Author: Kian Buckley Maher
SEG Bypassed: Microsoft
The Cofense Phishing Defense Center (PDC) has noted an increase in the number of malicious emails utilising this attack vector. In an attempt to bypass traditional file and text detection software, QR codes provide threat actors with a different tactic to encode malicious URLs.
While it is possible to open QR codes on a computer, they are most conveniently accessed using a smart phone or tablet with its inbuilt camera. As a user’s personal mobile device, they commonly lack the protection from network and endpoint solutions which would commonly prevent access to malicious URLs and create alerts for security teams to investigate. With most of the attack occurring outside of the protection bubble created by a company, it is more difficult to gather evidence of the attack and tracking any subsequent actions taken by the user.
Viewed through a phone screen these webpages, which endeavour to impersonate legitimate websites, are less likely to be spotted. Their imperfections can easily be attributed to the buggy nature of mobile browsers and their constant struggle displaying webpages efficiently, especially when a page is primarily accessed through a desktop browser.
Initial Email
The recipients of these campaigns will receive an email from the threat actor, it is light on critical information, includes a slight sense urgency as to its content, and lacks any tradition indicators of compromise like an attachment or link. This may invoke a desire from the user to investigate further. In this context the QR code is placed with prominence to draw immediate attention and lure the user to quickly scan it with their smartphone.
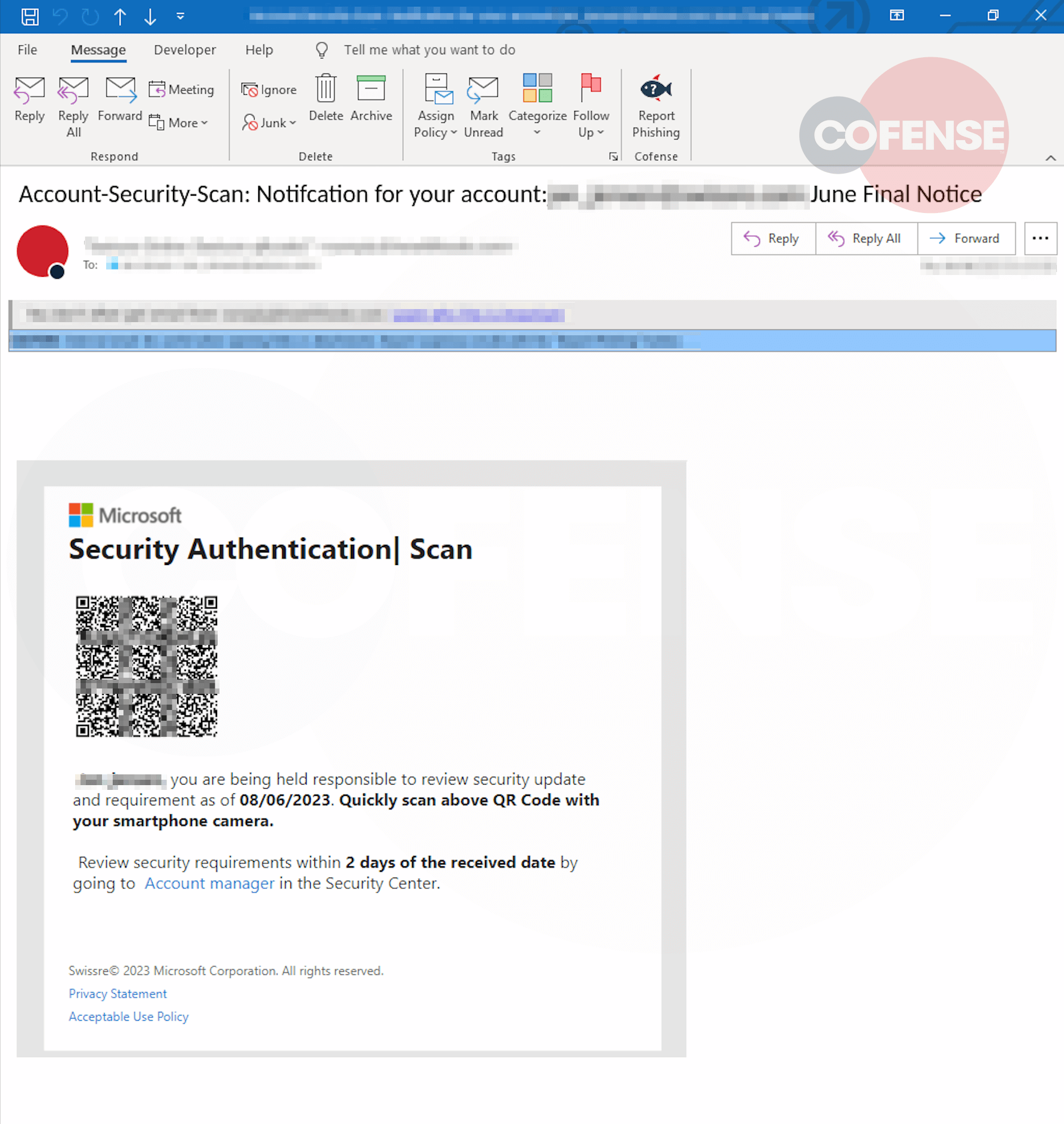
Figure 1 – QR Email
Once scanned with a QR code application on a smart phone the URL will be decoded. Upon agreeing to navigate further the user is presented with a captcha check, utilized in this manner it gives the impression of the final landing page itself being legitimate.
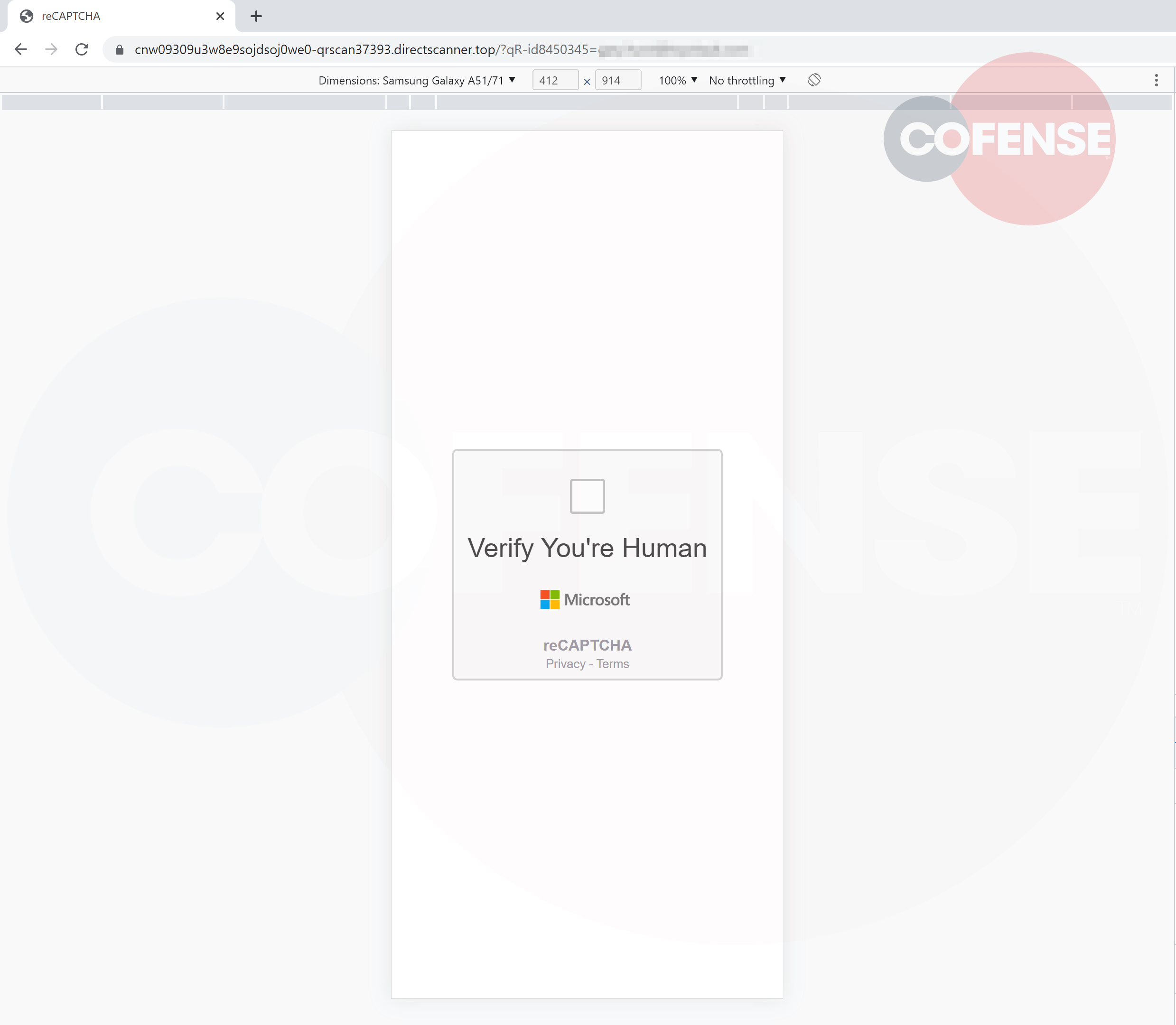
Figure 2 – Captcha Landing Page
After interacting with the captcha, a loading icon will appear followed by a green checkmark, and then user is redirected to the malicious page. In most recent cases noted by the PDC this method deploys a common Microsoft credential phish. However there have been numerous instances of delivery service impersonations also making use of a QR code.
The landing page reflects the intent of the initial email received, consisting of a generic Microsoft login page. Nothing about this page will immediately stand out to an unsuspecting user other than the URL present at the top of the page. The page in Figure 2 and 3 was accessed with the device emulation included in Chrome's developer tools. However, on a phone screen this obviously incorrect and bizarre URL is going to be more difficult to detect due to the smaller size of the address bar.
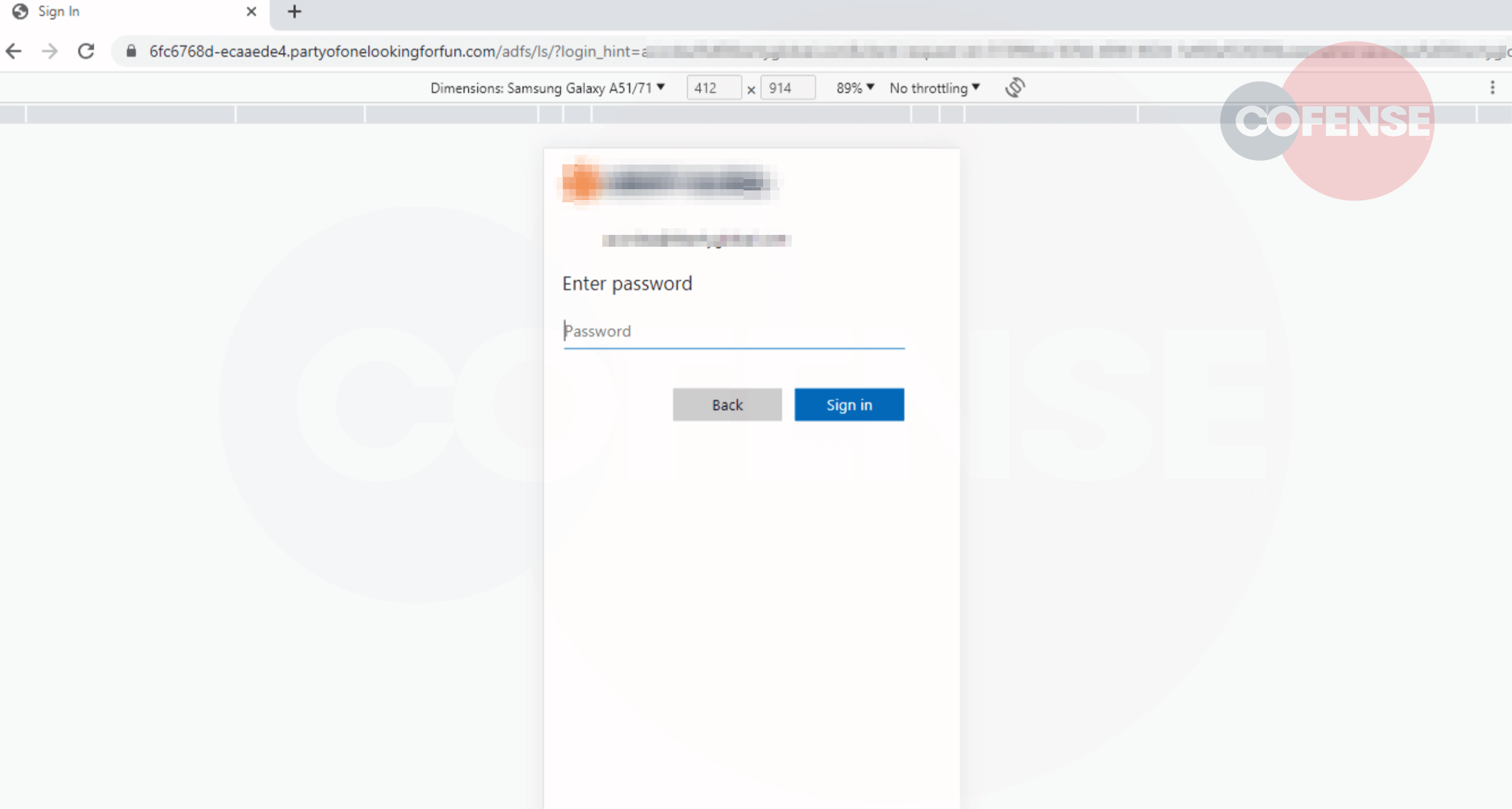
Figure 3 – Microsoft Phishing Page
Users should be wary of scanning QR codes from any source they do not trust. If uncertain, it is advisable to make use of a web-based service to scan the QR code such as the one seen below.
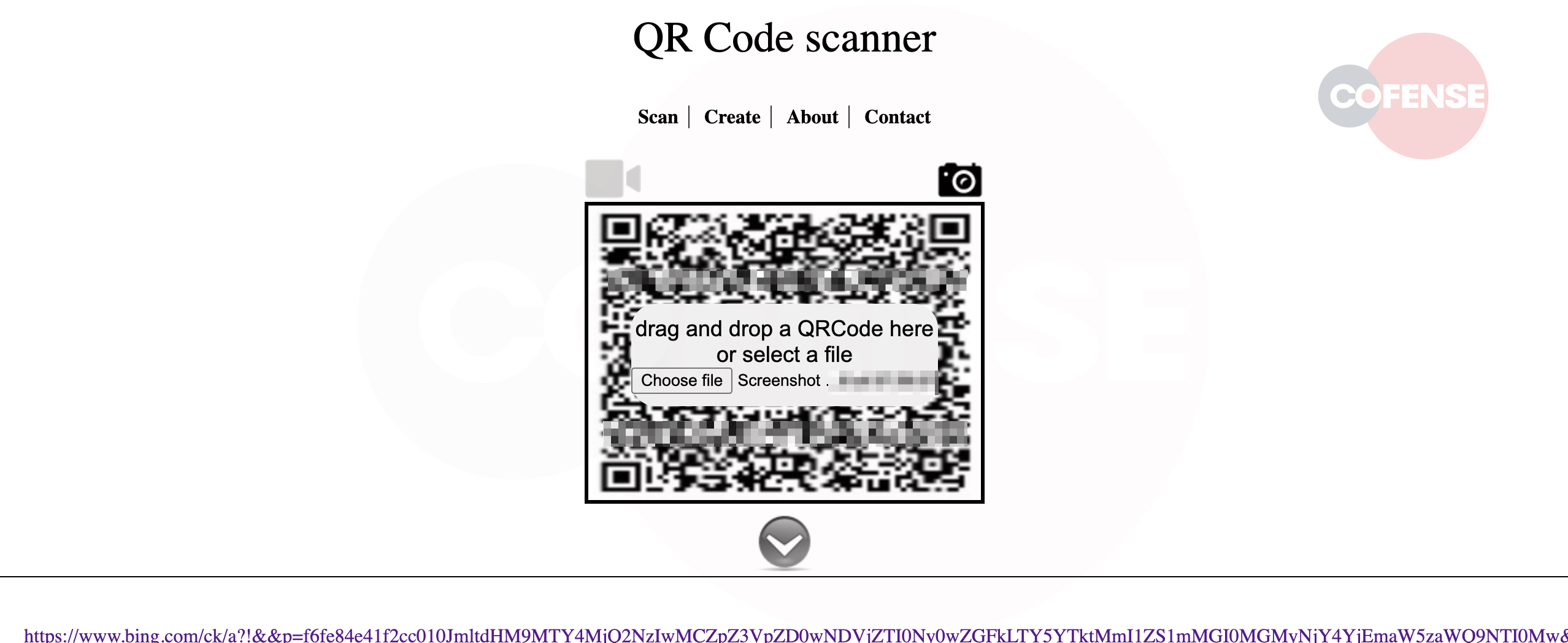
Figure 4 – Browser QR Code Scanner
These sites will enable an accurate review of the URL related to the QR code and prevent accidental navigation to a possibly malicious website.
We recommend educating employees to these dangers and ensuring they will take extra time to guarantee an email is legitimate before interacting with it further. Informed Employees making use of the suite of email protection and phishing education products provided by Cofense, you can more effectively ensure that QR code phishing emails such as this have less of a chance of affecting your business.
IOCs
| hXXps://garandguy[.]com/about-1-blog/ | 172.67.175.89 104.21.91.160 |
| hXXps://instuterapidinfectiononline[.]001387759264229[.]top/ | 45.155.250.159 |
| hXXps://qrz[.]nu/zqSE1W | 54.244.8.132 |
| hXXps://cnw09309u3w8e9sojdsoj0we0-qrscan37393[.]directscanner[.]top/ | 46.101.75.78 |