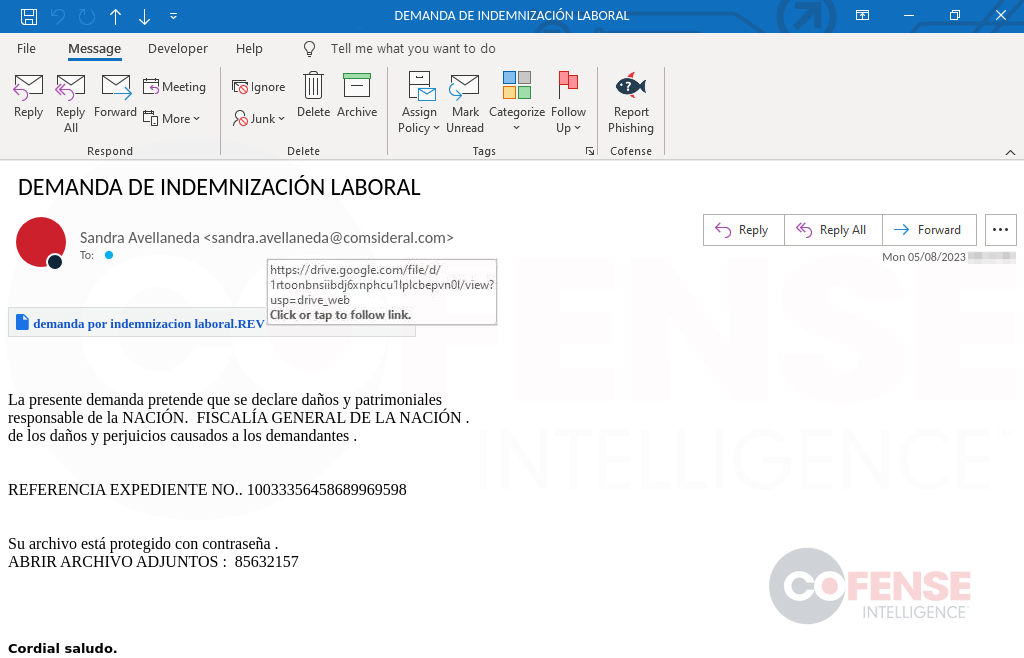
Figure 5: Phishing campaign utilizing an abused legitimate hosting provider to host Remcos RAT.
Mitigation
The first step in mitigating any email threat is to determine if a service is needed. For example, does your organization have an actual business need for allowing emails with Google Drive URLs? If not, then quarantining or blocking emails with drive[.]google[.]com in them is a perfectly valid tactic. Some SEGs allow for more granular handling of URLs and may even allow you to specify actions for domains that have been created within a certain time period.
A determination of the necessity of recently created domains and any potential exceptions should be done when this option is available. Using the creation date of a domain does not typically help with identifying compromised domains, but it can be used to avoid a large majority of the “Created” category of domains delivering malware. Finally, in terms of handling compromised domains there is no easy solution. Instead, the most reliable defense is detecting the malicious nature of the email itself rather than only focusing on the domain.
Given the fact that emails with compromised domains end up in inboxes so frequently it is clear that SEGs are unable to fully defend against them. Accordingly, the most reliable way to defend against the use of compromised domains in emails delivering malware is to have well trained employees that spot suspicious emails, provide those employees with a simple mechanism for reporting those emails, and efficiently integrate particular IOCs and intelligence derived from those human-reported emails into automated solutions.