By Ashley Atkins, Cofense Phishing Defense Center
Since the start of the pandemic, cloud-based video conferencing has been heavily utilized. Whether for work purposes or for simply keeping in touch with family and friends, access to such a tool is vital. With the increased use of video conferencing, threat actors are taking advantage and abusing well-known video conferencing brands.
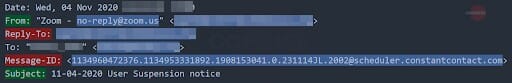
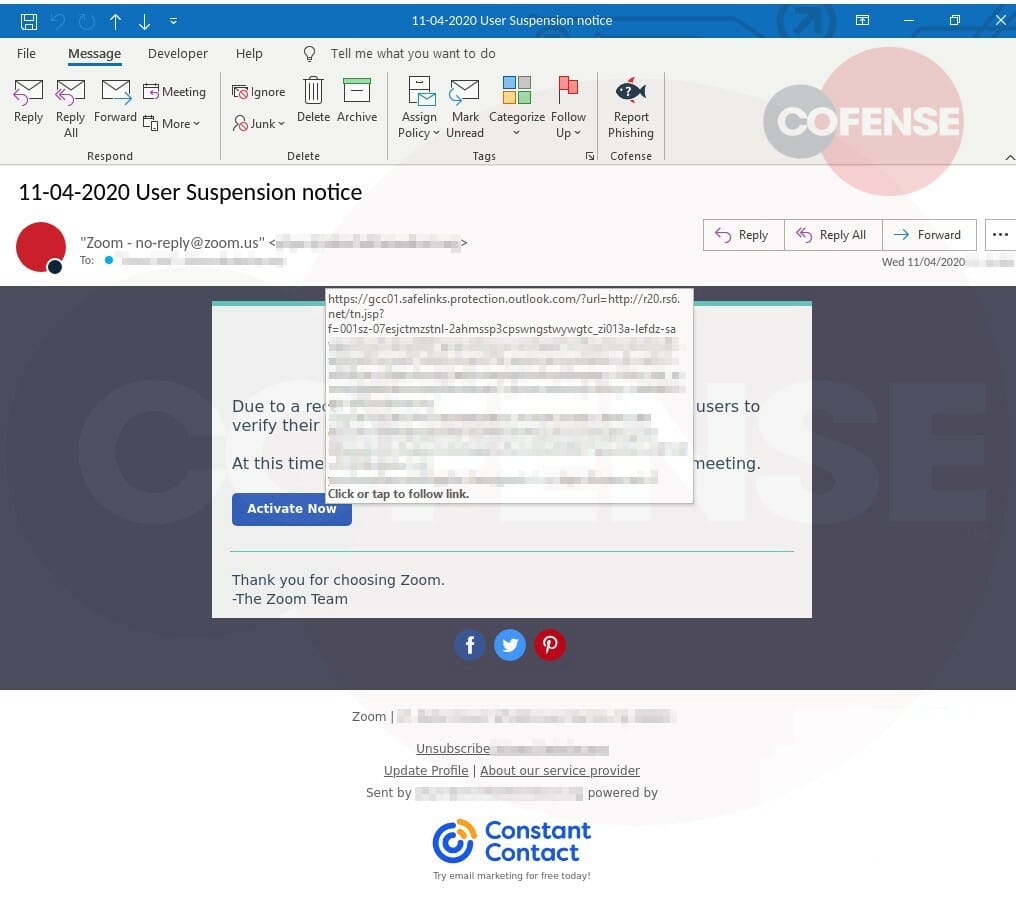
The Cofense Phishing Defense Center (PDC) investigated an email impersonating Zoom. The email claimed that a Zoom server upgrade had been performed and that the recipient would be unable to invite or join calls unless they verified their account. Upon analysis, the PDC quickly identified the email as a credential phish. Within the email headers, the “from” field typically shows a display name and email address such as John Doe <[email protected]>. However, instead of the display name showing a name, it showed “Zoom – no-reply@zoom(.)us” making it appear as though the email was from Zoom.
Figure 1: Email Body
While Cofense has written about Zoom in prior blog posts, it is important to note that this particular email was sent through Constant Contact, a service used to send email for marketing campaigns. As noted on the Constant Contact website, the company provides a unique campaign ID in the Message-ID field allowing them to identify the sender. The headers shown in Figure 2 confirm that Constant Contact was used in this phishing attack. The attacker may have believed that Constant Contact emails would be better able to bypass various SEGs – a maneuver that seems to have been solid given the substantial number of SEG environments in which this phish was found.
Figure 2: Headers
Figure 3: Malicious URL
In Figure 3, the email shows the sender’s name to be “Zoom – no reply@zoom.us.” However, the actual compromised sender account can be seen beside it. This suggests that the threat actor may have compromised a user of Constant Contact, and has utilized that account to send out the attacks.
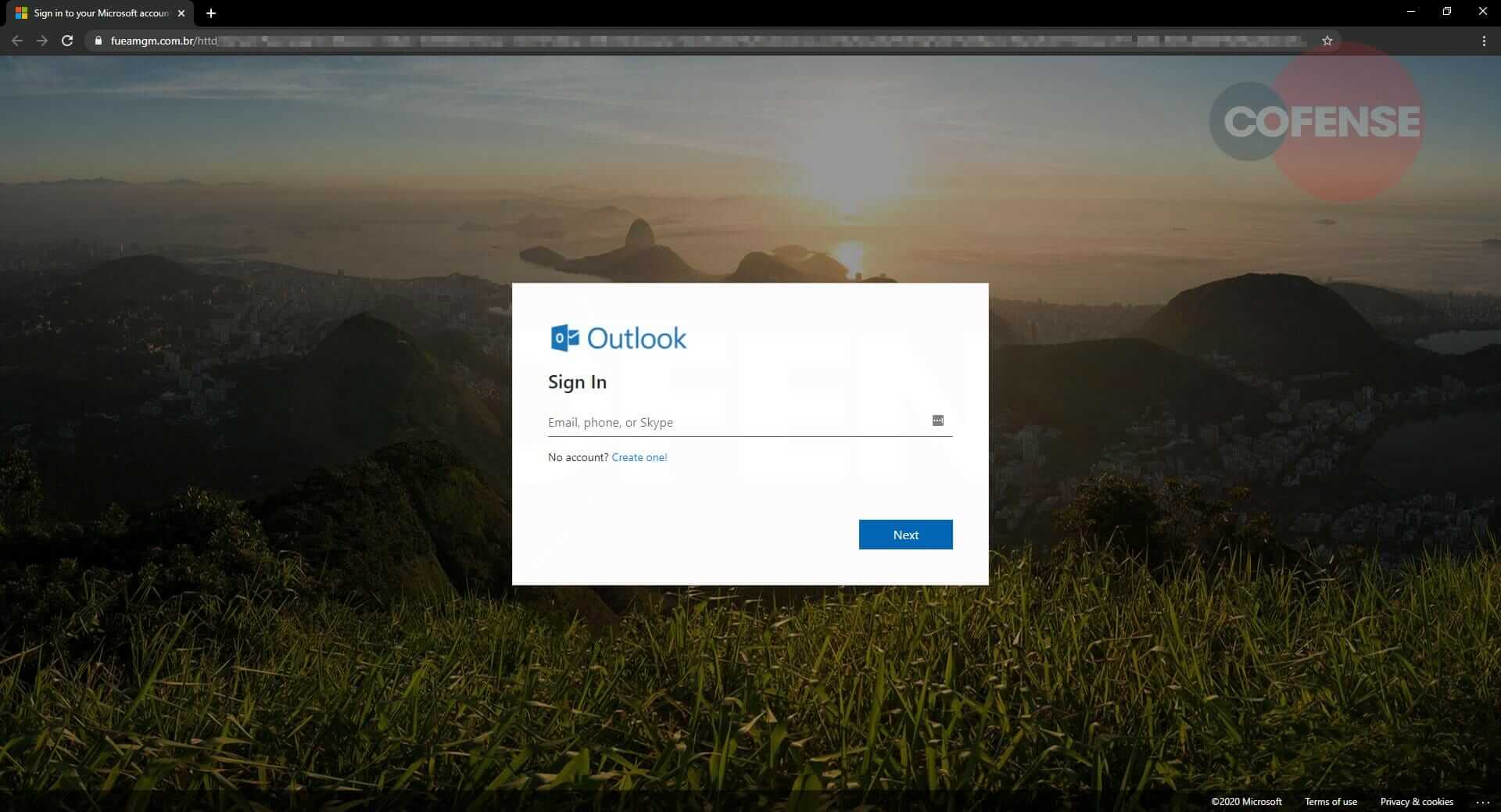
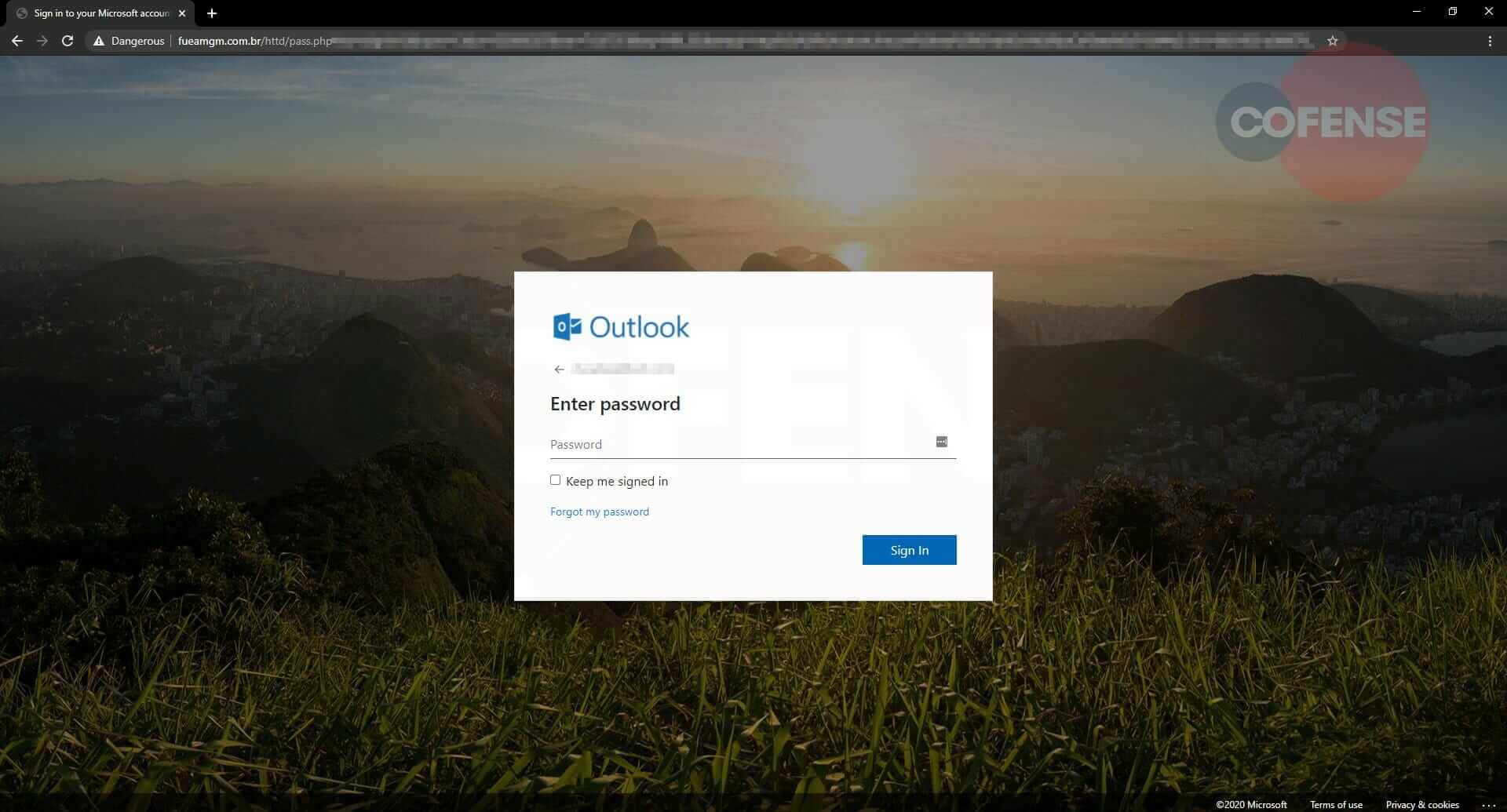
Hovering over the “Activate Now” button, Constant Contact’s tracking URL (r20[.]rs6[.]net) can be seen, as shown in Figure 3. When clicked, the recipient is directed to “sankamilan[.]com” and is redirected to a fake Microsoft login page at “fueamgm[.]com[.]br,” as shown in Figure 4. Once credentials have been entered, the recipient is redirected again to a Microsoft inbox.
Figure 4-5: Phishing Page
As we can see, two different brands were used in this phishing campaign, which could result in attackers harvesting multiple sets of credentials.
Indicators of Compromise
| hXXp://r20[.]rs6[.]net/tn.jsp?f=001SZ-07esJCtmzsTnl-2ahmSsp3CpswNGStwYWGtC_zI013A-LeFdz-SawGYz8wUt1zjLruZbLT67G_tPvkDNXRwcoznHPJSK7RS79ZwHLoicSBO6M6Tr-sPHkQ365MAq327s4IDhxhcGO2259_pUcjNZeRvwUri8p&c=3H_CP9T_hN834FXay-T3bJQcfuvdg7UAdRmIAMdqKRos8XzZ8B | 213[.]190[.]6[.]27 |
hXXps://sankamilan[.]com//httpd/
| 208[.]75[.]122[.]11
|
hXXps://fueamgm[.]com[.]br/httd/
| 162[.]144[.]238[.]226 |