By: Dylan Duncan
Threat actors are using employee’s annual responsibilities like open enrollment, 401k updates, salary adjustments, and even employee satisfaction surveys as lures to steal credentials. Most of these responsibilities tend to fall towards the end of the year, which is subjective to the calendar the employer uses.
Employees typically expect, and in some cases, look forward to receiving notifications and even emails at least once a year that fall into these categories. This makes social engineering attacks that use these types of lures extra deceptive since employees often expect to interact with emails. This report brings awareness to these types of social engineering lures by highlighting a few examples of phishing emails found in the inboxes of intended targets.
Employees often anticipate or even look forward to receiving annual updates like the ones covered in this report. It’s important that organizations have a consistent schedule so employees know when to expect these types of notifications, but it’s equally important that employees are made aware of how these updates can be used maliciously. These tasks generate emotions for employees whether they are considered extra work, an exciting change in finances or benefits, or even a task to be completed urgently.
This added emotion can cloud even the most well-trained employee’s judgment when it comes to phishing emails. The examples in this report use many different tactics to force employee interaction like QR codes, malicious attachments, or just the common phishing link. Regardless of the tactics, all the emails below reached their intended targets with nothing left to prevent credentials from being stolen except for the employees’ education on phishing attacks.
Open Enrollment
Open enrollment is used as a phishing lure year-round, but the volume tends to increase towards the later part of the calendar year when most companies start their open enrollment. The reason we see this lure used year-round is due to companies with fiscal years starting the open enrollment process on dates that align closer to the end of their specific fiscal year. This lure is appealing to threat actors, because employees may be anticipating an open enrollment email in their inbox if sent at the right time of year.
The email below (Figure 1) is an example of a phishing email that reached the intended target during December of this year. It includes a ZIP archive attachment that contains an HTML file used to steal login credentials. Emails using this theme vary greatly but typically involve some sort of attachment or link that leads to some form of credential phishing. Like the example below, the emails can appear very realistic and even include recipient information. For instance, the email includes the name of the company that the recipient is employed with in the subject, attachment, and email body.
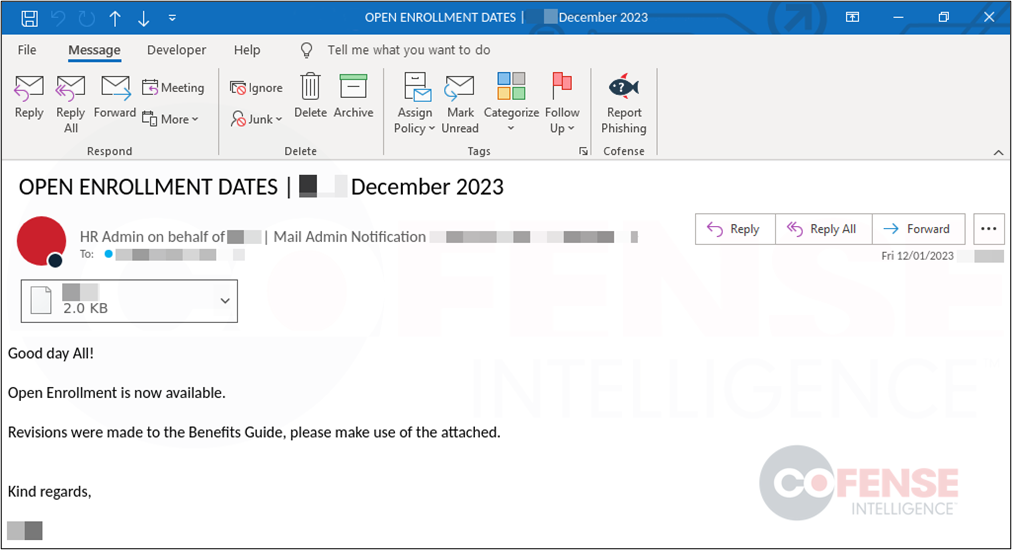
Figure 1: Real Phishing Email using Open Enrollment as a lure.
401k Annual Update and Statement
Retirement benefits can be a successful lure used in phishing emails, likely because of the emotions they generate for recipients. 401k notifications, updates, statements, and possible contribution increases can be exciting or at the very least more appealing for recipients to receive in their inbox rather than your average phishing lure. These types of lures can be seen year-round with the most popular 401k-related lure being increased contribution statements.
Figure 2 below is a phishing email that uses a 401k account update and annual statement lure with an all too familiar credential phishing tactic, a QR code. The use of QR codes has drastically increased throughout the year with the most common trend being an uphill line on the volume charts. In this email, the QR code leads to a malicious link that is phishing for credentials but there are many ways threat actors are abusing this evolving tactic. Cofense Intelligence recently published the Strategic Analysis Top Characteristics of a QR Code Phishing Email that breaks down the different ways QR codes are used in phishing emails.
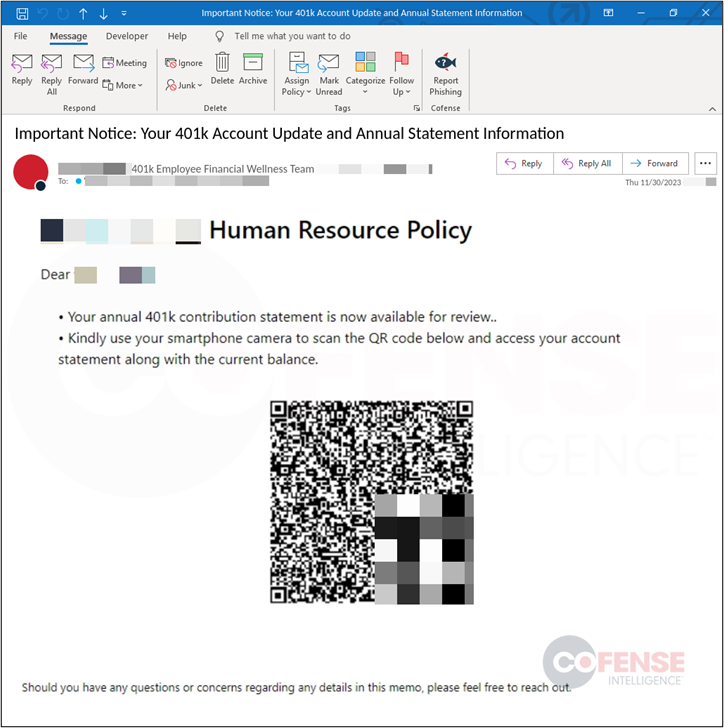
Figure 2: Real Phishing Email using 401k Update as a lure.
Employee Assessments and Satisfaction Surveys
Employee assessments and surveys are utilized by organizations all over to determine employee satisfaction, motivation, effectiveness, job performance, and various other areas. This feedback is useful in leading a company’s direction so that it may further increase an employee’s quality of life. As such, there is usually a lot of pressure for employees to complete these surveys and in a timely manner, which makes this a prominent phishing lure. Threat actors have been seen sending phishing emails referencing employee assessment reports, satisfaction surveys, and other anonymous surveys a victim might expect to receive from their employer.
The phishing email in figure 3 spoofed a human resource department sending out a fake access performance report. The email goes into details of the employees’ responsibilities to complete the report and even mentions how it is required, which may be the case for some organizations. Credential Phishing attacks like this one can be dangerous since any organization that does require employee assessment’s may be similar to this one, adding to the legitimacy of the social engineering behind this threat.
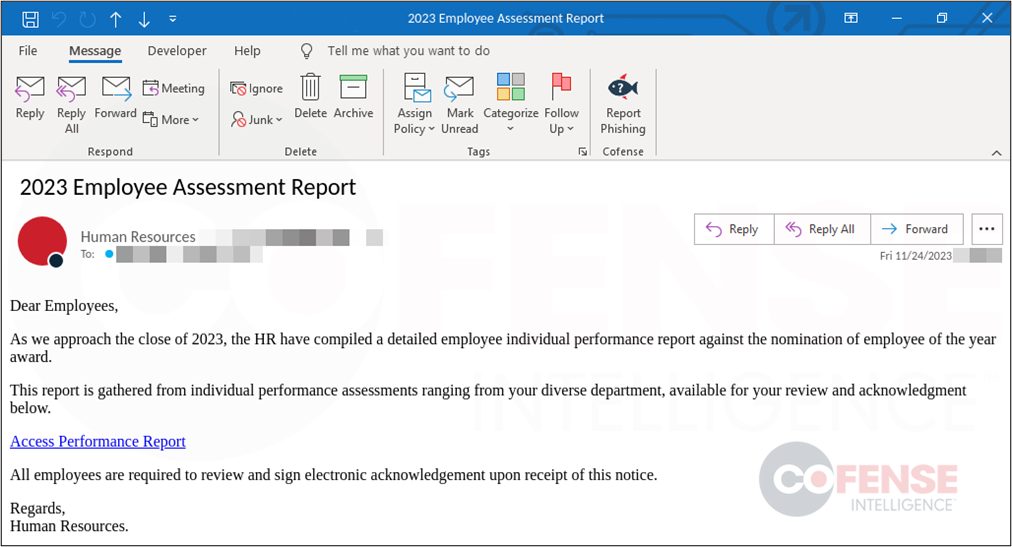
Figure 3: Real Phishing Email using Employee Assessment as a lure.
Compensation Increases and Adjustments
A more attractive phishing lure seen throughout the year is compensation increases or adjustments which employees would be more excited to receive in their inbox. We see these lures year-round, and the mention of payroll increases and bonuses creates a sense of enthusiasm from victims which could fog judgement. Pay raises, promotions, holiday bonuses, and any other ‘life impacting’ update are fair game for threat actors to utilize within their campaigns.
Figure 4 is an example of a phishing email referencing salary increases, dividends, and benefits updates. The campaign uses a QR code to lead employees to enter their email login credentials into a phishing site on their smartphones. Combining the use of QR codes with an enticing theme like salary increases can lead to a potentially successful phishing attack.
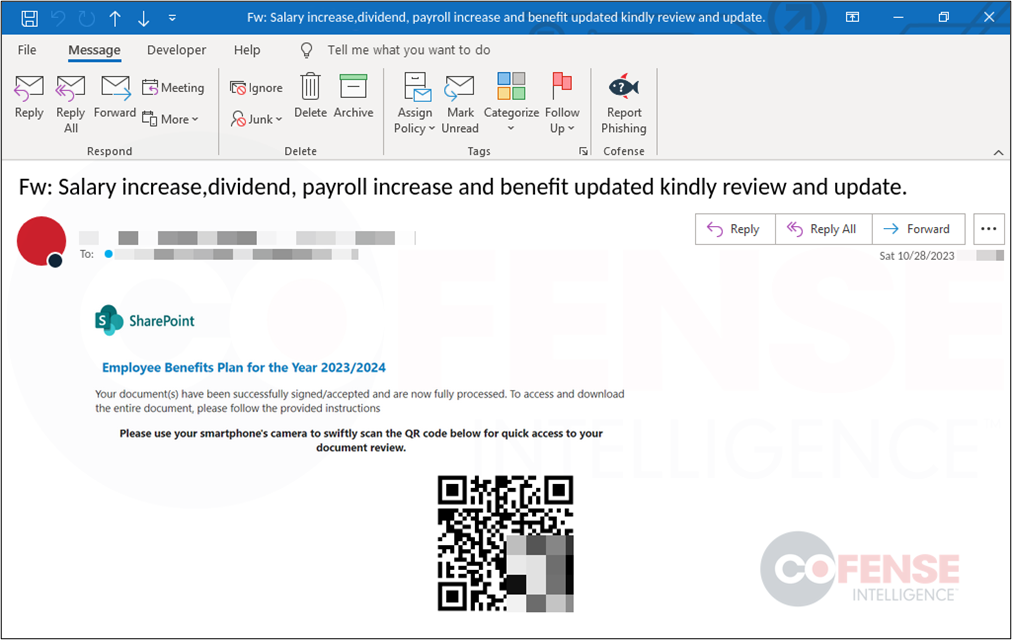
Figure 4: Real Phishing Email using Salary Increase as a lure.