Mimecast
By Fabio Rodrigues
Phishing threat actors are using Captcha methods to bypass automated URL analysis. By using Captcha techniques to prove human presence, the phish prevents the secure email gateway (SEG), in this case Mimecast’s gateway, from scanning the URL thereby enabling the threat to get through. Here’s how it works.
Email Body
The phishing email is sent from a compromised account at @avis.ne.jp as if it originated from a voip2mail service. The email alerts the recipient to a new voicemail message. The message is crafted in a simple format, with a preview of the voicemail to entice the recipient to click on the button to listen to the full message.
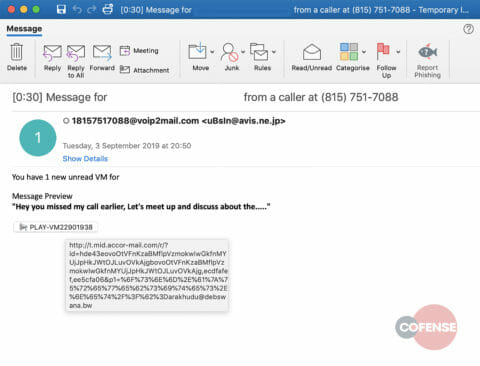
Figure 1: Email Body
This button is in fact an embedded hyperlink that will redirect the recipient to a page that contains a Captcha code to prove the victim is a human and not an automated analysis tool or, as Google puts it, “a robot.” It’s at this point that the SEG validation would fail. The SEG cannot proceed to and scan the malicious page, only the Captcha code site. This webpage doesn’t contain any malicious items, thus leading the SEG to mark it as safe and allow the user through.
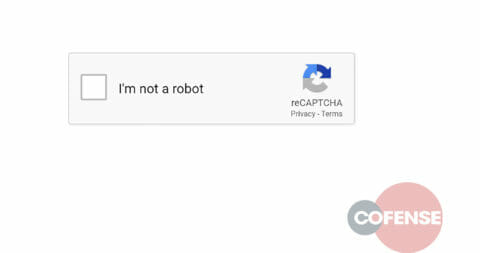
Figure 2: Captcha Page
Once the human verification process is complete, the recipient is redirected to the real phishing page. In this example, it imitates the Microsoft account selector and login page. When unwitting victims login, their credentials are captured.
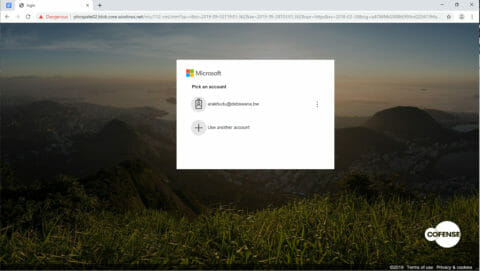
Figure 3: Phishing Page
As we can see, both the Captcha application page and the main phishing page are hosted on MSFT infrastructure. Both pages are legitimate Microsoft top level domains, so when checking these against domain reputation databases we receive a false negative and the pages come back as safe. SEGs frequently check URLS against reputation databases as part of a layered defense.
Table 1: Network IOCs
| hxxp://t[.]mid[.]accor-mail[.]com/r/?id= |
| hxxps://osnm[.]azurewebsites[.]net/?b= |
| hxxps://phospate02[.]blob[.]core[.]windows[.]net/vric/112-vml[.]html?sp=r&st=2019-09-03T19:01:36Z&se=2019-09-28T03:01:36Z&spr=hxxps&sv=2018-03-28&sig=q4OWNkGXIlBtE99JknDZ047J94uFFCc%2BoNaZmtHOt2k%3D&sr= |
| 52[.]239[.]224[.]36 |
| 66[.]117[.]16[.]17 |
| 52[.]173[.]84[.]157 |
HOW COFENSE CAN HELP
Thanks to our unique perspective, no one knows more about providing phishing awareness training than Cofense. Updated weekly, check out our Phishing Database for REAL phishing examples and threats. To learn about our comprehensive phishing detection and response solution, watch our video.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.


