By: Akhil Varghese, Cofense Phishing Defense Center
A recent phishing attack observed at Cofense Phishing Defense Center (PDC) has revealed a tactic used by cybercriminals to target Suncorp Bank customers. Phishing email uses an account deletion threat to create a sense of urgency and compel recipients to act quickly. Taking a closer look at this phishing attack we can observe the tactics used by cybercriminals. 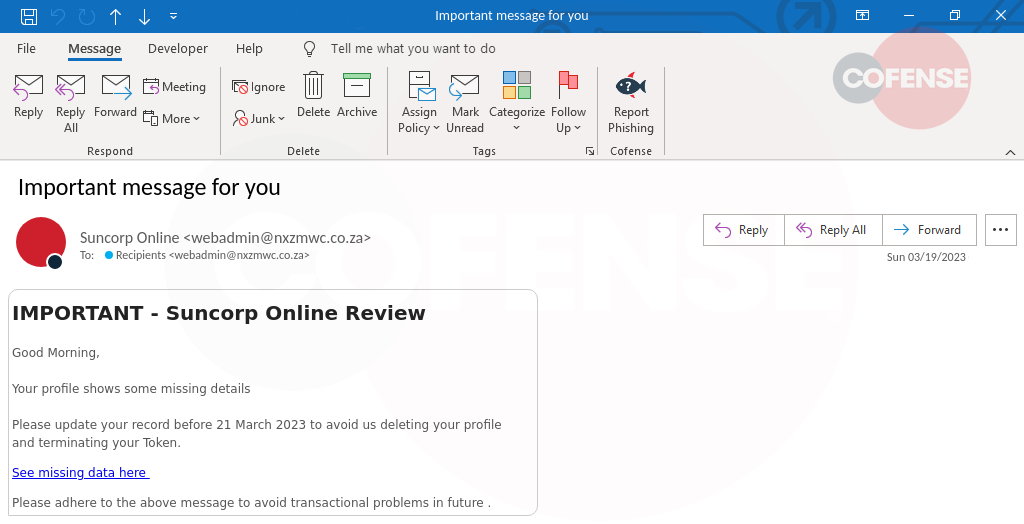
Figure 1: Email Body
The email appears to be from Suncorp Bank and states that the recipient's account will be deleted unless they take immediate action. It seems to be legitimate at first glance, but upon closer inspection, there are several red flags that indicate it is a phishing attack. The sender’s address is coming from a South Africa domain, which should immediately alert potential recipients as Suncorp Australia would not be based anywhere overseas. The email instructs the recipient to click on a link that takes them to a landing page, but if you hover over the hyperlink, can see that the website URL is not related Suncorp bank, but a phishing page that has been created to steal the user's login credentials. 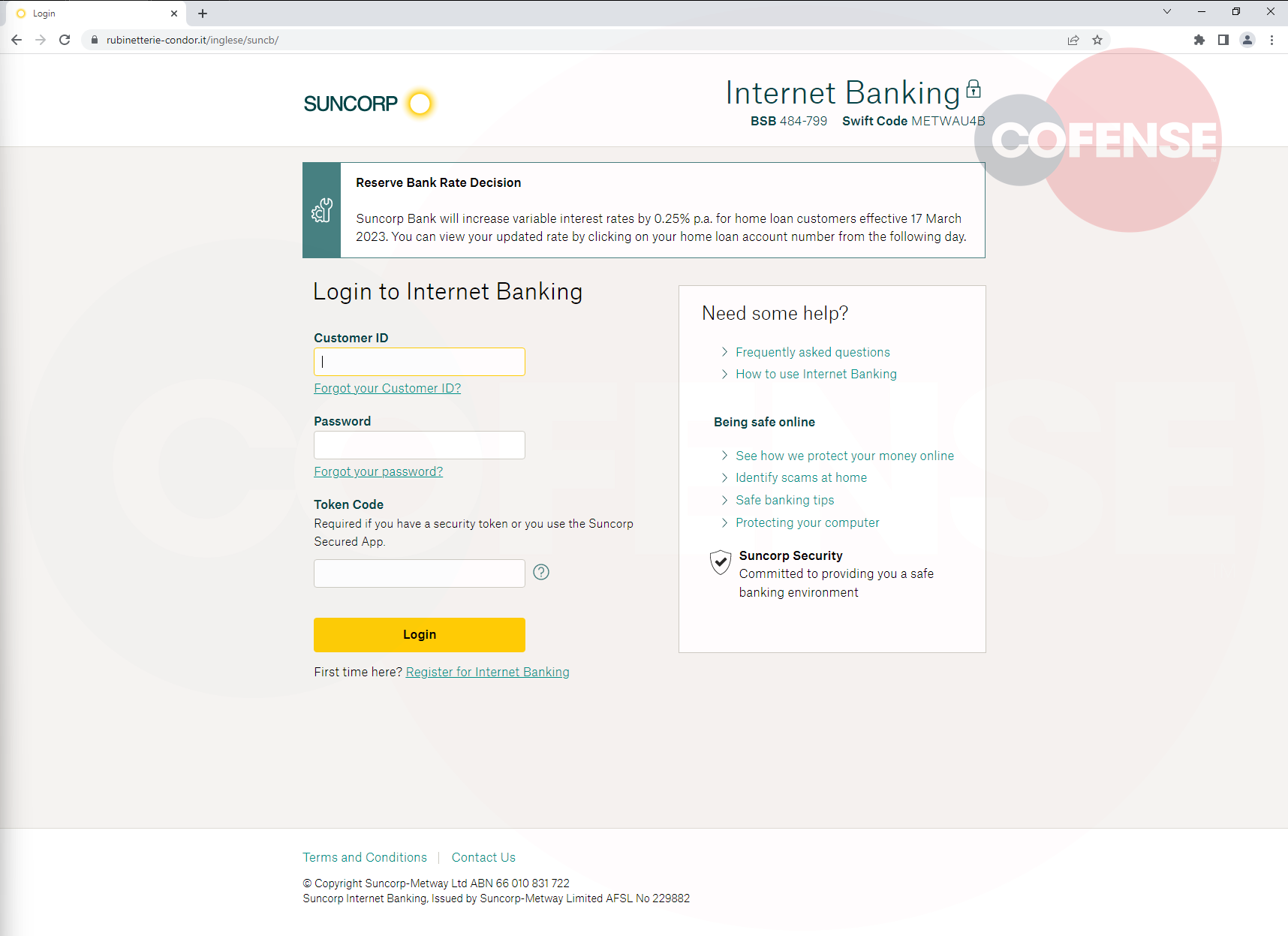
Figure 2: Phishing Landing Page
The landing page is an exact replica of the Suncorp Internet Banking login page. Once the user has entered their login credentials, they are directed to a second page which requests additional customer details, such as their full name, mobile number, and email address. This page is also designed to look like an official Suncorp Bank page, even displaying their legitimate BSB and Swift code at the top of the page to create trust with the user, but it is in fact a fraudulent page created to harvest the user's personal information. 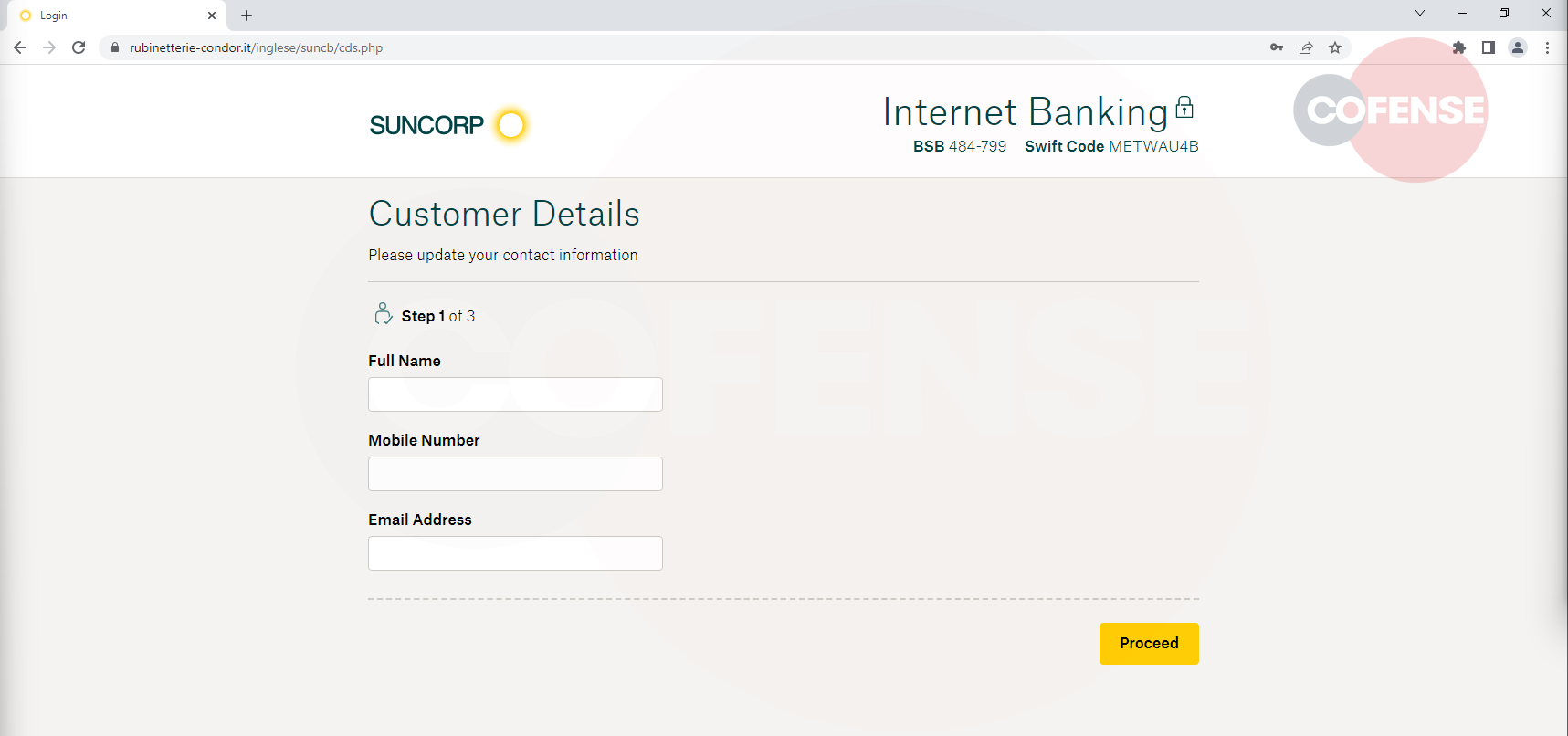
Figure 3: Fake Page for User Details
Finally, the user is directed to a page that asks for a One-Time Password (OTP). The page may claim that the OTP is required for security purposes, but it is a ploy to gain access to the user's account. It's important to note that the attacker does not generate the OTP themselves, instead they rely on the legitimate service provider to send the OTP to the victim's registered phone number or email address as part of the 2FA process. The attackers can prompt the OTP through scripts that will automatically try to login to the users legitimate Suncorp account. Once the user enters the OTP, the threat actor can use it to log in to the user's account and steal their money or personal information. Once the OTP is entered, the user gets a success message and recommends that they close the page. 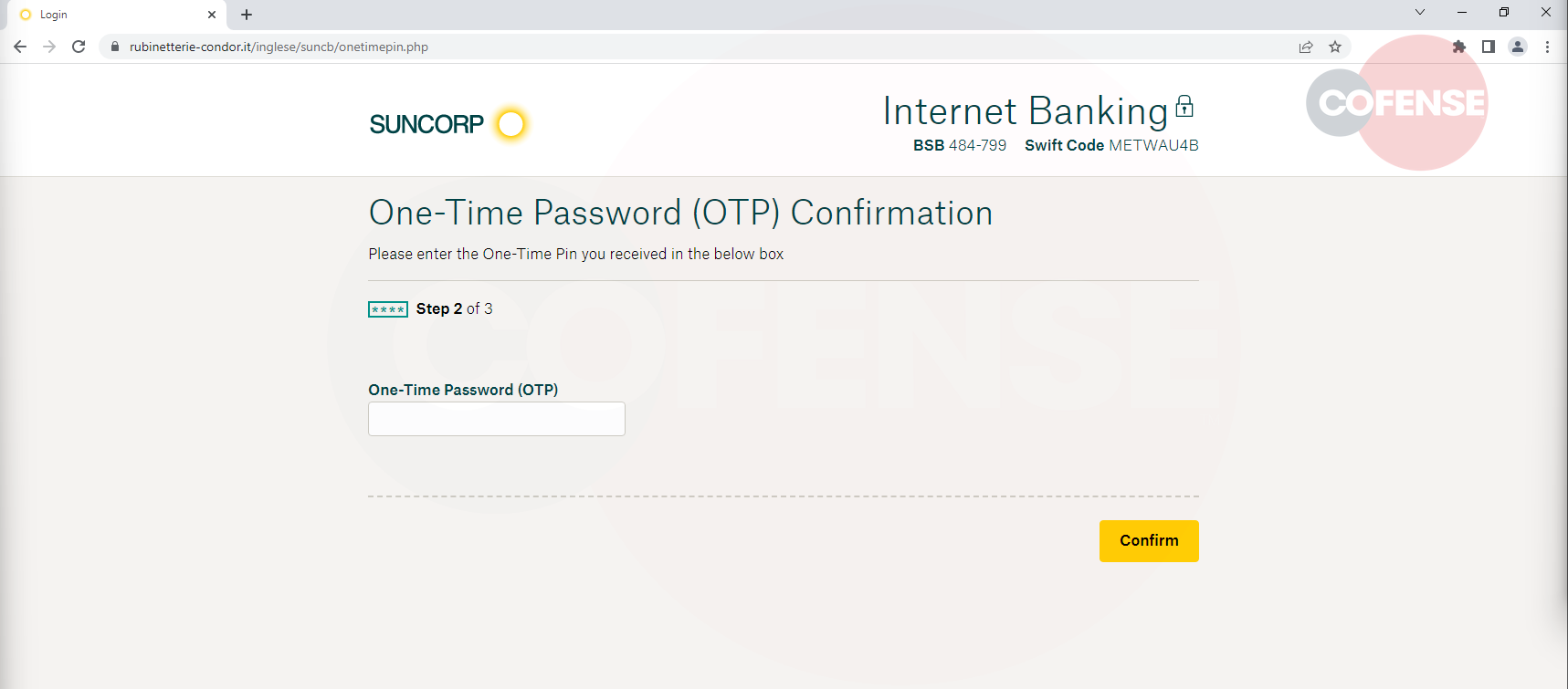
Figure 4: Fake OTP Page
In conclusion, phishing attacks that impersonate financial institutions like Suncorp Bank are a serious threat to online security. Cybercriminals are constantly evolving their tactics to trick unsuspecting users, but by remaining vigilant and learning to spot the red flags of phishing emails and pages, you can protect yourself from falling victim to such attacks. In Cofense Phishing Defense Center (PDC) we use advanced email filters that can detect suspicious patterns and known phishing signatures along with human vetted intelligence to prevent these kinds of phishing attacks. If you receive a phishing email like this, it is important to report it and delete the email from your inbox. If you have already fallen victim to a phishing scam, it is crucial to take immediate action to protect your accounts and personal information. If your enterprise would like to benefit from the protection of the PDC, contact us to learn more.
| Indicators of Compromise | IP | |
|---|---|---|
| hXXps://www[.]cyrelleblue[.]com/_core/banny[.]php | 89.46.104.42 | |
| hXXps://www[.]rubinetterie-condor[.]it/inglese/ | 89.46.110.54 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results. The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.