By: Max Gannon, Kahng An, Intelligence Team
Credential phishing and malware are often considered mutually exclusive; it is generally assumed that an email either delivers credential phishing or malware. While this is typically the case, several recent high-impact campaigns have combined credential phishing and malware delivery. These campaigns are noteworthy as they indicate threat actors diversifying and attempting to gather credentials in multiple ways. This method ensures that if a company has invested heavily in malware detection and response at the cost of credential phishing protection or vice versa, the threat actor will be able to gather credentials.
Key Points
- Four possible methods of delivering both credential phishing and malware are covered here.
- Some of the campaigns using this method happened in small numbers while others, such as the following “Hosted PDF With a Link to Credential Phishing or Malware” method are ongoing.
- The malware most commonly delivered by these methods is ConnectWise RAT.
- The brand most used in these campaigns is files.fm.
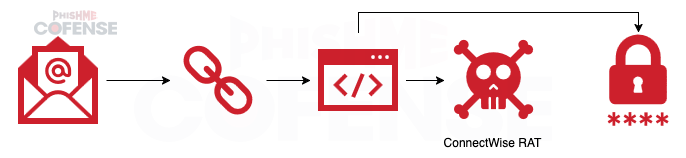
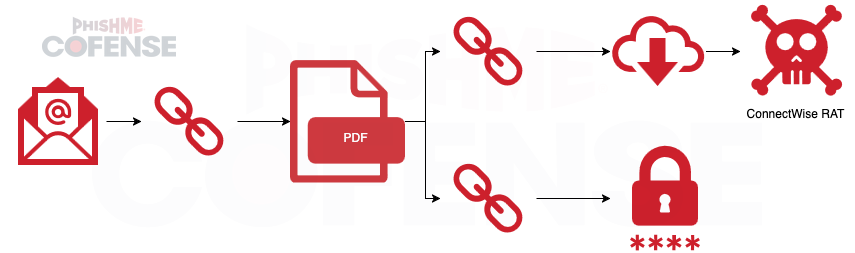
Figure 1: Infection chain of a campaign delivering malware and then encouraging victims to interact with a credential phishing page.
This campaign was part of an ongoing series of emails that were benefits-themed and spoofing the American Social Security Agency. In this campaign, victims clicked a link embedded in the email and were led to the page shown in Figure 2. If the victim followed the instructions, they would first download ConnectWise RAT and then continue to an extensive credential phishing page. What makes this campaign unusual is that the credential phishing page collected information that the malware might not have been able to, such as Social Security Number, mother’s maiden name, and the victim’s phone carrier PIN.
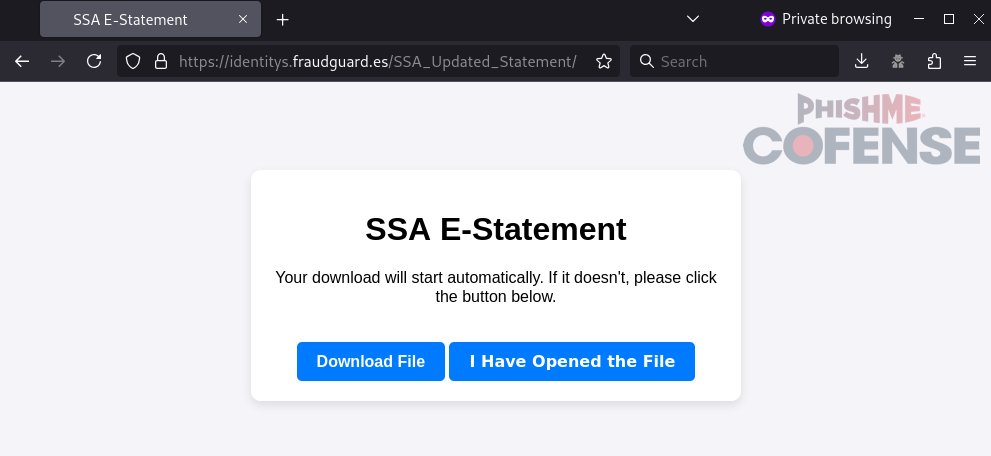
Figure 2: A page that delivers a ConnectWise RAT executable before encouraging victims to interact with a credential phishing page.
Similarly, this other campaign delivers an embedded link that leads to a PDF hosted on files.fm. The PDF contains embedded links to a credential phishing page and a download for ConnectWise RAT. This campaign is discussed in more detail here.
Figure 3: Infection chain of campaign delivering credential phishing and ConnectWise RAT.
Delivering Malware or Credential Phishing Based Off Browser User agent
Figure 4: Infection chain of a campaign delivering Android malware, credential phishing, or SimpleHelp RAT based of the browser user agent used to access the initial URL.
This campaign from July 2025 delivered an embedded link that led to two different malware payloads or a credential phishing page, depending on the browser user agent used to access the initial infection URL. When accessing the initial infection URL with a Windows user agent, the page will redirect to a Windows-specific Microsoft Store-spoofing page that will download SimpleHelp RAT.
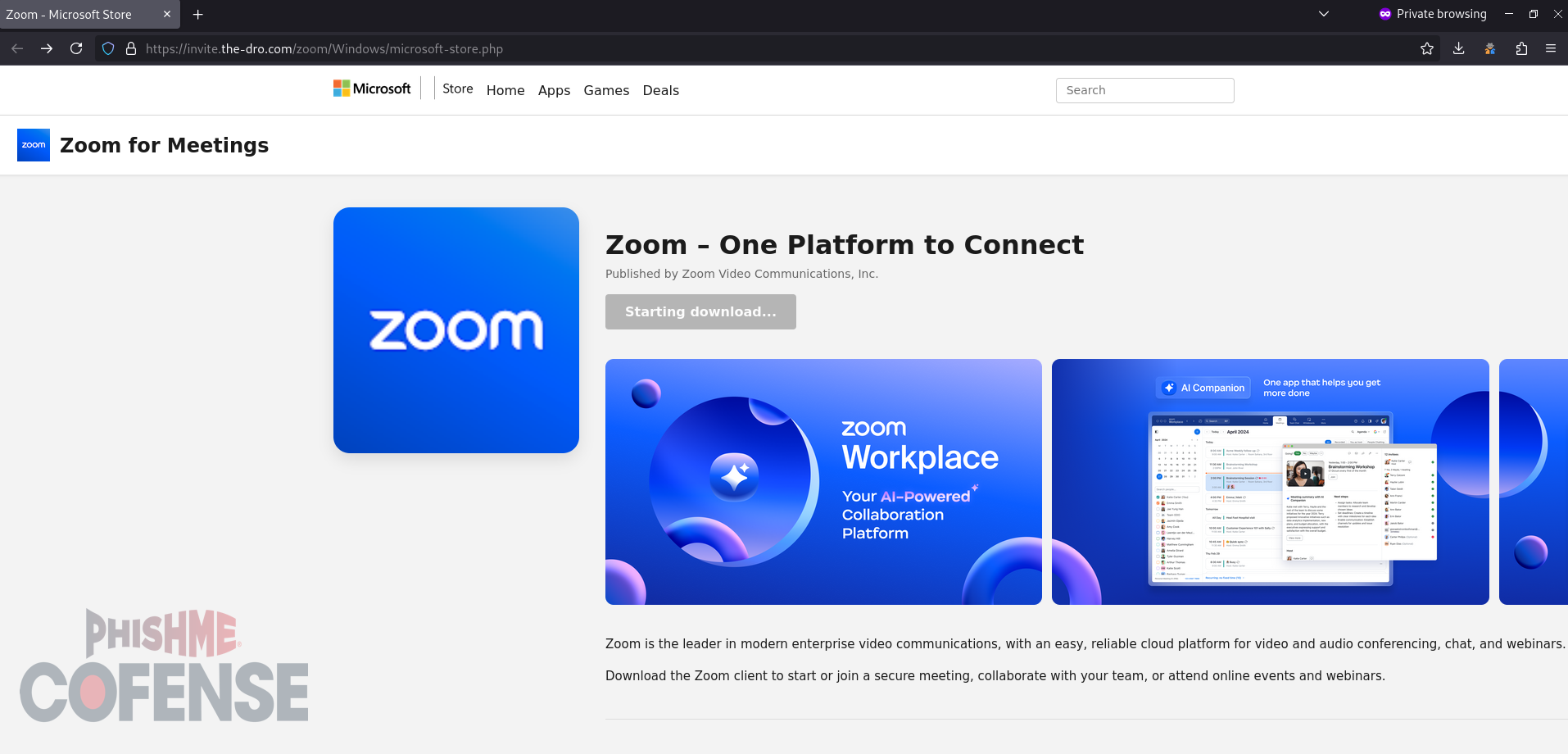
Figure 5: A Windows user agent directs to a Microsoft Store-spoofing page that downloads SimpleHelp RAT.
However, when using an Android user agent, the page will redirect to a malicious APK download that attempts to spoof the Google Play store.
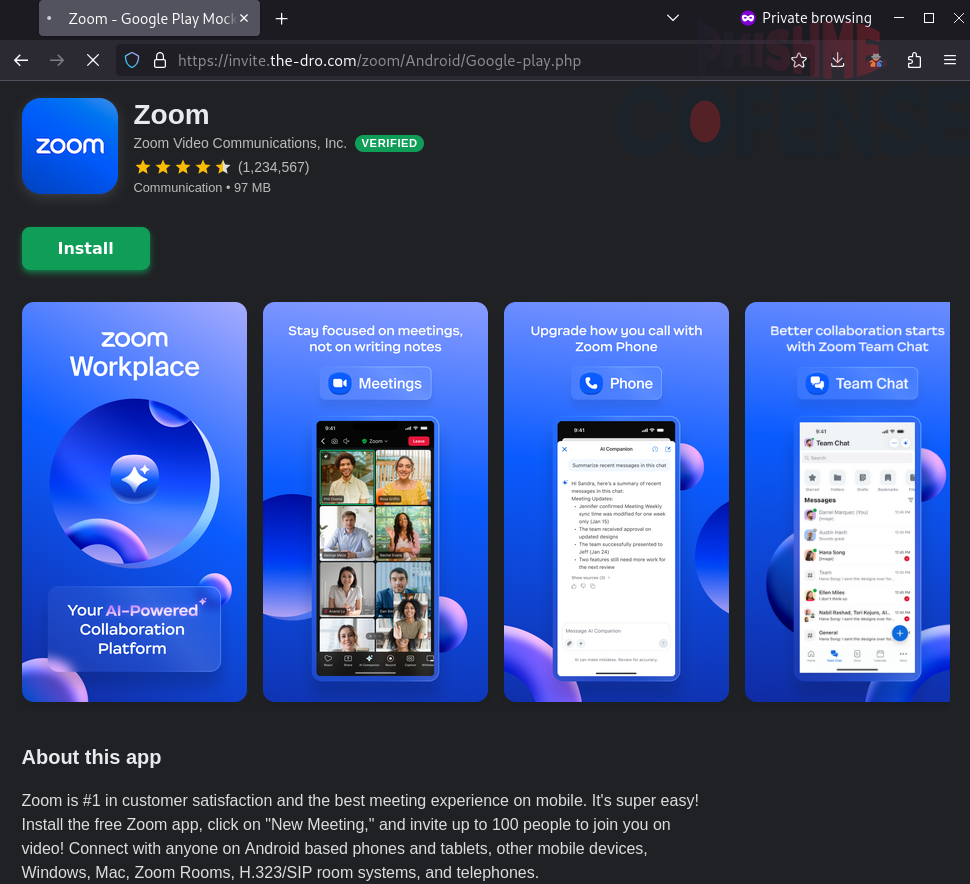
Figure 6: An Android user agent directs to a Google Play-spoofing page that downloads Android-specific malware.
When accessing the page from an iOS user agent, the page will redirect to a simple Zoom-spoofing credential phishing page.
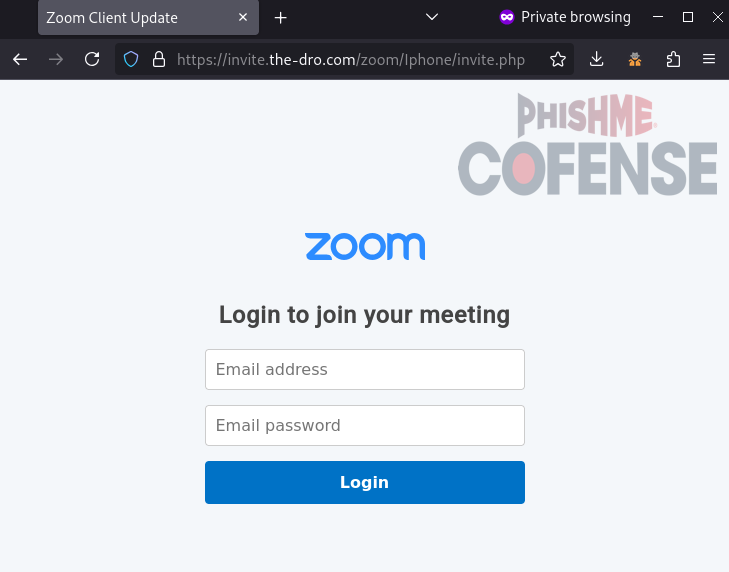
Figure 7: An iOS user agent directs to a credential phishing page.
Credential Phishing Page Delivering Malware
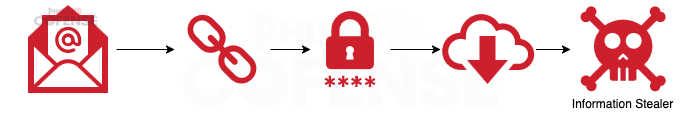
Figure 8: Infection chain of a campaign delivering credential phishing and then a customized Information Stealer.
This campaign from January 2025 delivered an embedded link that led to a credential phishing page like the one shown in Figure 9. Once a victim enters their credentials, a VBS script is downloaded. The VBS script initiates a chain of events that ends with a customized Information Stealer being run in memory. What is unique about this campaign is that the Information Stealer is not delivered until credentials are entered. Given its primary function, it is likely that the Information Stealer will also attempt to collect stored credentials, including the ones entered into the credential phishing page. This means that the threat actors are doubling up and very specifically targeting the Microsoft Office credentials of victims.
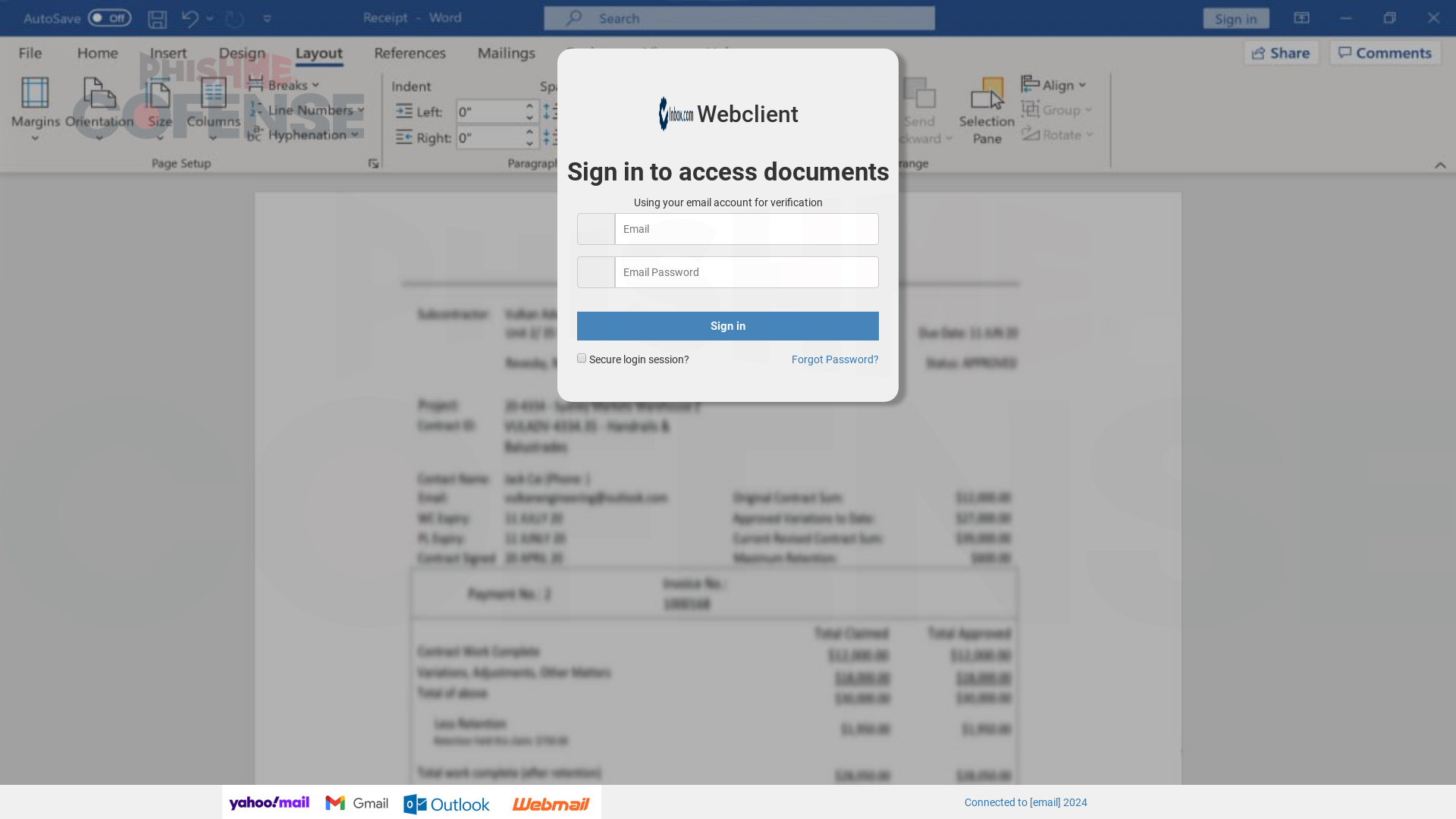
Figure 9: Credential phishing page that delivers a customized Information Stealer when data is entered.
Malware Delivering Credential Phishing
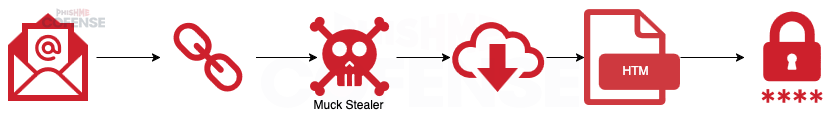
Figure 10: Infection chain of a campaign delivering Muck Stealer and then a credential phishing HTML file.
In this campaign from December 2024, the threat actor delivered a link embedded in the email that led to a malicious downloader, which then delivered Muck Stealer. When Muck Stealer was run, it launched an HTML file shown in Figure 11 that attempted to collect credentials from the victim. This HTML file serves both as an additional means of collecting information that Muck Stealer also targets, as well as a method of disguising Muck Stealer’s activities. When credentials are entered into the HTML file, they are then posted to a Google Sheet for the threat actor to access later.

Figure 11: Credential phishing HTML file delivered by Muck Stealer.
Conclusions
While credential phishing threats are typically not seen with malware threats, this report has covered four possible ways of having the two delivered in conjunction with each other. Having multiple branches provides more information than what a standard credential phishing page or Information Stealer/RAT can accomplish by itself. For example, delivering an Information Stealer or RAT along with a credential phishing page may be useful to log keystrokes for sensitive information, monitor potentially sensitive documents that may need to be referenced as a part of the credential phishing page, or provide additional reconnaissance on the infected host environment.