In the first quarter of 2017, PhishMe Intelligence has noted an increase in malware distributors utilizing OLE packages in order to deliver malware content to victims. This current trend was first noted in December 2016 with close association to the delivery of the Ursnif botnet malware. This technique abuses Microsoft Office documents by prompting the victim to double-click an embedded icon to access some content. These objects are used to write a script application to disk that facilitates the download and execution of a malware payload. This method adds to another iteration of techniques threat actors use to evade anti-analysis and sandbox environments and to successfully infect the intended recipient.
These documents make use of a similar look and feel to Office documents leveraging macro elements for malware delivery but lack the distinctive “enable macros” banner. These documents thereby defy the expectations for malware delivery that have been prominent over the past few years. While Figure 1 demonstrates the usual layout of a macro element and Figure 2 displays one of the many formats used by OLE packages, both show how the documents instruct the victim to “enable editing” in order to interact with the document and view its content but the document leveraging OLE packages lacks the characteristic yellow “enable macros” banner. However, both techniques allow for threat actors to deploy malicious files to the victim’s machine. Both documents may look similar, but are different enough to fool users who know what a macro looks like. As users become more aware of macro elements, OLE objects change it to facilitate the same result but with slightly different presentation.
Figure 2 presents a common example where three separate document icons are presented as documents that can supposedly be viewed by simply double-clicking on each icon. This method also allows for the threat actor to deploy multiple malware applications to disk—or the same malware application multiple times—to maximize the possibility of successful infections. multiple infections to occur simultaneously.
Due to the consistent popularity of Office macro documents among threat actors and the lengths to which security professionals go to prevent successful delivery and deployment of these documents, malware authors seek other innovative methods to deliver their malware content. The use of OLE packages in Office documents is another step in the ongoing online arms race that threat actors hope can grant them the ability to evade technical controls.
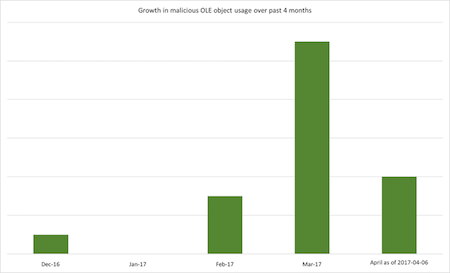
Use of these utilities is on the rise. The most prominent trend associated with the Ursnif malware began in December 2016 and this delivery mechanism has been seen with increasingly frequency since, as Figure 3 shows.
Although this delivery method of malicious OLE objects is not new, it does reinforce an ongoing trend in which threat actors hope to circumvent technical controls. However, threat actors have not yet gained the upper hand outright. Organizations whose users are prepared and empowered to identify and report suspicious emails will not fall victim to the lures created by threat actors and will therefore never encounter the malware delivery tools. Furthermore, security professionals whose toolset is bolstered by the inclusion of actionable threat intelligence can understand both the techniques popular with threat actors and anticipate their attacks. Beyond the standard toolset used by information security professionals, tailored utilities to help with the triage and mitigation of incidents like psparser.py, available in the PhishMe Github repository, can be used to gain an advantage over the threat actor.
For further information, PhishMe Intelligence customers can log into https://www.threathq.com.
For more information on PhishMe’s human vetted, Phishing-specific threat intelligence request a demo today.



