Found in Environments Protected By:
Microsoft, Trend Micro
By Elmer Hernandez, Cofense Phishing Defense Center
As the world recovers and learns to live with Covid-19, use of the pandemic as a phishing theme has started to wane. However, public wariness and anxiety surrounding an emerging medical concern will remain exploitable. Enter the current monkeypox outbreak. The Phishing Defence Center (PDC) has seen attempts to deceive enterprise staff with a series of monkeypox themed phishing emails. As this rare infection spreads around the globe and gains media attention, attackers are likely to continue tweaking their tactics.
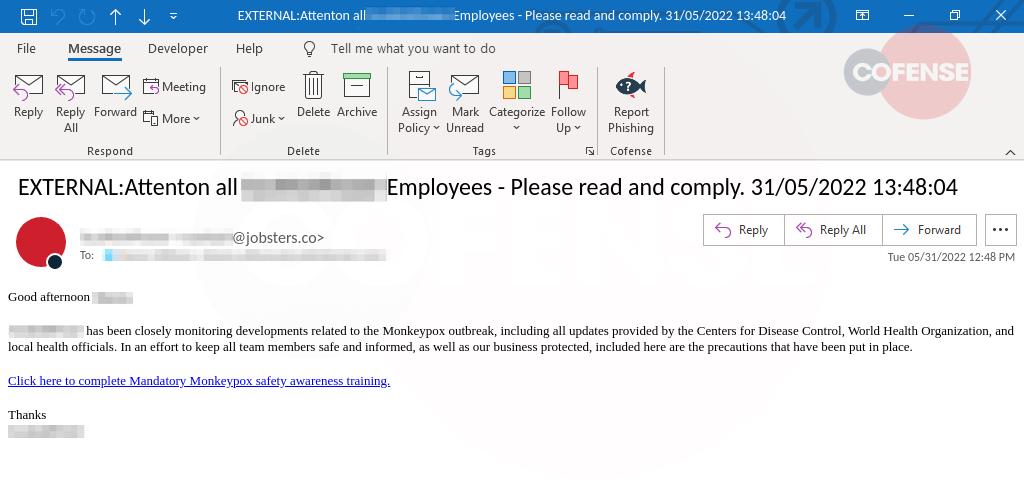
In the last week at least two PDC customers have reported emails such as the one displayed in Figure 1. Both the employee’s and company’s names change depending on who is targeted, but the email body stays the same.
The pretence is similar to what we have already seen with Covid-19 themed phishing emails. It opens up mentioning updates from reputable health organizations to give the impression of veracity and seriousness. It stresses the importance of keeping staff and the company safe, in an attempt to make the employee feel like they share part of the collective responsibility. Finally, it asks all employees of the company to comply with mandatory safety awareness training.
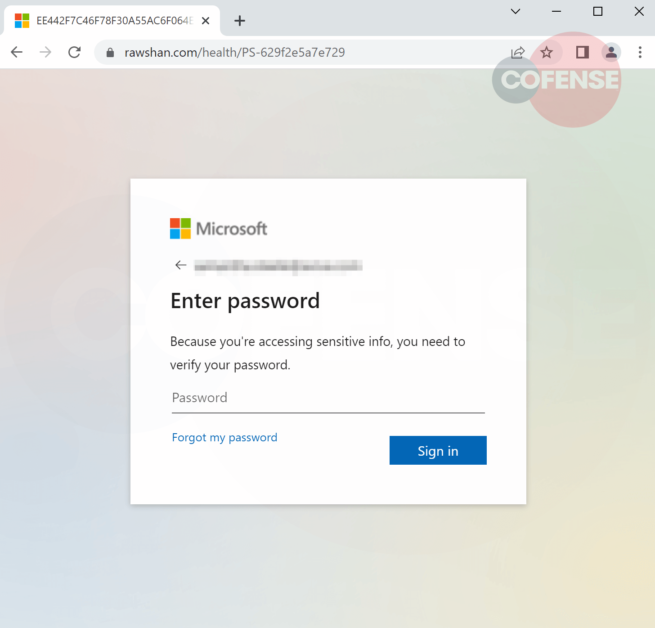
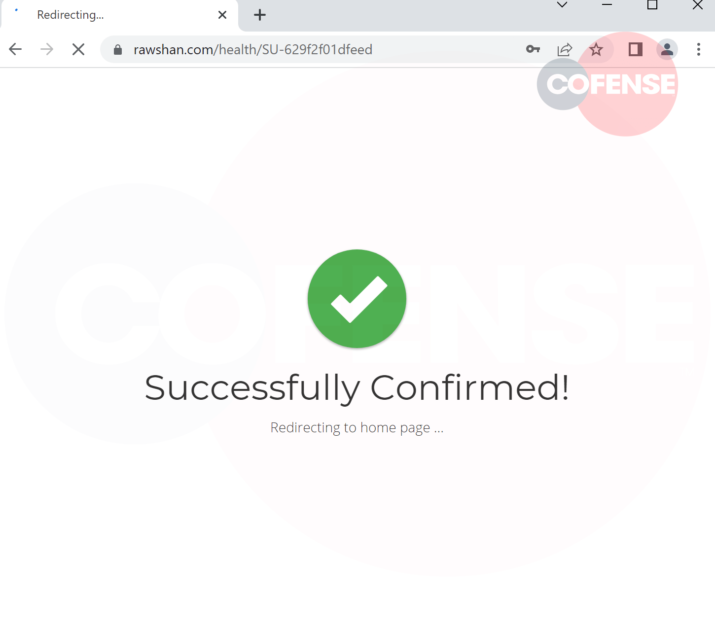
Users are taken to a compromised website and are directed to either a spoofed domain or already compromised website. Looking at the URL, it’s clear the threat actor wanted to add validity to the page by naming the directory as “health”. It is the standard Microsoft credential phishing otherwise. It first asks the user for the email address (Figure 2) and subsequently the password (Figure 3), adding confidence this is necessary due to the sensitive nature of the information being accessed. Once the user has provided all credentials a confirmation page appears for a few seconds (Figure 4) before being redirected to the real Office 365 website.
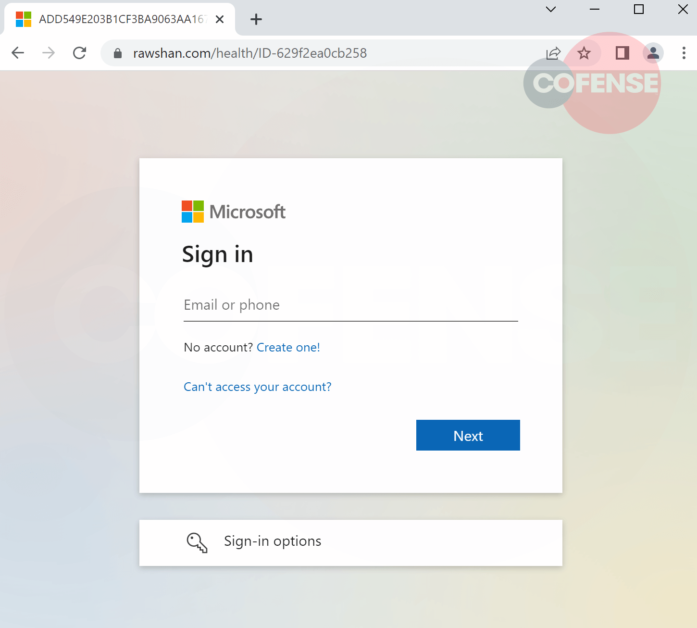
Figure 3 – Password
IoCs
hXXps://rawshan[.]com/health/