By Dylan Duncan
Cofense Intelligence is tracking an advanced campaign that is successfully reaching intended targets in the Oil and Gas industry. The campaign delivers an uncommon, but advanced, Malware-as-a-Service information stealer, the Rhadamanthys Stealer. This new and advanced phishing campaign employs a recently updated Malware-as-a-Service (MaaS) within days of law enforcement’s takedown of LockBit ransomware group, one of the most active Ransomware-as-a-Service (RaaS).
Based on a report by Cyberint published on January 22nd, the malware family recently received a major update on the black market which could be the reason we’re seeing such an unfamiliar family appear in such an advanced campaign. As of this moment, there are a high volume of phishing emails that employ several tactics, techniques, and procedures known to assist in bypassing secure email gateways to deliver the malware.
Breakdown of the Campaign
The campaign starts with a phishing email (Figure 1) using a vehicle incident report to lure victims into interacting with an embedded link that abuses an open redirect on a legitimate domain, primarily Google Maps or Google Images. Users are then redirected several times before finally reaching an interactive PDF file hosted on a recently registered domain docptypefinder[.]info (Figure 2). The PDF is a clickable image which reaches out to a GitHub repository and downloads a ZIP archive that contains a Rhadamanthys Stealer executable. Once a victim attempts to interact with the executable, the malware will unpack and start a connection with a command and control (C2) location that collects any stolen credentials, cryptocurrency wallets, or other sensitive information.
Rhadamanthys Stealer is an uncommon but very advanced Malware-as-a-Service that first appeared in 2022 and is written in the C++ programming language. The stealer implements several features to aid in its many stealing capabilities. The primary use for the stealer is for threat actors to steal device information, document files, cryptocurrency wallets, and credentials stored in various applications and browsers. Based on the report by Cyberint the malware recently received a major update to 5.0 giving threat actors who purchase the service a more customizable experience and allowing additional measures to counter security and exploit vulnerabilities. Table 1 at the end of this report shows a sample of the IOCs pulled from this campaign, and for Cofense customers the full stack can be seen on the Active Threat Report on ThreatHQ.
We will continue to provide more details when they become available.
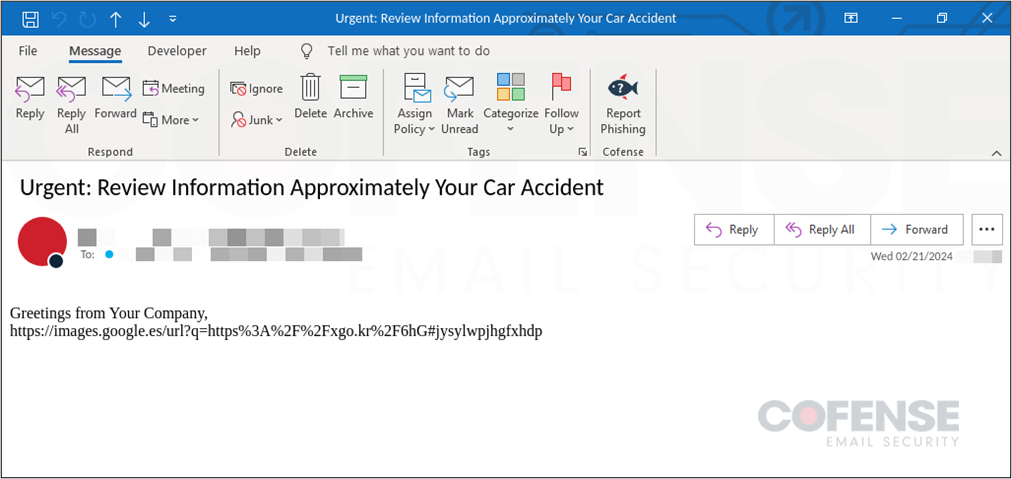
Figure 1: Phishing Email Targeting Oil and Gas Sector to Deliver Rhadamanthys Stealer.
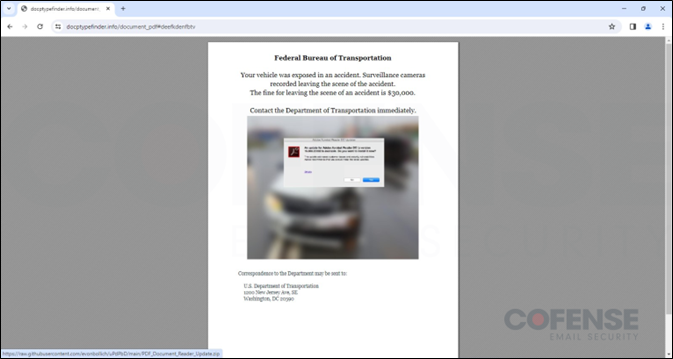
Figure 2: Recently registered domain hosting a clickable PDF file.


