Mining Phish in the IOCs
PhishMe® and Palo Alto Networks® are providing security teams with the ability to ingest human-verified phishing intelligence in a standard format that can be automatically enforced as new protections for the Palo Alto Networks Next-Generation Security Platform through the MineMeld application. Through this integration, PhishMe and Palo Alto Networks are providing a powerful approach to identifying and preventing potentially damaging phishing attacks.
The challenge of operationalizing threat intelligence
Ransomware, business email compromise (BEC), malware infections, and credential-based theft all primarily stem from a single vector of compromise – phishing. Operationalizing threat intelligence, especially when it comes to phishing, continues to weigh on the minds of businesses regardless of size. Security teams require the ability to ingest, verify and enforce new protections for potential phishing attacks, all within their existing infrastructure.
Where are the Phish?
PhishMe extends beyond a traditional data feed. Customers receive phishing intelligence. What’s the difference? Intelligence, vs. traditional data.
Information without context is data. Intelligence is information with context, and context is what security teams require in order to have confidence in their decisions.
Intelligence customers receive indicators specific to phishing and their criminal command and control (C2) and botnet infrastructure associated with malware families like Locky, Dyre, and Cerber. This is then backed up by threat intelligence reports with verbose context that provides security teams with insight into attacker TTPs.
PhishMe identifies what is nefarious, but more importantly, why, and what it means.
Integration Tackle Box for PhishMe and Palo Alto Networks
Security teams who wish to easily complement their Palo Alto Networks Next-Generation Security Platform’s security policies with PhishMe Intelligence will need an instance of MineMeld (version 0.9.26 and above) and PhishMe Intelligence API credentials (contact PhishMe for trial access https://cofense.com/product-services/live-demo). MineMeld will ingest intelligence from PhishMe, and can automatically feed new prevention controls to Palo Alto Networks devices, without adding heavy operational burden.
Configuring MineMeld with PhishMe
The following is a step-by-step guide to configure MineMeld in order to ingest PhishMe Intelligence phishing URLs, aggregate them, and construct into an output capable of preventing malicious URLs in security policies within PAN-OS devices. Before we dive into the configuration of MineMeld, it is important to review the three key concepts behind the application:
- Miners: responsible for retrieving indicators from configured sources of intelligence and data feeds. Miners will bring in new indicators on a configurable, periodic basis, and also age-out any indicators that are no longer needed.
- Processor: The processor node will aggregate the data obtained by the Miner and conforms the data to IPv4, Ipv6, URLs, or domains. Once aggregated, the data is sent to the output nodes.
- Output: The output nodes gather data from the processor node and convert the data into a format that is capable of being consumed by PAN-OS (and other non-PAN-OS external services)
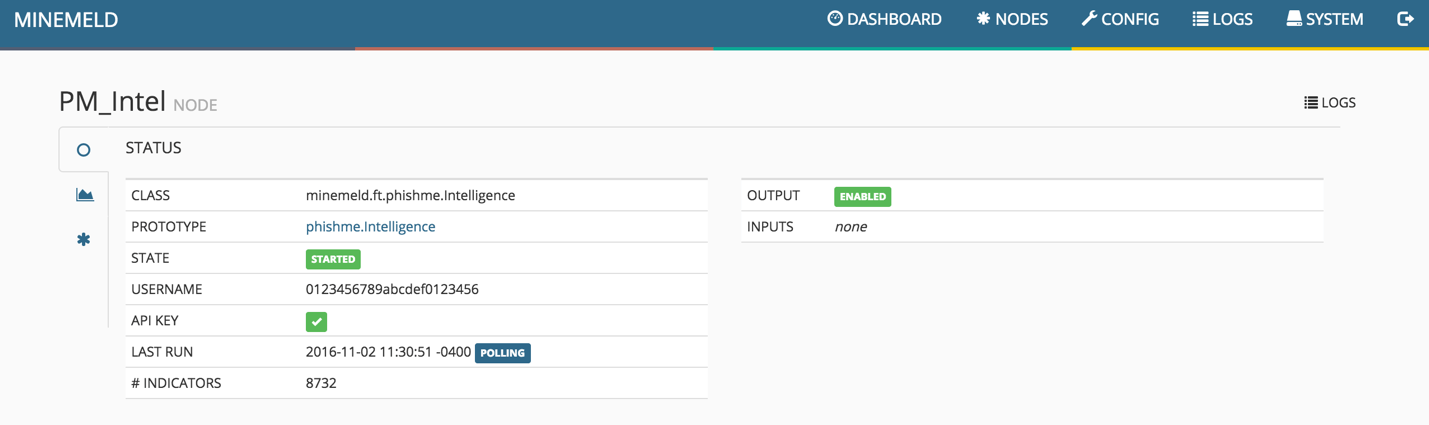
PhishMe Intelligence Miner Node
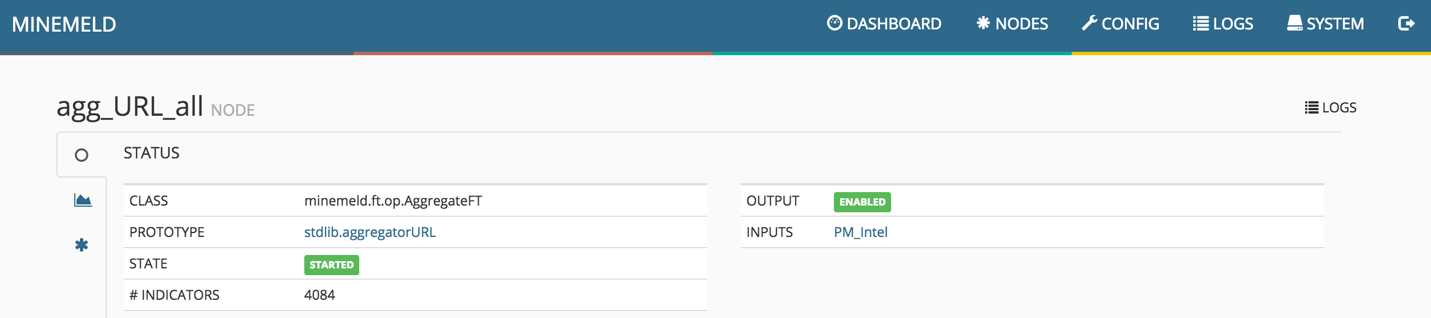
Processor Node
Output Node
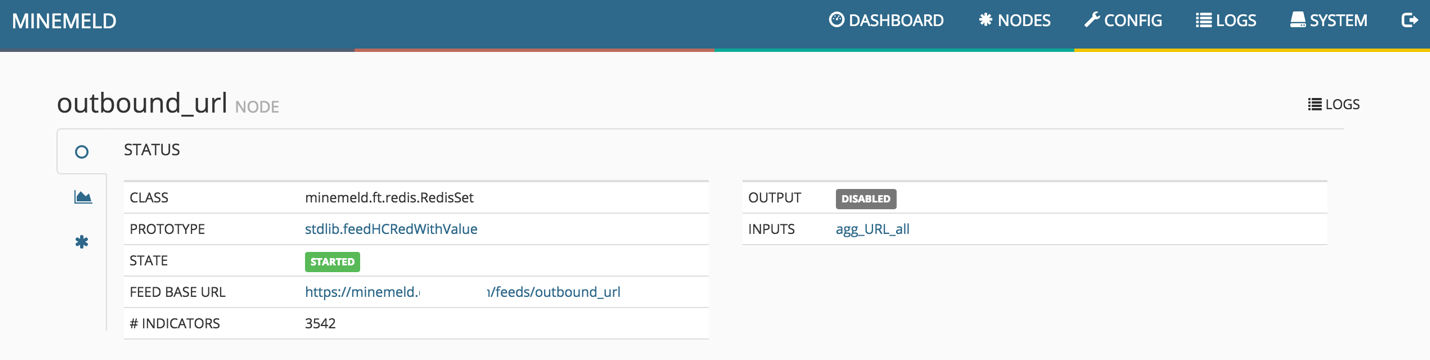
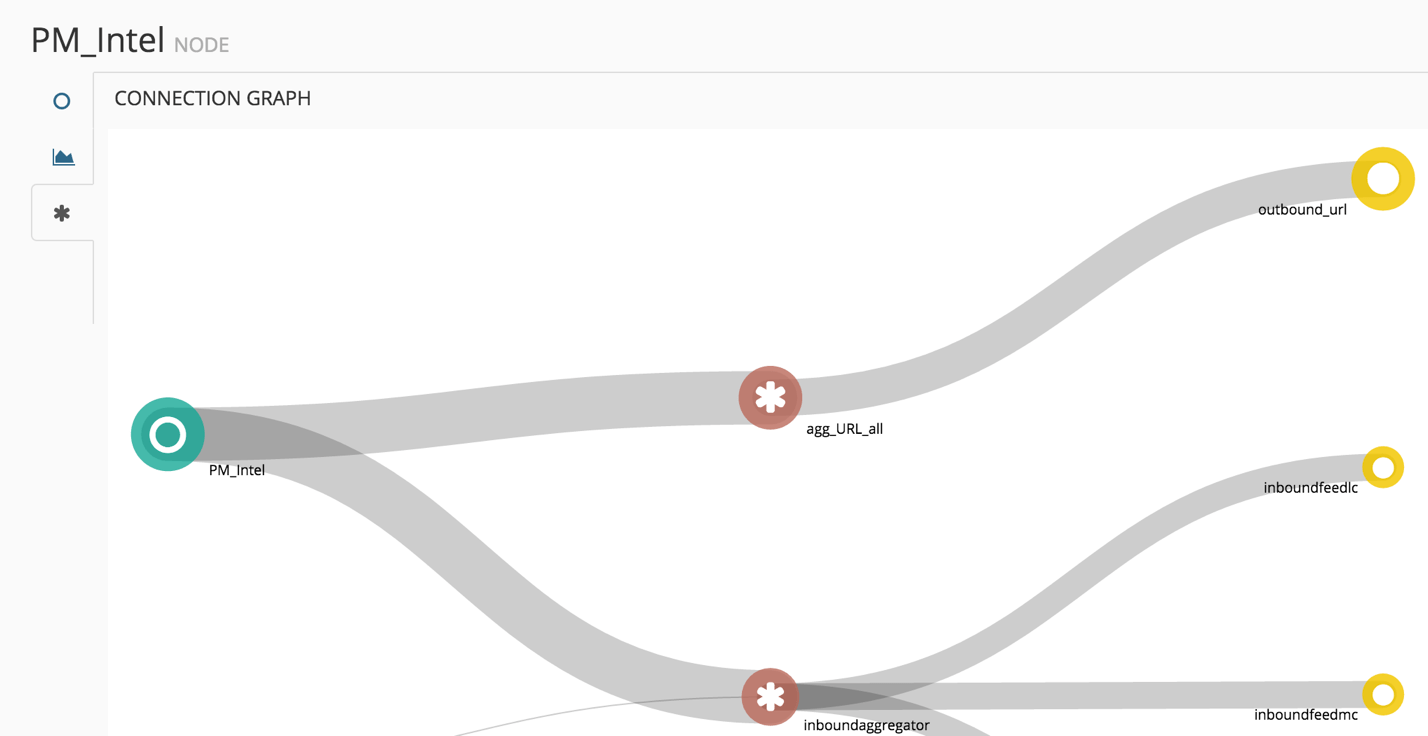
Configuration Graph Summary
The configuration graph is a summary exhibiting the flow of PhishMe Intelligence. The miner collects intelligence, aggregates, and the output node structures the data to be usefully applied to prevent phishing.
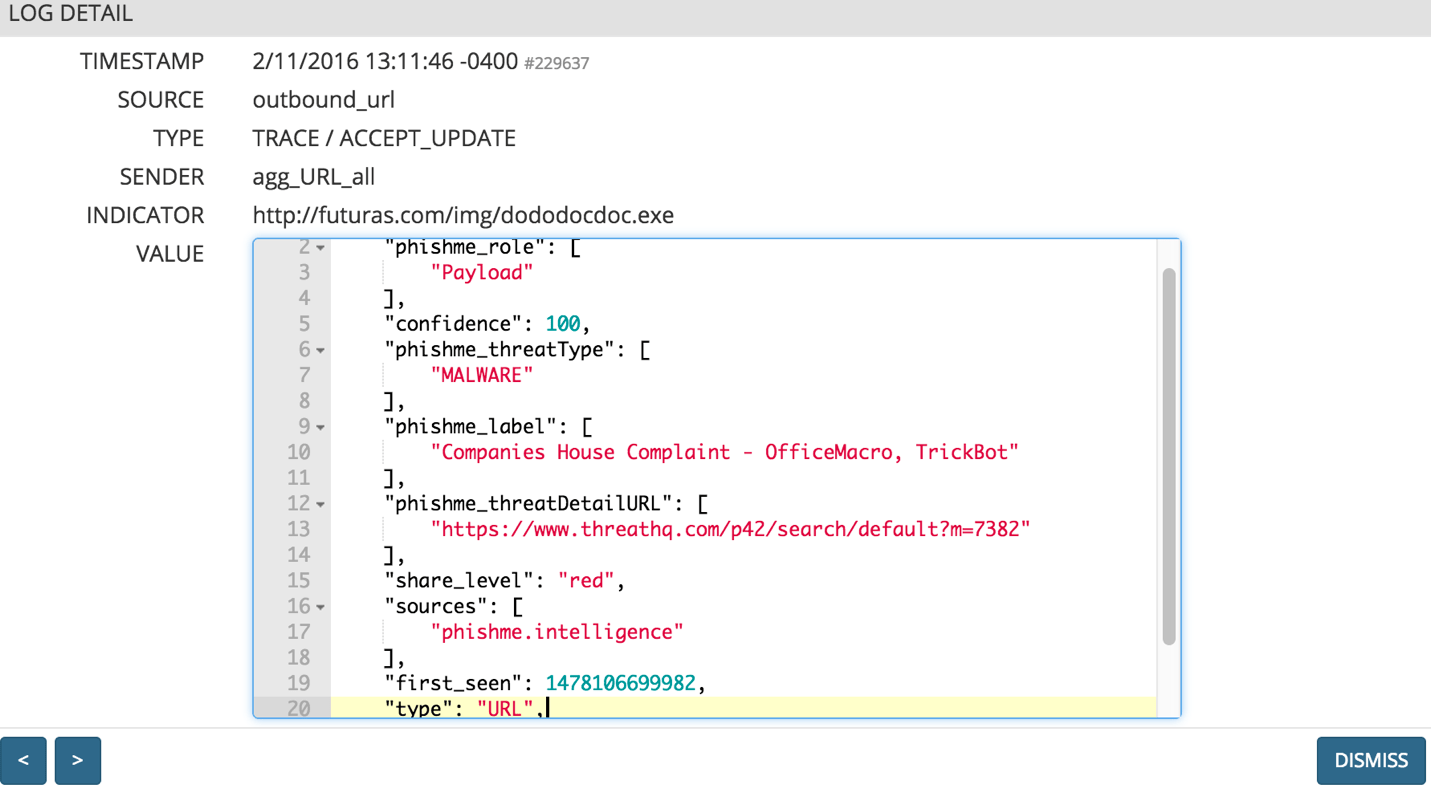
Log Detail with URL Indicator and High Confidence rating of 100
The image below represents an example of URL intelligence received in the MineMeld log. This snippet specifies a malware payload from an OfficeMacro and TrickBot (similar to Dyre) family. If they choose to, analysts can then use the URL to the Threat Report with executive and technical details that explain more about the malware.
The above summarization of the MineMeld setup portrays how easy it is to take very relevant and useful information and structure it so that it can be operationalized with other security investments. Far too often teams have underutilized technical resources or processes that place a strain on the workforce. MineMeld reduces the human burden and provides security teams with the ability to create actionable prevention-based controls.
Phishing Intelligence Operationalized = PhishOps!
Let’s review an example of how to operationalize these indicators of phishing (IoPs) and apply them to a Palo Alto Networks security policy to deny egress traffic to these phishing URLs.
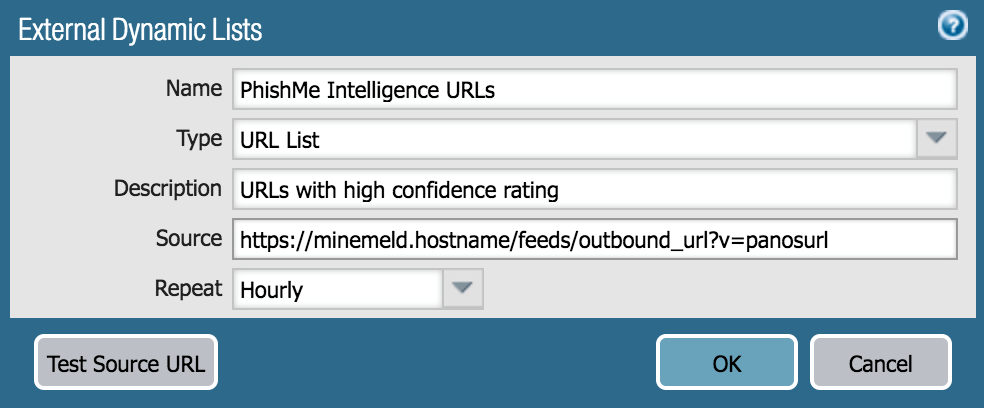
Create New Object in PAN-OS
From the Objects tab, select External Dynamic Lists from the navigational pane. Analysts just need to provide the relevant information to pull in the list of URLs from MineMeld.
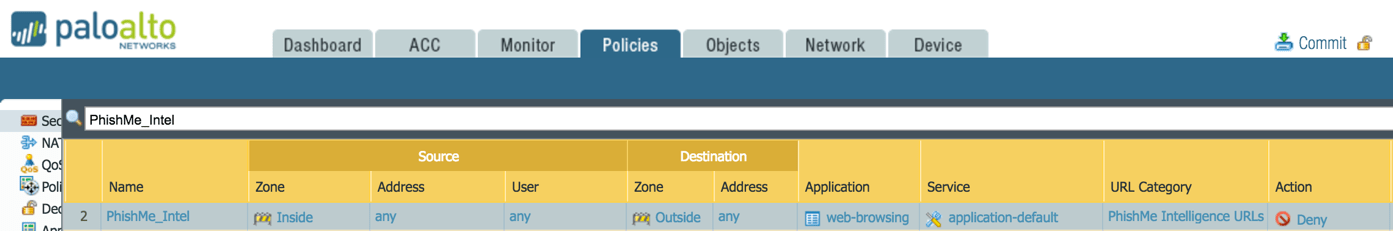
Apply to PAN-OS Security Policy
With the External Dynamic List defined, security policies can now be created based on acceptable criteria. In the case below, inside sources browsing externally and matching the PhishMe Intelligence URLs will be denied.
FINito! Wrapping up
A similar process can be repeated like the above, with IP lists and domains, and applied according to phishing threats facing the business. The way MineMeld handles the data received makes applying it to Palo Alto Networks Next-Generation Security Platform very effective. Security teams will need to determine where they want to apply the policies once MineMeld has compiled the data.
The phishing threat is alive and very well and the ability for security teams to maximize their investments and operationalize with low administrative overhead should be enticing to tackle the threat.
More about MineMeld:
MineMeld, by Palo Alto Networks, is an extensible threat intelligence processing framework and the ‘multi-tool’ of threat indicator feeds. Based on an extremely flexible engine, MineMeld can be used to collect, aggregate and filter indicators from a variety of sources and make them available for consumption to peers or to the Palo Alto Networks Next-Generation Security Platforms.
To learn more about the Palo Alto Networks Next-Generation Security Platform, visit: https://www.paloaltonetworks.com/products/designing-for-prevention/security-platform.
To learn more about the PhishMe Intelligence, visit: https://cofense.com/product-services/phishing-intelligence/.