By: Kurtis Nicks
Don't you just hate it when you receive an unexpected email about an EFT payment, asking you to "please see attached"? Well, buckle up, because the latest phishing scam has an interesting twist that leaves its victims more confused than ever. The Phishing Defense Center (PDC) has observed credential phishing campaigns that use a novel deception technique, luring unsuspecting users into a false sense of security after they've given away their Microsoft login information.
Phishing attacks have evolved significantly over the years, and threat actors continue to develop more sophisticated methods to trick users into handing over their credentials. While it's common for these scams to involve malicious attachments or fake login pages, this particular phishing campaign stands out due to the unusual redirection that occurs after the recipient enters their credentials. The clever ruse employed by the threat actor involves sending the user to a seemingly unrelated Google Drive voice recording about catering prices, further muddying the waters and leaving victims questioning what just happened.
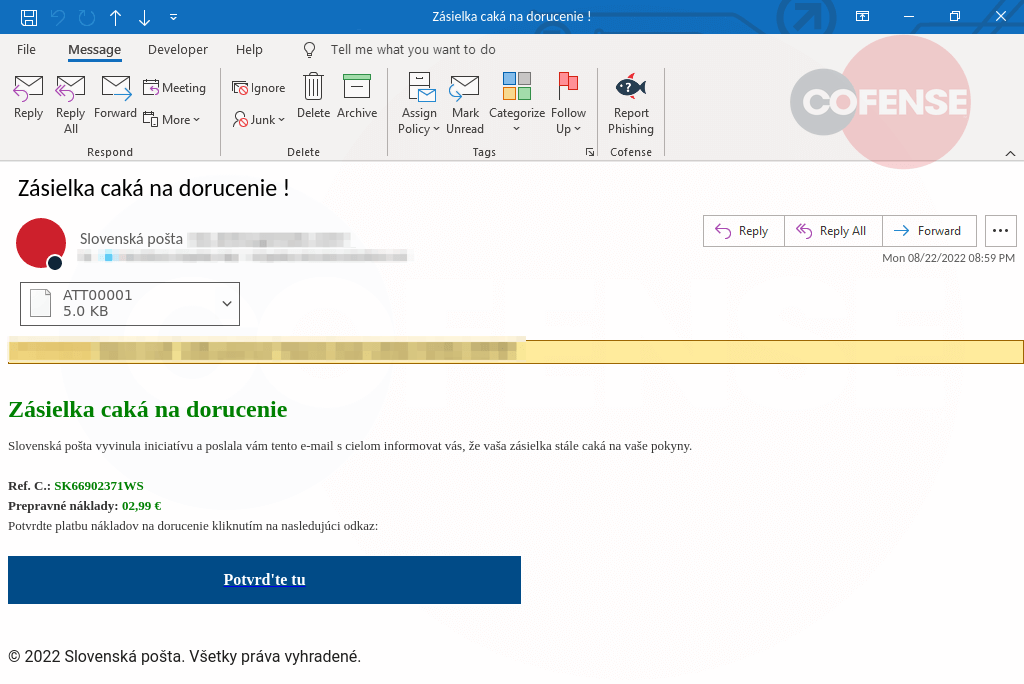
Figure 1: Email Body
To make the phishing email appear legitimate, the threat actor employs several tactics. First, the "From" address is spoofed to appear as if the email is coming from a legitimate source, such as a well-known bank, financial institution or even an internal department. This is often enough to make the recipient curious about the content and compel them to open the attachment. The layout of the email is also designed to look professional, further increasing the likelihood that the target will interact with the message.
The intention behind the email is to pique the recipient's curiosity, which is accomplished by using a subject line related to EFT payments and the vague content requesting them to review an attached file. This entices the user to open the attachment and subsequently be led to the fake Microsoft login page. Once the user enters their email and password, the real deception begins.
The attachment in this phishing campaign serves as a gateway to the fake Microsoft login page. Upon opening the file, users are redirected to the fraudulent page designed to harvest their credentials. An examination of the source code reveals that the threat actor has gone to great lengths to make the login page look authentic, using official Microsoft logos and design elements.
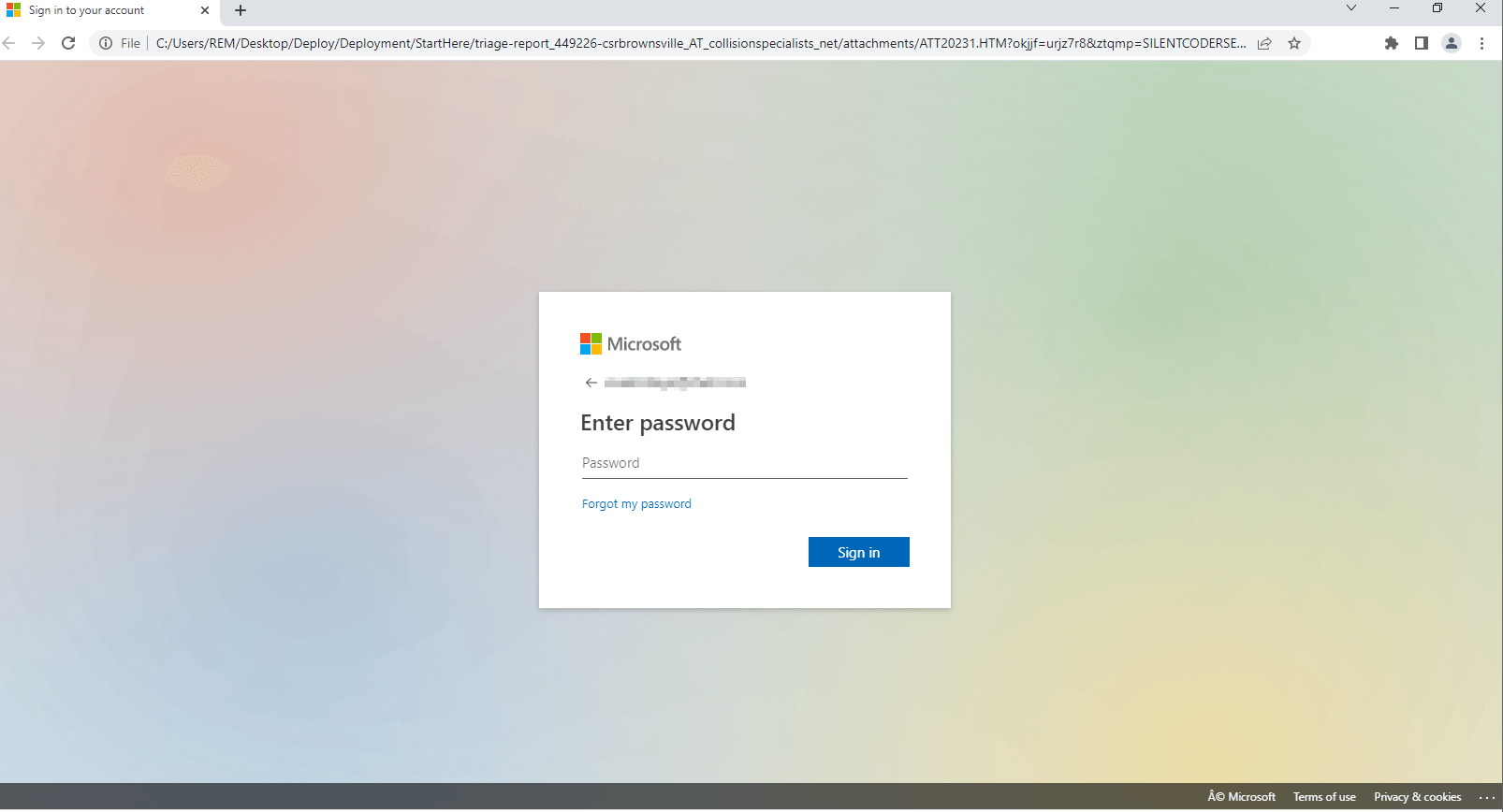
Figure 2: Phishing Page
After the user enters their credentials, they are then redirected to a Google Drive voice recording of a young woman asking about catering pricing. This unexpected turn of events is designed to throw the user off the scent and create confusion, making them question the legitimacy of the entire interaction. The clever use of misdirection showcases the lengths that adversaries are willing to go to in order to maintain the illusion that nothing malicious has taken place.
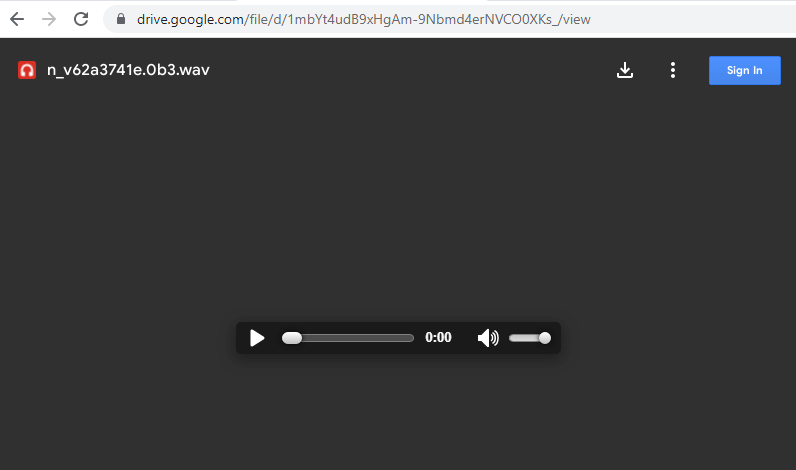
Figure 3: Phishing Page (Post login)
In conclusion, this phishing campaign highlights the evolving tactics of threat actors and the importance of remaining vigilant when dealing with emails requesting sensitive information. Always verify the authenticity of emails and websites, and never provide personal or financial information without being certain of the recipient’s legitimacy. This campaign illustrates how automated systems – such as those identified at the top of this article – fail to outperform humans, and the network effect of people as sensors, spotting and reporting suspicious email With Cofense Managed Phishing and Defense, provided through our Phishing Defense Center (PDC), enterprises benefit from our complete view of real phishing threats.
| Indicators of Compromise | IP |
|---|---|
| hXXp://dnd[.]mb0xffice[.]xyz/main/action[.]php | 193.47.61.212 |
| File Name: ATT20231.HTM MD5: 1cefc6d80e4f1b68ea708aa8fe17dfb1 SHA256: 94306c696ca08f12529dc819899a6aa9dacb7ce0f41cc4f37e62a6c02c634753 File Size: 41524 bytes (40K) |