Microsoft ATP
IronPort By Zachary Bailey, Cofense Phishing Defense Center
The rise in phishing attacks and increased delivery of sensitive information over email has fueled the demand for “secure mailers.” These services encrypt and store your organization’s emails, only unlocking them if the designated recipient signs in. This takes the stress off the organization’s SEGs, or secure email gateways, when it comes to checking emails for sensitive or personally identifiable information (PII). However, secure mailers can be spoofed, and their credentials harvested – creating a new threat vector relative to sensitive emails.
Zix is a common secure mailer that is observed by the Cofense PDC. One threat actor mimicked Zix branding to create a lookalike phishing page using a custom domain that bypassed SEG protection. The attack relies on the target’s familiarity with Zix as they click through the encryption message and land on a Microsoft phishing page. After submitting their credentials, the victim is redirected to a legitimate OneDrive error page.
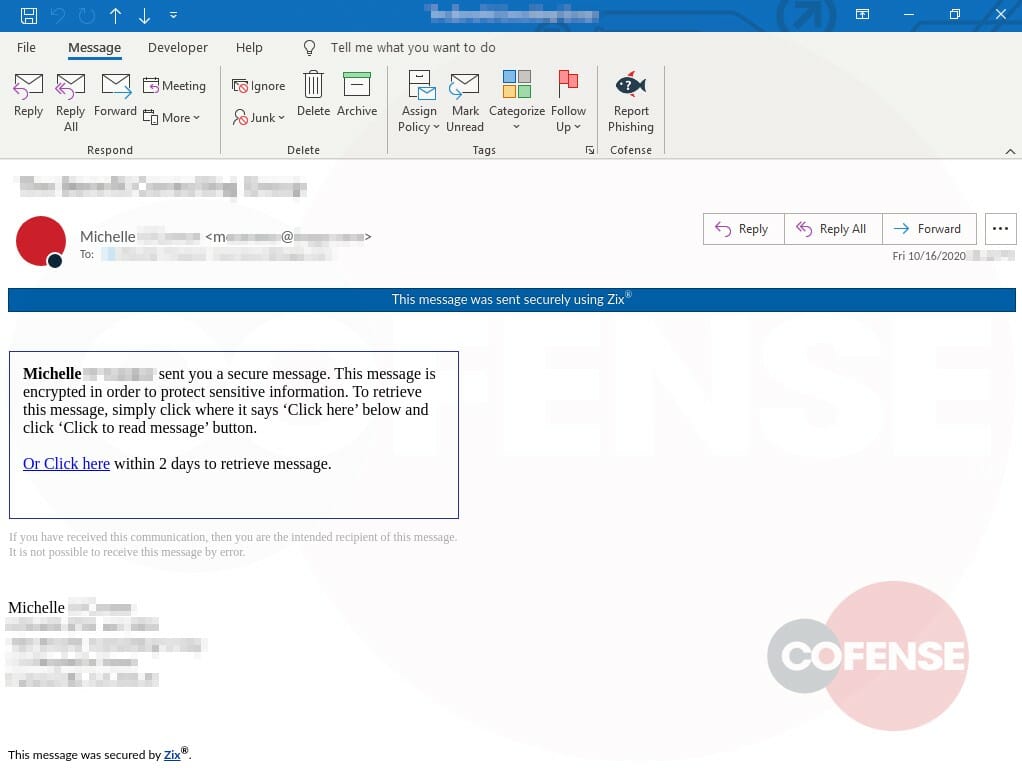
Figure 1: Email Body
The email in Figure 1 looks typical of a secure mailer and uses a Zix message tag. The note saying “Michelle sent you a secure message” reinforces familiarity and lures the recipient into a false sense of security. The only lure here is asking the user to “Click here” to read on, while also advising how to complete the next step once they land on the website.
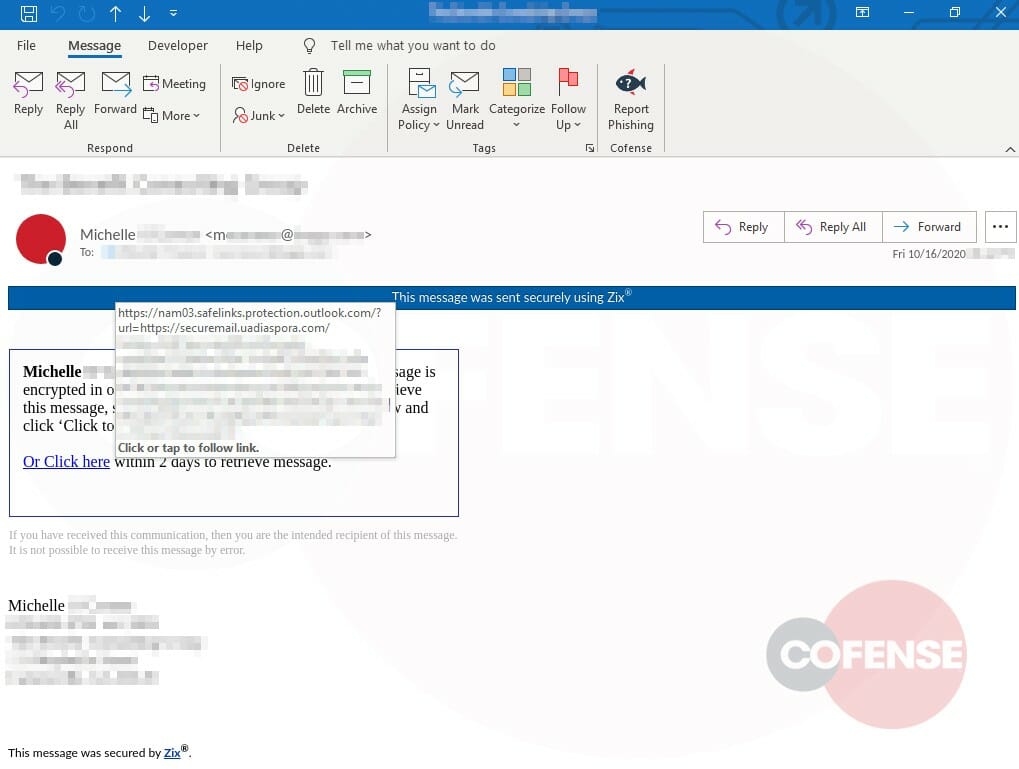
Figure 2: Email Body Showing URL
If the recipient hovers over the link, as shown in Figure 2, they will see that it goes to a “securemail” sub-domain, which is a common setup for these services. In the body of the message, they also see the expiration for retrieving the message.
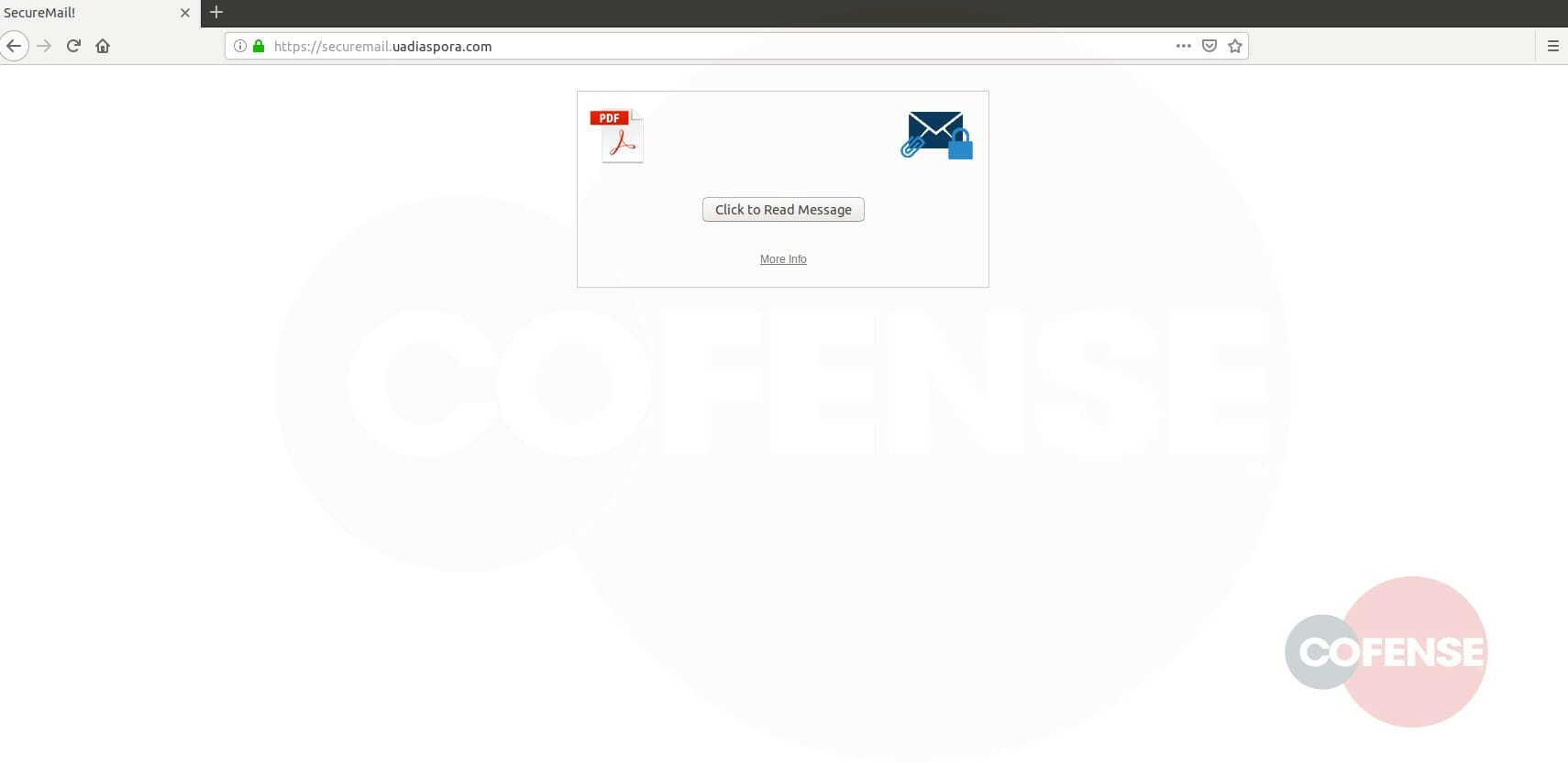
Figure 3: Phishing Page
In Figure 2 we see the website mimics a Zix landing site, which directs the recipient to interact with a “click to read message” button (Figure 3). The site is also HTTPS encrypted, so any data sent through it cannot be read. If the user hovers over the button, they will notice that it leads to a different website. This is shown in Figure 4.
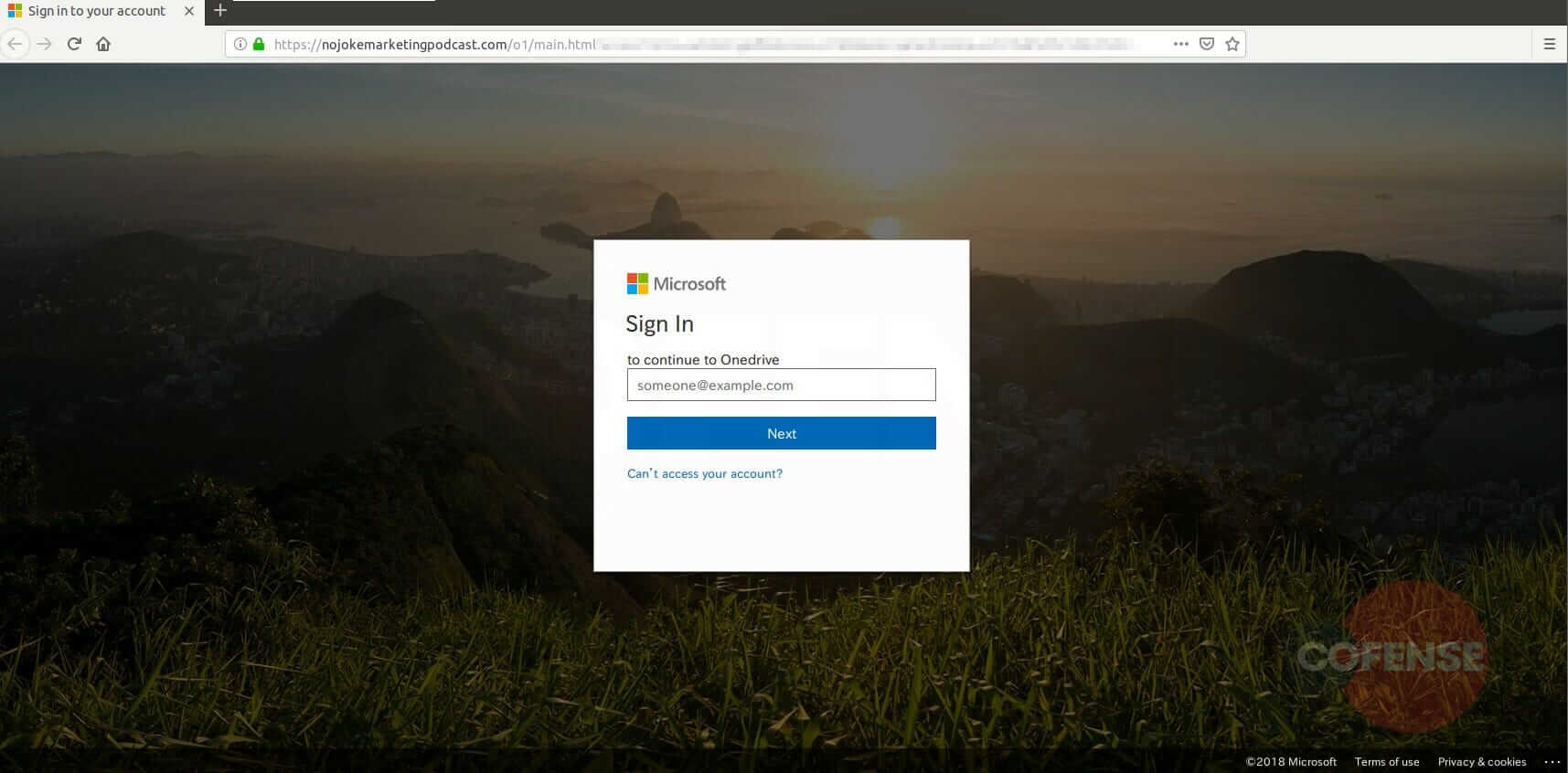
Figure 4: Phishing Page
During the transition from the secure mailer page, the title of the tab has changed from “SecureMail!” to “Sign in to your account,” accompanied by a Microsoft login page. This is an uncommon occurrence for secure mailers as they typically have their own login pages.
Figure 5: Phishing Page
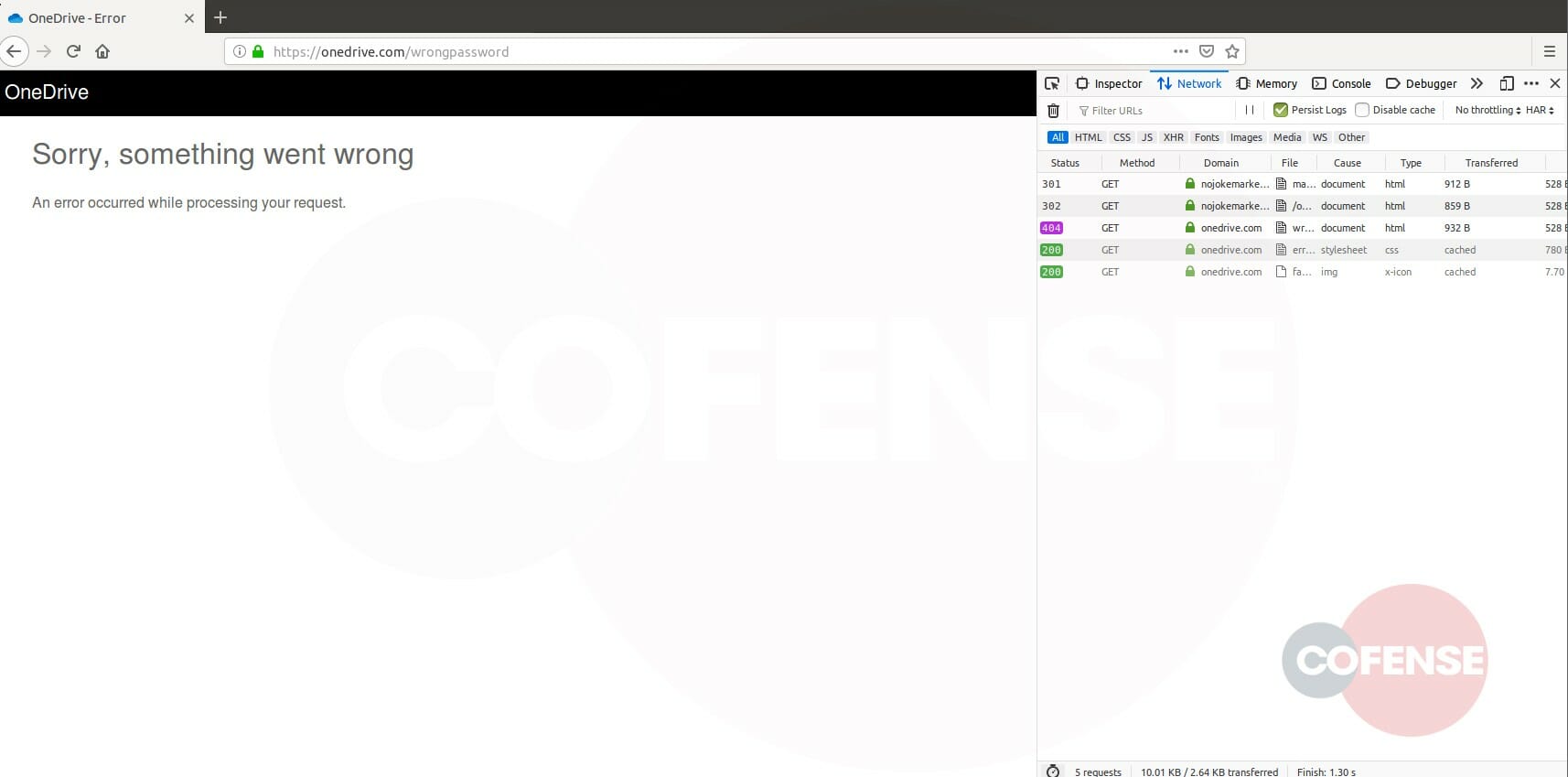
After the user provides their credentials, a redirect occurs taking them to a OneDrive error page. Inspecting the network traffic shows that the entered credentials have been sent to the threat actor rather than Microsoft.This error page is a common tactic to convince the user that “something went wrong” and postpone or prevent recognition that their credentials were harvested.
Indicators of Compromise
| hXXps://securemail[.]uadiaspora[.]com/ | 4558117154 |
| hXXps://nojokemarketingpodcast[.]com/o1/main.html? | 16224115765 |