By Jhon Revesencio, Cofense Phishing Defense Center
Zoom is well known to be a go-to service for everything from critical business meetings to collaborative projects. But what if this tool could be exploited by threat actors to infiltrate your accounts? In our increasingly digital world, even the most reputable platforms can be weaponized for phishing attacks, putting organizations at significant risk. Understanding these threats is essential to safeguarding your business and maintaining trust in the tools we use daily.
The Cofense Phishing Defense Center (PDC) has identified a cunning credential phishing scheme targeting Microsoft accounts through legitimate Zoom Docs links. This phish often presents itself as a shared file, tricking users into clicking on it. By initiating urgency and exploiting the trust associated with well-known platforms, it skillfully manipulates individuals into compromising their credentials.
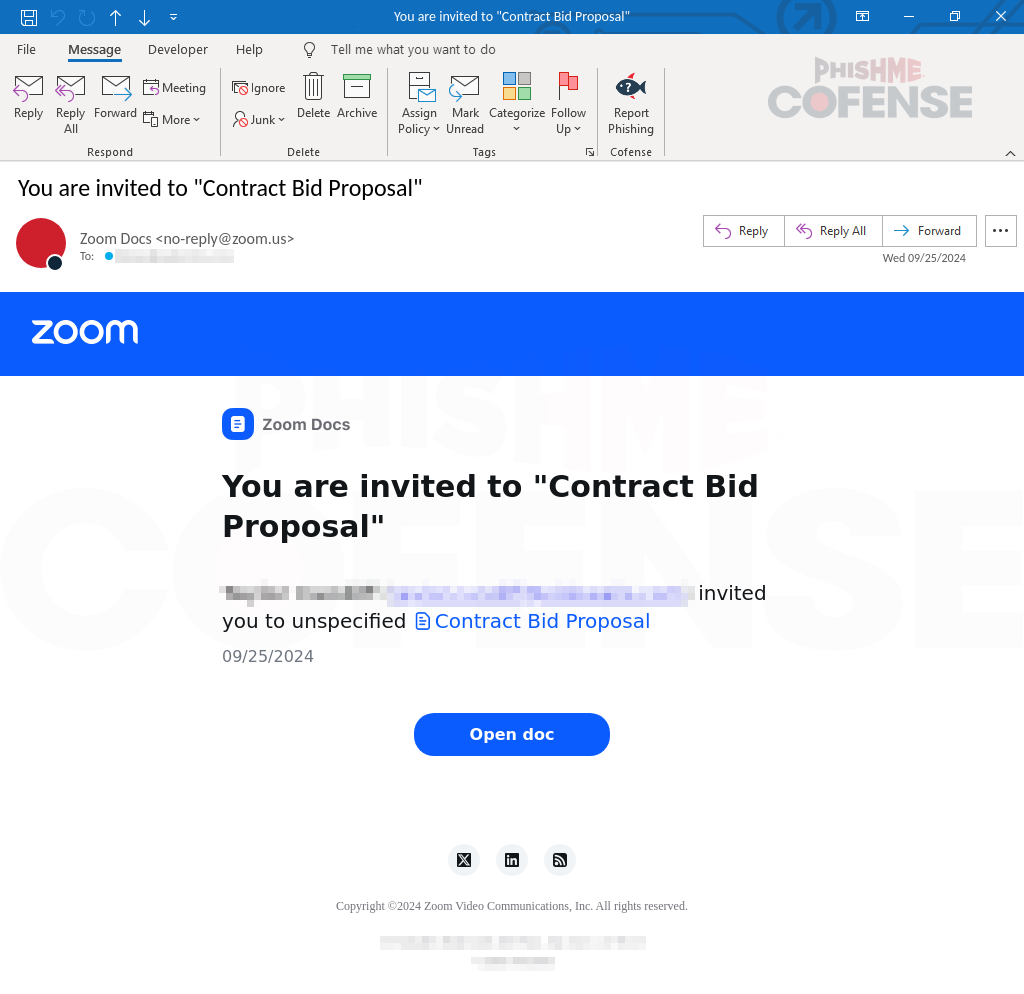
Figure 1: Email Body
In Figure 1, the email appears to originate from no-reply@zoom.us, a typical address seen with many legitimate Zoom emails. No-reply email addresses are commonly used by many organizations for a myriad of reasons. In this case, Zoom uses it for their Zoom Docs emails. This email was designed to look like an official invitation for a Contract Bid Proposal, and since Zoom Docs is used to send this email, typical identifiers for a threat are not as plainly visible. By employing this tactic, the threat actor could possibly diminish the recipient's suspicion, as the link directs them to a legitimate Zoom Docs URL.
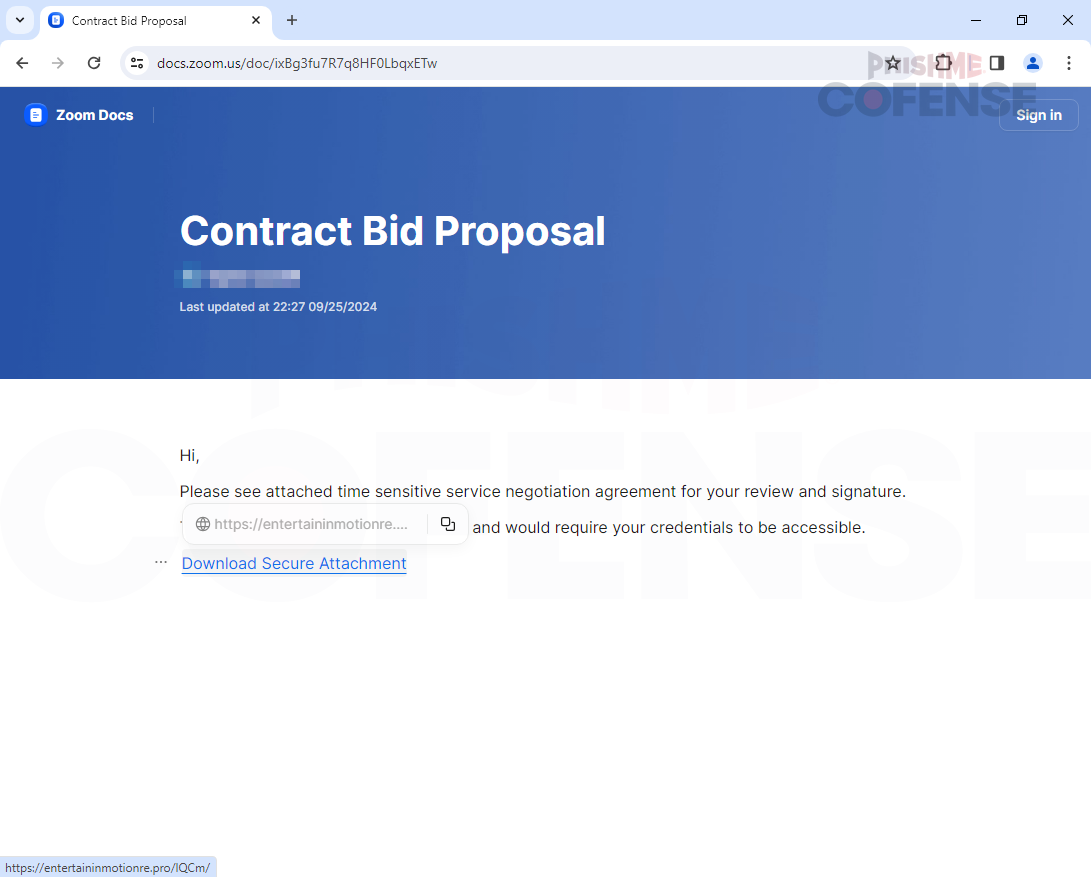
Figure 2: Zoom Docs Page
Upon clicking the “Download Secure Attachment” hyperlink, the recipient is taken to a genuine Zoom Docs page. The intent behind this page is to spark curiosity and create urgency. By presenting the proposal as a time-sensitive opportunity, this page is attempting to pressure recipients to click links or download something without thinking twice.
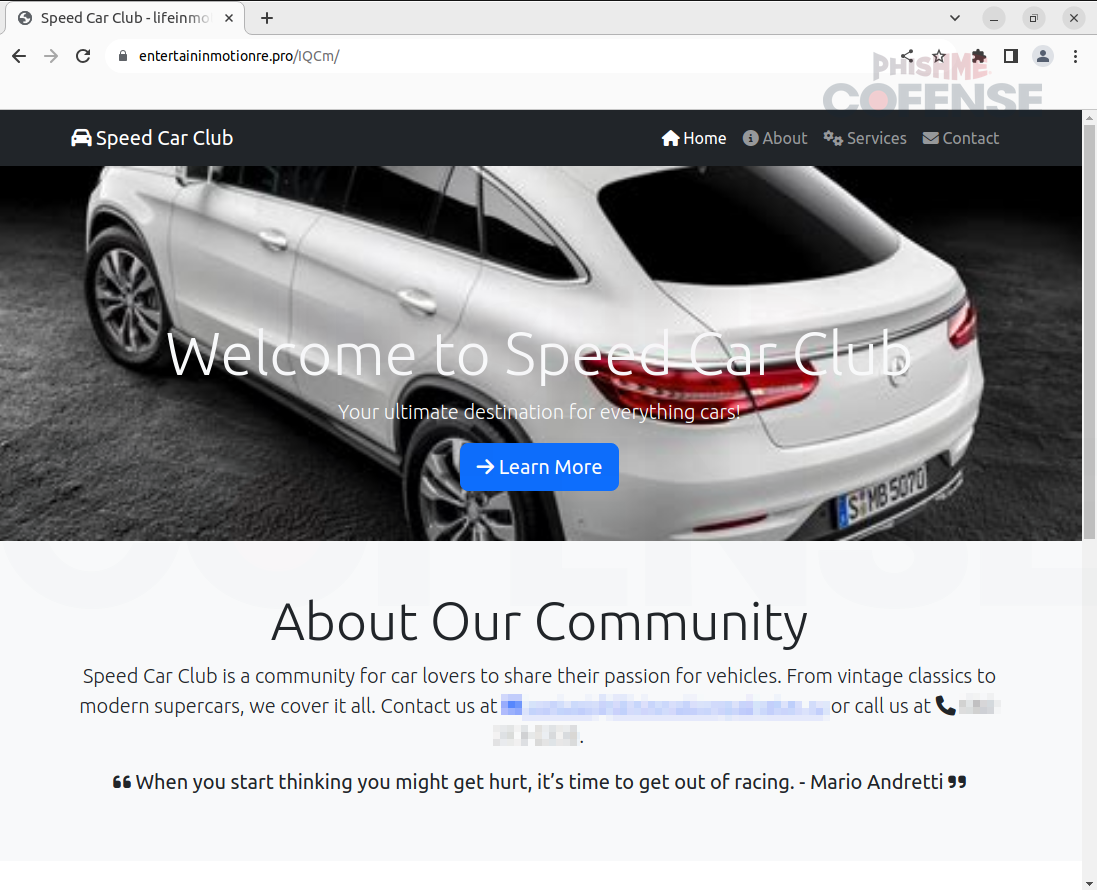
Figure 3: Non-Windows Landing Page
One of the most intriguing aspects of this phishing campaign is its tailored approach, specifically designed to ensnare Windows users while misleading others. When the user clicks the malicious link from the legitimate Zoom Docs page, they are stepping into a sneaky trap designed just for them. This phishing campaign uses an intuitive technique by verifying whether the user is operating within a Windows environment. Non-Windows users are met with the page in Figure 3 which, in fact, does not lead to the credential phishing page. This showcases just how creative the threat actor can be in their attempts to capture unsuspecting users.
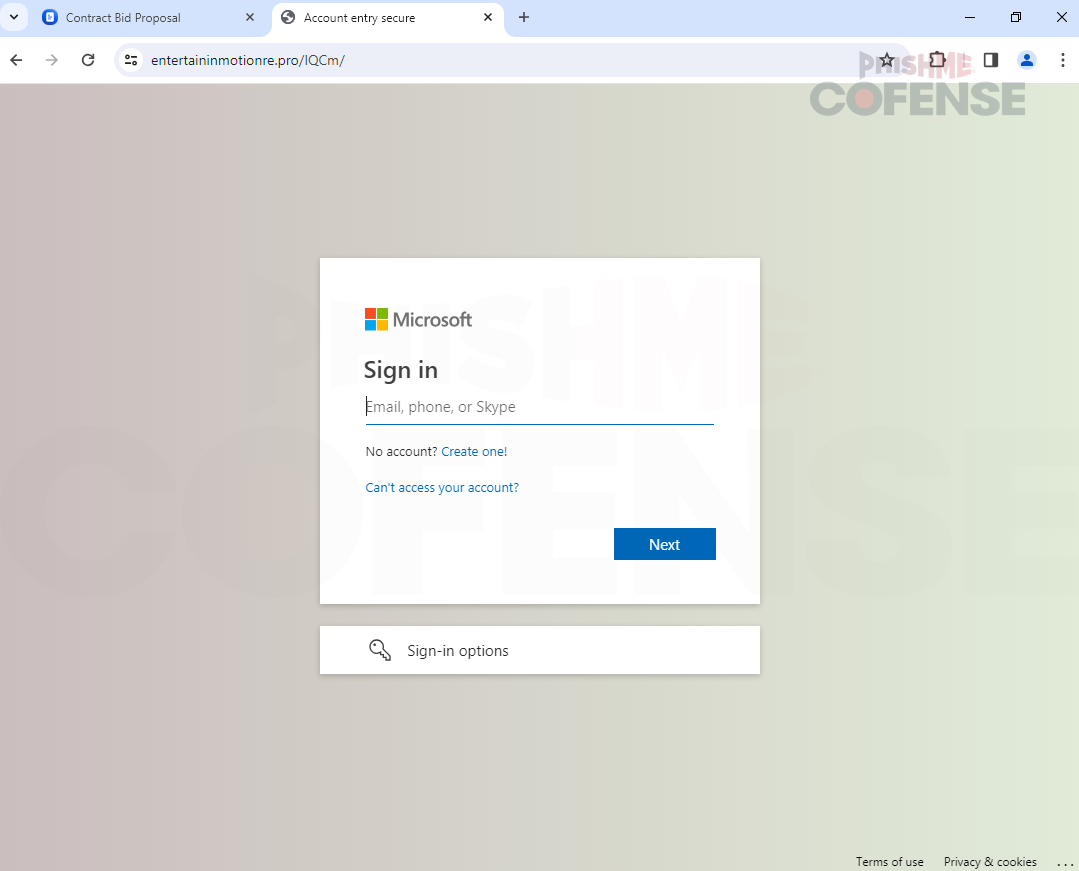
Figure 4: Phishing Page
Once the user visits the malicious link from the legitimate Zoom Docs page, if the user is operating within a Windows Environment, they are met with the fake Microsoft login page shown in Figure 4. Since this phishing campaign is designed to specifically target Windows users, it’s only natural that a threat actor would imitate such a widely used login page.
Such strategies reveal the shortcomings of automated security systems, emphasizing the critical role of human oversight in detecting and reporting suspicious activity. By leveraging solutions like Cofense Managed Phishing Threat Detection and Response (MPDR), organizations can gain comprehensive insights into real phishing threats, significantly bolstering their defenses against these evolving tactics. Cofense MPDR empowers organizations by providing a multi-layered approach to security that goes beyond traditional defenses. With real-time threat intelligence and proactive monitoring, Cofense helps organizations stay one step ahead of cybercriminals. Their Phishing Defense Center (PDC) equips enterprises with the tools to identify, respond to, and mitigate phishing attacks effectively. By fostering a culture of awareness and equipping employees with the knowledge and resources to recognize threats, Cofense ensures that organizations are not just reactive but also resilient against sophisticated phishing attempts. This comprehensive strategy significantly enhances an organization’s security posture, reducing the risk of breaches and promoting a safer digital environment. Contact us to learn more.
Indicators of Compromise | IP |
hXXps://docs[.]zoom[.]us/doc/ixBg3fu7R7q8HF0LbqxETw?from=email | 170.114.52.96 |
hXXps://entertaininmotionre[.]pro/IQCm/ | 104.21.37.223 172.67.213.235 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.