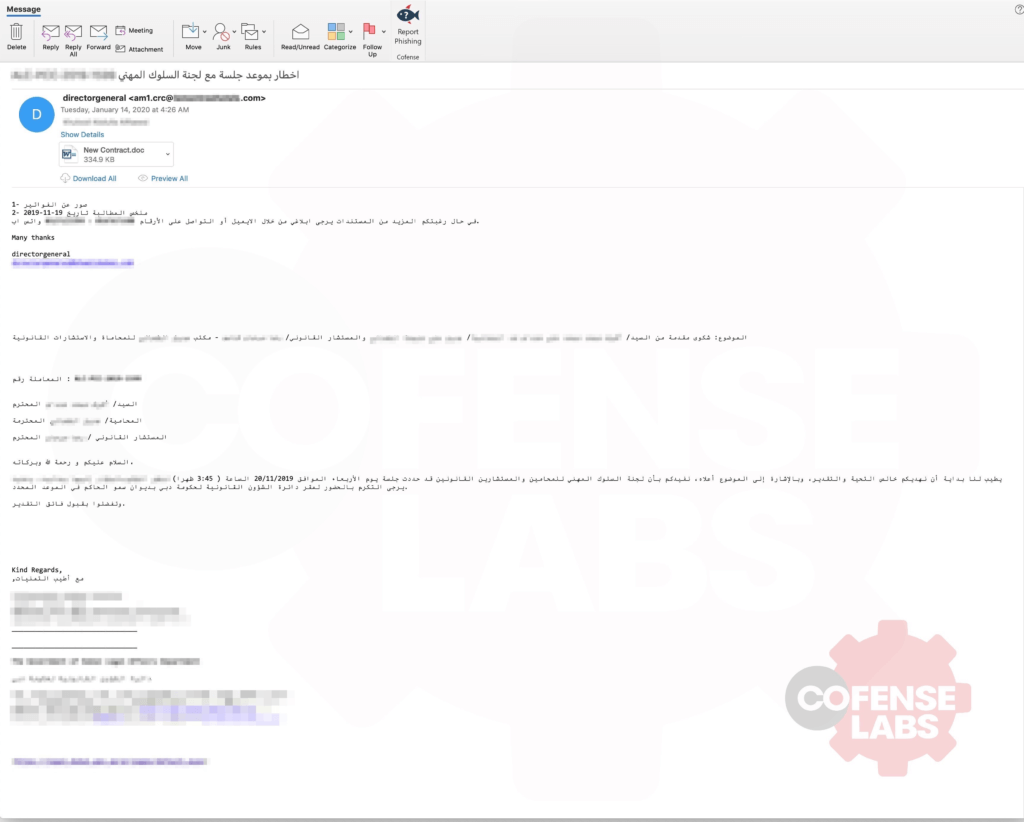
Yes… another Emotet post, but they just keep on changing things up! We were having a look around our data from the Emotet botnet and came across an interesting example of the reply-chain tactic that has become the new normal for them.
As can be seen in the example above, the majority of the email is in Arabic and is properly formed for the language. That alone is not that impressive, but taking in to account that the actors behind the Emotet botnet likely don’t speak Arabic and have automated psuedo-spearphishing in to their code, it highlights just how devastating and effective they have become. With nothing more than a single compromise, they have been able to achieve the following:
1. They have gotten a users email credentials to spread their malware.
2. They stole that users contact list and began sending emails out to them.
3. They pulled in that users most recent emails and repurposed them to further phish people known to that user with emails that appear to come from that user.
4. They now have a host to sell off to other actors for further malware deployments (TrickBot, DreamBot, Ryuk, etc…)
5. They ensure that their phishing emails not only look legitimate, but they don’t even have to worry about language, grammar and spelling issues for the most part.
The reply chain tactic was added in the beginning of 2019 and shows no signs of leaving their portfolio. Likely created to allow for a larger global presence and to increase the effectiveness of their phishing campaigns, it has become a nightmare for any organization that is compromised. We see sensitive data (think PII, PCI, HIPAA) being thrown around in the botnet daily. We have also noticed a propensity to utilize this tactic against higher value targets (Businesses, Governments, and Military targets)
We have seen a marked increase in the number of middle eastern countries being targeted as well as compromised by the botnet over the past 6 months. While this may just be a result of the continued growing effectiveness of their tactics, it is concerning to see. We have also noted a sharp escalation in targeting and compromise of entities based in Japan.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.