Mimecast
By Deron Dasilva and Milo Salvia
Last week, the CofenseTM Phishing Defense CenterTM saw a new barrage of phishing attacks hiding in legitimate PDF documents, a ruse to bypass the email gateway and reach a victim’s mailbox. The attacks masquerade as a trusted entity, duping victims into opening what appears to be a trusted link, which in turn leads to a fake Microsoft login page. Once there, victims are tricked into providing their corporate login credentials.
Here’s how it works.
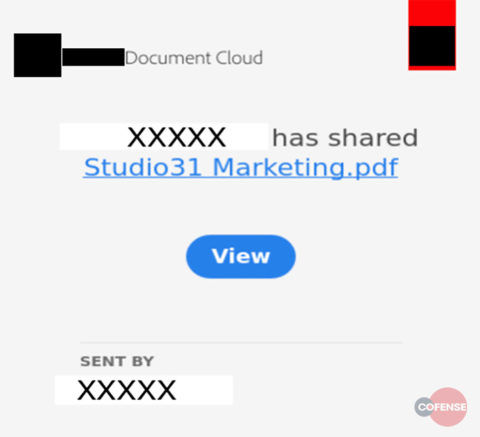
Email Body: From the message body we can see that the victim received an email from a legitimate website, asking them to view the shared document. This is one of the most common attack methods Cofense sees. It works because it uses a legitimate service to evade detection.
Fig 1. Email Body
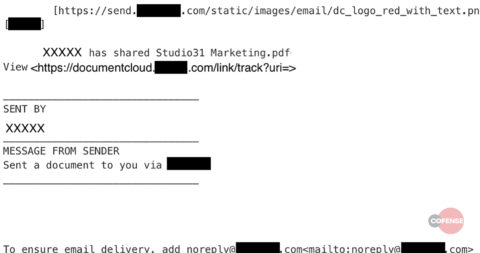
Message Body in Plain Text: If we take a deeper look into the message body, we can see there’s an embedded hyperlink leading to the legitimate website. The site even provides an advisory stating that you should whitelist their domain to ensure delivery of their emails. By using this site to hide their malicious link, the attackers make it nearly impossible to determine whether this document is a phish or a legit email.
Fig 2. Email Body in Plain Text
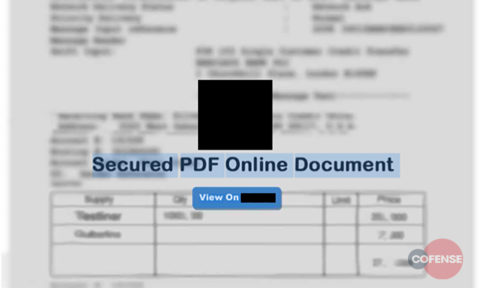
Execution: Once the recipient goes to the website, everything looks fine. You’re about to view a genuine document. Sure…
Fig 3. Execution
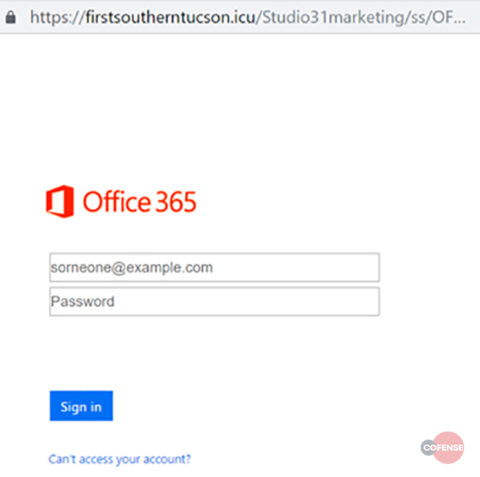
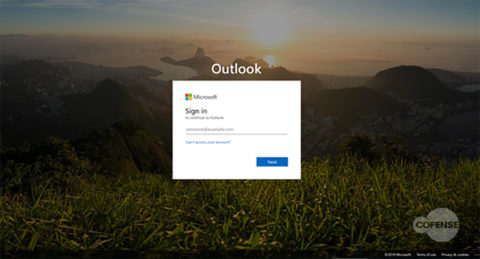
Phishing Page: After clicking the ‘view document’ button, you’re taken to another website that appears to be a Microsoft SharePoint site. But if you look closer, you will notice the URL hxxps://firstsoutherntucson[.]icu/Studio31marketing/ss/ does not match up to a legitimate Microsoft webpage.
Here, victims are tricked into giving their username and password. Once their credentials have been harvested, they’re redirected to the real Microsoft page. This technique is extremely effective, since it plays on human trust in popular business tools.
With the victim’s credentials in hand, the attacker can do many things: launch business email compromise (BEC) attacks, attempt identity theft, inflict financial losses on the user or the business, and even prevent users from accessing their own accounts to cripple productivity.
Fig 4. Phishing Page
Email gateway: This threat was found in an environment running Mimecast’s secure email gateway.
Conclusion: Malicious attachments, especially ones abusing trusted services, are a proven way to evade gateway detection and deliver phish. It’s smart to train users, like the ones that reported these attacks, to recognize and report phishing emails.
Protect your organization from attacks with our team of experts at the Cofense Phishing Defense Center™ (PDC). The Cofense PDC provides skilled resources to overwhelmed security and incident response teams. We specialize in defending against phishing attacks and have visibility into the threats that other security solutions miss.
Learn more about the Cofense Phishing Defense Center. Our team analyzes emails reported by customers’ users and supplies actionable intelligence to accelerate mitigation.