Cofense Intelligence™ uncovered a resurgent Sigma ransomware campaign on March 13, 2018 following a noted three-month hiatus of the malware. Although many aspects of this campaign—including its anti-analysis techniques—are consistent with previously analyzed Sigma samples, its return is in and of itself atypical.
Since 2016, Cofense Intelligence has observed rapid turnover and evolution in ransomware varieties delivered by phishing campaigns. Only a handful of ransomware varieties found a stable and recurring share of the ransomware market. Exceptions include Locky, Cerber, and GlobeImposter. These exceptions suggest that operators of some ransomware varieties are better able to overcome infrastructure disruption and enhanced technical controls to warrant continuous investment in their malware. Sigma’s return may suggest that its operators have taken time to improve or adapt the ransomware and its delivery—a fact that puts it in a category with few peers.
Sigma Delivery
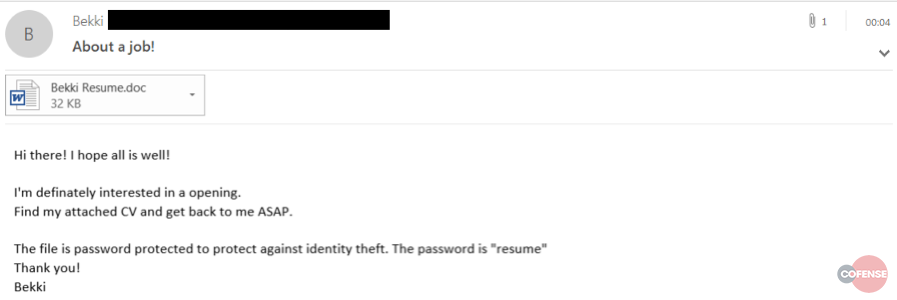
Sigma ransomware operators have leveraged various techniques to evade detection and mitigation by automated security controls and gateways, some of which we highlighted in a December assessment. In the most recent campaign, phishing emails were constructed to appear as applications or expressions of interest for professional opportunities with password-protected attachments that were purportedly resumes.
Figure 1: Example of Recent Sigma Phishing Narrative
By password-protecting the document, the Sigma operators increase the email’s legitimacy and make it more difficult for a complete automated analysis of the inbound document at the network perimeter. This increases the chance that the document evades detection and reaches the target user’s inbox. Sigma campaigns have included different variations of this tactic, and users should be aware of modifications of this technique. In December, what appeared as the email body text was in fact an image of text embedded within the email body.
Ransom “Options”
Following Sigma’s deployment and encryption of its victim’s files, a ransom message is displayed indicating two different ransom amounts that depend on how quickly the victim pays. A lower ransom is accepted by the attackers if the ransom is paid within a certain time frame, but the amount increases if the victim waits to pay. This adds to a growing trend of a diversified ransom payment process. Over the last year, ransomware operators have increasingly shed the one-ransom-fits-all instructional in order to increase their monetization of the malware.
In this case, victims are encouraged to pay quickly, almost certainly to make them feel that they are getting a “deal” of sorts. Also, ransomware operators hope to lower the chances that they will consider other options to mitigate the infection outside of payment. With other ransomware families, we have seen several examples where victims are instructed to enter negotiations with threat actors or where multiple tiers of decryption service are offered so that people can pay what they can afford over time.
Defense Against Ransomware Families Like Sigma
Threat actors are consistently innovating to find ways to increase the likelihood of their phish reaching targeted inboxes, requiring evasion of automated perimeter technologies. Sigma operators have done this by password-protecting the malicious attachment and thereby increasing the level of interaction required to open and fully inspect the attached document. As threat actors devise new delivery schemes, user identification and reporting of suspected phishing emails becomes increasingly important. It is vital that users are educated and empowered to report malicious emails to ensure a robust network defense strategy.
Sign up for free threat alerts. Get phishing and malware trends delivered to your inbox: https://cofense.com/threat-alerts/
*For details of the most recent Sigma Ransomware Campaign, see Threat ID 11070. For past campaigns, see Threat IDs 10416, 10406, 10402, and 10360.