By: Nathaniel Raymond
In 2022, the Cofense Phishing Defense Center (PDC) detected phishing campaigns that used LinkedIn links called Smart Links or “slink” to bypass security email gateway or SEG to deliver credential phishing, which was covered previously in the smart links LinkedIn blog. Smart links are links utilized by a LinkedIn team or business account connected to LinkedIn Sales Navigator services that provide content and track engagement metrics. A year later, in late July into August, a resurgence of Smart Links was identified in a sizable credential phishing campaign targeting Microsoft Office credentials creeping into inboxes once again. While Smart Links in phishing campaigns are nothing new, Cofense identified an anomaly of over 800 emails of various subject themes, such as financial, document, security, and general notification lures, reaching users’ inboxes across multiple industries containing over 80 unique LinkedIn Smart Links. These links can come from newly created or previously compromised LinkedIn business accounts.
Key points:
- LinkedIn Smart Links are connected to LinkedIn’s Sales Navigator services for marketing and tracking solutions for team and business accounts. This may suggest that these accounts are either newly created or previously compromised LinkedIn business accounts, allowing threat actors insight into the phishing campaign with its tracking capabilities.
- LinkedIn is a trusted brand with a trusted domain name that can allow malicious actors to take advantage of when sending emails with Smart Links embedded into them. This will enable emails to bypass SEGs and other security suites.
- Cofense identified large-scale phishing attacks using LinkedIn Smart Links as early as 2021.
- In 2023, Cofense Intelligence received and identified a phishing campaign comprising over 800 emails and 80 unique Smart Links in late July into August, targeting various industries.
What are LinkedIn Smart Links?
A LinkedIn Smart Link is used by LinkedIn business accounts to deliver content and track user content engagements through LinkedIn’s Sales Navigator services. The Smart Link uses the LinkedIn domain followed by a “code” parameter with an eight-alphanumeric character ID that may contain underscores and dashes. However, malicious Smart Links can include other parts of information, such as obfuscated victim emails, as seen in Figure 1.
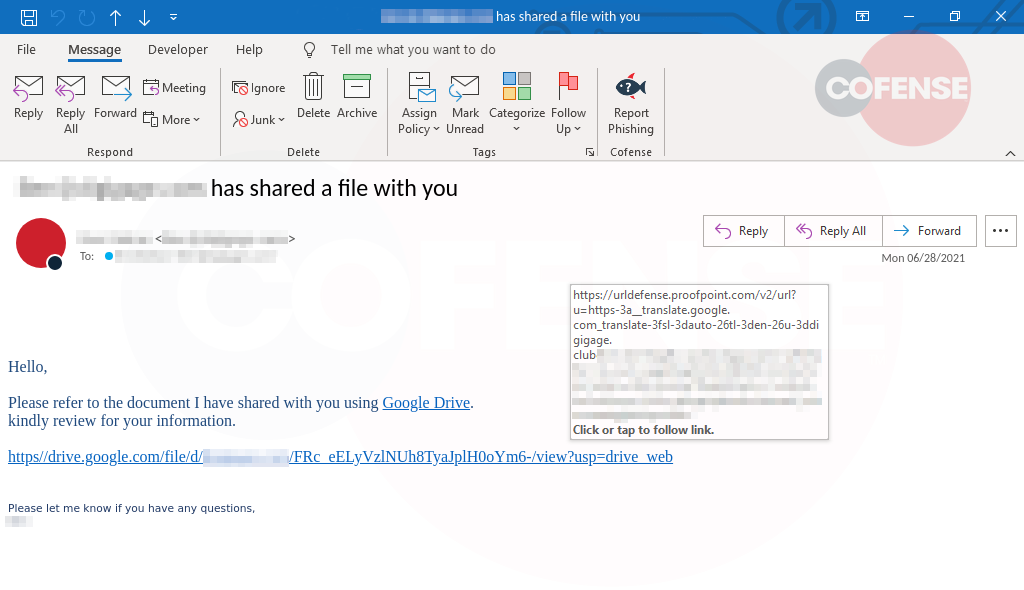
Figure 1: Malicious Smart Link Structure.
The designated phishing kit will read the victim’s email attached to the Smart Link to autofill the malicious form to add to the illusion of legitimacy that the victim has landed at the legitimate Microsoft sign-in. However, a Smart Link will still lead to a credential phishing page without the victim's email in the URL.
The LinkedIn Smart Links Campaign
Using LinkedIn Smart Links is not a new tactic. However, Cofense does not consistently see many emails that use Smart Links. Despite the scarcity of malicious emails, Smart Links have proven themselves to bypass SEGs and other email security suites due to the link using a trusted domain. The emails use generic subject lines that fit the themes of financial, human resources, documents, security, and general notifications. Figure 2 is an example of a malicious email.
Figure 2: Email Example Using HR and Payroll Themes
Upon clicking the link in the email, the user will be sent directly or through a series of redirects to the phish. Once at the phish, the user will be instructed to log in using their Microsoft Office credentials. The phishing pages are made to appear as generic and legitimate as possible, as shown in Figure 3, to encompass the large industry target spread. Notice in Figure 3 that an example email address is used in the URL address bar, which auto-fills the form upon landing on the phishing landing page.

Figure 3: Phishing Page Example
Who Were Targeted?
Looking deeper into the data, Cofense witnessed that this campaign targeted several industries. However, the Finance and Manufacturing sectors were the most targeted, as shown in Figure 4. Despite Finance and Manufacturing having higher volumes, it can be concluded that this campaign was not a direct attack on any one business or sector but a blanket attack to collect as many credentials as possible using LinkedIn business accounts and Smart Links to carry out the attack.
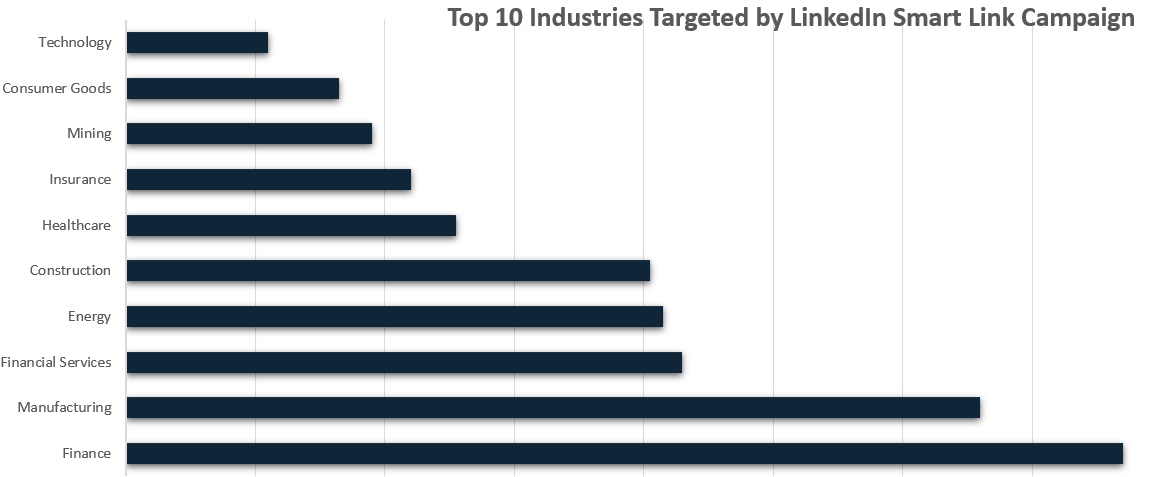
Figure 4: Top 10 Industries Targeted by LinkedIn Smart Links
Conclusion
While LinkedIn Smart Links have been used in phishing attacks over the years, this campaign was an anomaly of over 800 emails sending over 80 unique Smart Links using an unknown number of created or previously compromised LinkedIn business accounts. This campaign has been seen to blanket across industries, with the Finance sector being the number one target, harvesting mainly Microsoft Office credentials. Malicious actors abuse the Smart Links to bypass SEGs to reach the inbox of their intended victim due to the inherent trust of the link's domain, LinkedIn.com. While it's important to use email security suites, it is also essential for employees to constantly be up to date on their training to combat any phishing campaign. Employees must be taught not to click links from emails that seem suspicious or unexpected.