Sextortion: What You Need to Know and How to Protect Yourself
Giving New Meaning to “Not Safe for Work”
Cofense Labs has identified a sextortion phishing campaign with over 330 million recipients in its sights. Learn how you can recognize the threat and stay safe here.
What is Sextortion?
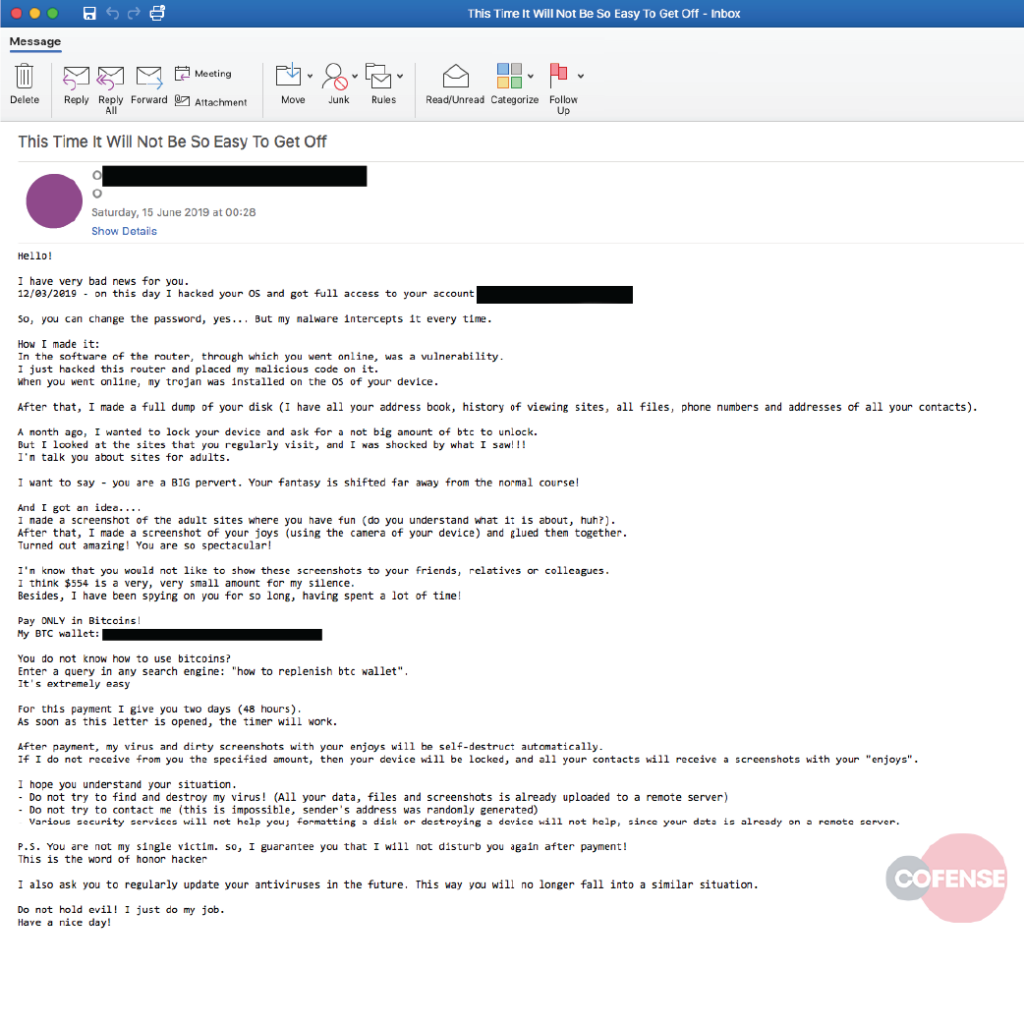
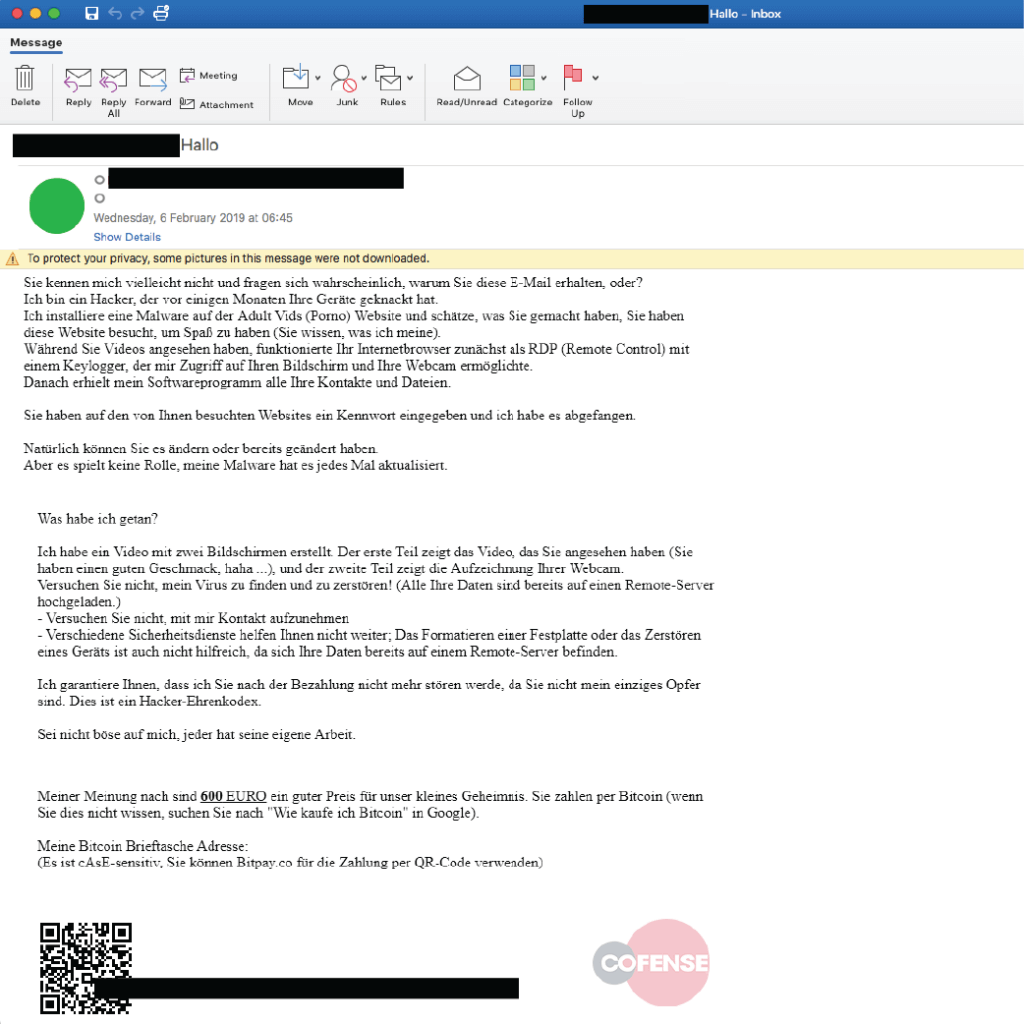
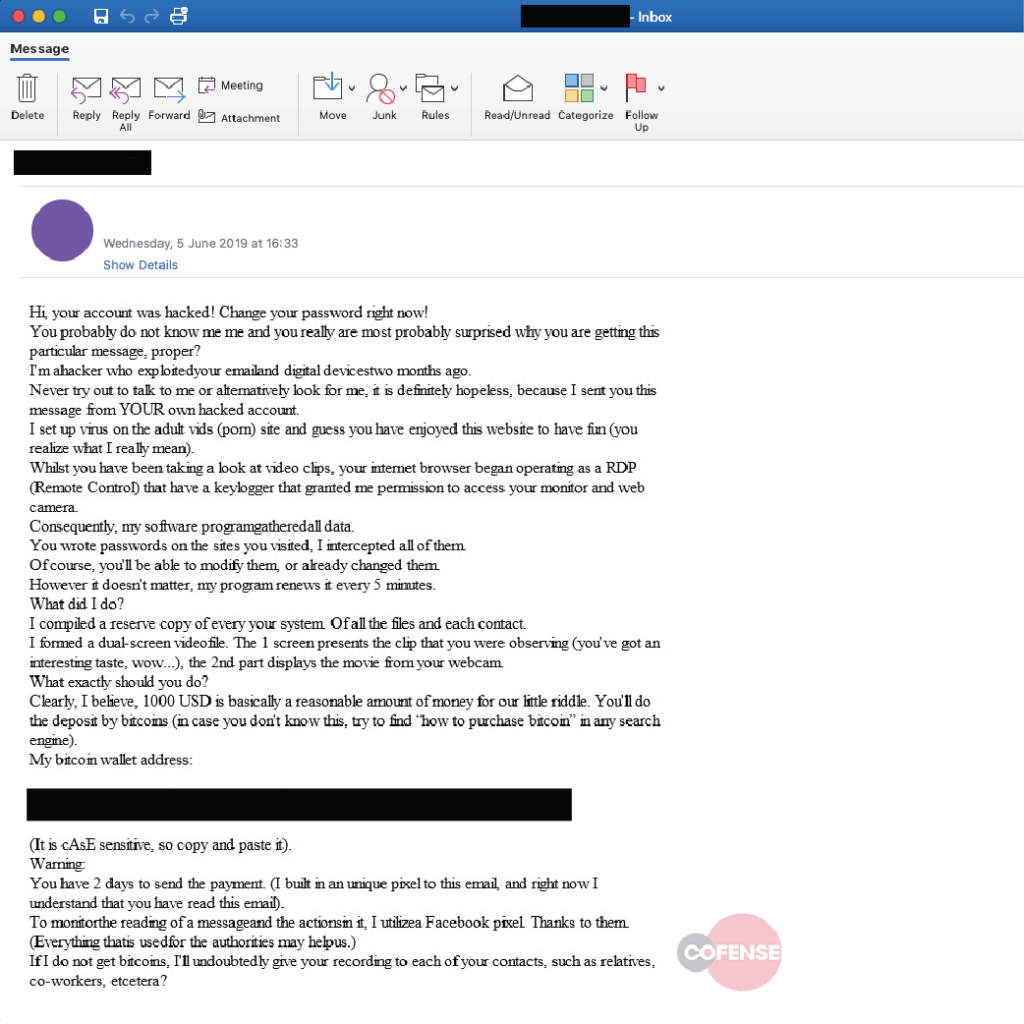
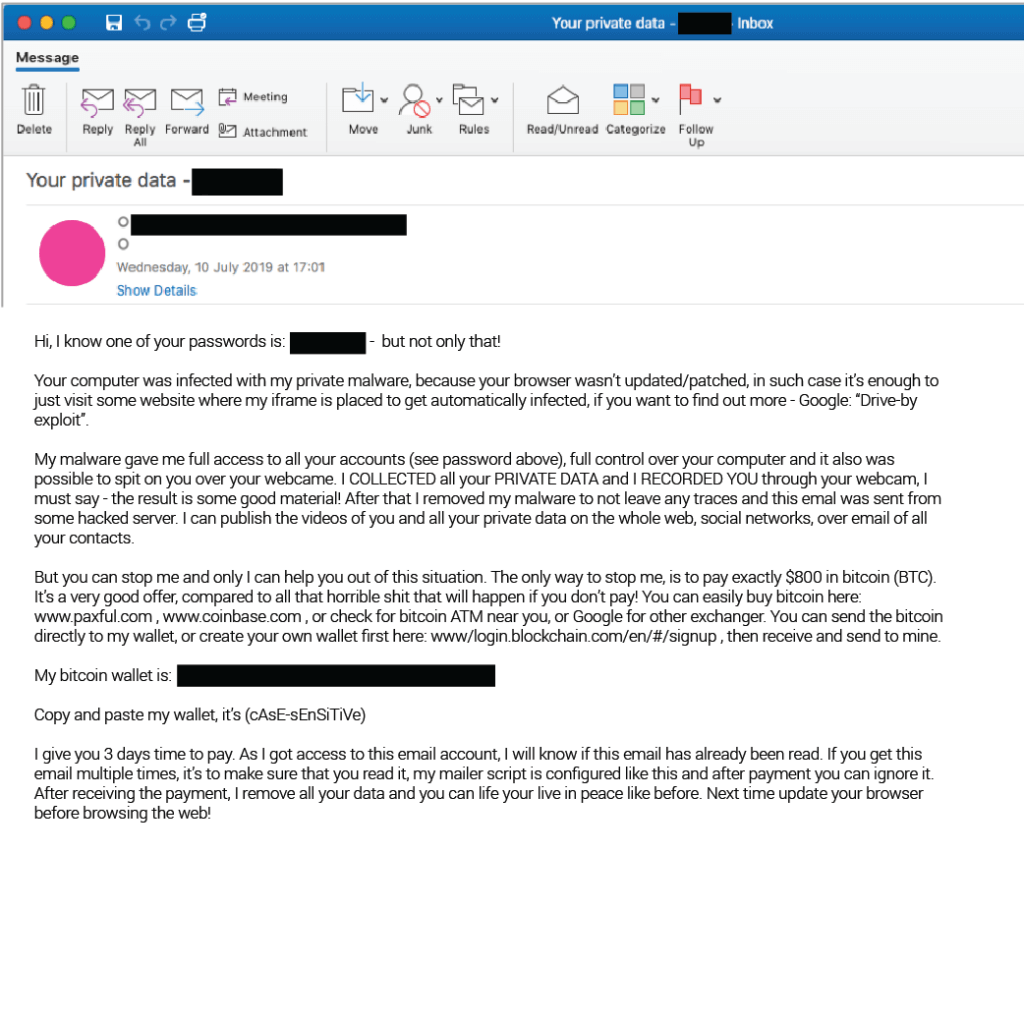
Revisiting scam email tactics of old, sextortion emails mix the prospect of shame with the tried and tested motivators of fear and urgency to extort ransom payments from victims.
Data breaches going back years give scammers a new angle. The inclusion of YOUR passwords harvested from past data breaches adds to the emotions, dials up the authenticity, and improves the chances of payment. For more information on sextortion, view our infographic and Sextortion 101 guide.