Over the US Thanksgiving holiday, PhishMe Intelligence™ observed a recent ransomware campaign, Scarab, that shares some similarities in behavior and distribution with Locky. In this campaign, Scarab was delivered by the Necurs botnet, which made headlines due to its distribution of Locky, which was one of the most prolific ransomware families of 2016 and 2017. Like Locky, Scarab can encrypt targets via both online and offline encryption.
Scarab differs from Locky in two notable ways. First, Scarab does not present a ransom amount with its encryption message, instead it provides instructions to the victims for how to negotiate with the operators. Second, Scarab reports newly infected machines via a service that collects click statistics on opened or viewed artifacts, as opposed to using command and control resources as Locky does.
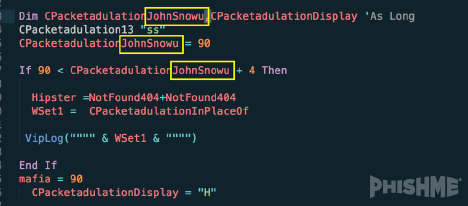
The Scarab ransomware is deployed when the victim executes an initial VBScript application, directing victim machines to payload websites from which Scarab is downloaded and run. This VBScript shares similarities to the delivery mechanism of Locky with its references to Game of Thrones in the source code as shown in figure 1. This content indicates that Scarab threat actors may also be responsible for distributing Locky.
Figure 1 – VBScript referencing Game of Thrones character, Jon Snow
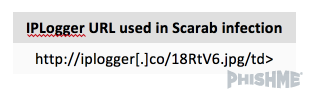
After the Scarab payload file is retrieved and executed on the victim’s machine, the malware attempts to connect to a website used to report and log IP addresses and machine information. Scarab leverages a feature of the IP Logger service, called “Invisible IPLogger”, to embed an invisible image that acts as a counter to track and log IP addresses that access the malicious content. Figure 2 shows the website used in the Scarab ransomware analysis, as detailed in Threat ID 10370. The malware attempts to establish a connection to the location. However, regardless of whether the victim’s machine is online or offline, Scarab encrypts each file on the machine with a .scarab file extension. Then, it presents the victim with a ransom note detailing the instructions for engaging in ransom negotiations.
Figure 2 – IPLogger URL to report IP address of the victim’s machine to the threat actors
Because of Scarab’s ability to encrypt offline, it is possible to become infected without compromising the victim’s geographical location. Once the related artifact is accessed, for example by opening a phishing email or executing a binary, the IPLogger provides the victim’s location information to the malware operators.
Unlike Locky, Scarab does not specify a Bitcoin rate for ransom payment. Instead, threat actors require victims to act quickly by emailing them at the provided email address in the ransom note to negotiate payment. While different than Locky, we have seen this tactic used in other ransomware campaigns, such as GlobeImposter, BTCWare Aleta, and BTCWare Gryphon.
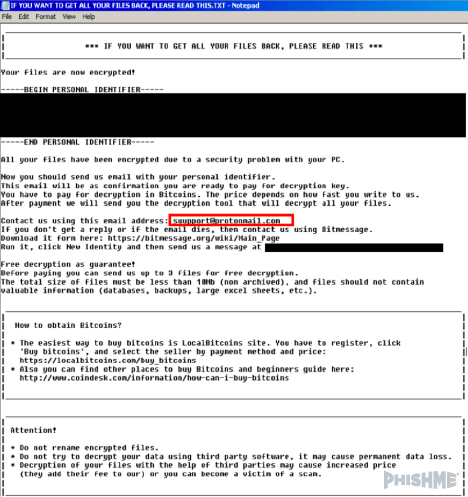
PhishMe Intelligence assesses that ransomware operators may be shifting to this negotiation tactic due to the fluctuations in Bitcoin value. With the generally rising rate of Bitcoin, it becomes increasingly difficult for victims to pay the ransom amount and for threat actors to collect payment. As of December 4, 2017 the current rate of 1 BTC is roughly equivalent to $11,200 USD. While some victims will pay whatever they can to retrieve any and all sensitive files, some individuals simply cannot afford the ransom. As seen in figure 3, below, Scarab can bypass this by allowing victims to contact the email address included in the ransom note to negotiate payment. We assess this technique will benefit ransomware threat actors because if the victim can negotiate the payment amount, they may be more likely to pay.
Figure 3 – Scarab Ransom note detailing the instructions to pay the ransom
Over the last two years, PhishMe Intelligence has documented how threat actors have modified and improved their tactics, techniques, and procedures (TTPs). The ability to encrypt machines offline and the establishment of a negotiation platform for ransom payments highlights the ongoing evolution of ransomware.
Enterprises must develop a strategy for countering the great range of risks posed to their infrastructure by ransomware. All data should be inventoried and backed up so if an enterprise falls victim to ransomware, they will have an increased chance of recovering all of their data safely. Furthermore, enterprise network defenders must stay up to date on evolving ransomware campaigns and their TTPs. Security professionals must also enact comprehensive security mechanisms to combat the most reliable and flexible attack methods, like phishing emails, by consistently educating their users and by providing a way to report phishing emails. By empowering their organization’s users to identify and report ransomware and other phishing emails, network defenders gain insight into the latest attempts to attack their organization. This approach provides valuable intelligence that can then be compared with external intelligence reporting to understand the risks posed by an attack and how to mitigate it.
Don’t ever miss another threat – sign up for PhishMe® Threat Alerts today and receive updates on new and emerging phishing and malware threats, completely free.