By: Clint Ilagan, Cofense Intelligence Team
In recent years, threat actors have persistently adapted their methods to bypass security defenses and exploit Google Accelerated Mobile Pages (AMP) and Google redirect methods. Google AMP is an open-source HTML framework that is primarily used to build websites for both mobile and desktop users. While Google AMP was created to enhance the performance of web content, threat actors continue to find new ways to abuse its features for malicious purposes. In this article, Cofense Intelligence will be revisiting the Google AMP Abuse Strategic Analysis from early 2023 to compare the phishing techniques previously documented, as well as exploring how threat actors have changed their approach to continue to remain effective against improved security defenses.
Key Points
- Google redirect abuse is a tactic that has been common throughout recent years. Threat actors utilize Google redirects to mask malicious content from Secure Email Gateway (SEG) detection.
- The quarterly volume of Google AMP abuse has stayed consistently high between 2023 and the time of this report.
- Threat actors have modified their approach to Google redirect abuse by utilizing different Google URL paths and TLDs to mask malicious redirects, such as using Google with different country code TLDs like .br,.fr,.sg, and many more.
- Google Maps and Google Translate are also abused for malicious redirects.
- Google links are typically allowed by SEGs due to the reputation of the domain name.
Google AMP – 2023 Trend Review and Growth
Cofense Intelligence has reviewed the previous Tactics, Techniques, and Procedures (TTPs) and the new TTPs that threat actors have used with Google redirects in 2024. The main TTPs referenced in the May to July 2023 report were CAPTCHA challenges, trusted domains, URL redirection, and image-based phishing emails, which is an HTML image that contains a clickable embedded link.
Consistent TTPs
The use of Google AMP in phishing attacks has continued to follow consistent trends from 2023 to 2024, with attackers leveraging the same effective techniques to deceive users. One of the more notable tactics that we observed is the usage of CAPTCHA challenges, which counted for 63.3% of all phishing emails utilizing a Google AMP redirect URL. The usage of CAPTCHA in phishing campaigns continues to become increasingly common, possibly due to the effectiveness that it can have in bypassing security measures implemented by SEGs and automated detection methods. Many SEGs rely on web crawlers, which are a feature that will automatically search for a link, and in some cases, any redirects to determine if the link is indeed malicious. However, CAPTCHA challenges can act as a barrier that can prevent web crawlers from reaching the phishing page due to the manual input that CAPTCHA requires.
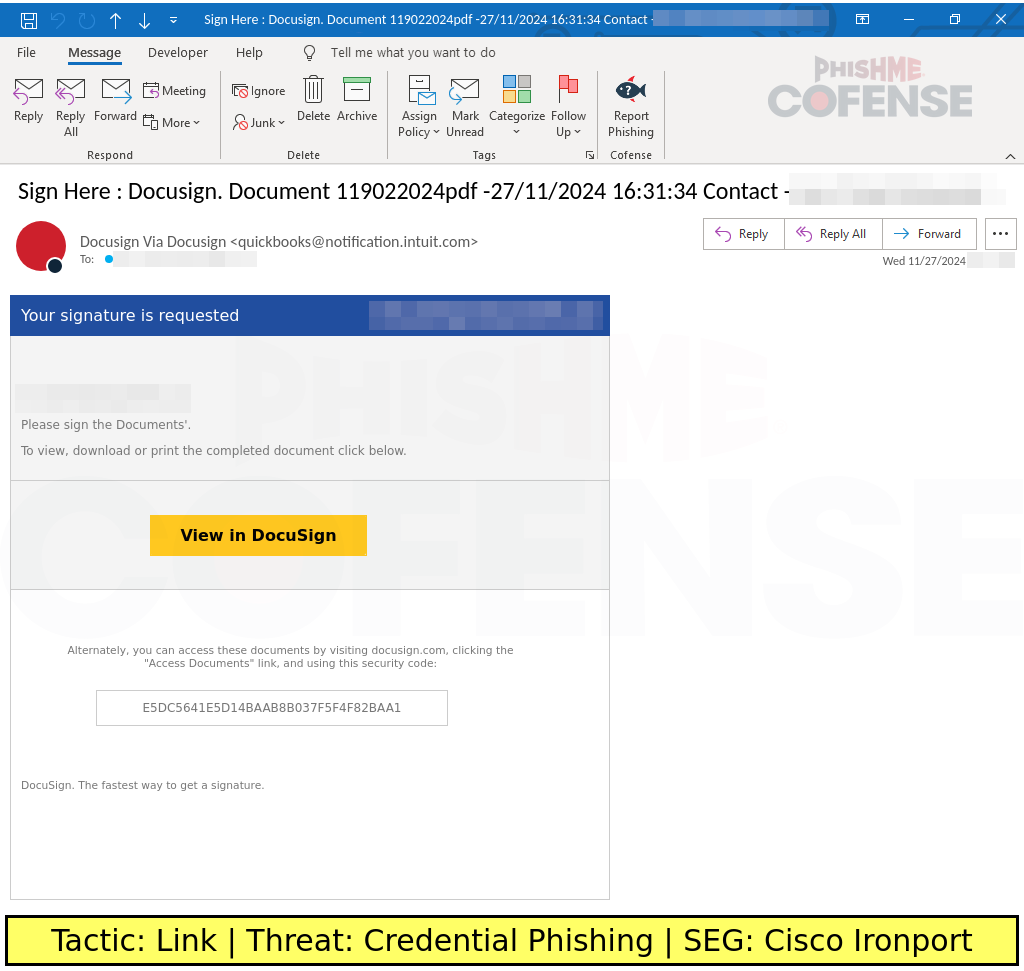
Figure 1: Docusign phishing email utilizing Google AMP within an embedded link.
New TTPs
Threat actors continue to refine their techniques to adapt to defenses by utilizing different variations of Google AMP redirects. One common trend that was observed is the use of different countries’ specific TLDs along with the Google AMP service. Instead of threat actors previously utilizing hxxps[://]www[.]google[.]com/amp/s or hxxps[://]www[.]google[.]co[.]uk/amp/s/, threat actors have begun to incorporate alternative TLDs such as France, Brazil, and Austria. Examples of the various TLDs are in Table 1.
While the base function of the tactic remains the same, the use of different TLDs can further increase the difficulty of detecting this threat.
Table 1: Top 5 Most Used Google AMP with TLD modification by Percentage Share of usage in 2024
Google AMP TLD modification | Percentage share of Google AMP usage in 2024 | Active Threat Report (ATR) Sample ID |
hxxps[://]google[.]co[.]za/amp/s/ | 19.48% | |
hxxps[://]google[.]fr/amp/s/ | 10.65% | |
hxxps[://]google[.]kz/amp/s/ | 4.94% | |
hxxps[://]google[.]co[.]nz/amp/s/ | 4.94% | |
hxxps[://]google[.]me/amp/s/ | 3.90% |
Evolution of Google Redirect Tactics in 2024
Cofense Intelligence identified several evolutions in Google redirect abuse TTPs in 2024. Threat actors have modified their Google redirect abuse techniques by adapting to SEGs with new URL structures, double Google redirects, and using other Google domains in order to make detection more difficult.
New Redirects but Same Tactic
Threat actors are now leveraging hxxps[://]google[.]com/url?sa as a redirect mechanism to disguise malicious links within legitimate Google URLs. This method still takes advantage of Google’s trusted domain to bypass SEGs. When a user clicks the Google link, they may not be taken directly to the intended website. Instead, the request is first routed through Google’s tracking system, and in some cases, the destination site may issue another redirect—potentially leading to a malicious site without the user's knowledge.
Double Google Redirect
Threat actor also uses the double Google redirect method which typically appears as hxxps[://]www[.]google[.]com/url?q=hxxps[://]google[.]com/amp/s/. This is to appear legitimate by using Google as the first domain that redirects and points to a Google AMP, thus allowing both users and SEGs to trust and open dangerous links. It also helps disguise the final destination from web crawlers that only follow the first redirect.
Google Maps and Google Translate Abuse
Another notable redirect is the use of Google Maps and Google Translate subdomains. The translate[.]google[.]al is an Albanian subdomain of Google Translate that threat actors can use alongside the Google AMP redirect to create a dual layer approach to increase the chances of bypassing SEGs. Google Translate is also used to redirect credential phishing pages or view phishing sites without visiting them directly.
Cofense Intelligence has observed that threat actors have also utilized several new Google services to change their techniques.
- New redirect paths but same result:
- hxxps[://]www.google[.]com/url?sa=t&source=web&rct=j&opi=89978449&url=hxxps[://]lcredubaiproperty[.]com/&ved=
- Google Maps redirect abuse:
- hxxps[://]maps[.]google[.]com/url?q=hxxps[://]google[.]com/amp/s/booking[.]reservation-approve-53465342.cfd/p/192401157
- Google Translate redirect abuse:
- hxxps[://]translate[.]google[.]com[.]sg/translate?hl=&sl=auto&tl=ja&u=hancentc[.]github[.]io/ethanc
- Google Translate malicious page hosting:
- hxxps[://]projectile186-sofug-com[.]translate[.]goog/?_x_tr_sl=auto&_x_tr_tl=ml&_x_tr_hl=my
All above methods mask the URL’s true destination, making it easier for attackers to slip phishing links into emails without triggering security flags. Examples of methods 1, 2, and 3 can be found in ThreatHQ using the tag “open_redirect”. The 4th technique of using Google Translate to render a malicious page without directly visiting the site has been used both for redirect purposes and to directly host credential phishing content. When used for redirect purposes, the threat actors simply embed “window.location.href” with the redirect URL into the HTML of the translated page. When used for hosting credential phishing content, the page is rendered in the browser, as seen in Figure 2.
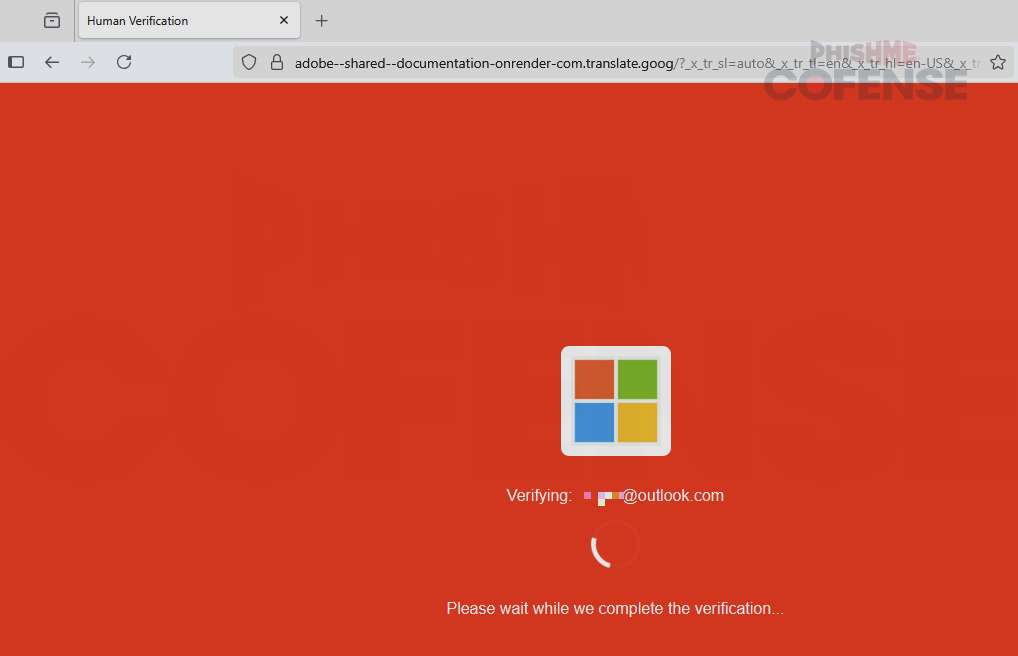
Figure 2: A phishing page hosted by Google Translate.
Quarterly Review of “New” Google Redirect URLs and “Old” Google Redirect URLs
Cofense Intelligence has observed the use of Google redirect URLs outside of Google AMP being abused frequently in 2024. Figure 3 shows the comparison between the volume of phishing used in Google AMP and the New Google Redirect tactic for 2024. During the initial quarter, Google AMP remains more prominent than the New Google Redirect tactic, likely due to its introduction or an early testing phase. In the following quarters, a transition from Google AMP to the New Google Redirect tactic is evident, suggesting the threat actor is evolving their tactics. This change may reflect efforts to bypass Secure Email Gateways (SEGs) targeting Google AMP and to enhance the effectiveness of their phishing campaigns.
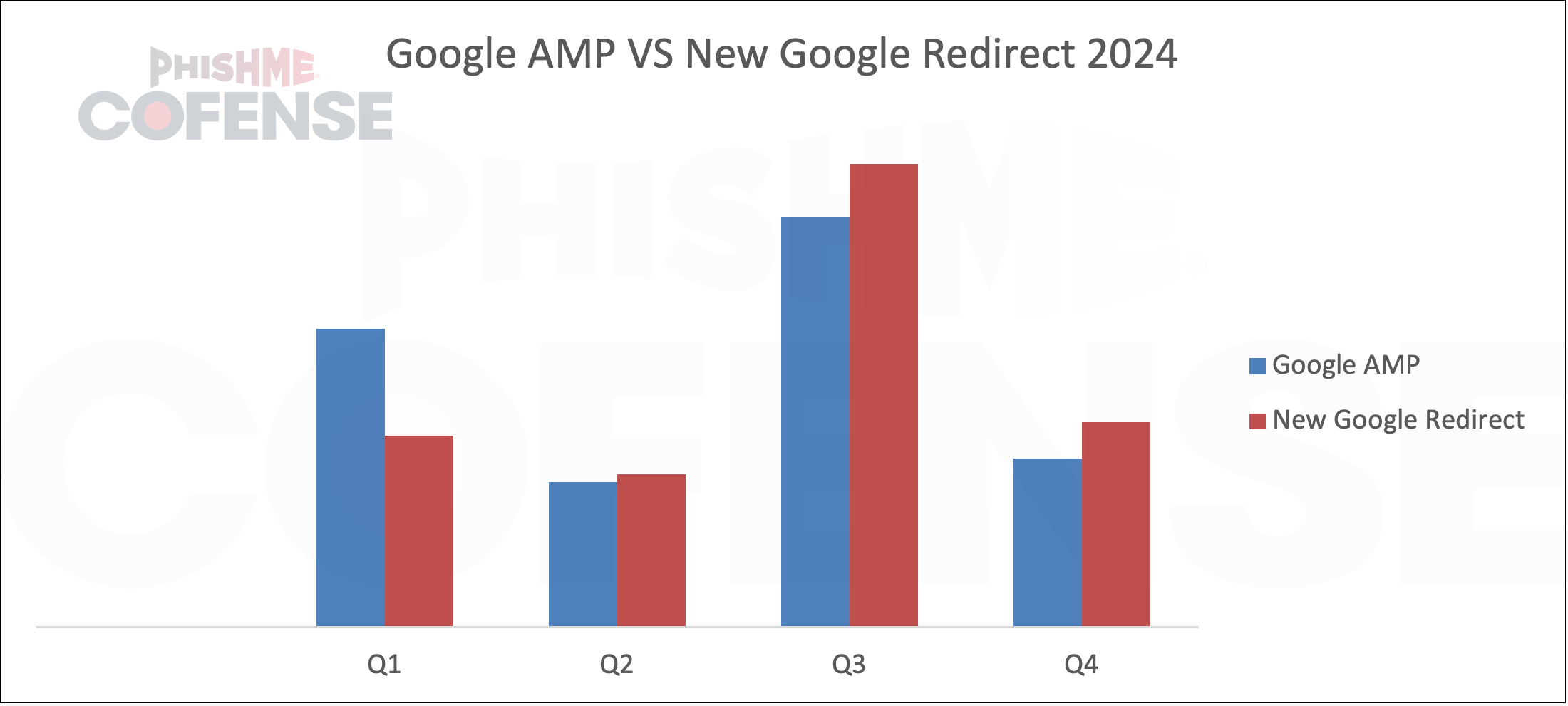
Figure 3: Google AMP vs New Google redirect total phishing volume distribution per quarter in 2024.
Mitigation
Google redirect abuse is a successful and effective tactic that threat actors use to bypass SEGs and other security measures. By masking malicious URLs behind a Google redirect link, attackers can increase the chances of evading detection from SEGs, which may struggle to identify the threat behind the redirects. Additionally, by utilizing Google’s trusted domains, attackers deceive users into believing that the site is legitimate.
To further enhance the security defense of your organization post-delivery, we recommend the implementation of Security Awareness Training (SAT) that specifically addresses Google redirect abuse. To increase the effectiveness of this training, organizations should incorporate the different tactics that threat actors use with Google redirect emails. This includes CAPTCHA challenges, redirect TLD variation, and the use of trusted domains to make the phishing attempts appear more legitimate. By exposing the user to real world attack techniques, organizations can improve their ability to identify and respond to sophisticated phishing attempts. This proactive education and awareness can play a major role in reducing the success rate of these attacks and adds a human element to the defense against threat actors’ evolving TTPs. Another step that can be taken is to adjust the SEG web crawlers to follow all redirects rather than stopping after the first one. Although this is not available for all SEGs, some SEGs should provide this capability.