By: Ronnie Tokazowski
Over the last few months, analysts at Cofense have been trying to gain more insights into the world's most lucrative cybercrime, Business Email Compromise. In July, the team set out to see how many responses a scammer would engage with from a potential victim before making their ask.
This time, Cofense analysts purchased $500 worth of trackable gift cards to intentionally give to scammers in the hopes of discovering what happens once scammers receive these funds. With gift cards continuing to be one of the more difficult cash-out methods to track, due to the complexity and locality of the information, we had no idea what we would find.
Something that stood out through this research was how quickly these scammers move funds.
In all but one case, each gift card was stolen, re-sold, and used for purchases within 24 hours. And while scammers do have preferences for the brand of cards they target, they are willing to pivot depending on the cards available. Based on the research, scammers prefer to use in-store cards over credit card gift cards.
So, from counterfeit toys sold in Myanmar to digital greeting cards to companies that don’t appear to exist and purchases for energy companies, let’s dive into the report.
Introduction
Business Email Compromise (BEC) continues to make headlines with arrests across the world and losses in the billions. The roots of BEC originated from Nigerian prince scams (419 scams), where attackers found new, creative, and innovative ways to target consumers each day. Attackers are constantly adding new types of fraud to their arsenal as security practitioners, law enforcement, and organizations change their defenses against these tactics. While many of these scammers operate in small groups, many are part of larger organized crime groups, international gangs, and criminal syndicates.
While the machinations on how dozens of tactics and objectives of these attacks are well known, one of the biggest "unknown” aspects of BEC is a deeper understanding of how gift card fraud fully works.
Based on empirical evidence captured by defenders around the world, we know that once gift cards are stolen, they are sold locally or remotely via gift card exchanges. For gift cards sold remotely, many appear to be sold on cryptocurrency exchanges, where cards can be sold for Bitcoin, Ethereum, or other forms of digital payments. While many of the remotely sold gift cards are exchanged for 80-85% of the face value, cards can be purchased locally for around 50% of the face value, depending on the country. While a fuller picture of how gift card fraud works are limited to the organizations and institutions who manage this infrastructure, we do know current losses are in the hundreds of millions of dollars.
The concept of our research project was based on a simple premise. What gift cards can be purchased, tracked, and used to engage with these attackers to help identify how, where, and when they’re used? With these concepts in mind, we purchased $500 in gift cards and engaged with 54 live BEC attacks over the course of 5 weeks to evaluate what type of insight and usage patterns we could uncover.
In addition, we discovered that most cards were used on the same day they were stolen, making the mitigation of this type of attack extremely difficult. Many financial institutions have anti-money laundering (AML) controls in place so that money can be reversed and recovered under certain circumstances. This normally results in a 72-hour “safety window” of asset recovery; however that window is closing, and scammers are aware of our inefficiencies. While it’s quick and easy to write the losses off, this does nothing to address the root cause and simply perpetuates the issue.
Going into this project, we didn’t know what we would expect to see or ended up with more questions than answers. Let’s look at the fraud.
What Does BEC and Gift Cards Have to do With Each Other?
Traditionally, Business Email Compromise (BEC) is straight forward. In these attacks, a scammer impersonates a C-level executive within the company to convince unsuspecting users to make urgent wire transfers to vendors, organizations, and other accounts that they control. As awareness of this tactic grew, organizations adapted and increased their diligence against these types of attacks. Attackers took notice and started to adjust their attack methods to include payroll diversion, invoice fraud, check fraud, and the topic of this research: gift cards.
Gift card scams play out like other types of BEC scams. Scammers ask unsuspecting employees to run tasks or errands under the guise of “helping out.” Within Cofense, we have seen dozens of different email lures, such as holiday surprises for employees, rewards for employee performance, or gifts for the CEO’s family members. We have also seen templates including a forgotten birthday or one last gift card for a sick and dying relative. While many of these attacks stay within an email, some scammers will ask for the phone number of the victim to converse with them while they are purchasing the cards or even start as SMS text messages.
Once the unsuspecting victim has taken the bait and responded to the scammer, they will be asked to go to a local store to purchase gift cards, often in $100 or $500 dollar denominations. After the cards have been purchased, the scammers ask the victims to scratch off the back code and send them pictures of the cards. Once received, the scammers confirm receipt and push the victim to send more cards or money over time.
Engaging With Scammers to Get Information from Them
The key to having successful scammer engagement is to respond to the initial email as if you had no idea you were about to be scammed. The actual context is dependent on what type of scam they are attempting, and what angle they are playing to entice their victim.
Most gift card scams start out with the CEO or another person in authority asking for help running a “task,” however scammers withhold the task until their email is acknowledged. Once a response is received, the scammer divulges what the “task” is, why they are asking for help, and why they can’t do it themselves.
Based on the knowledge of how these scams work and the communication patterns that these attackers are used to seeing from actual victims, we can socially engineer the scammers in an unsuspecting manner. For example, if a scammer is expecting a response to the question “do you have spare time at the moment?” we would provide a simple answer like “Sure, how can I help?”
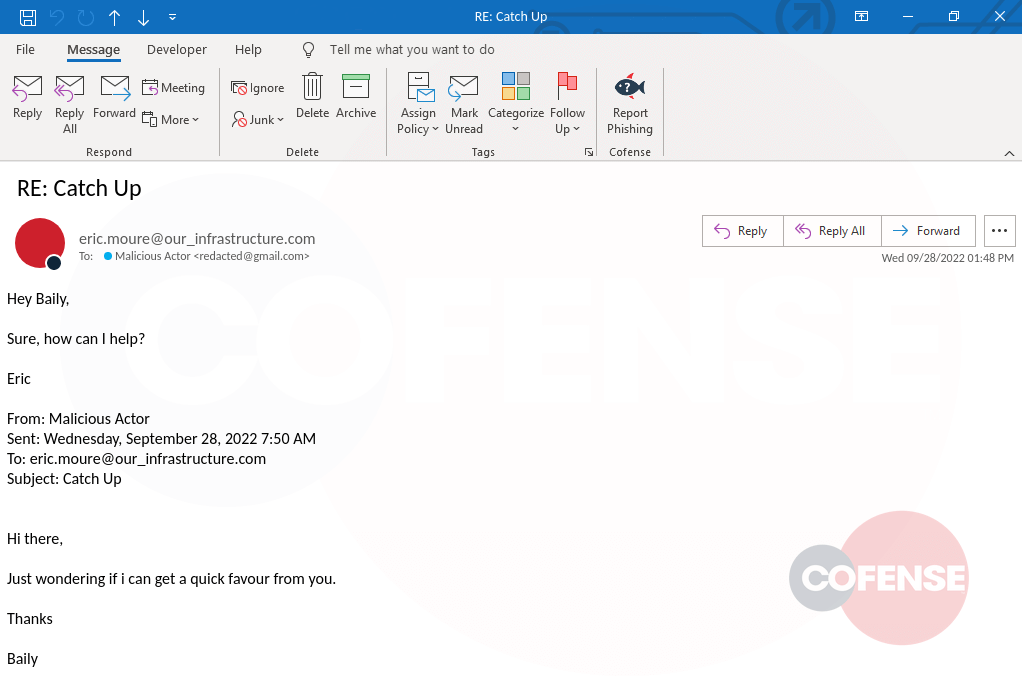
And just like clockwork the scammers respond right back.
Cards Scammers Want vs. Cards Scammers Get
In order to conduct our research, we used general branded credit cards which can be used as gift cards. As strange as it may sound, scammers were extremely hesitant to take these cards and would often push for store-specific cards, such as Apple, Steam, or Google Play cards. It took a surprising amount of work to make them pivot from their “normal” methods of gift card fraud. However, we were able to get a surprising number of them to accept our trackable gift cards.
In addition, we do not have full visibility into what happened to the gift cards after they were sent to the scammers. The gift card can take many routes after being sent, and here are a few possible scenarios.
- They are sold on gift card to cryptocurrency exchanges. Buyers could be legitimate persons looking to save a couple dollars on cards or criminal syndicates who are using cards as a way to launder stolen cryptocurrencies. Both have been publicly observed.
- Stolen cards could be sold locally for a smaller percentage, as many people don’t fully understand cryptocurrency. In one of our engagements, we know the card was sold locally.
- If scammers are part of larger groups, they may have ways to launder specific cards, thus turning larger profits.
While we focus on one small piece of gift card fraud, we acknowledge that there are many other areas of gift card fraud that are not fully understood. We know cryptocurrency theft, re-shipping scams, in-person purchases, and many other angles of gift card fraud exist. In addition, a fuller scope view of how gift card fraud works is held with card distributors and brokers, and more extensive collaboration is necessary in order to facilitate a better understanding of the gift card ecosystem.
Why Do Scammers Want Gift Cards?
Scammers are commonly tricking unsuspecting people into giving away their hard-earned money. One common tactic that scammers use is requesting payment through gift cards. But why do scammers want gift cards? The answer is simple: gift cards are essentially untraceable and easier to convert into cash than other forms of payment. Gift cards can also be easily sold or traded on the black market for cash or other goods. Additionally, gift cards can be bought in large quantities without raising suspicion, allowing scammers to maximize their profits. It is important to be aware of giving out gift card payments to untrustworthy sources. So, the next time you're asked to pay via gift card, remember that scammers have two motivations: staying off the radar and making money.
Engagements
First Engagement (GC1)
For this engagement, the attacker assumed multiple identities throughout our correspondence with them. Initially, the actor assumed the identity of “Ian William” and later pivoted to the display name “Ian Foy.” This happens frequently with scammers as they engage with multiple targets during a specific engagement. Both accounts will be described as “Ian.”
In the initial phish, Ian asked if we could do something for them right away. Ian was in a meeting with limited connectivity and asked if we could purchase 5 Steam gift cards, an online platform for purchasing video games, for a total of $1,000 (5x$200). To set up the bait, we told Ian that Visa cards were the only ones we could purchase and asked if we could use those instead of the requested Steam gift cards. Ian confirmed, and we provided a single $25 dollar gift card. Ian kept asking if there was something wrong with the transaction as they were expecting multiple cards, however we only provided one gift card in this engagement. The total interaction and engagement lasted two days.
We do not have visibility into how the card was laundered, however the gift card was later used at Amtrak, a railway company, on June 29, 2022. Since this card would have been considered “stolen” under normal circumstances, we provided Amtrak with the card details. No further information was provided by Amtrak as to what the purchase was for.
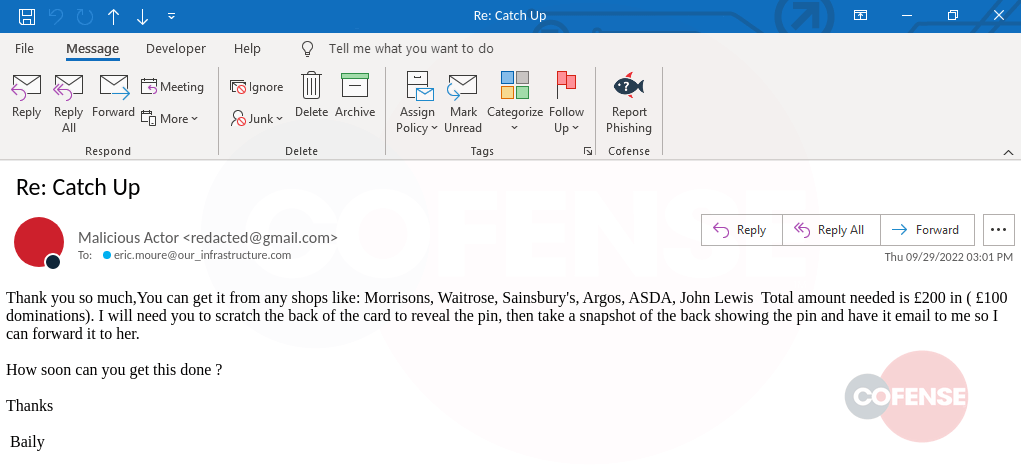 Image 3. Amtrak purchase from gift card
Image 3. Amtrak purchase from gift card
Second Engagement (GC5)
In this engagement, the BEC actor impersonated our CEO, Rohyt Belani, and attempted to steal funds from one of our senior researchers. The specific researcher targeted has spent the last 7 years raising awareness around how all things Business Email Compromise works and instantly knew it was a scam. Instead of letting the scam play out, Cofense used this as a chance to gain more information from the scammers and see if more information about the attacker could be found.
While the scammer initially tried to scam the researcher, they quickly turned the engagement back on the scammer and converted the scam attempt into an interview opportunity. After providing enough insights to the scammer that Cofense was well aware of how these scams worked, the scammer decided to open up and went off-script. We do acknowledge that it’s entirely possible that the attacker was still lying to us, however they did confirm that yes, they were in Nigeria. The scammer went into further detail about how he became a scammer, with one of the primary reasons being limited opportunities in Nigeria. Based on extensive research into Nigerian culture, economy, geopolitical status, and unemployment, this is an accurate sentiment shared by local sources.
Prior to scamming, he was a tailor and did other odd jobs just to survive. As a tailor he made shirts, and for the shirts he made, he would profit around #500 Naira, or $1.20 USD for each shirt. He also mentioned that he was 50, did not have an easy life in Nigeria, and all of those things combined led him down the path of scamming. And while many choose the scamming life as a way to make quick or fast money, there is much more going on than an over-simplification of “bad people doing bad things.”
We didn’t want to leave the scammer empty handed as he provided insights into the underlying ecosystem for us, so we provided them with a gift card to them for their efforts and purported honesty. He mentioned that he would be selling the card locally because he didn’t have access to any other exchanges, where he could have gotten a higher dollar amount.
After selling the card, it was used to purchase five instances of TikTok Live via the Google play store. The information was passed over to TikTok in case the card was used as part of another fraud scheme and no further information was provided to Cofense.
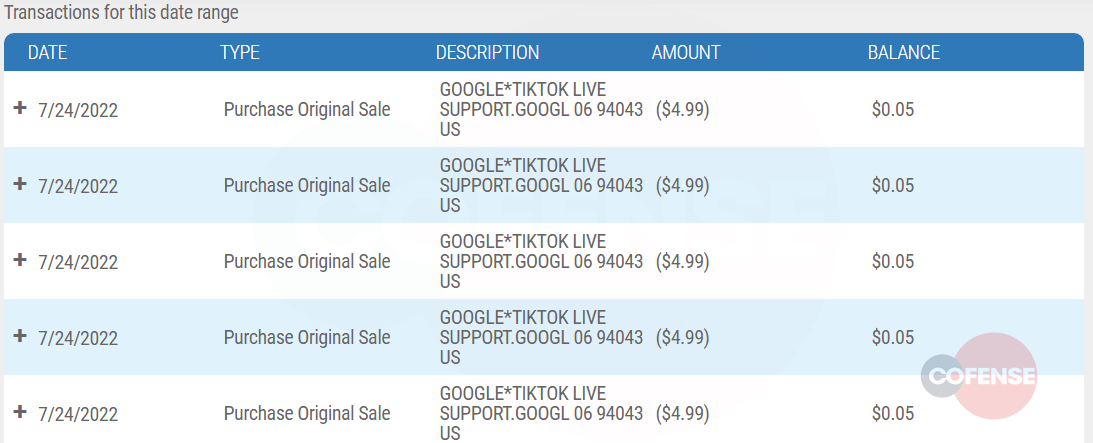 Image 4. TikTok Live purchases
Image 4. TikTok Live purchases
Third Engagement (GC7)
In this engagement, the attacker assumed the identity of “Andrew Quinton.” Andrew requested 5 AMEX gift cards to the tune of $500 each and asked if we could leave for the store soon. Once it was verified that a Mastercard gift card could be purchased, a card was sent to Andrew. Andrew asked “What’s going on” when no more cards were sent, however the attacker still successfully cashed out the card.
While researching the origins of the purchase on this card, we were quite surprised with what we uncovered. To get started, the retailer's name for this gift card was “BKIDZ” in Sheridan, WY. $25 was directly purchased emptying the balance of the card.
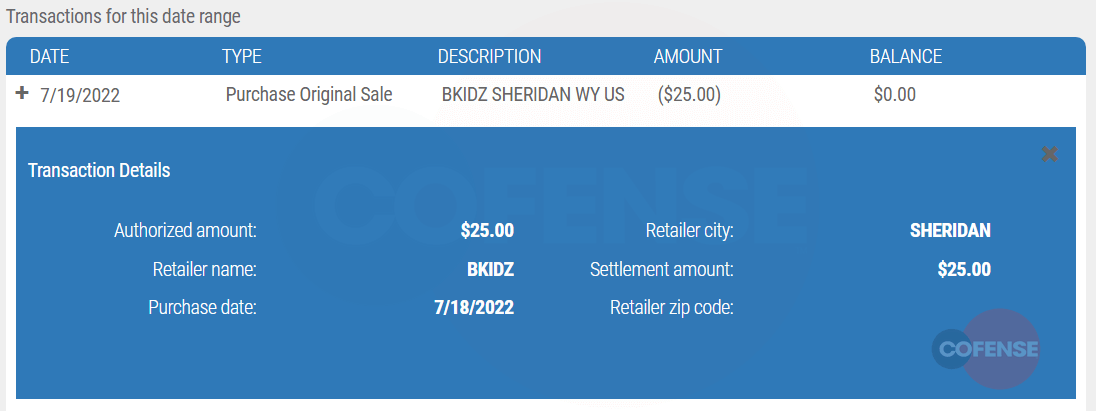 Image 5. Purchases to unknown retailer “BKIDZ”
Image 5. Purchases to unknown retailer “BKIDZ”
When researching the brand BKIDZ, limited information was available for the origins of the transactions in Sheridan, Wyoming, and found no references online that led us to a solid company. However, during our research we did find branded children's toys using the “BKIDZ” logo for the online marketplace KhitZay, an online store front that sells counterfeit toys in the currency of Myanmar Kyat.

One instance of counterfeit goods being sold directly under the BKIDZ brand was Marvel toys from Habsoro, with the item number E4353. While some of these counterfeit items are being sold on eBay and Ali Express, many of the counterfeit items are being resold on KhitZay.
 Image 7. Logo used on ”KhitZay” store using the” BKIDZ” branding
Image 7. Logo used on ”KhitZay” store using the” BKIDZ” branding
One instance of counterfeit goods being sold directly under the BKIDZ brand was Marvel toys from Habsoro, with the item number E4353. While some of these counterfeit items are being sold on eBay and Ali Express, many of the counterfeit items are being resold on KhitZay.
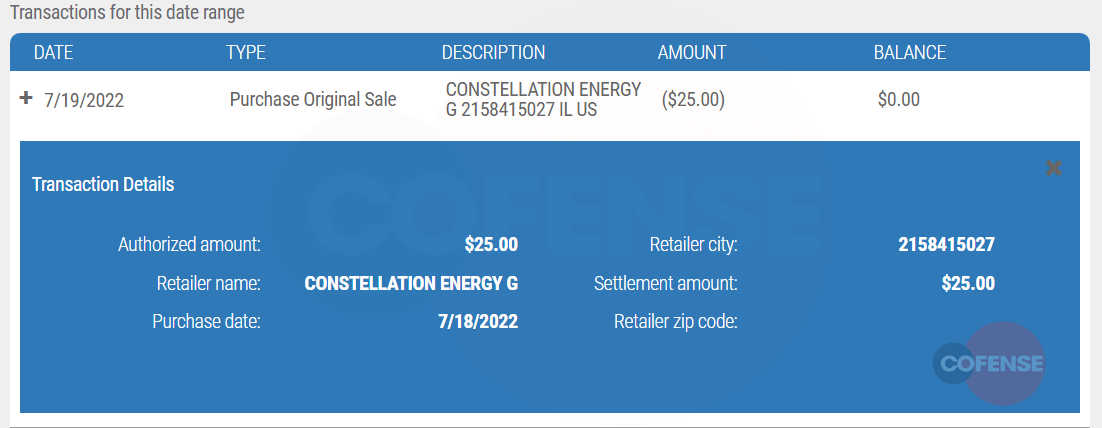 Image 8. Unknown purchase at Constellation Energy in Chicago, IL
Image 8. Unknown purchase at Constellation Energy in Chicago, IL
Fifth Engagement (GC11)
In this engagement, the attacker used the name “Amanda Johnson,” and the scammer wanted 10 pieces of Amazon gift cards for $200 each ($2,000 total). Initially, the scammer came from a sudenlink[.]net account, however after the initial email the scammer switched to a Gmail account with the display name of “Mary Webre.” We are unsure as to why the scammers decided to change the display name mid campaign.
After verifying that a Visa gift card could be used, one $25 dollar card was provided to the scammers, with the scammer confirming the receipt with an “Alright.” When no card was sent the scammer bumped the thread multiple times, and the following day they responded in a formal manner asking for a follow-up on the gift card. This was the last response from the scammer.
On August 6th, 2022, this card was used at “PF GSHOP” in New York.
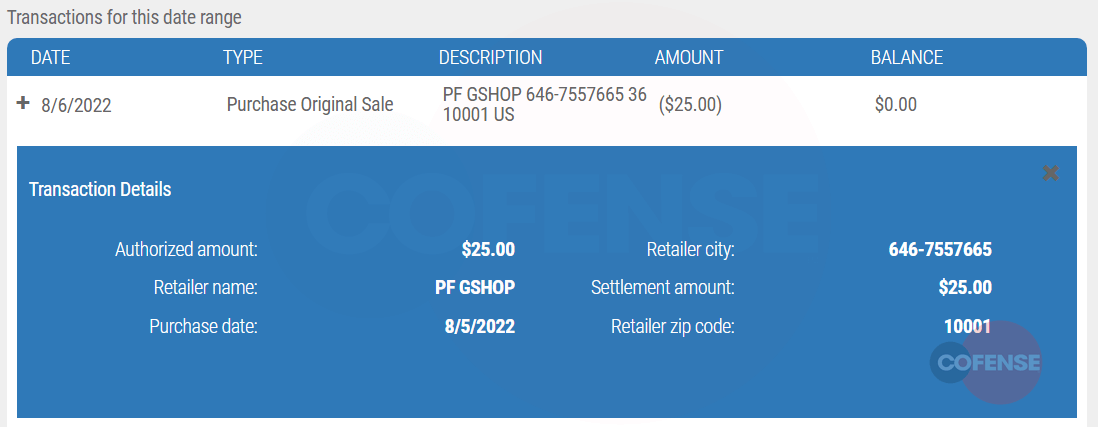 Image 9. Purchase at OneUp Trader
Image 9. Purchase at OneUp Trader
Sixth Engagement (GC14)
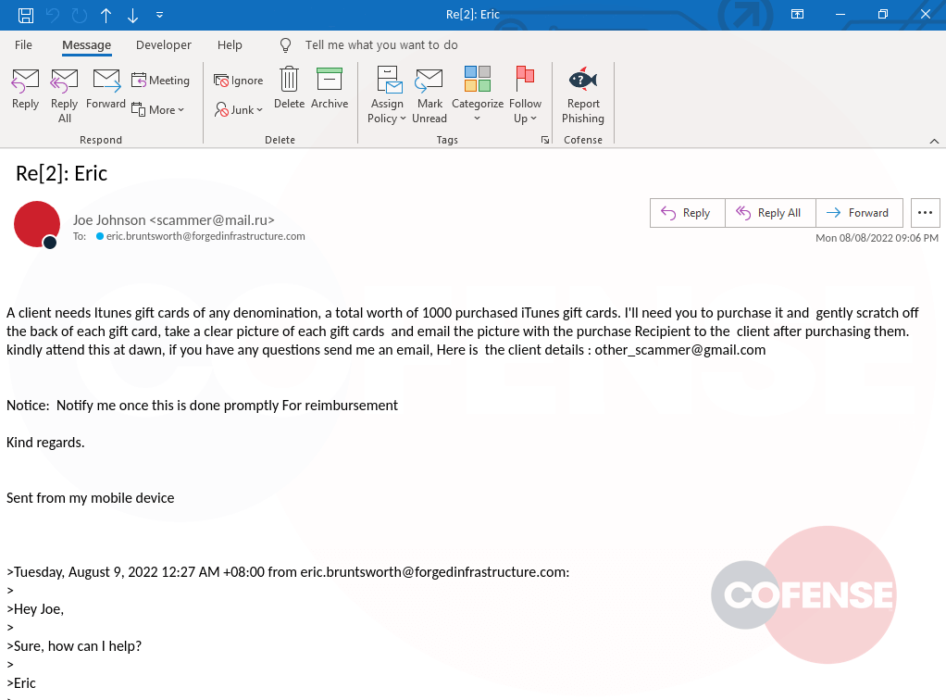
In this engagement, scammer “David Johnson” asked if we had some spare time and we said of course, how could we help. David mentioned that a client needed iTunes gift cards of any denomination for a total of $1,000. David’s instructions were that once the cards were purchased, to gently scratch off the back of each card, to take a picture of the cards, and email a clear picture to the client at a different Gmail account, which we will refer to as “Lim.”
At this point we had CC’d Lim on the email thread, and the scammer was now going under the name of Lim, different from the initial name of David. We tried to convince the scammer that all of the stores were sold out of iTunes cards, and they instructed us to instead purchase Amazon, iTunes, or Google Play gift cards. After telling them that four stores were sold out, David still insisted on purchasing iTunes gift cards online.
Finally, after convincing the scammer that we were only in possession of cash, Lim “asked their superior” and was instructed that Visa cards would be acceptable. After sending only $25 dollars, Lim asked if there were any bitcoin vendors in the area, as we only sent $25 of the $1,000 requested. Lim later bumped the thread asking if we could load the $25 dollar card with $900, and this was the end of our contact with the scammer.
For the gift card in this transaction, unknown persons purchased $25 worth of products with GivingLi, a greetings and gift card company. While we do not have visibility into the product or good that was purchased, historically we have seen Yahoo Boys and other scammers sending cards and flowers to romance victims to keep them in the scheme for longer periods.
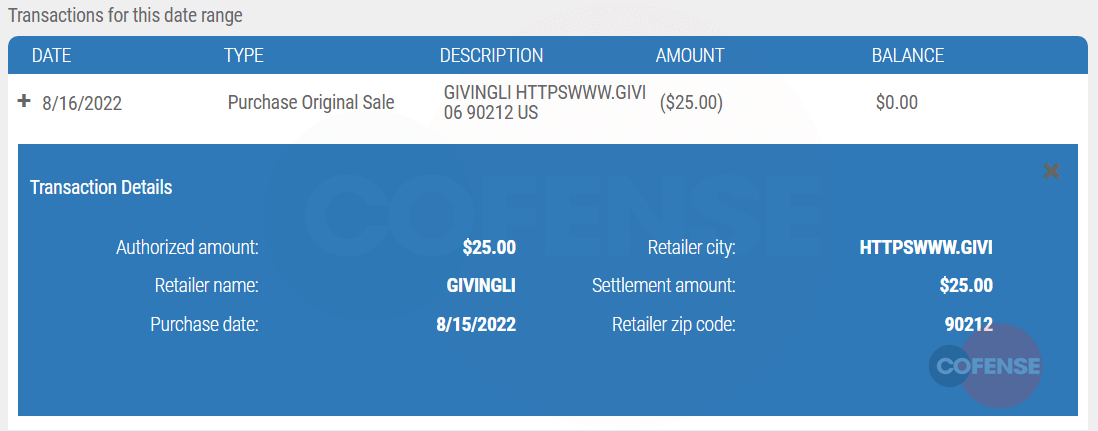 Image 10. GivingLi transaction
Image 10. GivingLi transaction
Seventh Engagement (GC15)
In this engagement, the scammer assumed the fake persona of Jared Russel. Jared said that he trusts he can count on us to keep gift card purchases as a surprise because he wanted to surprise the staff. Keeping this between us and Jared, he wanted to know how quickly we could purchase the cards and what local store could be used to make the purchase. Jared suggested Walmart Visa cards, American Express, or Vanila Visa gift cards “since we can use them almost everywhere.” After conversing back and forth to confirm what should be purchased, Jared confirmed that four pieces of Visa prepaid gift cards at the value of $500 ($2,000) should be purchased.
One of the interesting things we noticed is that we purchased the gift cards prior to the engagement and the scammer was quick to identify this discrepancy, however we just said that the credit card machines were giving the incorrect dates on the receipts, and this was enough for the scammer to accept the difference.
For this credit card transaction, unknown persons purchased $25 dollars of something from a company under the name “DEBEBTECH LLC.” At the time of writing no information about DEBEBTECH exists, even on Google or Bing.
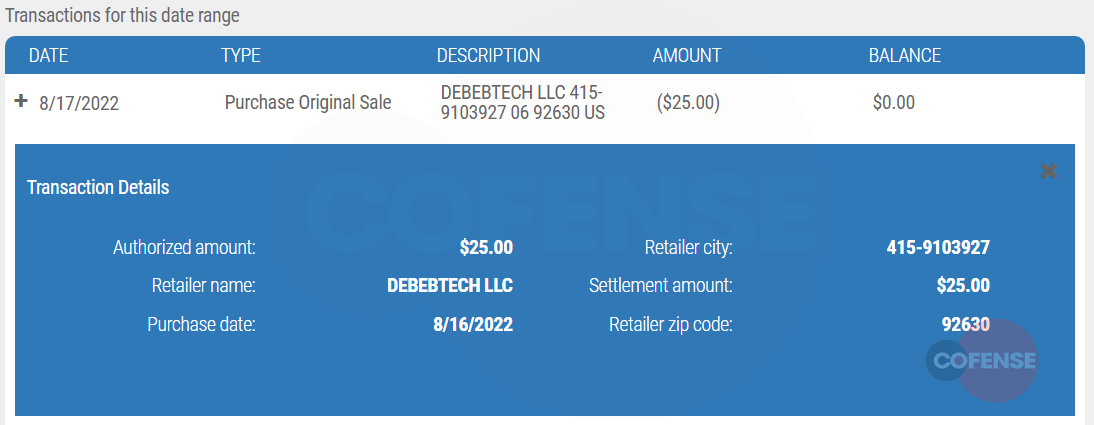 Image 11. DEBEBTECH LLC purchase
Image 11. DEBEBTECH LLC purchase
Eighth Engagement (GC16)
While most scammers assume one persona during an engagement, this scammer went through four different names for the entirety of the campaign. John Slattery, Jerry Williams, Roger Jenkins, and Stephen Timm all asked about gift cards in the same exact thread. This commonly happens when scammers get confused and use different display names during engagements, as they will sometimes engage with multiple companies per account. In addition, the scammer used six different subject lines during this engagement.
In this campaign, Jer..Rog....the scammer asked us to head to the nearest store to find and purchase gift cards. The cards were for their presentation on data analysis and evaluation and wanted to know how quickly we could get this done. After confirming that we could run to the store and pick them up, the scammer asked if we could purchase Target or Google Play gift cards. There was a lapse of 30 minutes between our next response to the scammer, which led to the scammer asking if we were there, if we were talking to them, and what was up. They were extremely pushy, and after saying that we didn’t like being yelled at, Jerry came back and said that he wasn’t yelling, and just that he didn’t have much time on the presentations.
Once a single card was provided back to the scammer, they continued being pushy, asking how many of the $25 dollar cards were able to be purchased.
After the card was provided to the scammer, the card was used at a company called FLUZ AWAY. Fluz is an application that runs on your phone that allows you to receive points and cash back on products and services that you use. Money can be loaded into the app then used at these locations for purchasing products.
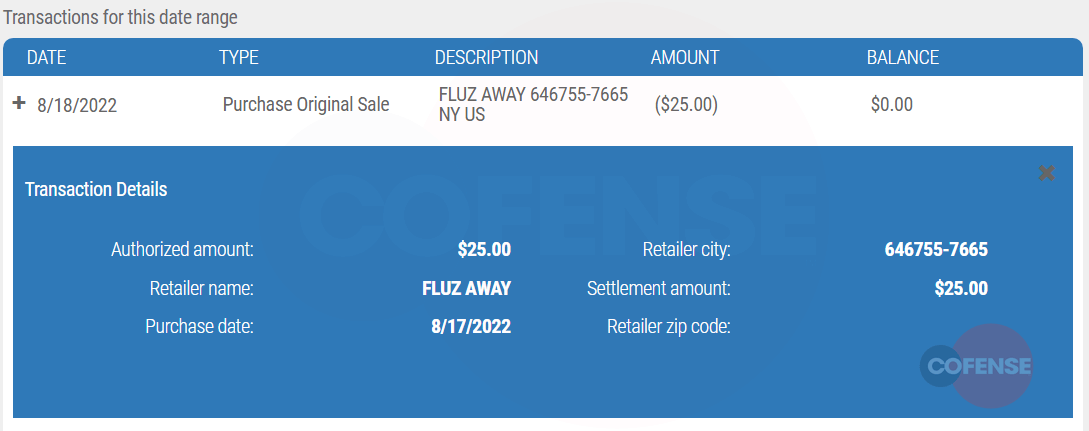 Image 12. Fluz Away purchase
Image 12. Fluz Away purchase
While researching the retailer “FLUZ AWAY,” it appears that the company has many complaints with the Better Business Bureau (BBB) about multiple values of gift cards being purchased and funds being stolen. Based on comments from BBB, victims of puppy scams, car rentals, and check fraud.
Ninth Engagement (GC18)
In our 9th and final engagement, the email came from CHIEF EXECUTIVE OFFICER (caps included) where the scammer asked if we had anything on our plate, as they had a task for us. They wanted us to “drop your phone number so I can concise you about it.” After telling the scammer that we didn’t have our phone with us, they asked if we could purchase an eBay gift card for a business prospect. After “running to the store,” we informed the scammer that they didn’t have any eBay gift cards, and the scammer asked if they had Steam or Apple gift cards. We denied their request, telling them that they did not have these cards. The scammers asked for a Visa Vanilla gift card, and we provided a Vanilla Mastercard to the scammer. Eventually the scammer confirmed the receipt of the $25 dollar gift card, and after ignoring a few more emails they lost connection.
And contrary to every other transaction previously discussed, the transaction on this gift card was the most normal. Unknown people purchased $25 worth of goods on Amazon.
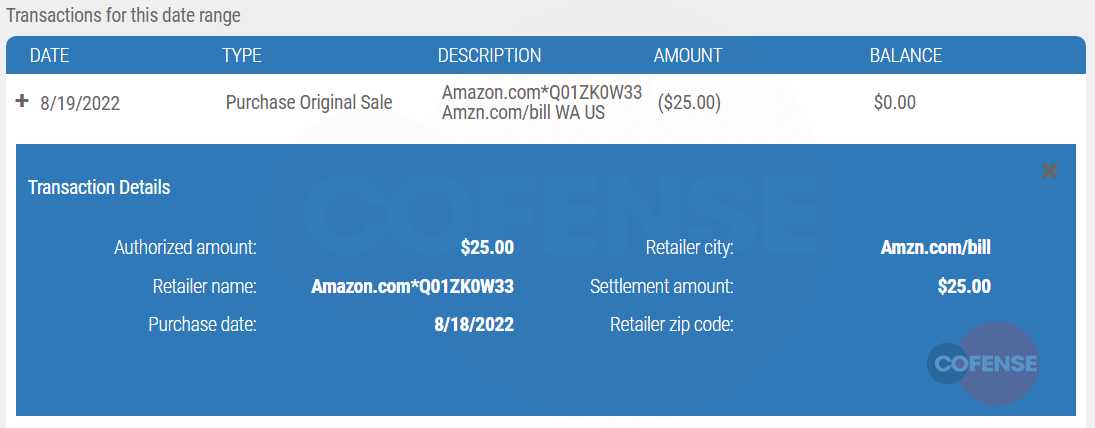 Image 13. Amazon purchase
Image 13. Amazon purchase
Other Findings and Conclusion
When we decided to kick off this research, we had no idea what direction this was going to take. Using gift cards to purchase things on Amazon seemed like a normal expense, however stumbling onto counterfeit toys sold in Myanmar, digital greeting cards, companies that don’t appear to exist, and purchases for energy companies were not even considered. While we did find some very interesting things about what happens to gift cards once they’re stolen in BEC attacks, we ended up with many more questions than answers.
And as counter intuitive as it may sound, it was especially difficult to convince scammers to take the gift cards that we had. They had pre-defined scripts in $100 dollar denominations, and if something deviated out of that it really seemed to throw them for a loop. In addition, timing of the receipts was also another metric that scammers looked for, and if something was outside the scope of the normal time frame scammers were very hesitant to use them.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
All names shown above have been changed to protect the privacy of the user.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.