As we have continued to improve anti-phishing capabilities for clients over the past few years, we have seen a myriad of changes in phishing email composition, style, and approach. Throughout all those changes however, one thing has remained the same.
The proliferation and subsequent visibility of both spam and phishing emails continues to climb and the need for real time or near real time analysis of reported emails is becoming paramount to getting ‘left of breach’ in the phishing kill chain.
Those real time analysis efforts are impacted by several factors, including but not limited to the following:
- Ebb and flow of spam and phishing campaign delivery
- Inclusion of benign spam in reported suspicious emails
- Ability to automate part of the analysis process, properly written rules and recipes for filtering known emails, and focused analysis on what remains
The Tide Continues to Rise
SPAM continues to make up the bulk of emails received and reported by our customers and there is certainly a ‘feeling’ that the amount of SPAM in the wild is increasing. While this is likely true, it’s more probable that spammers are getting better at using ‘Trusted Sender’ techniques that avoid detection and filtering.
For example, industrious spammers look to take advantage of sending from authorized accounts on webmail gateways. Utilizing multiple accounts, they are then able to send spam in smaller bursts to get their messages delivered with a higher frequency of success.
Add to that the technique of sending spam from compromised (known and trusted) email accounts and the amount of successful deliveries just continues to climb. Not to mention further increases in the successful delivery of BEC style phish designed to exploit gaps in technological defenses and email credential phishing (often posing as ‘file sharing’ notifications).
These increases in successful delivery can and often do present significant challenges for incident responders and others tasked with analyzing reported suspicious emails.
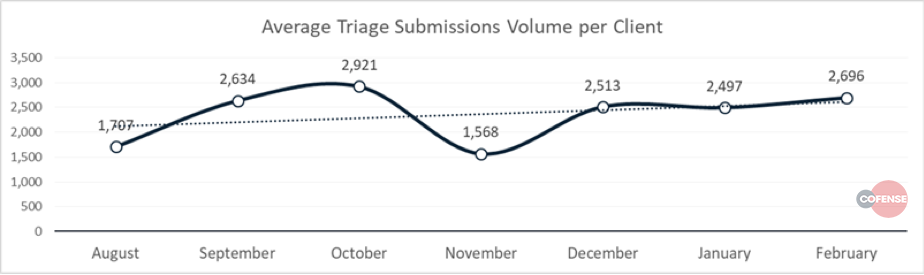
Within the CofenseTM Phishing Defense Center, we see evidence of increases in both spam and malicious emails within the user reporting that we analyze and help our clients respond to. Notice below, the ebb and flow of reports per month and the increase in average volume of reports over time.
To Deal with the Problem, Take a Multi-tiered Approach
To address those trends, you’ll need to consider multiple approaches to ensure incident response teams are prepared to deal with increases in both spam and real threats as the free flow timing of malicious email campaigns creates an uneven influx of emails to analyze and mitigate.
- Know who in your organization would be targeted and what could be the impact if compromised
- Dedicated incident response and threat analysis resourcing
- Automation of real time analysis (rules and recipe creation, sandbox integration, etc.)
- Specific procedures to handle phishing attacks (malware delivery, credential theft, BEC)
- Targeted active threat simulations
While anti-phishing programs are not limited to the above list of considerations, each of these is key to providing focus and opportunity to empower incident response teams in the ongoing battle against increases in the successful delivery of malicious email.
Because it is impossible to predict when phishing and spam campaigns will begin and end, and because we can not know their delivery success rates in advance, we need to consider an appropriate resourcing model for teams tasked with responsibility for response.
Understanding the cost limitations of being fully staffed for a heavy load, it’s critical that organizations find and maintain staff for standard workload while preparing to flex / increase resources when needed.
This can take the form of internal resources with other responsibilities being ‘turned up’ as needed, adding qualified 3rd party resources for peak times, or even outsourcing all your email incident response management.
In addition to resourcing flexibility, we can’t ignore the value of automated (high-level) analysis. Every opportunity to automate the identification of known / existing threats should be implemented to allow our human resources to focus on what is new so they can identify the unknown and proper steps for mitigation.
Last, we need to look at another primary driver of increases in IR workloads. That driver is the increase in recognition and reporting of suspicious email. Successful anti-phishing programs are changing end user behavior and increasing the amount of available phishing intelligence while also increasing the need for analysis and response; a good ‘problem’ to have.
That said, anti-phishing programs can help alleviate this issue as they mature. The greatest impacts on quality (i.e. – a higher percentage of real threats overall) within user reported threats is continuing education regarding differences between spam and an actual phish, as well as a simulation program that continues to close in on / focus on active threats specific to your organization.
Modeling and simulating active threats for your users helps them understand exactly what you are looking for and the threats they are facing. This focus will not eliminate spam resorts altogether, but as you continually assist your users to mature their recognition capabilities and automate known variables for analysis, you will be better able to manage any sudden influx of spam and phishing that arises.
Learn how Cofense PhishMeTM helps users recognize phishing and reduce susceptibility up to 95%.