Author: Brad Haas
Conti is one of the most prolific ransomware operations in the threat landscape today. In a recent act of retaliation against Conti’s leaders for their support of Russia, an anonymous person leaked documentation and internal chat logs from the group. This blog post series covers important phishing-related takeaways Cofense Intelligence analysts discovered in the leaks. In Part 3, we discuss elements of Conti’s phishing tactics and strategy.
Conti Produces Semi-Random Phishing Templates Using Simple Themes
Although the Conti group employs other malware operators to perform the work of sending malicious emails, it appears that the group provides the templates to use in the emails. Several English-language templates were included in the leaked Jabber chats, indicating a system that randomly chooses words or phrases from short lists. The templates included text that could produce a variety of wordings for email subject lines and bodies, along with a list of attachment names to choose from. Conti member “Lemur” contributed the following order-themed template in October:
lemur:
{Greetings|Hello|Good day|Good afternoon}{!|,|}
{Thank you for|We are grateful for|We are grateful for|Many thanks for} {your|your recent} {online order|purchase order|order}. {We|Our financiers have|Our team has|We have|Our shop has} {received|collected|processed|checked} your {payment|advance payment|money transfer|funds transfer} TRANSFER NUMBER. Now we {are and ready to|begin to} {pack|prepare|compose} your {shipment|order|box}. Your {parcel|packet|shipment|box} {will|is going to|would} {arrive|be delivered} to {you|your residence} within {4|5|6|four|five|six} {days|business days}.
{Total|Full|Whole} {order|purchase|payment} SUM
You {can find|will find} {all|full} {relative information|order info|order and payment details} and your {receipt|check} CHECK NUMBER {in|in the} {attached file|file attached}.
{Thank you!|Have a nice day!}
Subjects: Your {order|purchase|online order|last order} Purchase order number payment {processed|obtained|received}
Attachments:
ord_conf
full.details
compl_ord_7847
buyer_auth_doc
info_summr
customer_docs
spec-ed_info
Dozens of other templates appeared in the chat, with themes including invoices, shipping, payment processing, legal matters, and other business-centered subjects. In a TrickBot chat exchange, two team members discussed a more personal template impersonating a woman looking for a relationship. They went through several revisions, even incorporating feedback from an English teacher.
Conti Actively Develops and Tests Email Delivery Tactics
The spammers who work in and with the Conti organization showed familiarity with automated defenses against malicious email campaigns. In November 2021, “wind” discussed a way to abuse browser-centric email providers to send malicious emails:
wind: it will be necessary to create thousands of such docker containers and send only 10 letters from each mail account, sent by an AI emulator with mouse movements simulating human ones. Every mailer now has an AI, it recognizes all the movements in the browser, and their AI will just laugh out loud at the get requests to send hundreds of thousands of emails.
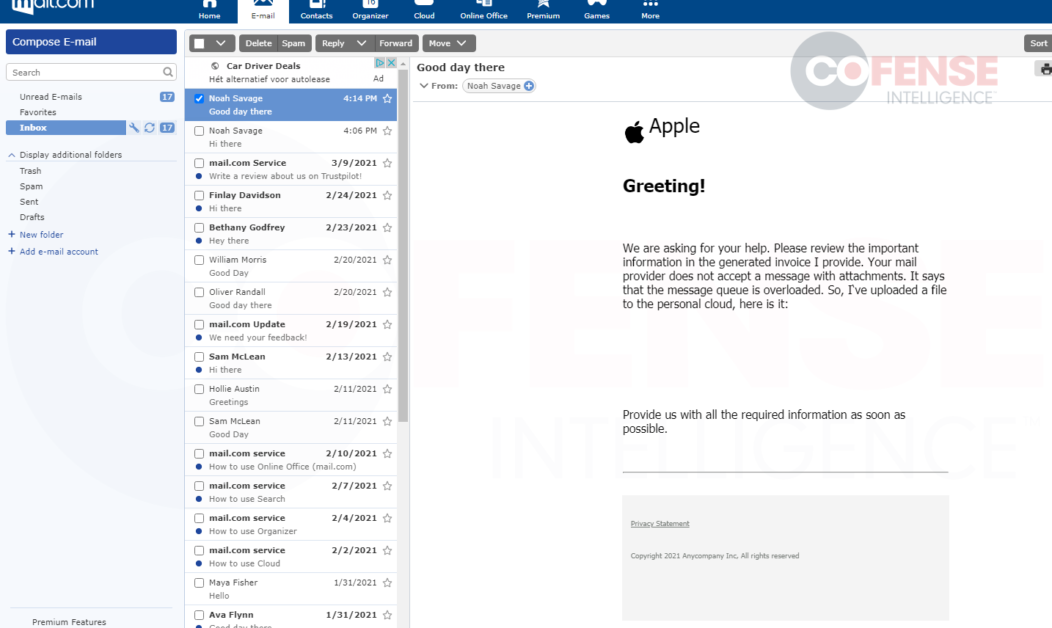
Another message from April 2021 shows an operator testing their emails on webmail platforms Gmail, Yahoo, Outlook, Mail.com, and AOL Mail. They included screenshots showing that an Apple-spoofing email had arrived in each of the inboxes.
A test of an Apple-spoofing email in a Mail.com inbox. The inbox includes several other test emails.
Phishing is Central to Conti’s Attack Strategy
Conti operators consider humans to be an effective target, and phishing is their mechanism for exploiting the human target surface with social engineering. Their “Hacker’s Quick Start” document lists dozens of OSINT sources to use, singling out people as “the weakest link.” The reference to “previously opened networks” indicates a repository of already-compromised data that can be leveraged against new targets.
Next, we look for the weakest link (see below).
Social engineering requires knowledge of personalities.
Everything is important: phone numbers, place of residence, dog’s name, hometown, favorite color, favorite band, hobbies.
Of particular importance: your candidate’s personal network of contacts, especially business contacts.
The structure of organizations reflects the structure of society.
As you move from one person to another through a network of contacts, you can change your entry point within one network, or open up new networks.
Both OSINT intelligence tools are used to gather information,
and information found in previously opened networks about contacts (Outlook address books, correspondence, etc.).
[…]
This data is then used either through phishing emails or phone calls.
In both cases, the load is triggered by a person.
Some of our previous takeaways highlight Conti operators’ consistency in dropping ineffective tactics and persisting with effective ones:
• TrickBot was effective enough for them to enjoy a tremendous amount of success early on, but when it started to cause too many problems, they shifted to other malware families.
• Despite all the attention, they used the BazarCall campaigns, knowing that the invoice theme would likely continue to succeed.
• They went to the trouble of bringing Emotet back, likely because it had been such a significant source of infections for them prior to its takedown.
This pragmatic approach accentuates the value that ongoing phishing activity must be providing to Conti operations. Given all of Conti’s investment in OSINT, email operations, and reviving Emotet distribution, phishing is clearly one of the group’s most important tactics, and it will likely be a staple for the group in the foreseeable future.
For more insights on Conti ransomware operations: