On Monday May 28, 2018, during routine operations, Cofense Intelligence™ identified traits across several campaigns that indicated they were linked. In fact, this discovery helped to reveal a sprawling criminal enterprise that uses linked infrastructure to host nearly 100 domains, along with corresponding malware campaigns.
At the early stages of the investigation, it was not possible to tell whether the similarities were the fingerprints of a specific actor or group, or if they were simply the artifacts of an email-templating kit, many of which are sold on the Dark Web. Scraping a little dirt away from the surface, the link between the campaigns seemed to be more than the mere residue of an automated toolkit.
Not only did the emails share traits, but the malware being delivered used an interconnected C2 infrastructure. With a combination of OSINT, freely available tools and proprietary infrastructure, Cofense Intelligence was able to pivot from a single indicator of compromise, to uncover a widespread criminal network.
Note: all ‘From’ fields depicted in this blog were spoofed by the attacker.
The Campaigns
Table 1 lists the six campaigns and their respective subject lines.
| Threat ID | Subject | Family |
| 11802 | RE: Bank Account Re-Confirmation URGENT!!! | Pony |
| 11801 | Payment Advise | Pony |
| 11800 | Ref | Pony |
| 11799 | Re: Freight Remittance | Pony |
| 11798 | RE: CONFIRM REMITTANCE | Pony |
| 11797 | RE: Problem with intermediary bank | Pony |
Table 1: Details of the campaigns that began the unmasking of this infrastructure
Despite there being a small amount of narrative overlap, each of these are generic enough to easily be construed as ‘just another Pony campaign’. The filenames used by these campaigns are as generic and distinct as the subject lines, as shown in Table 2.
| Threat ID | Filename | MD5 |
| 11802 | scan#0043221588FD_pdf.gz | 00e3cd63809c75894140842662afa8ba |
| 11802 | scan#0043221588FD_pdf.exe | e272d7929f073ad5590d39874414b609 |
| 11801 | doc#00645511089ZQ_pdf.exe | a73176f56c65e66c58361333ae90ff53 |
| 11801 | doc#00645511089ZQ_pdf.gz | 279f57837f1b2145bc7b506ed9bb53fc |
| 11800 | Final Invoice.pdf.zip | 148272fc803280662178e4241d11abbe |
| 11800 | Final invoice.exe | dc9582e50bca2540db32cefca5e2d378 |
| 11799 | scan#0015889820TT_pdf.gz | 4706f193903e2b242ffe0f06e13eb755 |
| 11799 | scan#0015889820TT_pdf.exe | 8f8bafc1d733b00ef3a2bf1424b057e7 |
| 11798 | Swift-Ref MIDLRZ31..exe | 85fd5a8cf30be8e3c361dc082d5e3c3c |
| 11798 | Swift-Ref MIDLRZ31..arj | 63d45d80cd7bfe71bd3252a7db8bc4a9 |
| 11797 | scan_05a-028_pdf.exe | 9fe3ba4abfb1cf6fe37a7658af972a2a |
| 11797 | scan_05a-028_pdf.arj | f1ab0bc861284dde66a1dc0628ab8e66 |
Table 2: The files used across the six initial campaigns
A tighter correlation was starting to emerge. Threat IDs 11802, 11801, 11880 11799, and 11797 all had filenames suffixed with a mock double-extension of _pdf.exe, or .pdf.zip.
Although a pattern can be discerned between about 83% of the campaigns, the omission of the final piece of the puzzle – namely Threat ID 11800 – there is far more to observe and correlate. The headers for these messages provided yet another clue to their origin.
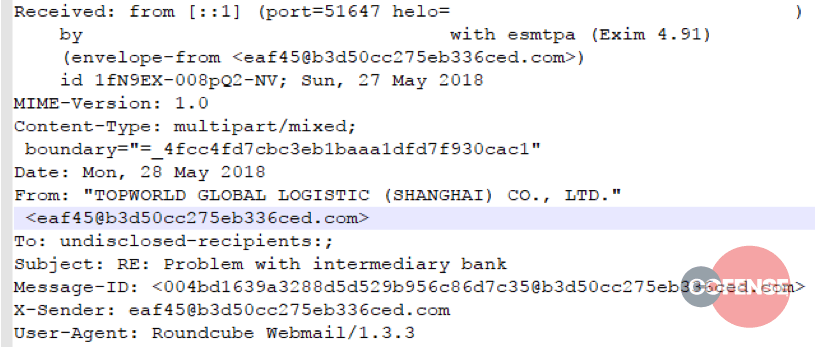
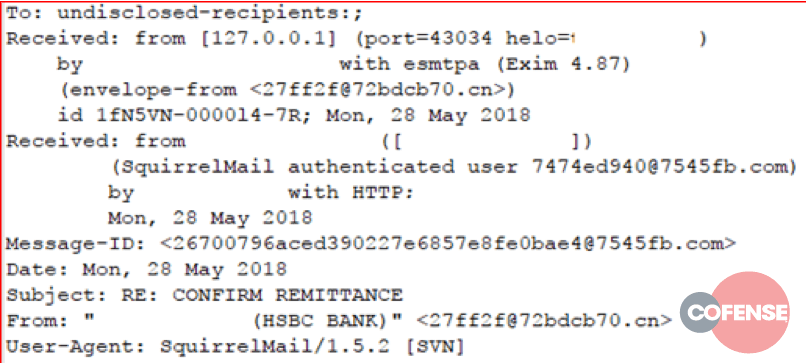
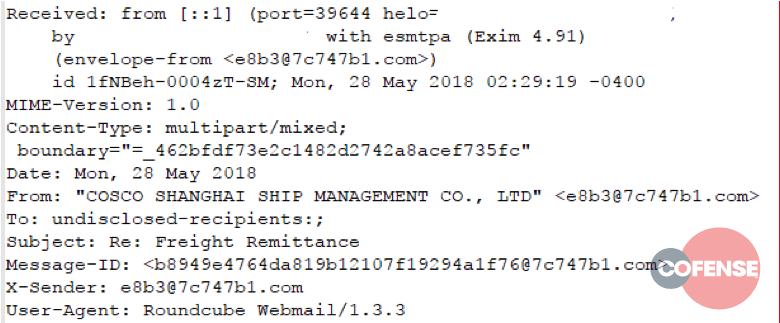
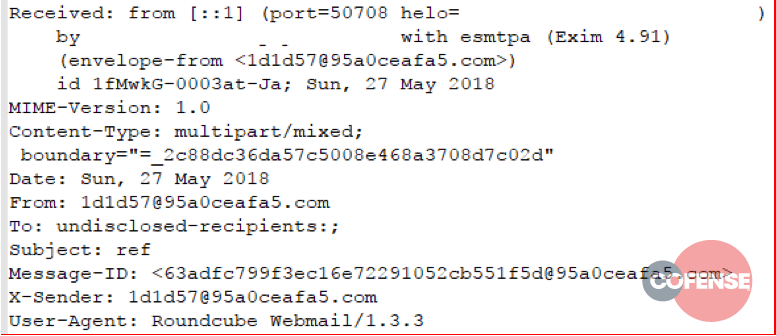
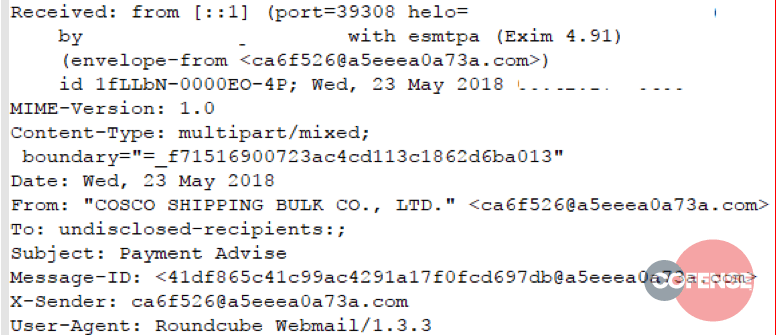
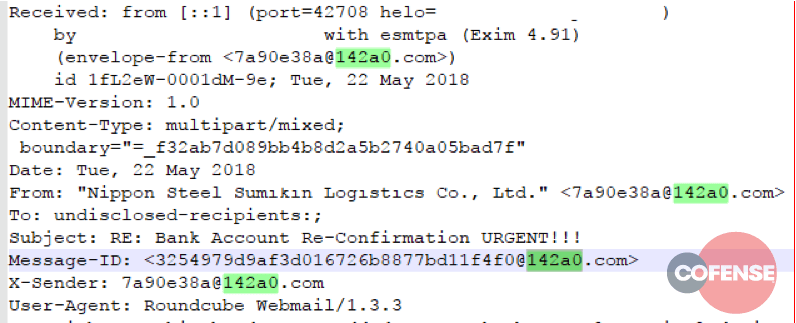
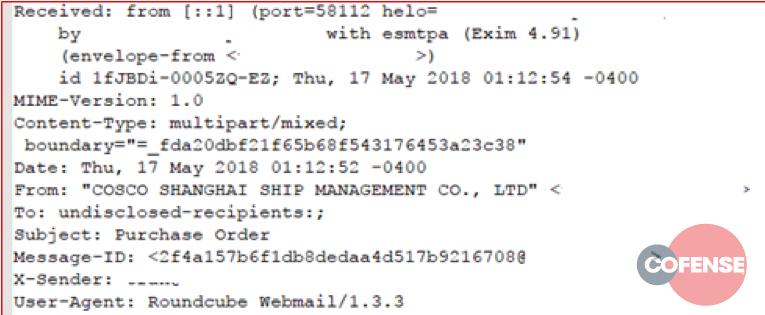
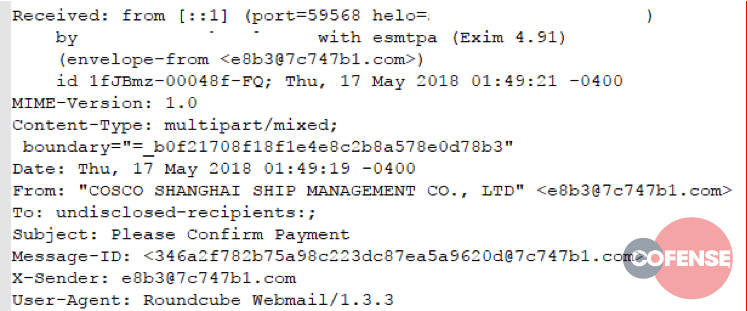
Figures 1 through 6 show example message headers for each of the campaigns.
Figure 1: Example message header from Threat ID 11797
Figure 2: Example message header from Threat ID 11798
Figure 3: Example message header from Threat ID 11799
Figure 4: Example message header from Threat ID 117800
Figure 5: Example message header from Threat ID 11801
Figure 6: Example message header from Threat ID 11802 with forged from domains highlighted
What can we glean from these message headers? An incredible amount of data. The first thing that should be noted is these messages all originated from servers running Exim MTA. In March of 2018, a critical vulnerability – 2018-6789 – allowed Remote Code Execution (RCE) on any version of Exim prior to 4.9.1. Although 5 out of 6 MTAs involved in these campaigns report as running version 4.9.1 – the version in which 2018-6789 was fixed – it’s almost certain that these servers were compromised prior to the patch being applied, and that the persistence mechanism injected into the compromised server is still functional.
There are several other circumstantial pieces of evidence in the header content:
- The To: field is always set to ‘undisclosed-recipients;’
- The messages all contain a single hop (one received from Header) or are proxied through a same-origin front end (the messages in campaign 11797 use SquirrelMail as an interface with Exim)
- Except for 11797, all messages use a RoundCube User Agent
- Many header fields contain the same random, faked email address or email address-like structure
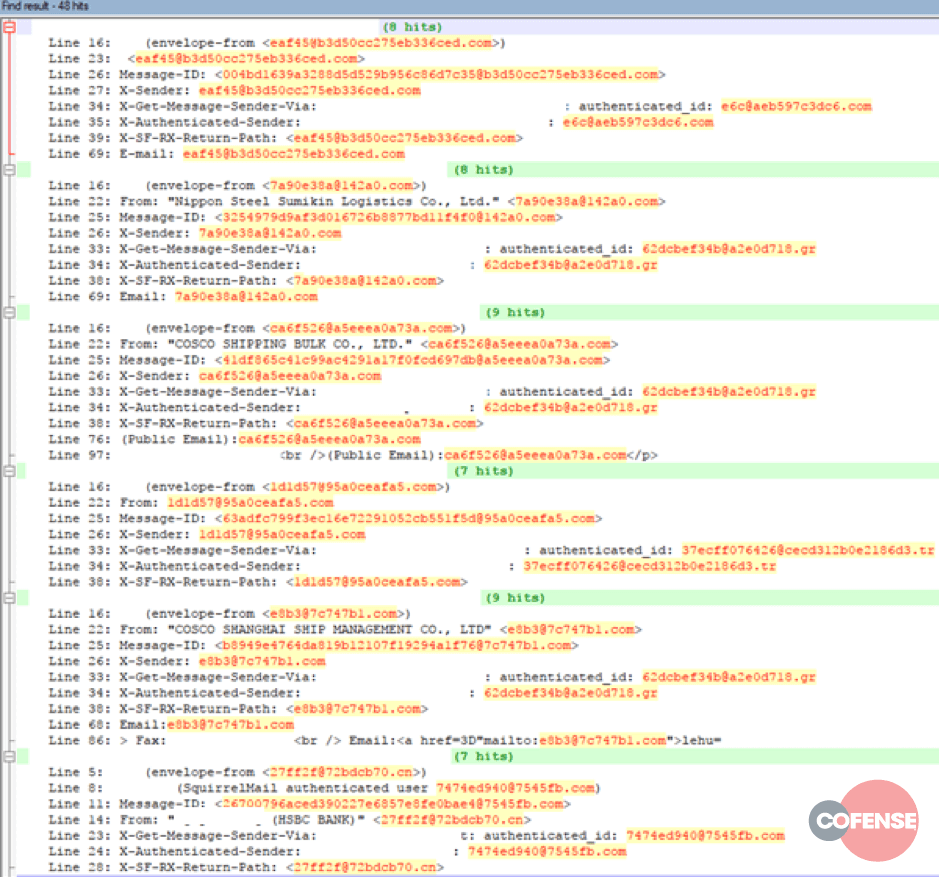
Although programmatically difficult to describe with any accuracy, the email addresses, X-Sender, and Message ID fields all follow a very distinct pattern: a series of hex characters, an ‘@’ symbol, more hex characters, a dot, then a gTLD or ccTLD. Given the limited sample size, we can loosely describe this pattern with a regular expression: +@+.+
Parsing our example messages, we get a clearer understanding of these structures, as seen in Figure 7.
Figure 7: Spoofed message headers containing random, hex-based email address and domains
Each individual element that we’ve discussed so far could be dismissed as circumstantial. To that end, we can begin working backwards, from an IoC chosen from Table 3, to a Threat ID, and associated messages.
| Threat ID | Block Data | Type | Impact |
| 11802 | 185[.]6[.]242[.]251 | IPv4 Address | Minor |
| 11802 | hxxp://stauniverseqp[.]com/roks9/gate[.]php | URL | Major |
| 11802 | stauniverseqp[.]com | Domain Name | Major |
| 11801 | 185[.]6[.]242[.]251 | IPv4 Address | Minor |
| 11801 | swift-be[.]com | Domain Name | Moderate |
| 11801 | hxxp://swift-be[.]com/roks7/gate[.]php | URL | Major |
| 11800 | swift-be[.]com | Domain Name | Major |
| 11800 | 185[.]6[.]242[.]251 | IPv4 Address | Major |
| 11800 | hxxp://swift-be[.]com/roks6/gate[.]php | URL | Major |
| 11799 | hxxp://stauniverseqp[.].com/roks9/gate[.]php | URL | Major |
| 11799 | stauniverseqp[.]com | Domain Name | Moderate |
| 11799 | 185[.]6[.]242[.]251 | IPv4 Address | Minor |
| 11798 | viettrust-vn[.]net | Domain Name | Moderate |
| 11798 | 185[.]6[.]242[.]251 | IPv4 Address | Minor |
| 11798 | http://viettrust-vn[.]net/adin/gate[.]php | URL | Major |
| 11797 | 185[.]6[.]242[.]251 | IPv4 Address | Minor |
| 11797 | http://swift-be[.]com/roks5/gate[.]php | URL | Major |
| 11797 | swift-be[.]com | Domain Name | Moderate |
Table 3: IoCs associate with the six campaigns
Of note are the multiple different overlaps in the data. Threat IDs 11797, 11800, and 11801 share a domain. 11802, 11801, 11800, 11799, and 11797 all adhere to the same URL structure. Unfortunately, neither of these overlaps are conclusive nor ubiquitous throughout our data set. There is, however, a single node that will give us the perfect platform from which to pivot: the resolved IP address for each domain, is the same:
185[.]6[.]242[.]251
185[.]6[.]242[.]251 is the final stitch that secures the tapestry of these campaigns. Given the ease with which internet resources can be obtained by malicious actors, and the sheer number of candidates available, having the same IP used to house infrastructure across six campaigns removes any doubt about this being a coincidence.
This IP functions as a pivot from which we can invert our previous efforts – in which we identified a campaign or campaigns and followed the trail until we reached an IoC – such that we can obtain campaign IDs from a single node.
We can now identify 48 distinct campaigns launched between 2018-04-13 12:45:03 and 2018-05-28 10:53:17. These campaigns served either Pony or Loki directly. Table 4 details a small subset of these findings.
| Threat ID | Block Data | IP | Family |
| 11780 | http://sunnynaturelstone[.]com/bally/five/fre[.]php | 185[.]6[.]242[.]251 | Loki |
| 11751 | http://dunysaki[.]ru/doncha-2/fred[.]php | 185[.]6[.]242[.]251 | Loki |
| 11741 | http://stauniverseqp[.]com/roks9/gate[.]php | 185[.]6[.]242[.]251 | Pony |
| 11740 | http://stauniverseqp[.]com/roks9/gate[.]php | 185[.]6[.]242[.]251 | Pony |
| 11729 | http://swift-be[.]com/roks7/gate[.]php | 185[.]6[.]242[.]251 | Pony |
| 11696 | http://joanread[.]ru/steph/fred[.]php | 185[.]6[.]242[.]251 | Loki |
Table 4: Some additional campaigns identified after pivoting from 185[.]6[.]242[.]251
These campaigns included malicious files as seen in Table 5.
| Threat ID | Filename | MD5 |
| 11780 | SCAN_DOC.zip | 61e85ba9cd0af9af699f5cab6fb65314 |
| 11780 | SCAN_DOC.exe | bc07cee626771b0b7decc39898bb2c10 |
| 11751 | PO4521.XLS | 5e1bbdb9cc30cd12e4727a39adc3250e |
| 11751 | msbu.exe | c72240663e68b69dfed6650d93f5cadb |
| 11741 | doc#00089852205FZ_pdf.exe | 218361dd4dce4cca77c2018991074e09 |
| 11741 | doc#00089852205FZ_pdf.gz | 68e7c7a2b3ea97ca7a38b3f12f222d36 |
| 11740 | doc#00089852205FZ_pdf.gz | 68e7c7a2b3ea97ca7a38b3f12f222d36 |
| 11740 | doc#00089852205FZ_pdf.exe | 218361dd4dce4cca77c2018991074e09 |
| 11729 | invoice#1550013485GZ_pdf.gz | 3e0b375e2a7bd99b3d104289d5f15ac5 |
| 11729 | doc#001500011185GZ_pdf.exe | 063888eed4aa7770f850b328a3cc7ab0 |
| 11696 | 511036970.XLS | e0b87b8b812d5a4bf2dbb12aff744072 |
| 11696 | 153414.exe | edae59ba0c5948e7bd0f45a1545ff585 |
Table 5: Companion malicious files to Table 4
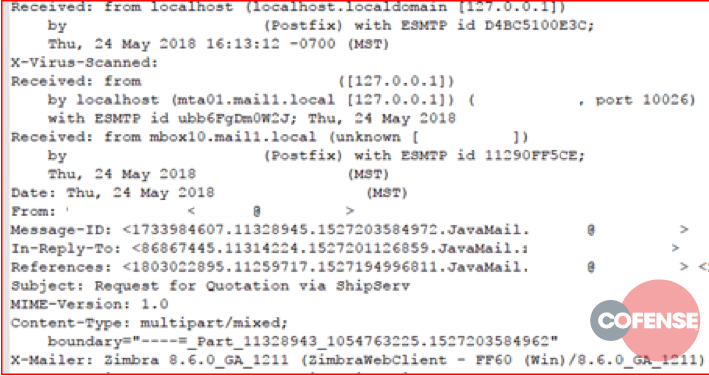
Figures 8 through 10 provide example message headers for these campaigns.
Figure 8: Example message header from Threat ID 11729
Figure 9: Example message header from Threat ID 11741
Figure 10: Example message header from Threat ID 11780
Messages in Threat IDs 11729 and 11740 show significant similarities with our initial six campaign message sets. Messages in 11780, however, are distinct from the observed consistencies in other campaigns. Despite being linked by the IP address, this campaign clearly bears no similarities with the other campaigns. This is likely because the actors controlling this campaign channel kept their tactics diverse, or the web server being used to host the C2s is shared among threat actors.
Where Do We Go From Here?
Despite demonstrating impressive correlation between Cofense™-identified campaigns, there is much more we can do to further investigate this infrastructure. Most importantly is to perform a Reverse DNS lookup to find domains hosted on an IP. Using an rDNS on our node, we can see what other sites may be lurking there. Table 6 details just such a lookup.
| Domain | IP | Email Address/Domain Count | Date Registered |
| Stauniverseqp[.]com | 185[.]6[.]242[.]251 | Grace[.]miller85@mail[.]ru 25 domains | 2018-04-04 |
| Theonlygoodman[.]com | 185[.]6[.]242[.]251 | greejames63@gmail[.]com 2 domains | 2017-07-04 |
| Domainsender[.]info | 185[.]6[.]242[.]251 | ifeanyiblunt@gmail[.]com 15 domains | 2017-11-19 |
| tiwana[.]website | 185[.]6[.]242[.]251 | rizmatseal@gmail[.]com 6 domains | 2018-01-18 |
| Sunnynaturelstone[.]com | 185[.]6[.]242[.]251 | Soft[.]mr@mail[.]ru 79 domains | 2018-04-12 |
| Uniqscans[.]com | 185[.]6[.]242[.]251 | whelas8@yandex[.]com 42 domains | 2017-09-03 |
Table 6: A small subset domains hosted on our node, as found during our rDNS pivot on 185[.]6[.]242[.]251
At the time of writing, there are 24 domains that resolve to 185[.]6[.]242[.]251. Of these, 19 are registered with Freemail addresses; 5 are registered with WhoIs privacy guards. Drilling down into these email addresses reveals 206 additional domains. These domains directly correspond to 28 separate campaigns, as far back as May 22, 2017. This brings the total number of linked campaigns to 96.
Understanding the way threats interact is a key component of responsive, and in many cases, predictive analytics. By discovering a unique feature and pivoting intelligently, it’s possible to uncover a veritable mountain of data from a single, initial node. Adding in recursion can, for all intents and purposes, lead to an infinitely connected series of domains, IPs, URLs, and files. Intelligence deliverables, then, aren’t just about what one directly observes; they’re about inference, judgement, and tenacity.
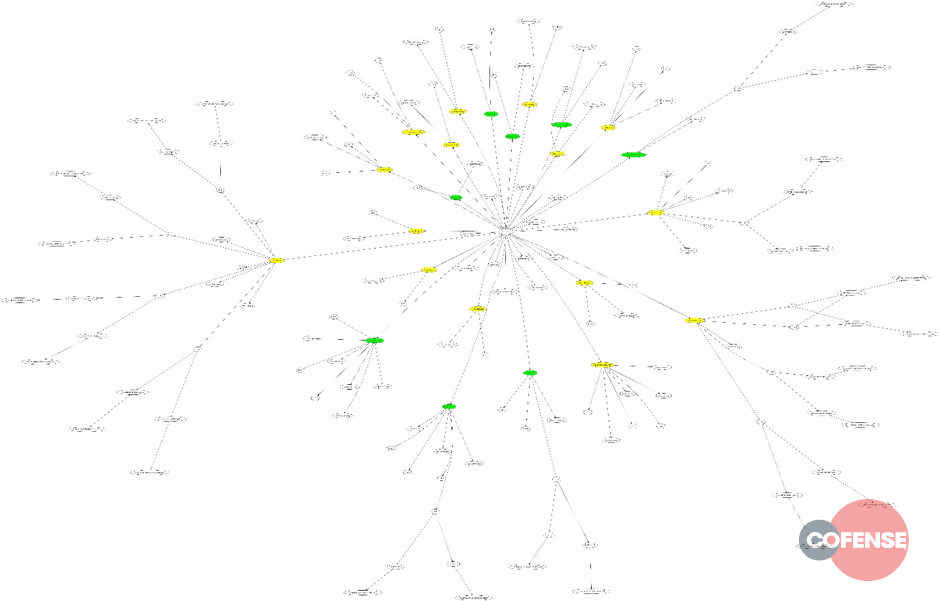
Here’s a visualization of the data points in this blog:
For a comprehensive analysis of the past year in malware, plus a look ahead, view the 2018 Cofense Malware Review.