By: Brad Haas
In early 2023, an increasing number of credential phishing URLs in emails reported to the Cofense Phishing Defense Center (PDC) have included a unique string showing that they were produced by a legitimate email newsletter program named SuperMailer. The inclusion of the string is a mistake threat actors made when crafting their email templates in SuperMailer. The error occurred in a small subset of what has turned into a high-volume credential phishing campaign. By combining SuperMailer’s customization features and sending capabilities with secure email gateway (SEG) evasion tactics, the threat actors behind the campaign have delivered tailored, legitimate-looking emails to inboxes spanning every industry.
Key points
- This threat activity employs open redirect abuse, varied email senders, and URL randomization to bypass email security measures.
- The monthly volume of this activity more than doubled in three out of the past four months.
- In May 2023 to date, it accounts for 14% of credential phish discovered by Cofense (PDC) in environments protected by a variety of SEGs, including Proofpoint, Microsoft ATP, Cisco Ironport, Mimecast, Fortinet, and TrendMicro.
- Campaigns within this activity set have broadly targeted a wide range of industries, including construction, consumer goods, energy, financial services, food service, government, healthcare, information and analytics, insurance, manufacturing, media, mining, professional services, retail, technology, transportation, and utilities.
Besides being a prolific current threat, the campaign discussed in this report is a case study in the constant evolution of the phishing threat landscape. The threat actors behind the campaign found a working combination of tactics, refined it, and scaled it up, all within a matter of weeks. The fact that the emails are reaching users so consistently underscores the importance of user awareness and a robust, intelligence-driven email security program.
Volume Started Low, Then Skyrocketed in May
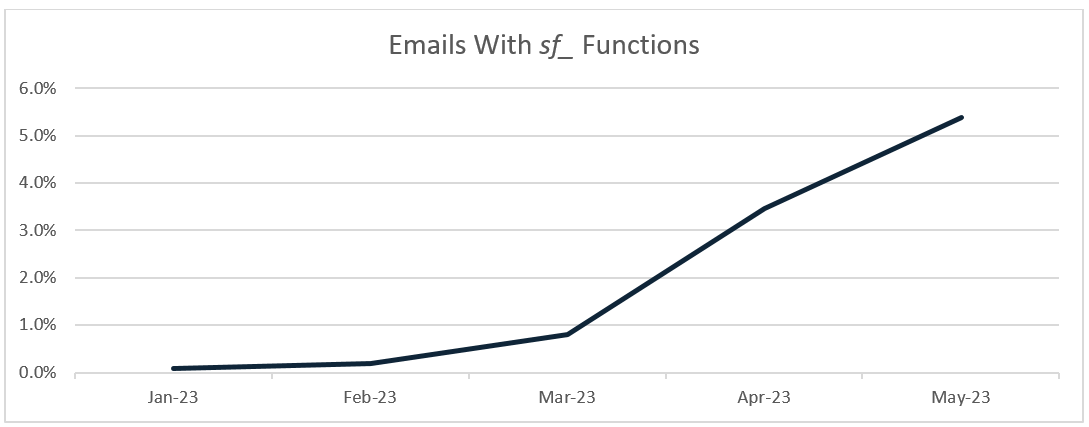
The SuperMailer generated emails have been reaching inboxes at an increasingly remarkable volume. Emails containing the unique SuperMailer string barely registered in January and February, but in the first half of May they accounted for over 5% of credential phishing emails reported by Cofense PDC customers.
Figure 1: Emails containing the error identifying them as generated by SuperMailer, as a share of all PDC-reported credential phishing emails through May 15, 2023.
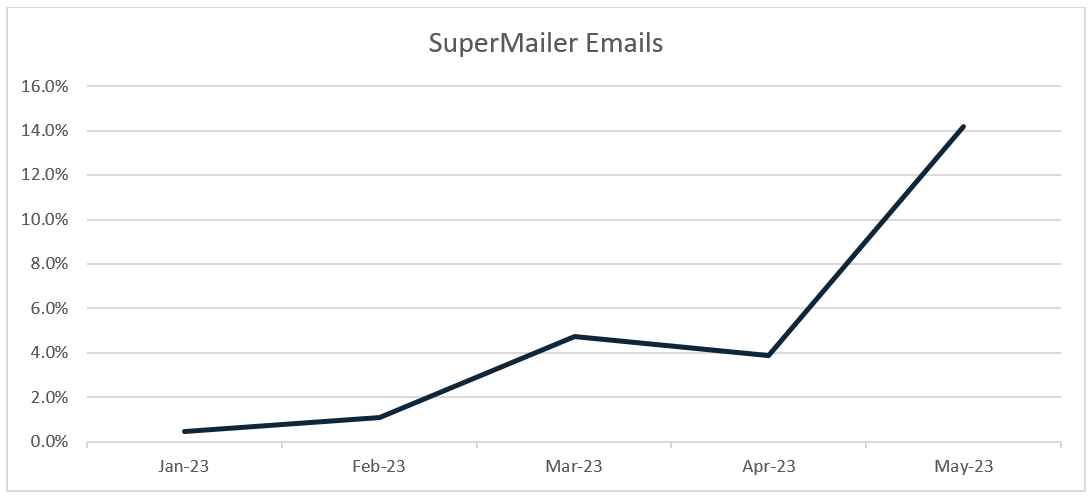
We identified other unique indicators in the emails that contained the mistake, and broadened our search to include those indicators. In other words, how many emails of these emails do not contain mistakes and are reaching users? The volume follows the same overall trajectory, but it has exploded in the first half of May, comprising over 14% of all reported credential phishing emails during the month to date.
Figure 2: Emails with IOCs matching the emails containing the SuperMailer error, as a share of all PDC-reported credential phishing emails through May 15, 2023.
The targeting appears to be as broad as possible; these emails are reaching users at organizations in every industry. Most if not all of the emails use the same tactics, suggesting that a single threat actor is responsible for the campaigns.
Core SuperMailer Features Are Attractive to Phishing Threat Actors
SuperMailer is a commercial desktop application that bills itself as “email HTML newsletter software to create and send newsletters and personalized mass emails.” The increasing pace of the SuperMailer-generated campaign despite the occasional errors suggests that the threat actors find a great deal of value in it. We researched SuperMailer to find out what would make it so attractive to threat actors, and we found that it includes several features that are useful not only for legitimate email list operators, but also for threat actors sending phishing campaigns:
- Placeholder fields allowing for emails personalized with the targeted user’s name, organization, or other details.
- A “what you see is what you get” editor makes it easy to generate visually appealing HTML emails that can appear more legitimate.
- Multi-threaded email sending allows for fast transmission of thousands of emails.
- Compatibility with several email systems allows threat actors to spread their sending operation across multiple services, minimizing impact if any are blocked or otherwise disabled.
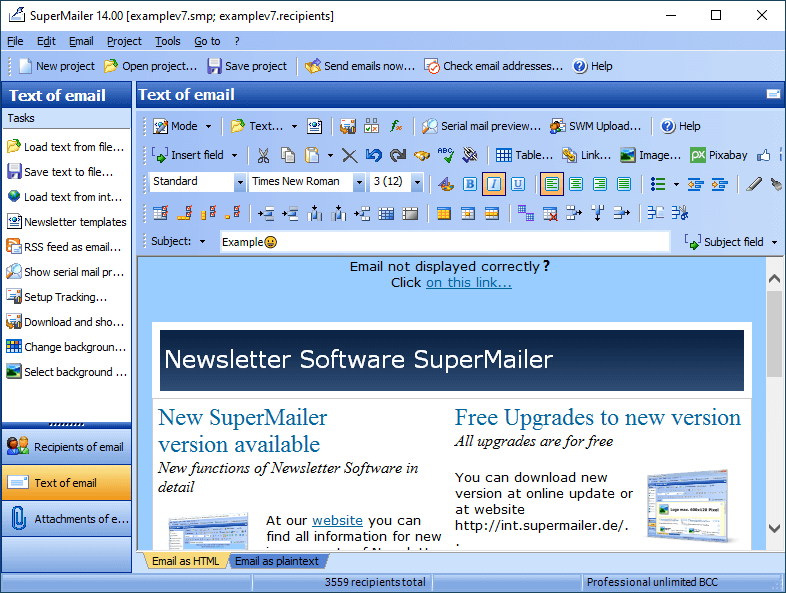
Figure 3: Example screenshot from the SuperMailer website.
Abusing legitimate software and services to send malicious email is not a rare or novel tactic. But the recent SuperMailer campaigns highlight its utility in a phishing threat actor’s arsenal, and the frequency at which these emails have been discovered in inboxes demonstrates an extremely high rate of success.
Campaign Combines SuperMailer Customization and SEG Evasion Tactics
SuperMailer’s templating and other features allow for personalized, well-crafted phishing emails, which have a higher chance of fooling the recipient. In the recent campaigns we analyzed, the threat actors used several customizable fields:
- recipient details: first name, last name, email address, username
- organization details: name, domain
- current or recent date and time
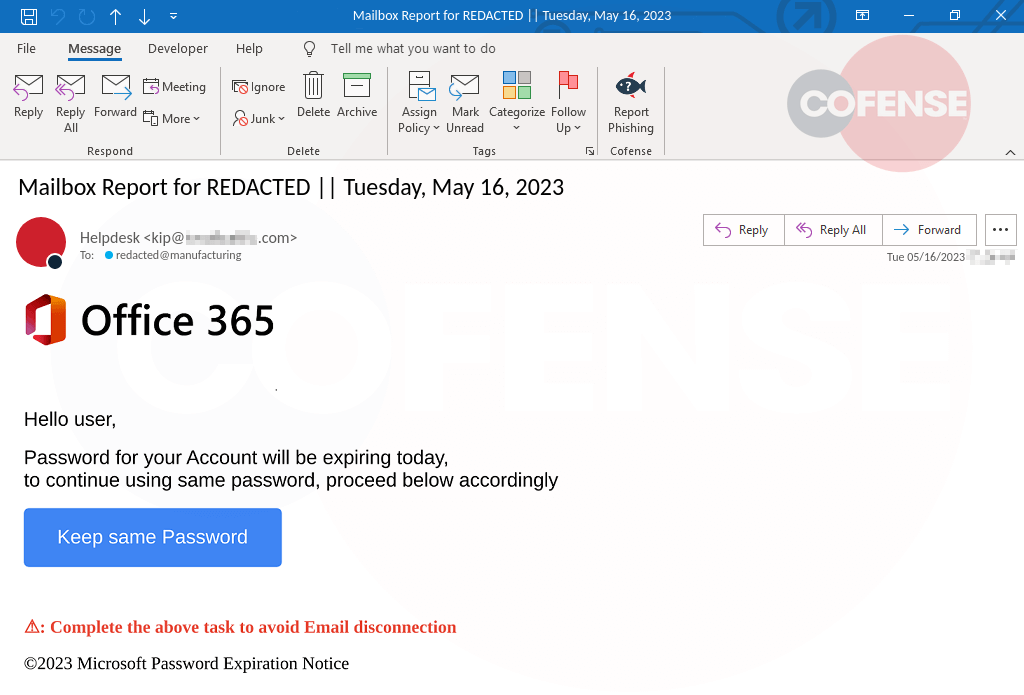
Figure 4: An email customized with the recipient’s email address (redacted) and the current date in the subject.
In addition to the customization, the threat actors are using well-established email themes, including notification of password expiration, documents from a scanner or signature service, and past-due invoices or payment notifications. We see the same themes quite often in other credential phishing campaigns, as well as malware campaigns, which suggests that they have the highest likelihood to get the recipient to click a malicious link. In the case of the recent campaigns, the threat actors are pursuing Microsoft login credentials.
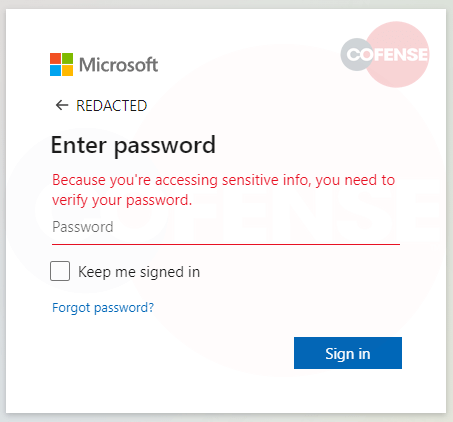
Figure 5: The spoofed login form on one of the phishing pages from the recent campaigns.
Of course, a phishing email has to reach the recipient’s inbox before it can fool them. To that end, the recent SuperMailer-generated campaigns are using a few different tactics to avoid detection by SEGs and other security measures:
- Open redirect abuse takes advantage of legitimate web pages that automatically redirect to any URL included as a parameter. If a SEG does not follow the redirect, it will only check the content or reputation of the legitimate website. Although open redirects are generally considered to be a weakness, they can often be found even on high-profile sites. For example, the campaigns we analyzed used an open redirect on YouTube.
- Varied email senders decrease the risk that a SEG or upstream email server will classify emails as unwanted due to reputation. Headers in the emails we analyzed indicate a variety of origins, including regular email accounts, scripts on web servers, and even dedicated email services. The threat actors likely have access to a variety of compromised accounts, and they use SuperMailer’s sending features to rotate through them.
- URL randomization makes it harder to detect malicious emails based on block lists or URL patterns. The threat actors’ phishing pages are set up to work no matter what string is included in certain parts of the URL.
- Reply chains appended to some of the emails may make them more likely to pass SEG evaluation or appear legitimate to recipients. The reply chains are not specific to the individual recipient or stolen from their contacts – rather, the threat actors use one reply chain template for many different recipients.
Although it was a coding mistake that prompted us to investigate this campaign, the combination of tactics shows that it should be taken seriously as a sophisticated threat.
Outlook
We are not certain how long phishing emails with these characteristics will continue to bypass SEGs and reach inboxes. However, the current trajectory is concerning. As more such phishing emails reach inboxes, the chances of users being compromised by those emails increase.