By Nathaniel Sagibanda, Cofense Phishing Defence Center
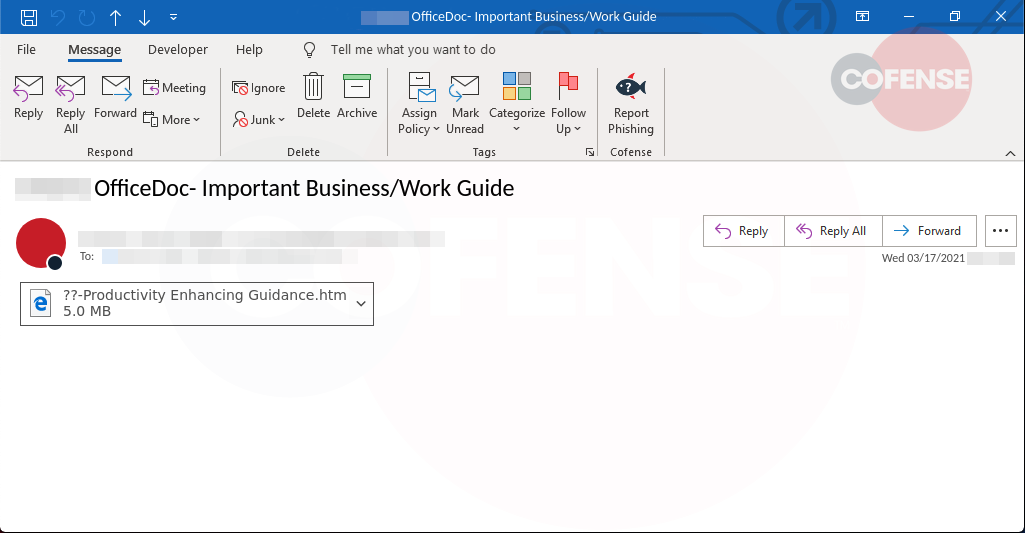
The Cofense Phishing Defense Center (PDC) has observed a credential phishing trend whereby threat actors are sending out several emails to employees with nothing more than an HTML attachment and subject line, “OfficeDoc – Important Business/Work Guide.” As organizations are planning for return-to-work procedures, threat actors are leveraging this theme to increase the likelihood of user interaction with the attachment.
Security protocols such as secure email gateways (SEGs) have a tough time stopping such malicious emails because the HTML attachment discreetly hides the malicious URL. The threat actor uses a popular and trusted cloud-based SMTP relay – SendGrid – to release their campaign.
Figure 1 – Email Body
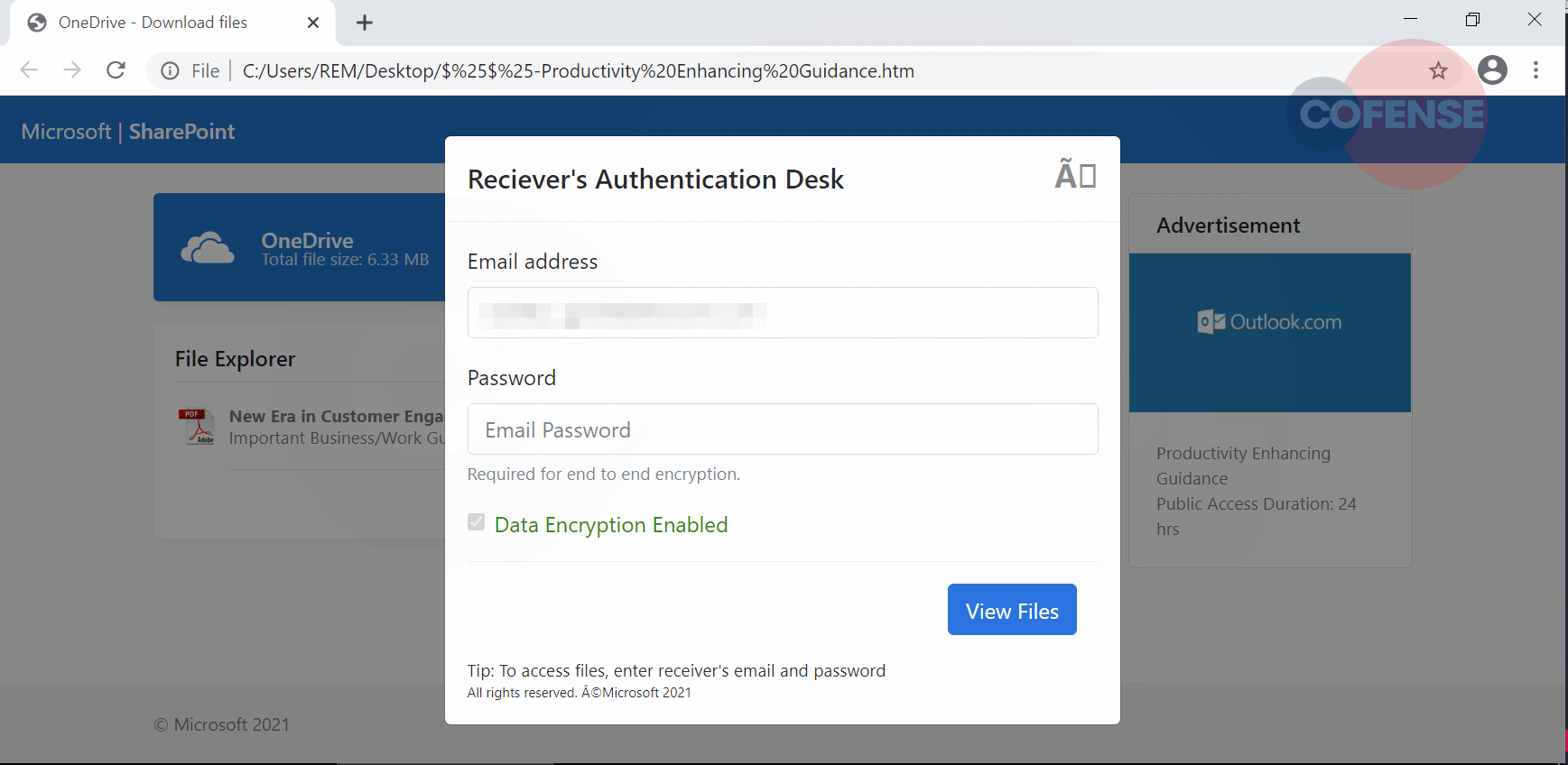
Once the attachment has been opened, it redirects the user to a Microsoft SharePoint webpage with a OneDrive banner, as shown below in Figure 2.
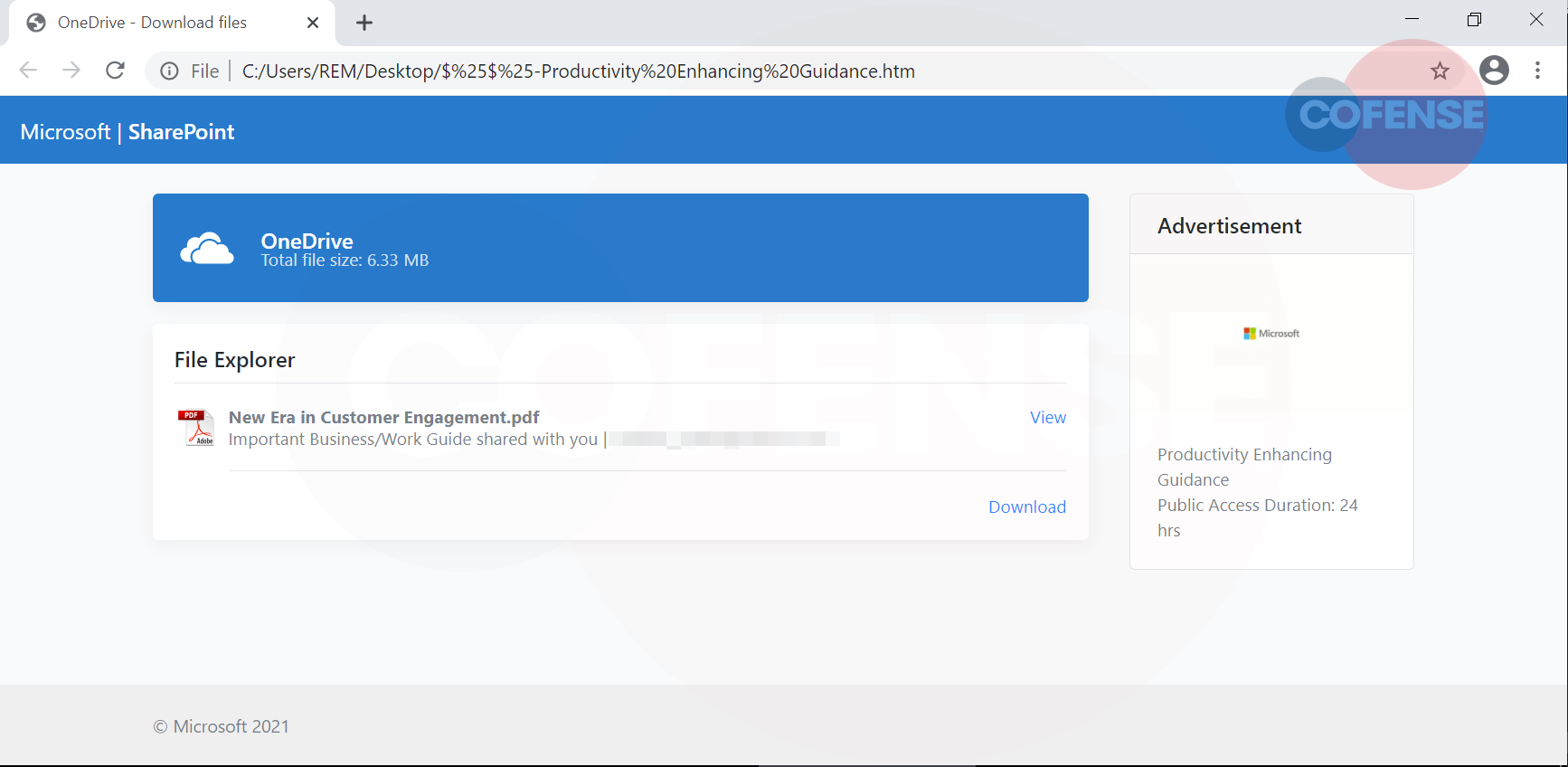
The URL is not evident within the address bar of the web application. The webpage contains a convincing looking PDF file named “New Era in Customer Engagement.pdf,” which has options to either “view” or “download.” Upon further inspection, we note that both options lead to the same outcome – a pop-up sign-in page appears. The threat actor has even gone to the effort of including a “secure” message: “Data Encryption Enabled” in a bid to socially engineer the user into thinking they are being authenticated legitimately.
Figure 3 – Second Redirect (Phishing landing page)
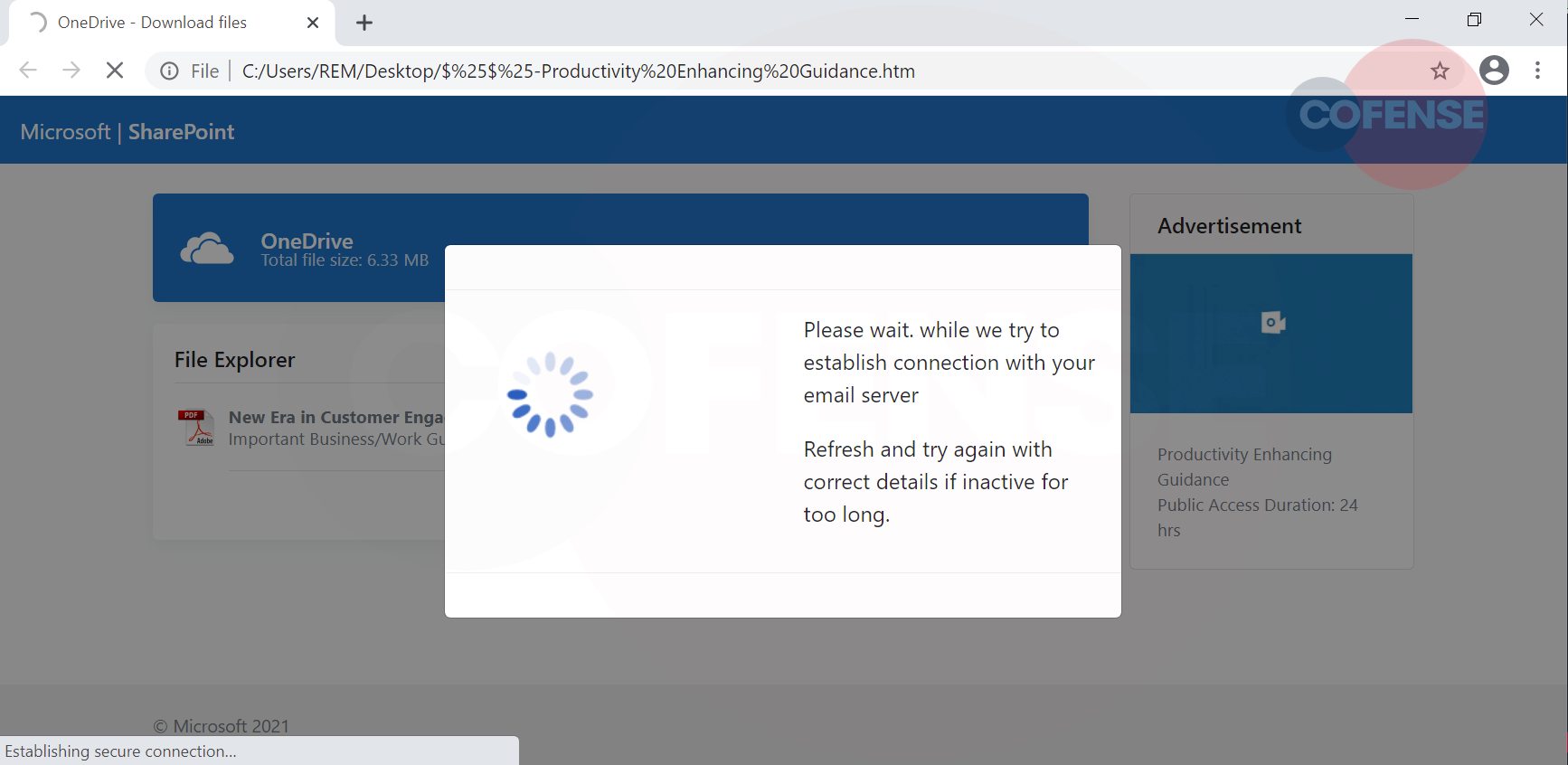
Furthermore, additional security phrases, such as “Required for end-to-end encryption,” display. Once the user has entered their password, a loading page appears that acts as though a secure connection has been establishing. This is shown in Figure 4. Should the user login with their actual credentials then, unfortunately, their data is exfiltrated to the threat actor.
Figure 4 – Loading Page
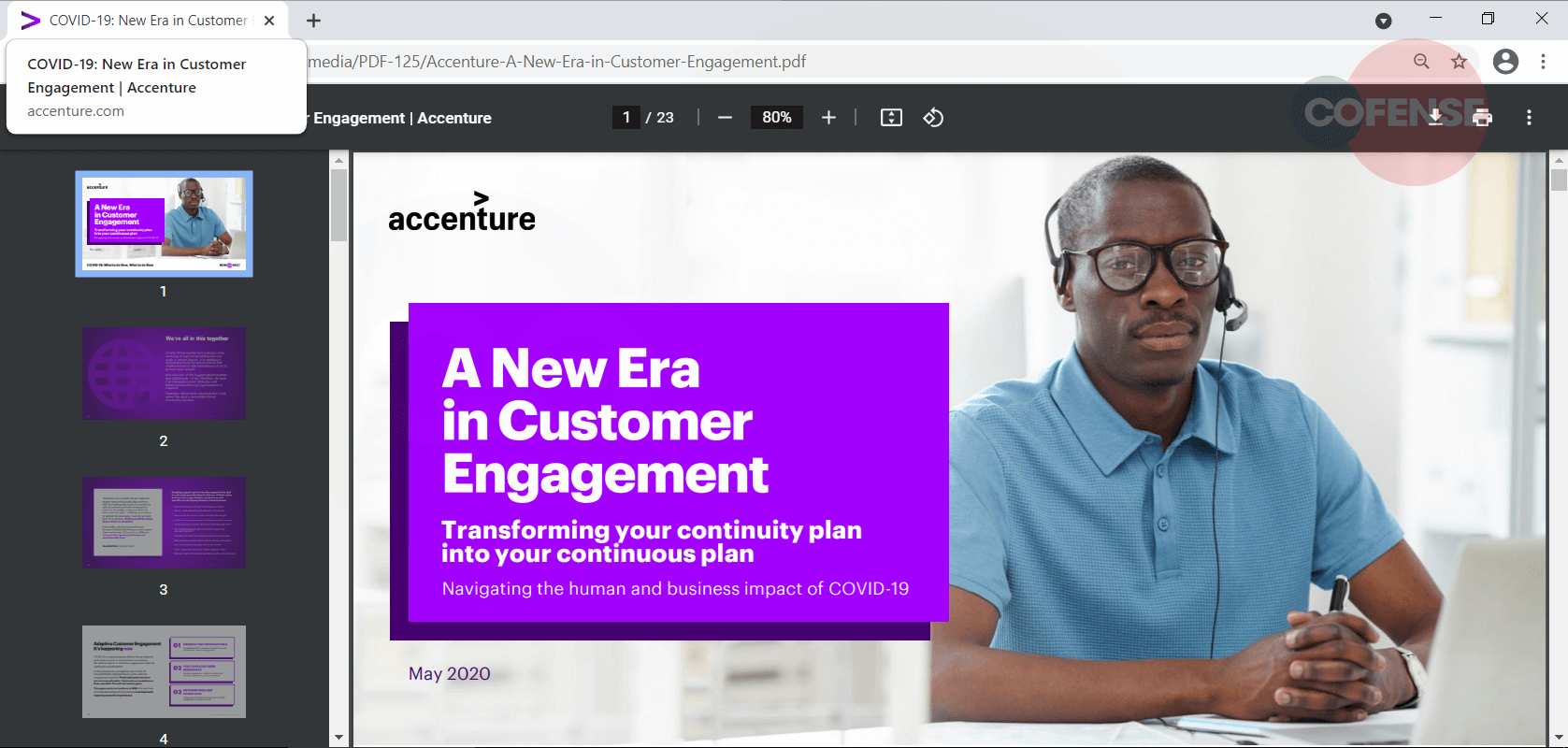
Finally, the last stage of this campaign redirects the user to a random PDF document shown in Figure 5. A common tactic used by threat actors to divert attention and suspicion from malicious activity is to provide the document referenced in an earlier step. The content of the document doesn’t correspond to the attachment name, which is “Productivity Enhancing Guidance.”
Figure 5 – Redirect
This campaign showcases the fact that threat actors are constantly innovating and trying to improve on their techniques to trick users while bypassing existing security protocols to steal credentials. These attachment emails are hard to stop by security protocols such as SEGs, and they force the user to click on the attachment to learn more. A well-conditioned user alerted us to this campaign upon recognizing suspicious elements of the phishing email . They used Cofense Reporter to quickly send it to us for evaluation and remediation.
| Indicators of Compromise | IP |
| Hxxps//winsoftsolutions[.]xyz/369065cp065cps036ess/ | 104[.]168[.]145[.]194 |