Phishing Incident Response – Human-Verified Phishing Intelligence Meets OSINT
Ransomware, business email compromise (BEC), malware infections, and credential-based theft all stem from a primary vector of compromise – phishing. And no business large or small is exempt!
The attackers continue to hit businesses directly or use a soft targeting approach, which is a combination of business email compromise and spear-phishing. Soft targeting involves a tactic where an attacker will tailor their email to a particular business role (e.g., finance) with slight customization towards their target, such as their name in the salutation. PhishMe has seen an increase in this form of attack throughout 2016.
Across the open, deep, and dark web, attackers tip their hand. The question is: will your business know about these early warning indicators to defend the enterprise?
PhishMe and Recorded Future deliver security teams with enriched, contextualized threat intelligence.
PhishMe Intelligence is 100% human-verified machine-readable threat intelligence (MRTI) and subscribers receive a fully-vetted source of intelligence. PhishMe also provides security teams with context around the criminal infrastructure to extend beyond expected IOCs, and enables teams to see their adversary’s full operation as opposed to one-offs that change rapidly.
Recorded Future enables analysts to capture and exploit relevant threat intelligence from the entire web, in real time. This is made possible by Recorded Future’s patented Web Intelligence Engine, which structures the latest content from the open, deep, and dark web into highly contextualized threat intelligence. As a result, analysts get the benefit of prioritizing their efforts where it matters most.
And for many, phishing is where it matters most. PhishMe Intelligence doesn’t just tell you what is bad, we tell you what is bad and more importantly why, along with all of its associated artifacts in our Active Threat Reports (excerpts below).
“We’re really excited to be partnering with PhishMe! By combining PhishMe Intelligence and Recorded Future’s real-time threat intelligence, we’ve made it really easy for our mutual customers to find hidden connections and research emerging threats faster. An added benefit is that our customers increase the value from existing security investments,” said Glenn Wong, Director of Product Management, Technology Partnerships, at Recorded Future.
Here’s how Recorded Future partnered with PhishMe’s API to allow the analyst to pivot from within Recorded Future into PhishMe’s fully-vetted Intelligence.
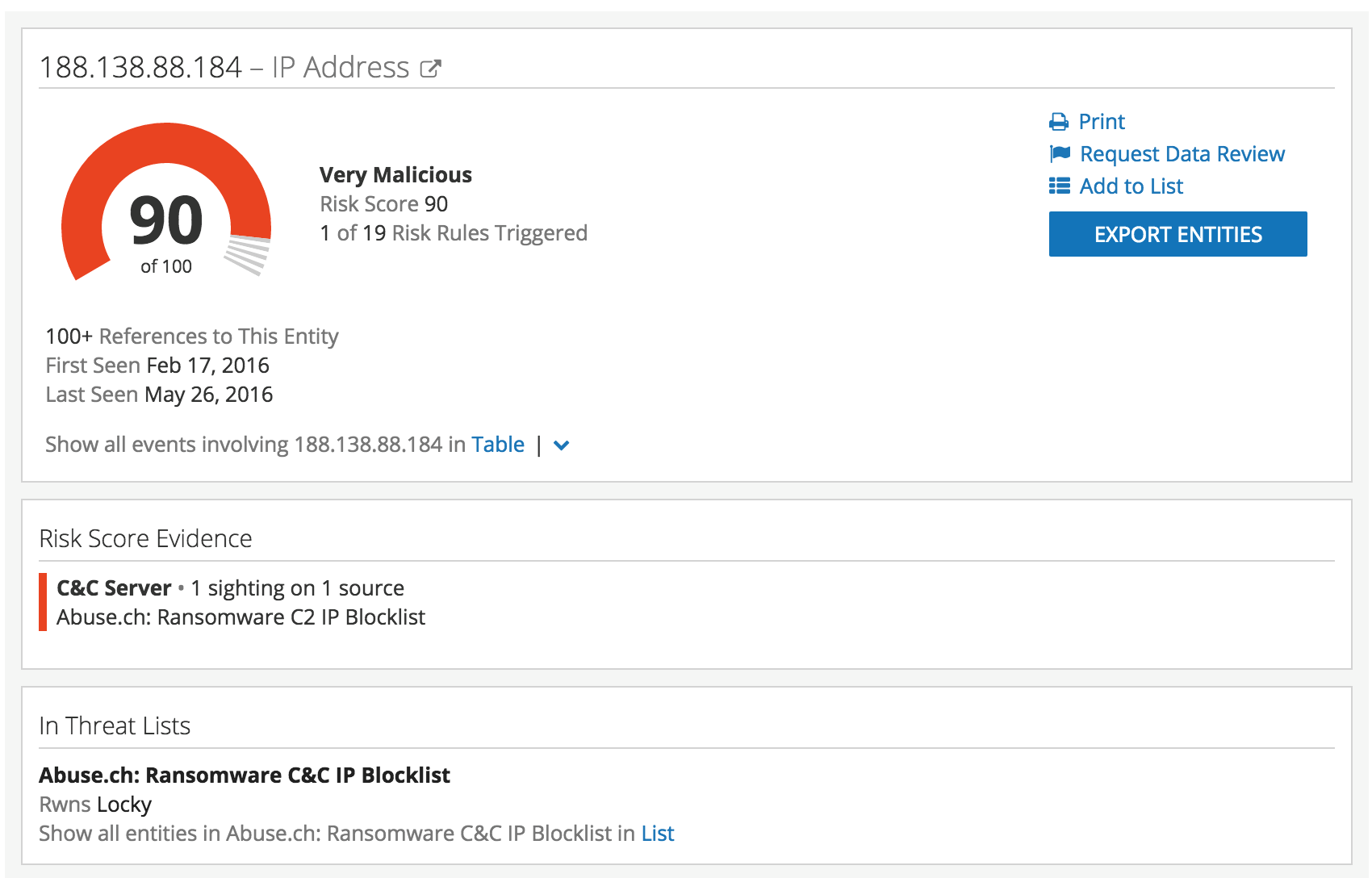
1.) A security analyst has an IP address indicator that is suspicious. The analyst enters the IP address into Recorded Future and pulls back information from their intel card. The example below shows some immediate insight that Recorded Future has harvested and presented for the analyst.
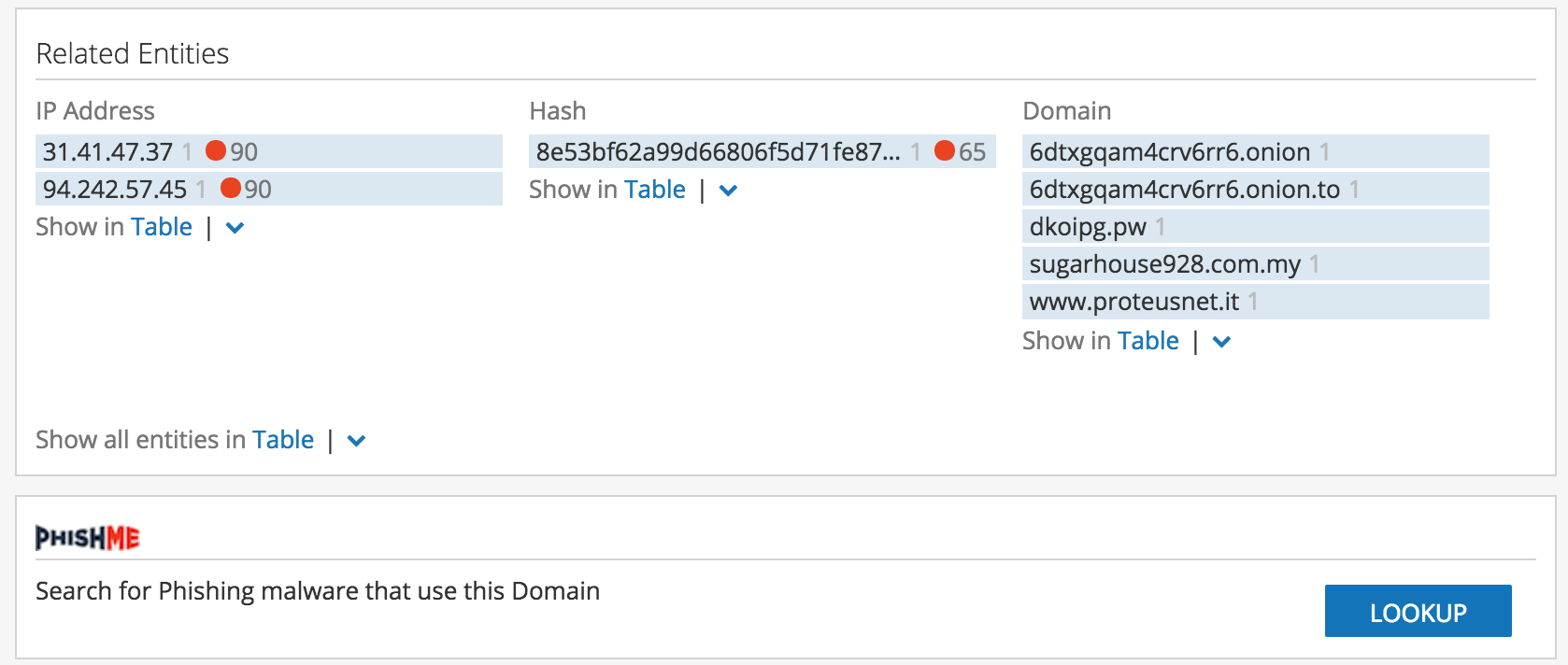
3.) The analyst can quickly determine from within Recorded Future this indicator has been involved with multiple phishing campaigns, and PhishMe provides insight into their infrastructure.
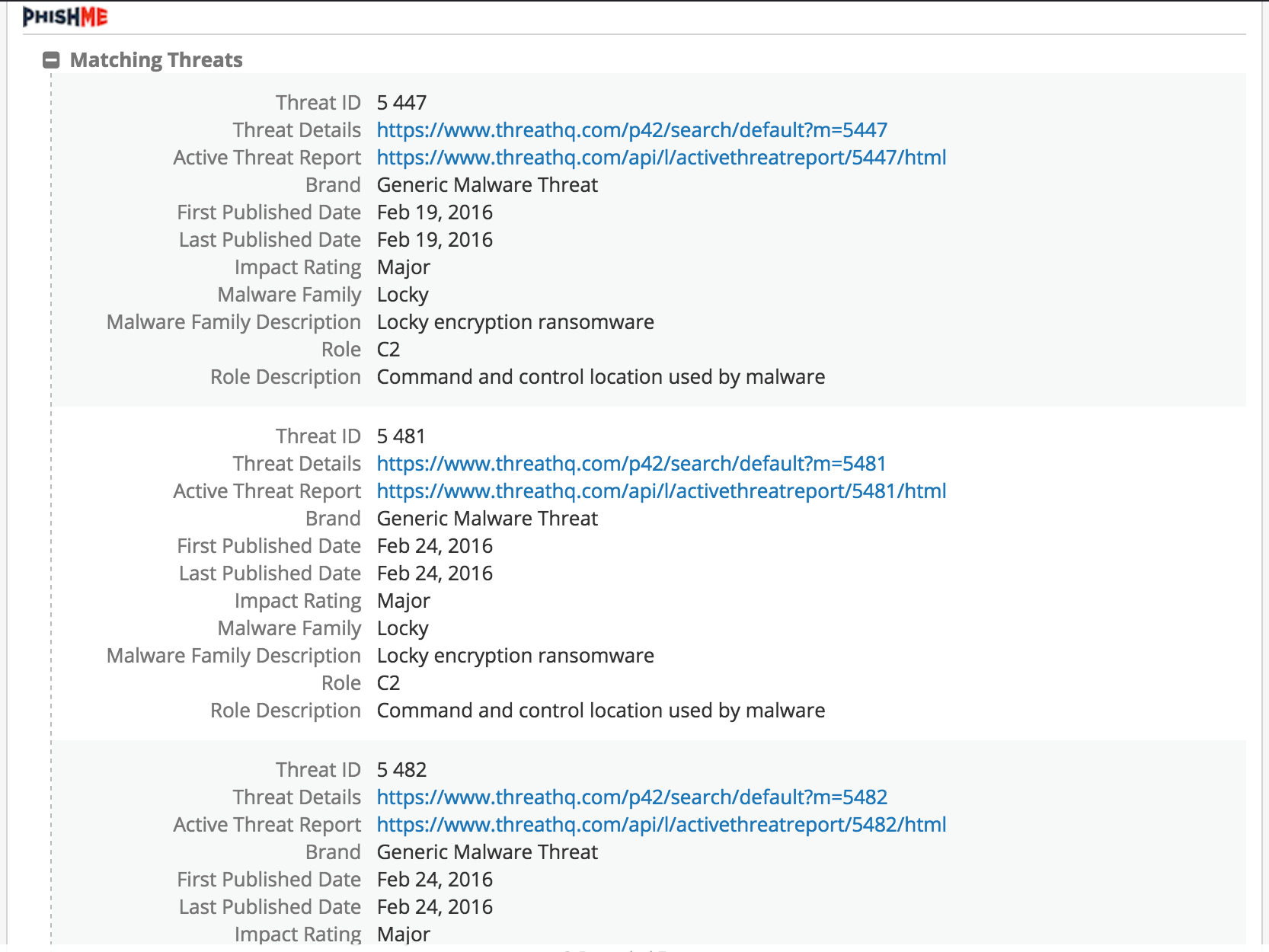
Full Context Report:
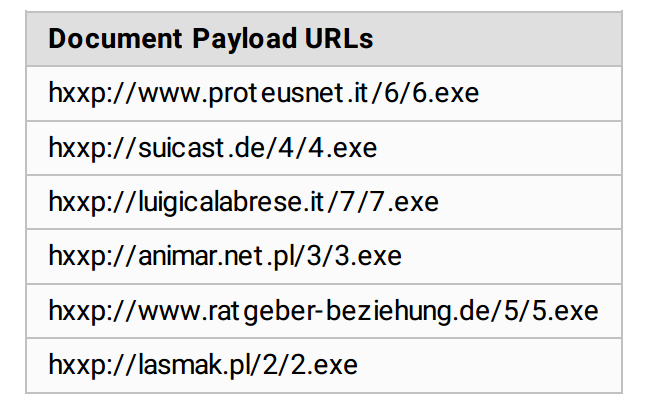
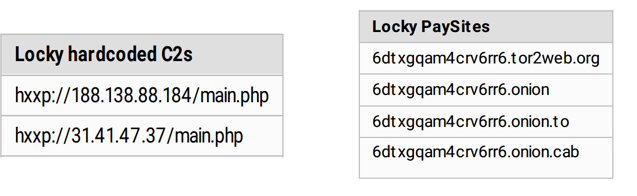
Command and Control and Locky PaySite:
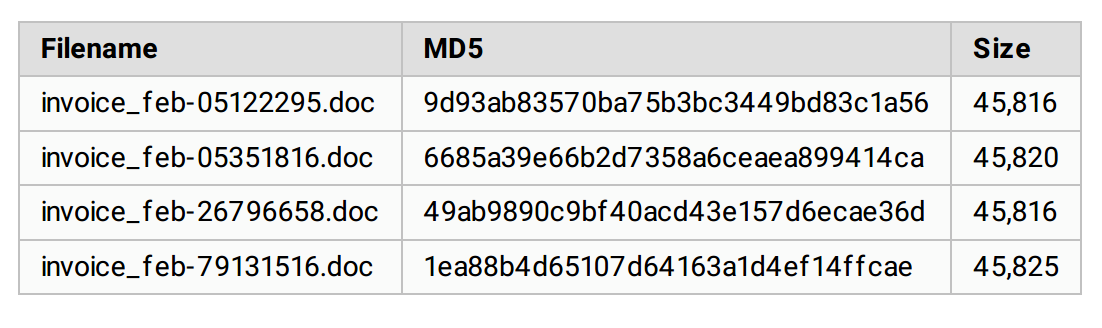
Hash and File Attributes:
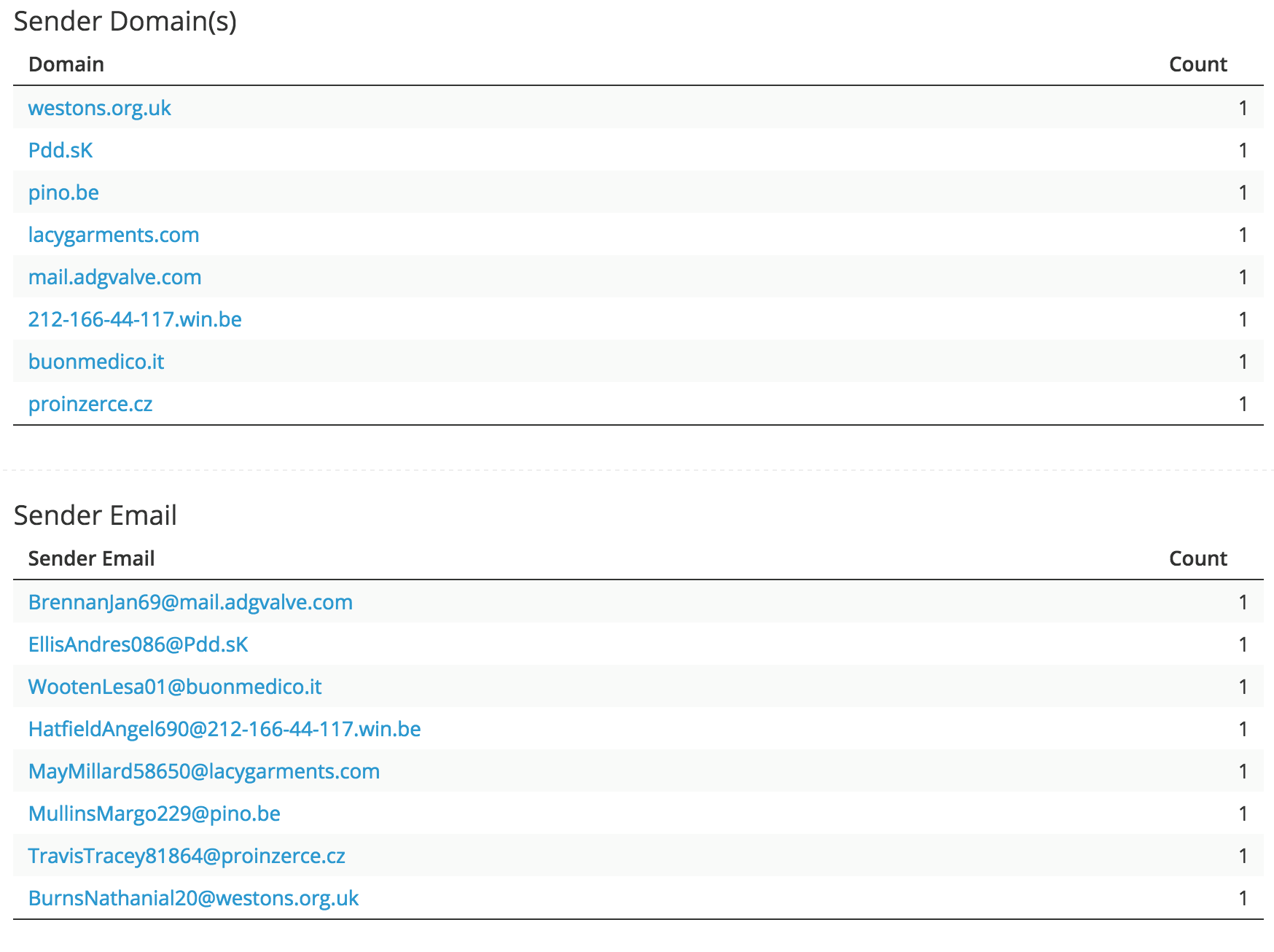
Sender Domains and Email:
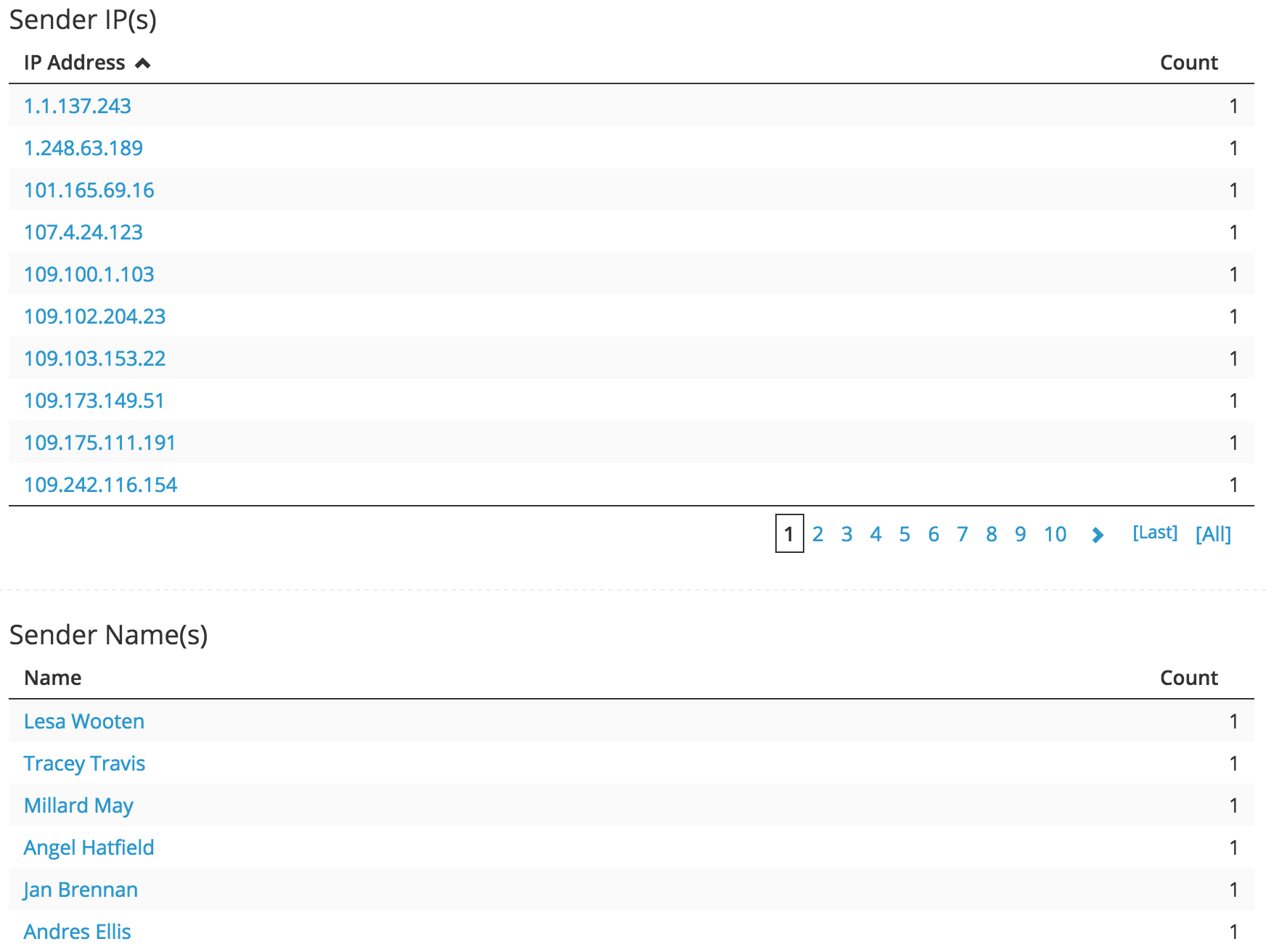
Sender IPs and Name(s):
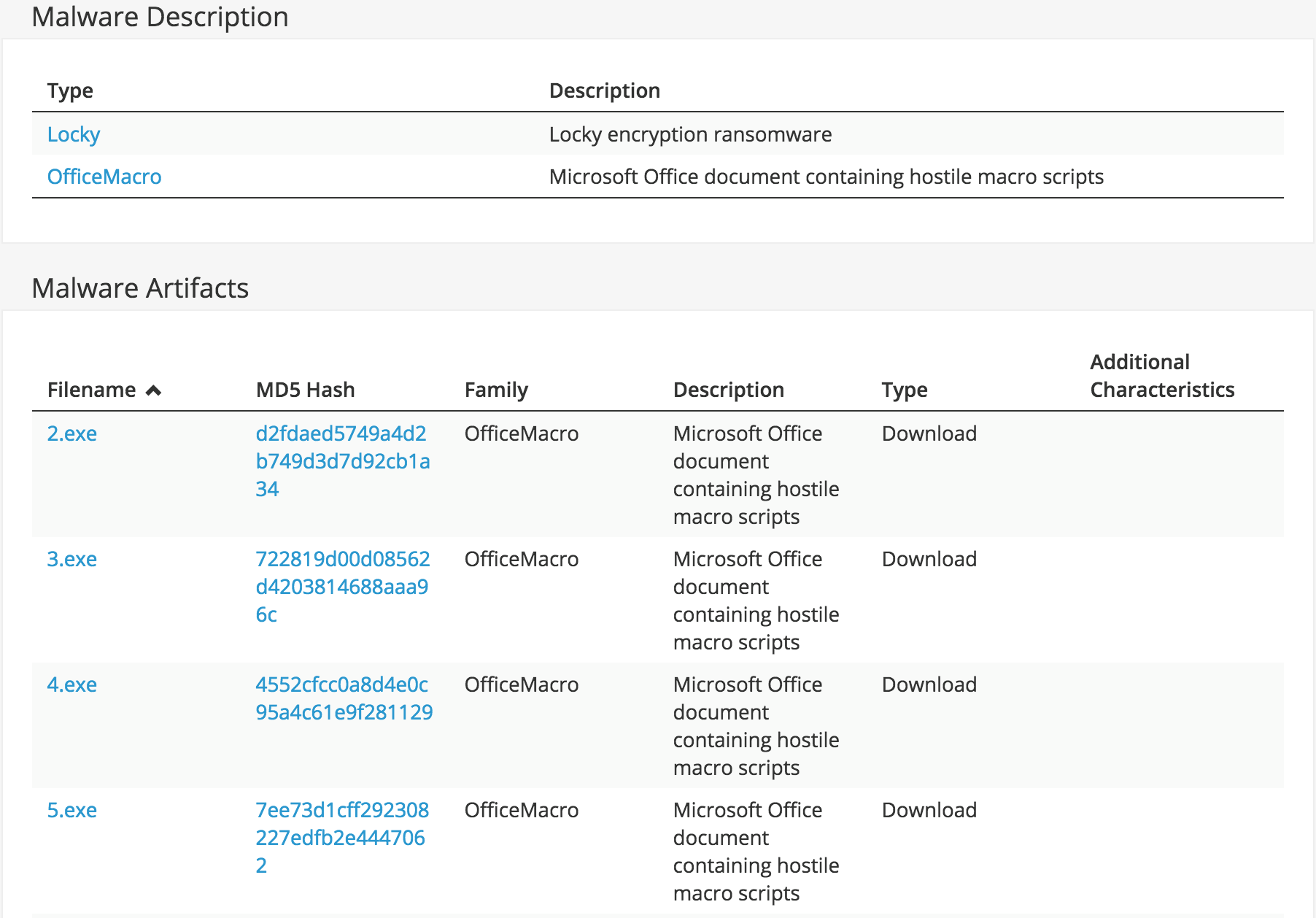
Malware Description and Artifacts:
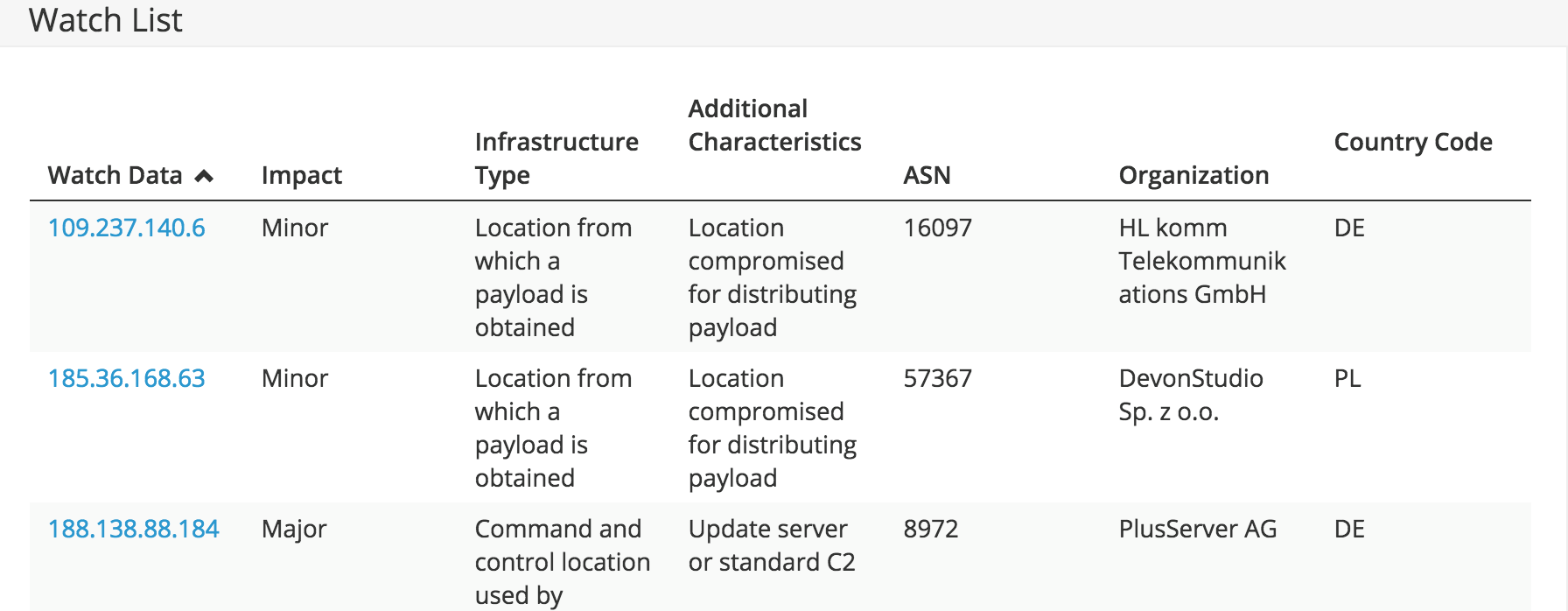
Watch List:
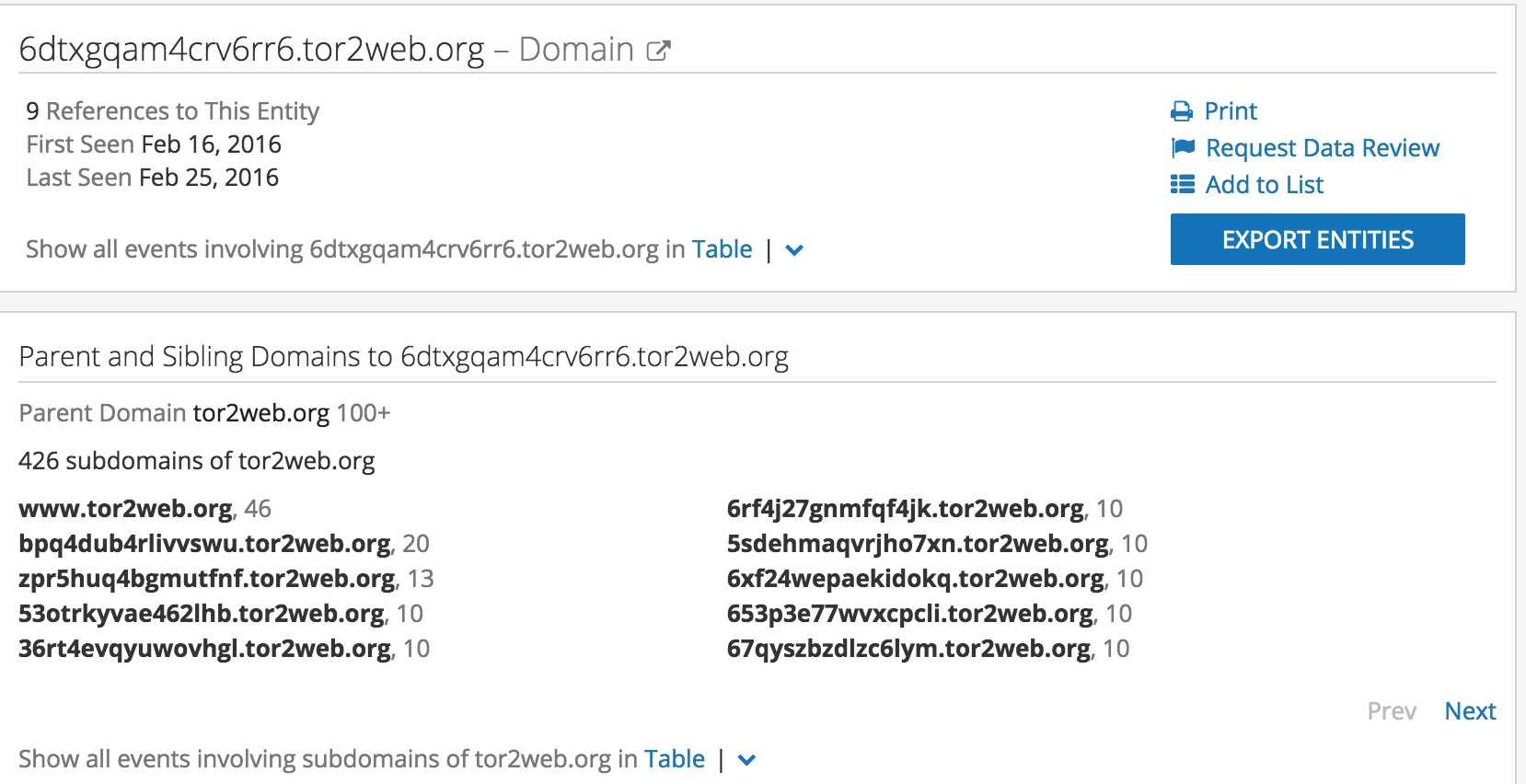
Pivot Back into Recorded Future (investigate 6dtxgqam4crv6rr6[.]tor2web[.]org) PaySite
The analyst can pivot back into Recorded Future from PhishMe to determine other OSINT events and then pivot back into PhishMe using the lookup capabilities with the API. What this does is provide the analyst with multiple trusted sources of intelligence where they can pivot and validate their research or uncover new activity which warrants additional investigation.
The above intelligence can be operationalized and prioritized and analysts can pivot between trusted sources. The analyst has a continuous opportunity to investigate as opposed to a simplistic one-off. It’s the combination of technology partnerships and APIs, machine-readable data, and rich contextual reports that provide organizations the intelligence needed to defend the business and understand their threats.
PhishMe Intelligence and Recorded Future is a great example where businesses can use their existing investments and pivot from one source of intelligence into another and back again. PhishMe and Recorded Future are very excited to provide our customers with valuable solutions that complement each other. This is not the first time, and at RSA 2016, we announced our integration from PhishMe Triage™ into Recorded Future, with additional insight available here.