The PhishMe Research team recently received a campaign escalated by one or our analysts. We’ll explore the campaign delivery, malicious attachments, and analysis of the malicious attachments, and we’ll provide a simple method for extracting the credentials being used for this keylogger family’s data exfiltration.
Campaign
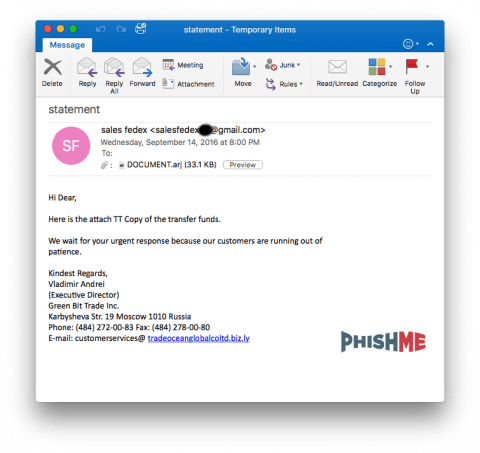
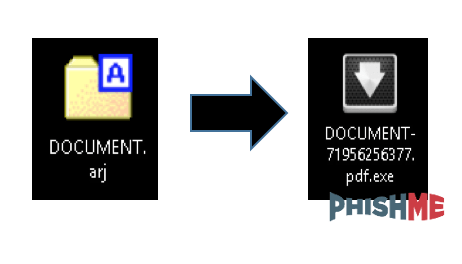
The PhishMe Triage platform allows SOC analysts to identify, analyze, and respond to email threats that have targeted their organization. For this particular campaign, the suspicious email had an ARJ archive attachment, which contained a Windows PE32 executable.
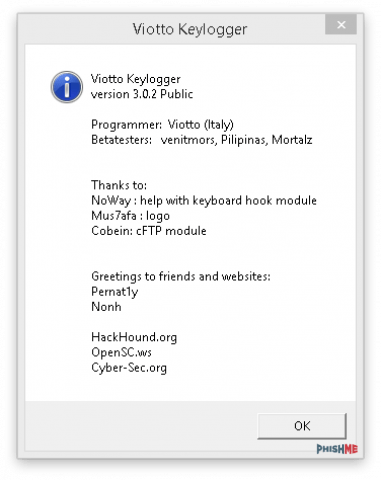
Since this malware was written in VB6, we can decompile the unpacked, malicious binaries to verify our classification. By viewing the VB6 forms, we can see that the hidden Form1 contains the name of Viotto Keylogger:
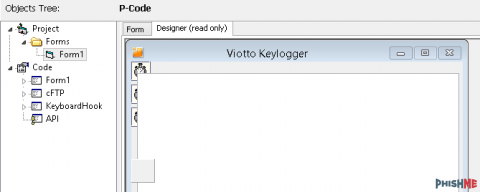
Now that we have seen an example of how this malware propagates in the wild, let’s examine the family itself. When an analyst has access to a malware’s builder (an application that enables the easy customization of malware samples), we can save precious reverse engineering time by analyzing its capabilities and features to better understand how this malware behaves.
Builder
Most of the indicators that comprise a Viotto Keylogger infection can be set at build time when the actor creates the stub (the malware sample that infects a victim’s computer). In the public version 3.0.2 of the builder, the malicious actor can specify where the keylogger’s logs will be stored, the installation method for persistence, and the delivery method of the logs via SMTP and/or FTP. In the paid, private version of the builder, the actor is able to control even more settings, such as encrypting the Keylogger logs with RC4 with a hardcoded key and enabling a Screen Capture feature that periodically sends screenshots of the victim’s desktop back to the actor. Another feature included in both versions that is not highlighted in the builder’s options is the ability to capture all text copied to the victim’s clipboard.
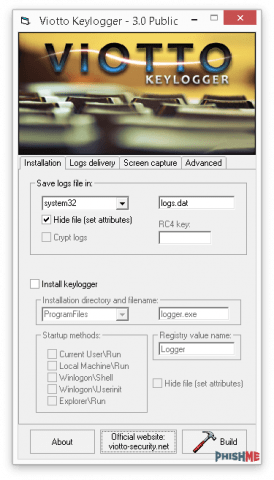
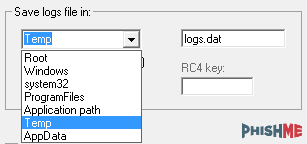
The storage location option for the keylogger log files can be set by the malicious actor at build time. They also have the ability to specify a custom log filename and to set hidden file attributes. The log files can be saved in the following locations on the infected machine’s disk:
- Root (C:)
- Windows (C:Windows)
- System32 (C:WindowsSystem32)
- Program Files (C:Program Files)
- Application Path (copied where originally executed)
- Temp (C:Users{username}AppDataLocalTemp)
- AppData (C:Users{username}AppDataRoaming)
Persistence
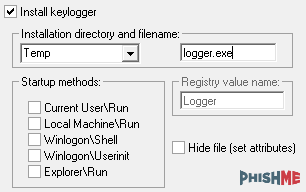
As described above, depending on the settings enabled during built time of the stub, the actor has the ability to enable infection persistence through reboots of the infected machine. The actor can also select the option to save a copy of the executable which has the same file system options as the log file storage locations. The copy of this executable can then be executed during Windows’ start up events for persistence through computer restarts. Although multiple instances of the stub can be launched by selecting any combination of startup entries, the stub ensures it’s the only process currently running by checking the mutex (a program object lock used to avoid multiple instances of the same malware from running). The default mutex is “ViottoLogger”; however, this setting can also be changed in the builder. The following startup registry keys are viable options:
- Current UserRun (HKCUSoftwareMicrosoftWindowsCurrentVersionRun)
- Local MachineRun (HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun)
- WinlogonShell (HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWinlogonShell)
- WinlogonUserinit (HKLMSOFTWAREMicrosoftWindows NTCurrentVersionWinlogonUserinit)
- ExplorerRun (HKLMSOFTWAREMicrosoftWindowsCurrentVersionpoliciesExplorerRun)
Keylogger Data Exfil
Viotto Keylogger is capable of sending the recorded keystrokes, clipboard contents, and screenshots to the perpetrator in an email (via SMTP) or to a file server (via FTP). The email option can be delivered to open relays that do not require authentication or to accounts that require authentication over SMTP using Transport Layer Security (TLS). By utilizing TLS, the account credentials and email contents will be encrypted in transit. Most of the VB6 code in this keylogger was copied from sources freely available on the internet, as indicated in the builder’s About screen:
Extracting Exfil Credentials
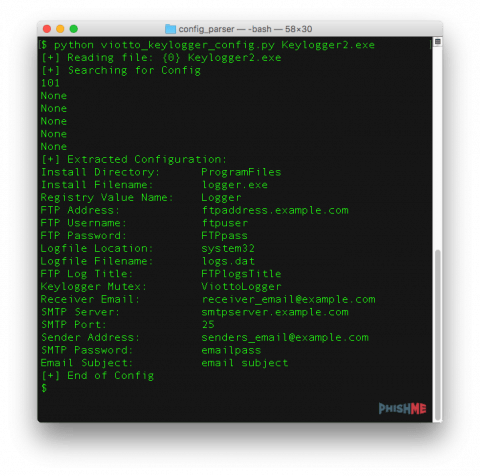
Skids wishing to use this malware creator be forewarned: your email and FTP credentials can be easily obtained! Although most of these samples in the wild will be packed, a quick and easy way to extract the malware actor’s credentials being used for victim data exfiltration is by analyzing the application’s process memory. Analysts are not only able to extract this information on the same machine utilizing a program such as Process Hacker, but personally, I prefer keeping my memory analysis tools outside of the infected machine by analyzing full VM RAM dumps with either the Rekall or Volatility memory analysis frameworks. We can also extract the malware sample’s configuration, including any SMTP/ FTP exfil credentials, statically. The malware sample’s configuration is stored plaintext in the Resources section of the stub:
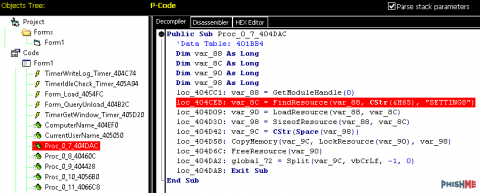
The PhishMe Research team also wrote a Python script to extract the Viotto Keylogger configuration from an unpacked sample:
Conclusion
The recent sighting of the freely-available Viotto Keylogger in the wild reminds us that cybercrime has a low barrier to entry and that tools built years ago continue to be used to exploit unsuspecting users. PhishMe Simulator trains and encourages users to recognize and report the type of email messages that are delivering this threat. The next step is to act on those reports, and PhishMe Triage enables your team to sift through all reports and quickly and efficiently act on the ones that pose a threat to your organization. Click here to learn more.
Related SHA256 Hashes
271781975987737466077146acc7309b6d1e794e2ead0876e0a204f0fb1169ef
6fee7e06eff76397354455665919aa53ee62957f3ef5a47aa16558f7799937ad
7961671bc61cb4c0df3d81dff85f707be2fc666708e5fba626c328e6a6bfcd17
7d74f30b5a663972d9984ef8cb8dbfba478a4968e1d626e39c4fb8a80385f37b
91b30f5368a1c102d496e82099cb6222551131f74607e1a694b0ff3ed3c04cfd
9640db7cfb5e083c58166905386c5472cf38823364ff719ad3e59c6fbeb696b3
e75684f5e16cf6476726b0c2b51f760035746742334238c13172e4fe73970ff2
f8b1cd7524a5183fe7aa3abb0aae7e660c201df095a1df83e139cecad145a253
Miscellaneous
Download the Viotto Keylogger yara rule or the configuration extractor.