CISO Summary
Since the latter part of 2018, threat actors have increasingly exploited two Microsoft vulnerabilities: CVE-2017-11882 and CVE-2018-0802. The first of these is especially popular. Cofense IntelligenceTM has seen it surge ahead of Microsoft macros as a favorite malware delivery method.
CVE-2017-11882 is an older vulnerability that in fact has a patch. However, it presents a conundrum for security teams that haven’t addressed the problem. They can choose to skip the patching, live with the risks, and keep on using the legacy program. Or they can update, patch, and lose the application entirely to gain much better security.
In the meantime, threat actors will happily exploit every chance they get.
Full Details
The vulnerabilities in Microsoft’s Equation Editor that are exploited in CVE-2017-11882 and CVE-2018-0802 have been “patched” for over a year. However, these vulnerabilities remain popular with threat actors and have become increasingly common since their inception. There are several factors involved, but Cofense Intelligence assesses that CVE-2017-11882 is still commonly used simply because it works, reaffirming the challenges associated with patching and the risks of operating legacy platforms. CVE-2017-11882 still works as a delivery mechanism on unpatched or unsupported versions of Microsoft Office and is most commonly used to deliver simple information stealers.
The Progression
In September 2018, Cofense Intelligence covered the most common malware delivery methods and highlighted Microsoft Office macros as making up the majority of the most common malware delivery methods. Over the last six months, we have observed a sharp increase in the exploitation of CVE-2017-11882.
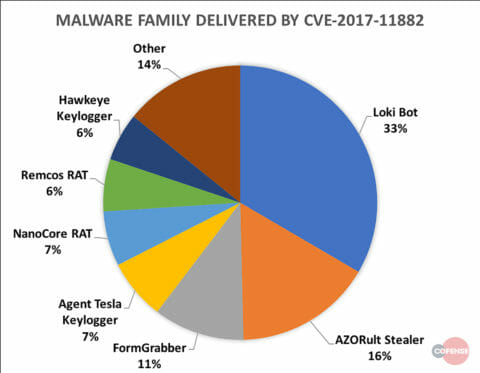
The threat actors who switched to using CVE-2017-11882 as their primary delivery method focused significantly on information stealers, such as Loki Bot and AZORult, which make up 33% and 16% of the malware delivered respectively. In contrast, the most common Remote Access Trojan (RAT) is NanoCore RAT, which is the fifth most frequently malware delivered at only 7%.
Figure 1: Frequency of malware family delivered by CVE-2017-11882
But You Said There is a Patch!
Cofense Intelligence assesses that the most common reason CVE-2017-11882 still works for threat actors is that the patches intended to remedy it simply are not in place on several endpoints. Rather than assuming that support teams are incompetent, given that over a year has passed since the first patch, it is more likely that companies are being faced with a product support conundrum.
Businesses must choose between two options. The first is accepting a level of risk and continuing to use legacy programs by not patching. The second is to update, patch, and in this case, allow the removal of an application entirely in order to have significantly higher security. This is much easier for large businesses with great resources to devote to upgrades and security. For smaller businesses—including boutique subsidiaries of major businesses—this is much more difficult. Again, given the amount of time that has passed, it is unlikely at this point that anybody who has not yet updated will do so any time soon, allowing threat actors continued access.
To stay ahead of emerging phishing and malware threats, sign up for a free trial of Cofense™ Intelligence. Learn more about the complete Cofense Phishing Detection and Response here.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks.