Bitcoin and most other cryptocurrencies are based on the idea that coins can be generated by causing computers to solve a difficult problem. The more CPU cycles an individual can dedicate towards the mining problem, the more likely the chance that they will create a new coin. For years, botnets have scanned corporate networks for high-powered machines and installed Bitcoin or other cryptocurrency mining software on the fastest computers. We’ve seen a wide variety of methods for infecting people with cryptocurrency miners, with Monero miners being launched as stand-alone malicious executables since June 2017 after users unwittingly open a malicious Word document attached to an email message, causing the Monero-mining executable to be downloaded from the Internet and launched.
More recently, the news has been riddled recently with stories about a particular Monero mining software that runs in a browser. The site most commonly associated with this behavior is CoinHive. The level of exploitation is such that recently CheckPoint Software said that CoinHive Miners were their “Most Wanted” malware, with at 55% of their customers having been exposed to one or more cryptocurrency mining malware families.
We know from experience that many email recipients, even if they believe an email is likely to be a phish, will still click on it simply because they are curious. Many believe that if it is a phish, they will be smart enough to recognize it once they see the page and “not fall for it.”
The growing trend now is to embed the miner into more traditional credential-phishing sites, where an email lures users to a fake website designed to steal the userid and password to an online service, email system, or financial institution. When this approach is used, popular browsers launch instances of themselves which are hidden from the user, allowing coin-mining to continue in the background even if the user has closed all of the browser windows he or she can see.
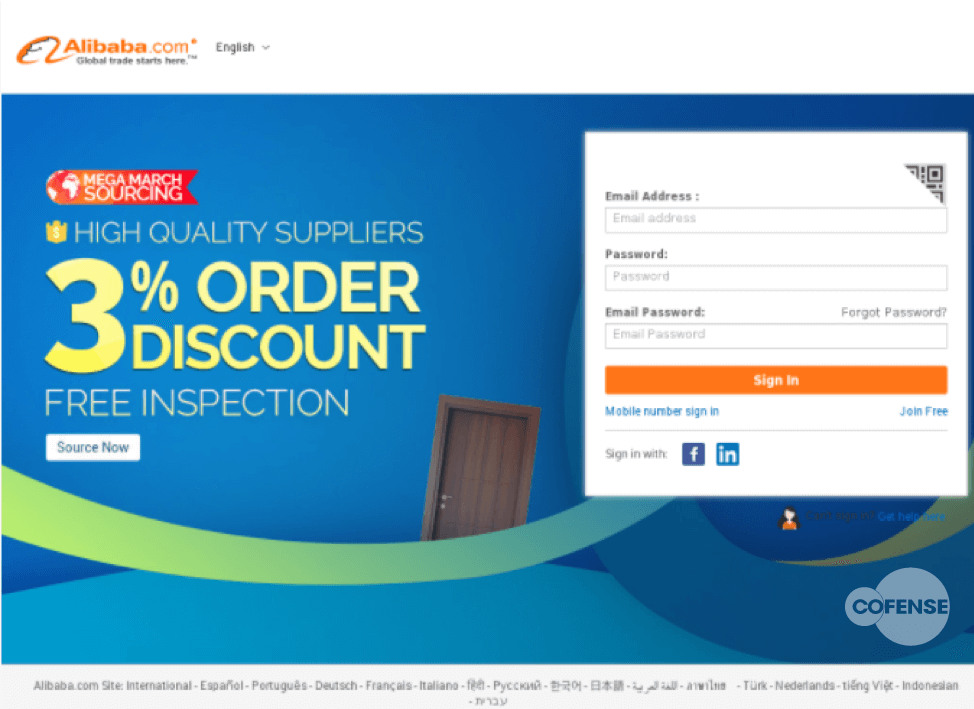
And here is where CoinHive and phishing collide. Consider for example this Alibaba phish. In this case, the phisher has modified his phishing website to load a tiny javascript program from a hard-coded IP address in Brazil, which in turn loads a full Monero CoinHive-based Miner.
Figure 1 – An Alibaba Phish – PhishMe Threat ID: 26007111
In the HTML Source code for this page is a tiny Javascript file, which in turn calls a much larger script from a hard-coded IP address in Brazil, seen on both Alibaba and Banking phishing websites. This script opens 32 Miner threads, each in a separate invisible window in the victim’s browser by passing credentials to CoinHive.com via the “WebSocket Shards” protocol.
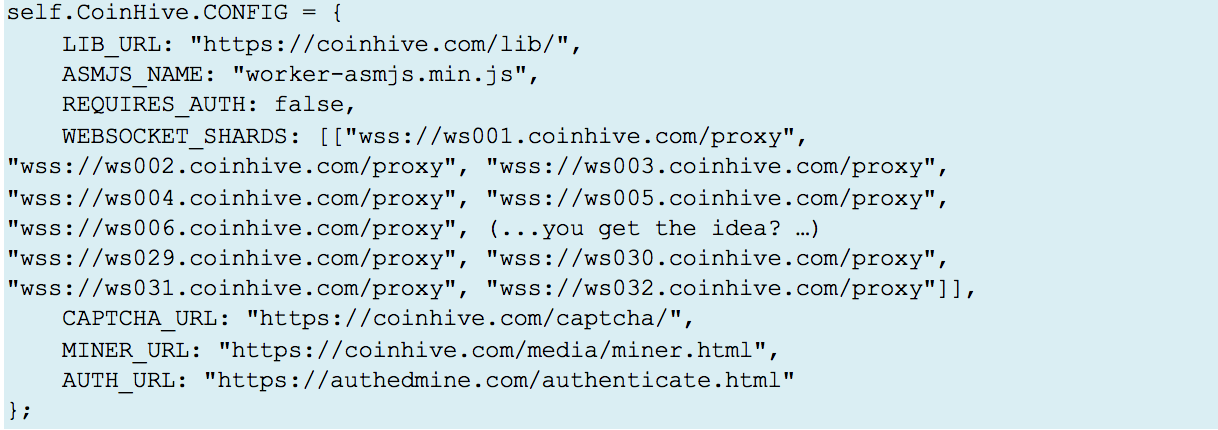
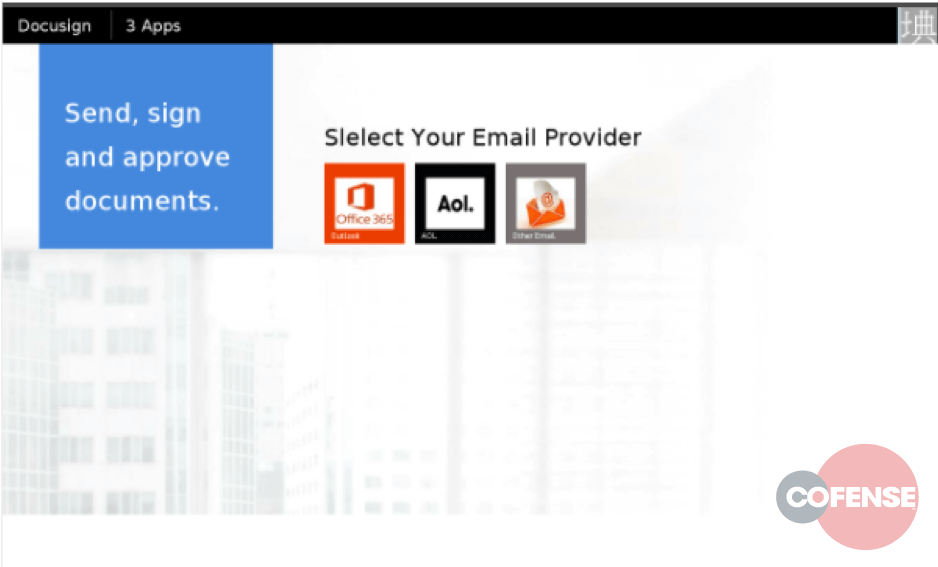
Figure 2 – Docusign Phish (email credential stealer) – PhishMe ThreatID 25865106
Although the phisher did not include the CoinHive code, the WordPress site which was hacked by the phisher to host his DocuSign phish was ALSO hacked to install a CoinHive-based Monero miner in such a way that every visitor to the site began to mine Monero. Although Sucuri reported back in September that CoinHive miners had been seen on hacked websites, it was not until late December 2017 that we saw massive exploitation of WordPress sites to install CoinHive Miners, as documented by BleepingComputer. This attack was quite successful, earning the hackers at least $100,000 worth of Monero in just two of the Monero wallet addresses observed by security researchers. Other researchers have also reported wide delivery of this malware, including Malwarebytes, who says they block CoinHive related API calls as many as 8 million times per day!
Recommendations
We’ve now evaluated dozens of phishing sites that launch “in the browser” Crypto-miners, both those that have been intentionally placed by the phisher, and those who are placing their phishing sites on pre-compromised servers, and so far, they have all been linked to CoinHive. While I’m sure that there may be legitimate reasons that a company might want their idle machines to mine for Monero on their behalf, we suspect most businesses would rather not have their machines used to enrich strangers. I simple fix? Consider blocking all access to “coin-hive.com” on “coinhive.com” from your network (as access shouldn’t be needed for your employees’ day-to-day work at any rate!). Be aware that if these URLs are blocked, some javascript that we have seen will load the session from an alternatively named domain, so a wise network administrator might observe traffic immediately AFTER rejecting traffic to CoinHive just to be extra cautious. While there are other browser-based mining scripts, this is currently the site we are seeing most actively exploited. Many anti-virus products also provide protection from this class of “Probably Unwanted Programs”, and there are even browser-plugins, such as “No Coin” that are said to offer protection.
Sign up for free threat alerts from Cofense Intelligence™ and Cofense Research.