Phish Found in Environments Protected by SEGs
Proofpoint
Symantec
TrendMicro
Microsoft ATP
Cisco IronPort
By Dylan Duncan
Cofense Intelligence has discovered a COVID-19-themed phishing campaign that delivers a new version of the Hentai OniChan ransomware. The new variant, known as King Engine, exfiltrates data and charges a significantly higher ransom than previously analyzed versions of Hentai OniChan. Previous campaigns delivering the Berserker variant of this ransomware used similar phishing emails to target the financial and energy sectors and did not exfiltrate data. Ransomware campaigns that exfiltrate data are becoming more of a common trend as they add to the pressure of paying ransom and reduce the efficacy of file backups.
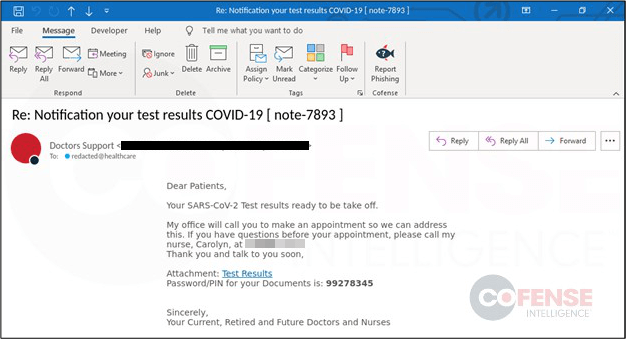
The phishing email shown in Figure 1 was found in environments protected by secure email gateways (SEGs) and currently targets the healthcare industry using response subjects allegedly returning patients’ COVID-19 test results. The spike in coronavirus cases during October has led to more testing and makes this type of phishing campaign even more threatening. This campaign uses common tactics, techniques, and procedures (TTPs) to reach end users and deliver Hentai OniChan ransomware that belongs to the Quimera ransomware family. Though, of course, the addition of data exfiltration, almost certainly to support data leaks should a targeted victim refuse to pay the ransom, is new. This addition highlights a new trend seen in ransomware that is similar to the Avaddon ransomware campaign that was first seen in June and was delivered by the Trik botnet.
Figure 1 – Phishing Email Delivering Hentai OniChan Ransomware.
Hentai OniChan Ransomware
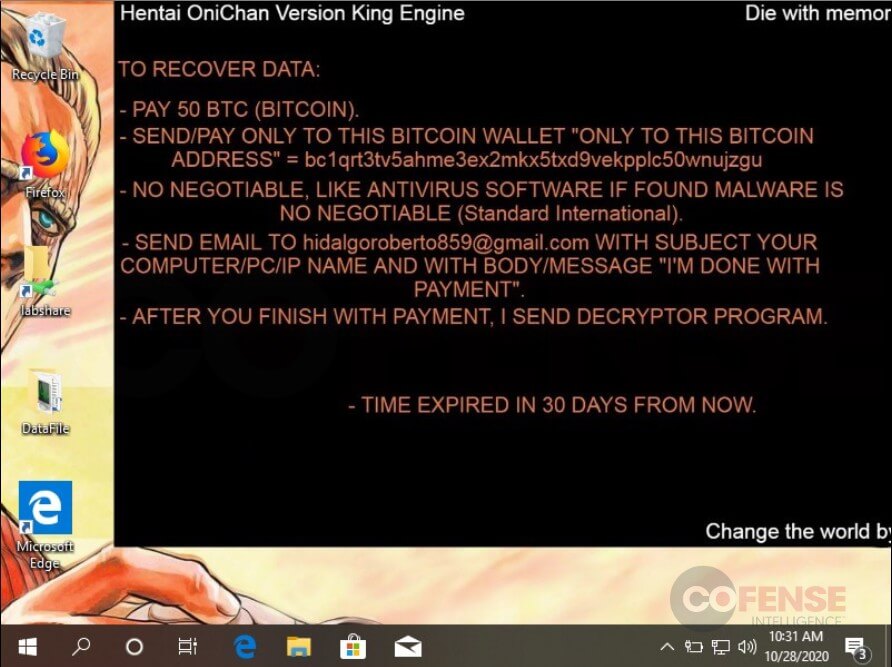
Campaigns observed by Cofense that deliver the Hentai OniChan ransomware date back to September and have been found in environments protected by Proofpoint, Symantec, TrendMicro, Microsoft ATP and Cisco IronPort. These campaigns use a common tactic to reach end users by delivering embedded URLs to download an HTML or PDF file. The downloaded files contain components to drop and run the ransomware executable encrypting victims and holding them hostage, promising to provide a decryption application upon receipt of the ransom payment. Once the target’s files are encrypted, a ransom note is provided and a background image, shown in Figure 2, is set explaining the means by which the encrypted user may pay the ransom and regain access to the encrypted data. The ransom note explains to victims affected how to pay the ransom and includes a price, Bitcoin address, timeline and contact email address.
Figure 2 – Hentai OniChon Ransom Note
Berserker v. King Engine
More ransomware operations have added to the chaos by using data exfiltration. This campaign shows Hentai OniChan has joined the trend.The early stages of the Hentai OniChan ransomware that used the Berserker version did not exfiltrate data, and encrypted files with the .HOR extension. The new strain, King Engine, as of now, has only been seen targeting the healthcare industry and exfiltrates data to an email address found within the ransomware executable. This version encrypts files with a .docm extension and charges a significantly higher ransom of 50 Bitcoin (BTC) (~$650,000 USD), whereas the previous version only charged 10 BTC (~$130,000 USD). Based on our analysis, other ransomware threat actors who have followed the data exfiltration trends often set up data leak websites to publish stolen data if the ransom is not paid. As of now, data leak websites have not been seen by Hentai OniChan operators.
Indicators of Compromise
| Active Threat Report | Date Published |
| 80619 | 2020-10-28 |
| 56658 | 2020-09-14 |