By Schyler Gallant, Alex Geoghagan, Cobi Aloia, Cofense Phishing Defense Center
The Cofense Phishing Defense Center (PDC) employs expert Threat Analysts to analyze emails on behalf of enterprise customers across the globe, in various industries, who are analyzing phishing attacks delivering malware. To help keep up with evolving tactics and top ongoing threats affecting real customers, the PDC has created a breakdown of the top five malware families we have seen across the Managed Phishing Detection and Response (MPDR) customer base over the past thirty days. If you have any interest in learning more about how your organization can be protected by our expert Cofense Threat Analysts, please contact us for additional information.
Top Malware Families in April:
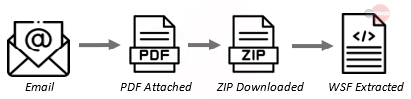
1. QakBot – QakBot is a modular banking trojan with worm-like features that enable its propagation across a network. Once installed, it will use a man-in-the-browser technique to harvest credentials. QakBot has also been known to deliver other malware. The campaigns delivering QakBot re-use legitimate emails to deliver either embedded URLs or attached PDF documents with embedded URLs.
- Subject: Subjects for emails that delivered QakBot for the month of April were typically replies and so they have varied subjects.
- Attachment: Most deliveries of QakBot were done using an attached PDF file this month.
- Behavior: After the victim interacts with PDF links, a WSF file is downloaded which when run will nest in system processes and grab DLLs/Dat files.
- Brand: Re: // FWD // Replies
- Infection Chain:
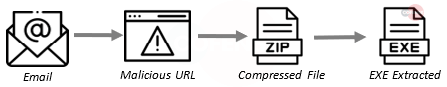
2. Remcos – Remcos was originally a remote desktop connection tool that has since been repurposed as a remote access trojan capable of taking control of a user’s system. Its chief capabilities include key logging, information stealing, and audio/visual monitoring.
- Subject: A majority of the deliveries of Remcos were styled to appear as if they were Judicial summons/correspondence and were predominantly in Spanish.
- Attachment: Remcos is mostly delivered using an infection URL instead of an attached file.
- Behavior: Once Remcos is unpacked from the archive and run it will stay as an active process and provide backdoor access to the machine, which can then be used for a variety of malicious tasks.
- Brand: Legal // Spanish
- Infection Chain:
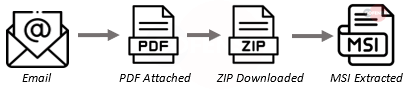
3. Grandoreiro – A banking trojan targeting Latin America countries, written in Delphi. Uses techniques such as remote overlay for financial theft, with the added ability to log keystrokes, capture clipboard data, steal cookies, and more.
- Subject: The subjects of emails delivering Grandoreiro had some variation but were usually about unpaid traffic tickets or account statements.
- Attachment: The majority of Grandoreiro deliveries were done via an attached PDF. However, a noticeable number of them also relied on deliveries using link shorteners like Bitly.
- Behavior: Behaves in a similar way to past deliveries, however, it now includes a PDF for the initial infection. Once the PDF is interacted with and the MSI is run, it pulls the required DLLs and files it needs to continue the attack. During this process it will make a check to see if it is being run in a Virtual environment or on a computer with a Latin American language selected.
- Brand: Citibana // Banking // Spanish
- Infection Chain:
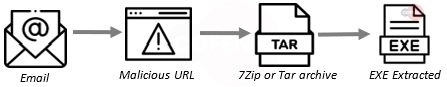
4. Agent Tesla – This information stealer and keylogger is known for checking browser activity to steal banking information and will send the data through various methods. The most recent variants will use FTP, Telegram, and mail servers under the control of the threat actor to exfiltrate information.
- Subject: Agent Tesla emails were made to be about Product orders or Purchase inquiries and came in a variety of languages with subjects supporting this.
- Attachment: Agent Tesla is delivered via a URL instead of an attached file.
- Behavior: Agent Tesla is sometimes nested within 2 archives, (Tgz and Tar). Whether this is the case or not, once the executable file within is run it will sit in processes and relay information back to the TA.
- Brand: Purchase Inquiries // Product Orders
- Infection Chain:
5. LokiBot – An information stealer targeting cryptocurrency wallets, LokiBot will send extracted information from a machine as a POST request to a command-and-control server. A keylogger component also monitors user activity to harvest credentials as they are entered into the browser.
- Subject: Subjects varied greatly when delivering LokiBot. All the subjects are focused on drawing attention to the attached document either as a shipping document, PO, or other important piece of supposed business communications.
- Attachment: LokiBot emails contain an attached document delivering the malware.
- Behavior: Malicious office macros nested within attached XLS will download the executable which, when run, will establish persistence and attempt to obtain stored passwords for things like cryptocurrency wallets.
- Brand: Shipping // PO
- Infection Chain:
Summary:
The month of April has seen QakBot continue to rise, while incidences of Emotet have dropped. This trend has been accompanied by notable campaigns of Lokibot and Grandoreiro which were not seen in previous months and should be considered when planning security measures. Also of note is the fact that most of the malware this month was delivered by attaching the files directly to the email (the exceptions being Agent Tesla and Remcos). The PDC will continue to monitor these ongoing threats as well as look for new campaigns on the horizon.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.