Found in Environments Protected By: Microsoft By Noah Mizell, Cofense Phishing Defense Center (PDC) It's unsurprising to see threat actors attempting to use tax season to target recipients with a potential refund. One campaign observed by the Cofense Phishing Defense Center (PDC) uses the Adobe filesharing service to deliver the phish. 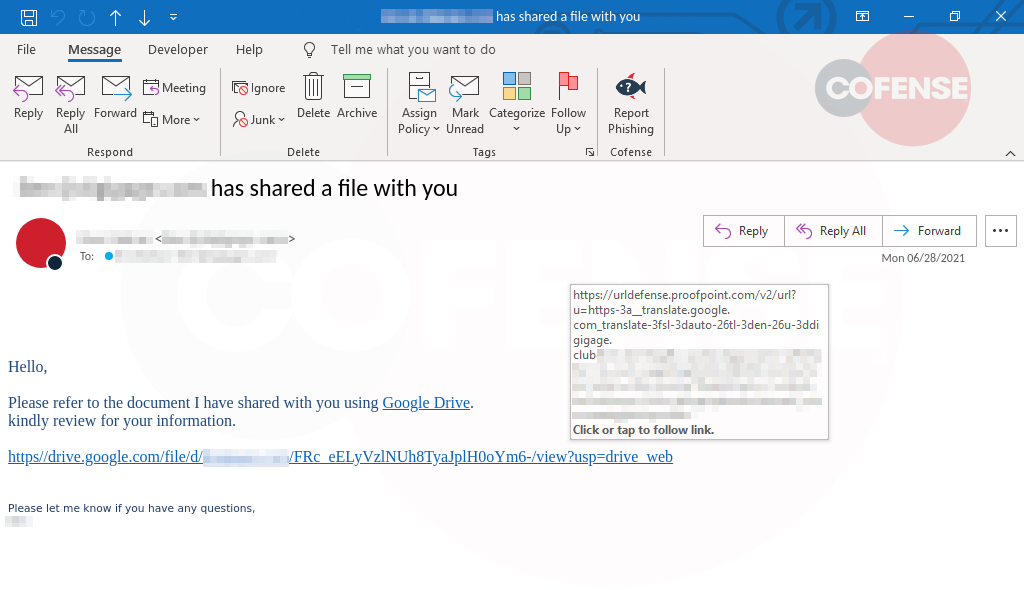
Figure 1: Email Body
Figure 1 is the email body generated by the Adobe file-sharing service use. Cofense has observed Adobe as a popular file-sharing service threat actors use to deliver their lure. The attack could be sent out using just about any similar service. By naming the file “TAX PAYMENT REFUND,” the recipient is more likely to interact with the link in hopes of getting money back instead of writing a check. Clicking the “Review and sign” button directs the recipient to an Adobe file-sharing page which in turn eventually leads to a Microsoft SharePoint site
. 
Figure 2: SharePoint Page
Figure 2 shows the SharePoint page the target is taken to from the shared file on Adobe. We see the shift in the subject went from being about taxes to simply “Payment Details,” it’s common for threat actors to reuse pieces of one campaign for another. Once the user clicks “View Payment Details” they are taken to the final landing page. At this point, the recipient may have realized this was a phish and hit the Reporter button.

Figure 3: Phishing Page
The landing page in Figure 3 is another standard style for a Microsoft-themed phish. There is one unique feature: the blurred-out W-9 form in the background. It’s a small detail, but it still holds the potential to convince a user into believing there is an actual form to view once logged in. Though this specific campaign is not the most detailed or unique, it is still important for the users to be wary of any tax-related emails. Within the coming months, there are bound to be more campaigns such as this one, and it is fair to assume that some will be more complex and trickier than the ones on display here. If your enterprise would like to benefit from the protection of the Cofense Phishing Defense Center (PDC), contact us to learn more.
| Indicators of Compromise | IP |
|---|---|
| hxxps://na4[.]documents[.]adobe[.]com/public/esign?tsid=CBFCIBAA3 AAABLblqZhCP48aUN7RoG-VJgs3s k2MItAA74xTWpSvSX-Fb-D9J0VXGy9NdV_0IHCY7YwUDvjH | 44.234.124.132 |
| hxxps://researchtriangle-my[.]sharepoint[.]com/personal/driver_rtp_org/_ layouts/15/Doc[.]aspx | 13.107.138.8 |
| hxxps://bafkreibjszhtiz6ochdcjf42t4x43fe4fxqau3m3rrgyzvq oyn6ncbrxyi[.]ipfs[.]dweb[.]link | 209.94.90.1 |
| hxxps://kalamfarik[.]com/wp-includes/onsupport/ui[.]php | 43.250.140.40 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results. The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.