Author: Tonia Dudley
Earlier this year, Cofense released its 2022 Annual State of Phishing Report highlighting insights and analysis seen in customer environments. One major takeaway, the amount of phish that continue to bypass Secure Email Gateways (SEGs). To provide more insights on this topic, Cofense CTO & Co-Founder, Aaron Higbee, and myself sat down to go in-depth and highlight findings on SEG misses.
While organizations analyze data across industries to see how they compare against peers, we also recommend you compare your organization against your technology stack. As you tune your security controls and SEG, are you able to detect and respond to new threats as they land in the inbox?
Key Takeaway #1: Threat Actors tune their tactics.
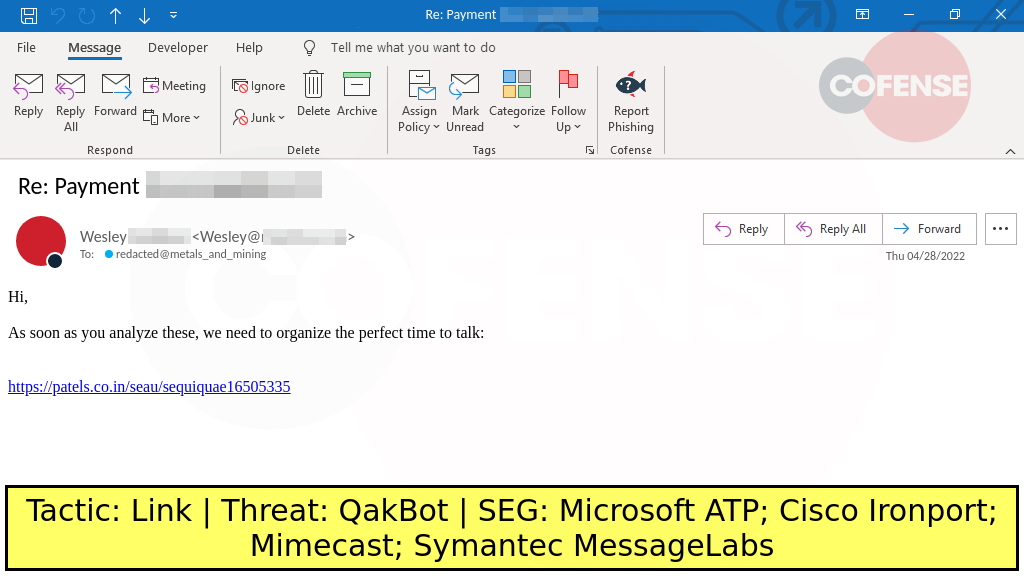
As SEGs tune for file attachment threats, which continues to show low inbox hits, Cofense continues to see new file attachment types used to bypass the SEG. These odd file types may appear obscure to your user surfing their inbox, but often times these odd file types are very much still recognized by native Microsoft Windows endpoints. Along with odd file types, we stay abreast of new behavior tactics used by threat groups. The email in Figure 1 is related to the known QakBot malware family, but this particular campaign switched their tactic by directing the recipient to click the link that is a download of a zip file. However, when the recipient interacts with this zip file and extracts the .MSI file, QakBot is then launched onto the device.
Key Takeaway #2: The top file attachment type landing in the inbox.
Threat actors continue to leverage the one file type they know will land in the inbox and likely get engagement from the recipient – HTML / HTM files. This file type can be difficult to mitigate by configuring a hard block as many legitimate business applications or SaaS solutions use this file type. Look for ways to mitigate this risk by working with the business owners to identify the recipient population that need to receive these emails. Then provide resources that allow your users to validate a legitimate service that send this file type. The best way to condition and prepare your organization to identify and report this threat is to use this file type in simulation phishing campaign.
Key Takeaway #3: Microsoft updated Office file types – did you?
Not only are odd file types being leverage, but what about file types that have been sunset. I don’t know about you, but I’m not sure the last time I used an MS Office product that didn’t add the ‘x’ to file extension (.xlsx or .docx). This can be a simple configuration to add these to archived file types to your block list and minimize the risk of these files landing in the inbox.
As we closed out the discussion on odd file types and opened the floor for questions, we received a question that has been a discussion point lately as organizations are looking to focus their phishing defense programs.
What are you using to measure the effectiveness of your phishing defense program?
Tune into the recording for our summary and stay tuned as we publish more recommendations on this topic.
Threat actors are continuing to use emerging tactics and techniques to bypass traditional email security solutions and the only way to stay ahead of the curve is to have a comprehensive phishing defense strategy. If you’re interested in a more detailed analysis of SEG effectiveness, BEC insights or catching ransomware at the phishing stage, sign up for our upcoming webinars.


