By: Kahng An, Intelligence Team
Threat actors often abuse legitimate remote access tools (RATs) for malicious deployments on unsuspecting victims. These legitimate RATs are different from remote access trojans (also abbreviated as RAT) because they are software originally intended for legitimate use. Threat actors can abuse trust in RATs because the software is technically legitimate and often designed for enterprise use. Once a RAT's agent is installed onto a victim’s machine, threat actors could quickly pivot to delivering additional malicious payloads or monitoring for sensitive information such as credentials or confidential business information. The overall versatility of RATs combined with their perceived legitimacy makes them particularly dangerous. This report will offer an overview of some commonly abused RATs and their associated campaign tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs).
Key Takeaways
- ConnectWise RAT is the most popularly abused legitimate remote access tool and accounted for 56% of all active threat reports (ATRs) with legitimate remote access tools in 2024.
- Notable campaigns include spoofing the Social Security Administration with benefit-themed emails and spoofing files[.]fm with shared file-themed emails.
- FleetDeck was popular in the Summer of 2024 when it targeted French and German language speakers with finance-themed emails.
- Because of the number of different technically legitimate tools that exist, threat actors are quickly able to pivot to new deployments of the same tool or use different ones entirely for cheap or entirely free.
ConnectWise ScreenConnect (ConnectWise RAT)
ConnectWise ScreenConnect (formerly known under its prior names “ConnectWise Control” and “ScreenConnect”) is a popular RAT intended for both non-commercial personal use and enterprise use. Notably, it offers a 14-day free trial that is often abused by threat actors. After the 14-day trial expires, the account is downgraded to a permanently free tier that is only able to deliver 3 agents, limiting the campaign’s overall scope and scale. Upon creating an account, a threat actor would be able to generate agents as a Windows .exe or .msi file, though the vast majority of ATRs for ConnectWise RAT use .exe files. These trial or free tier accounts typically use ConnectWise’s cloud infrastructure for hosting the C2 servers which generally are formatted like below where the “#” represents a random alphanumeric character:

Notably, a cloud instance can be customized to have a custom URL to make use of a domain that the threat actor controls. Additionally, a threat actor could opt to run the ConnectWise RAT server software on their infrastructure. This server will run on port 8041 by default, creating C2 URLs like the following:

The download URL for a ConnectWise RAT agent installer will often include the C2 as a part of the parameters. Additionally, the same parameters can be found in the process information for the ConnectWise agent when it is running. The following example contains the C2 URL “verify[.]uniupdate[.]net” in the “h” parameter and the port 8041 in the “p” parameter.

ConnectWise RAT accounts for the majority of abused legitimate RATs seen in ATRs from 2024 appearing in 56% of ATRs involving legitimate RATs. ConnectWise RAT is accelerating in popularity in 2025 with its current ATR volume already equaling the amount identified in 2024 as of the time of this report. Given its popularity, it is featured in a few notable campaigns.
United States Social Security-Spoofing Benefits-Themed Campaign
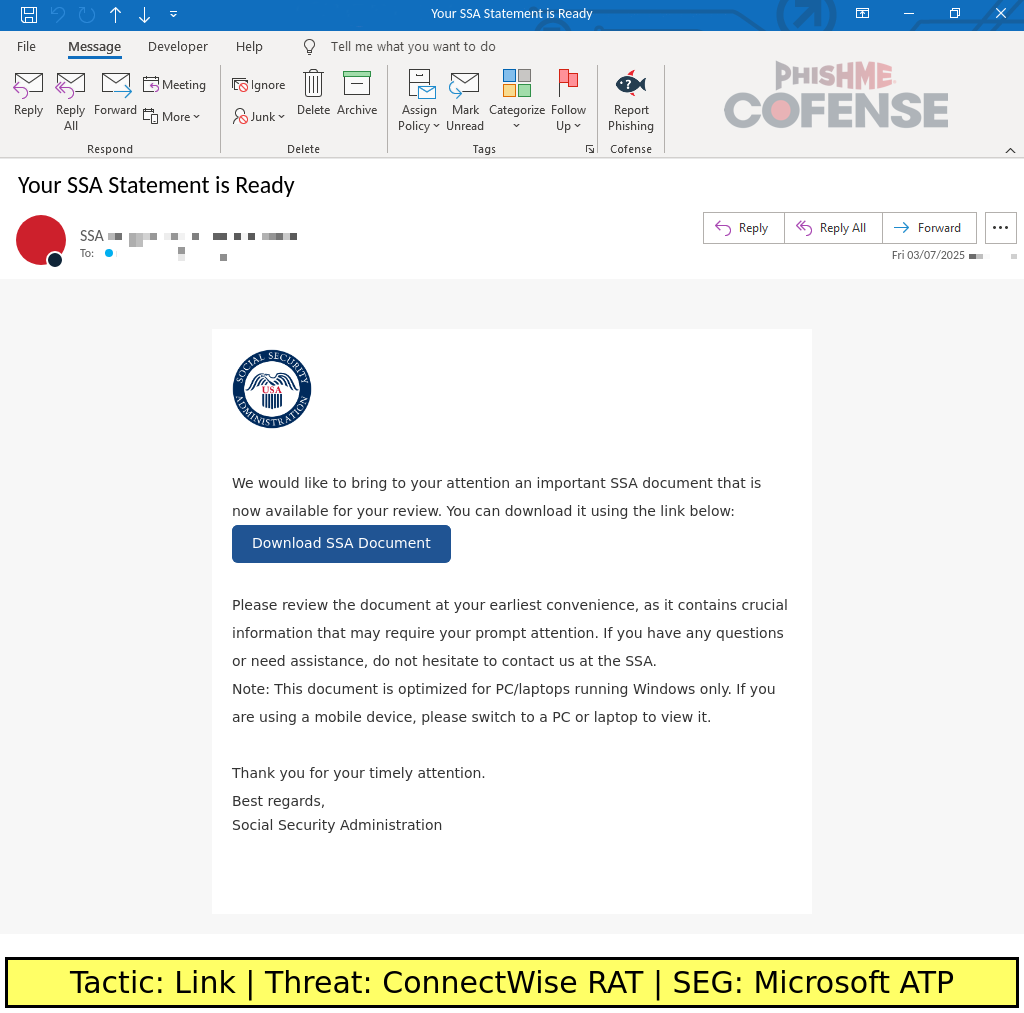
Figure 1: A sample Social Security-spoofing email that delivers ConnectWise RAT.
Emails in this campaign claim to deliver updated Social Security benefits statements which need to be accessed via an embedded link. The embedded link typically leads to a website controlled by a threat actor with a link that purports to be the statement. Alternatively, the embedded link in the email may directly lead to the file download. Regardless of this distinction, the file itself is typically named as if it were a PDF viewer or PDF file such as:
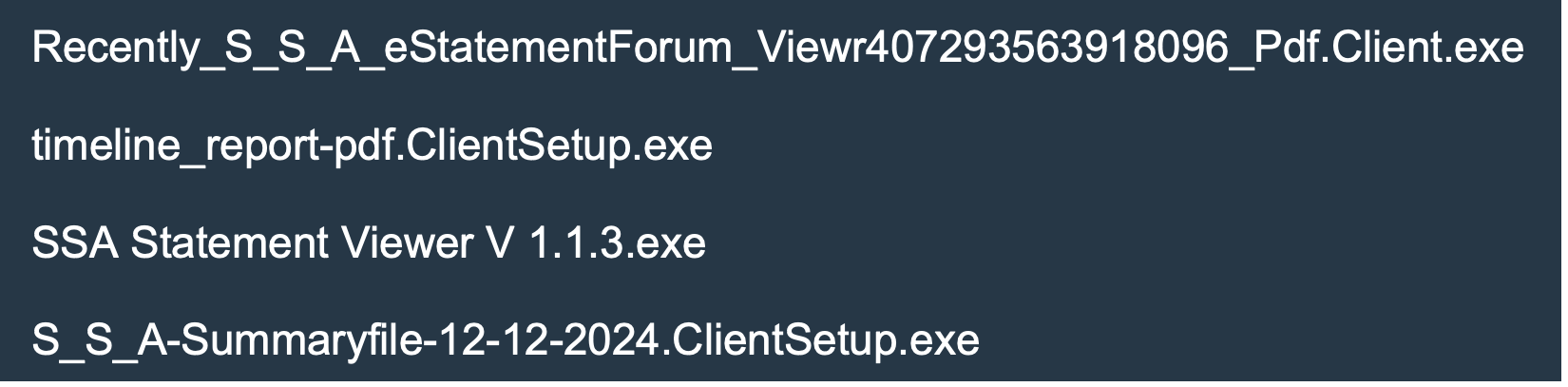
This campaign has also been previously featured in the blog post “Hackers Spoof Social Security Administration to Deliver ScreenConnect Remote Access Tool” which provides further details on the historical evolution of its tactics. In some cases, the campaign delivered credential phishing on top of ConnectWise RAT.
Files[.]fm-Spoofing Shared File-Themed Campaign
Starting on Feb 5, 2025, this campaign delivers shared file-themed emails purporting to notify that the recipient had received a PDF file on files[.]fm, a cloud file storage site. The emails contain an embedded link to a document hosted on files[.]fm that claims the recipient received a secure document which needs to be downloaded from Microsoft OneDrive via the provided link which delivers the ConnectWise RAT installer. The installer is notable for being named as if it were a OneDrive client needed to open the secure document:
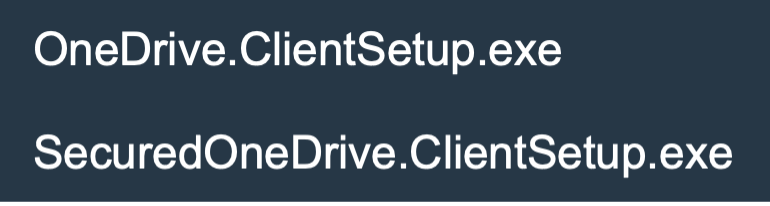
Additionally, some instances of this campaign deliver embedded links to a PDF file hosted on files[.]fm which contains a link to a credential phishing page and a link to download ConnectWise RAT.
Atera and Splashtop
Atera is an all-in-one remote monitoring and management suite that offers remote access via built-in integration with Splashtop, Anydesk, TeamViewer, and ConnectWise ScreenConnect. Many of its features are aimed at enterprise IT teams that need a remote system monitoring and patching solution. However, its permissive 30-day free trial gives access to all features and allows threat actors ample time to conduct prolonged campaigns. This report will focus specifically on Atera with Splashtop integration, which appears to be the most popular method of remote access within Atera due to its seamless integration.
From an IOC perspective, the Atera agent is notable for generating lots of network traffic spread across multiple different API endpoints. The following is a non-exhaustive list of sample endpoints:

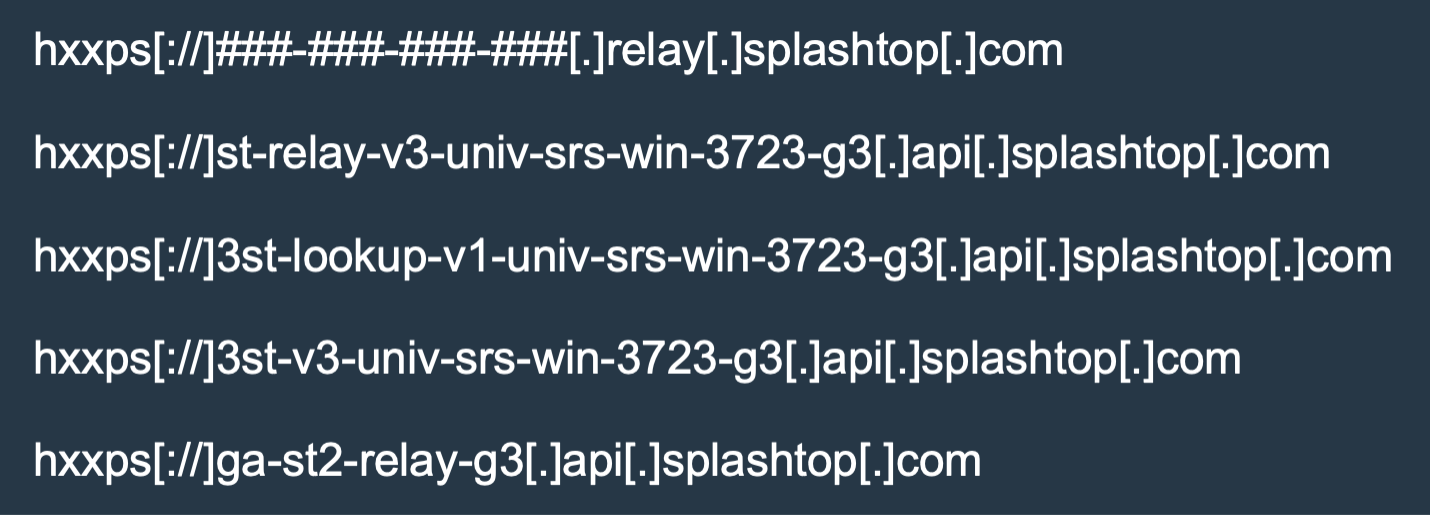
The Splashtop agent similarly uses multiple different relay server endpoints for C2 traffic formatted as shown in the non-exhaustive list of sample endpoints below where the “#”s represents an IPv4 address:
Finance or Legal-Themed Brazilian Portuguese Language Campaign
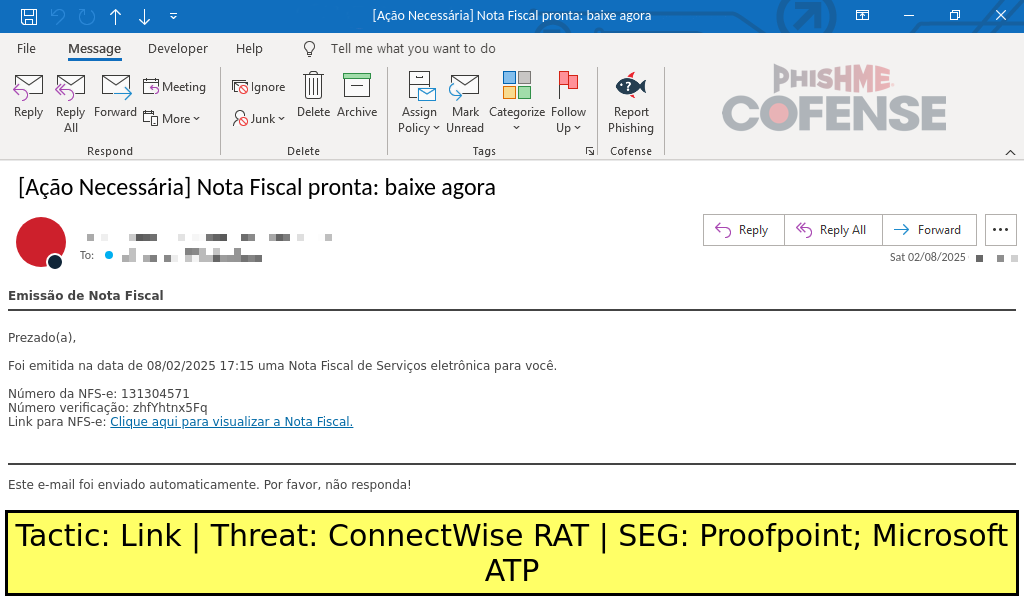
Figure 1: A sample Brazilian Portuguese email that delivers Atera and Splashtop.
Starting in October 2024, a Brazilian Labor Court-spoofing email was found delivering an embedded link that is purported to be a legal notice that is pending processing. However, the link delivers an Atera agent installer which then deploys Splashtop for remote access. Further samples claiming to be invoices instead of legal notices were found in November 2024 and February 2025. Emails in this campaign are in Portuguese and appear to target Brazilian victims.
FleetDeck
Compared to the other remote access tools discussed in this report, FleetDeck represents a more boutique remote management solution that is less commonly used in enterprises but could still theoretically be legitimately used in one. However, it is far more likely to be used maliciously than legitimately within an environment compared to tools such as ScreenConnect or Atera. In this sense, FleetDeck is more similar to BreakingSecurity’s Remcos remote access “tool” which is tracked by Cofense as Remcos RAT. Threat actors often use older versions of Remcos RAT that have been cracked and are freely distributed online. FleetDeck’s last update appears to be from April 2022, and the product does not appear to be actively maintained since then, making the product unlikely to be used in any legitimate enterprise setting.
FleetDeck instances appear to be hosted on FleetDeck’s cloud infrastructure with the FleetDeck agent being unique to each instance:

Similarly, FleetDeck infrastructure is used for C2 communications:
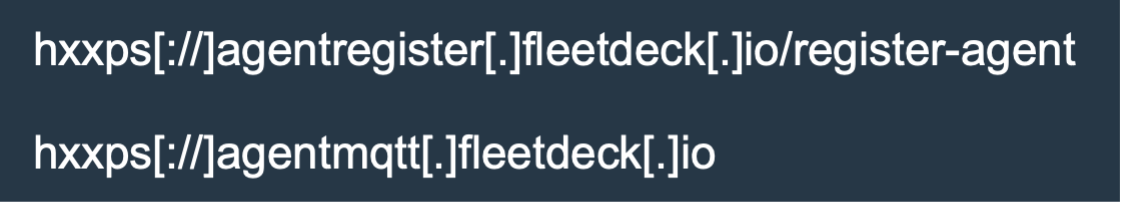
FleetDeck campaigns were first seen by Cofense in large volume during July 2024 and quickly ramped up in frequency during early August 2024 before trailing off in popularity. This is possible because FleetDeck uses a shared URL endpoint for all C2 traffic, meaning that blocking traffic to that endpoint will block all FleetDeck traffic.
Finance-Themed French or German Language Campaign
The majority of FleetDeck samples in 2024 appear to be French or German-language emails purporting to be notifications for unpaid invoices or processed payments. The emails include an attached PDF document shown in Figure 3 that contains an embedded link to the FleetDeck agent installer and claims that “Adobe FleetDeck” is required to view the document. This campaign is notable for attempting to socially engineer the email recipient into thinking that FleetDeck is a legitimate service that is required to view the attached document.
Other Miscellaneous Remote Access Tools
While this report focuses on the previously mentioned tools because of their popularity as legitimate tools or in notable campaigns, there have been multiple smaller RATs that have been used in recent ongoing campaigns. LogMeIn Resolve (formerly known as “GoTo Resolve”, “GoToAssist”, and “Rescue Assist”) is tracked by Cofense as GoTo RAT and was seen in an English-language campaign themed around order invoices. Gooxion RAT is a Chinese RAT that has been used in Chinese language emails with finance themes. PDQ Connect, Mesh Agent, and N-Able are all RATs that have been used in Portuguese language emails with finance or shipping themes. Teramind was used in an Italian language email spoofing the Agenzia per la Cybersicurezza Nazionale, an Italian government agency for cybersecurity.
These campaigns are generally one-off events and do not appear to be sustained over time. It is possible that the threat actors quickly pivot between different RATs because of the overall large number of different options that are available on the market.