Threat actors using the Dridex botnet malware received a great deal of attention recently for their purported utilization of content exploiting a previously un-patched vulnerability in Microsoft Word. This exploit, which took advantage of unexpected behavior in the handling of certain document types, was reportedly used to deliver the Dridex botnet malware via documents attached to phishing emails. However, the bulk of Dridex campaigns leverage far more common delivery techniques that abuse the functionality that already exists in Microsoft Office and Adobe Reader rather than deploying some complex exploit content. This serves as a reminder that threat actors don’t always rely on exploit content because exploits of un-patched vulnerabilities are no longer required to break into an enterprise; simple phishing messages can accomplish this same goal.
While the merits of consistent, regular, and diligent software update protocols cannot be refuted, many of the vulnerabilities threat actors seek to exploit cannot be fixed by a software update. For the past three years, one of the most commonly-used means for delivering malware by phishing email has been through macro-enabled Microsoft Office documents. These files, now familiar to most all information security professionals, are designed to encourage the victim to enable the macro scripting contained within the Office document to facilitate the download of a malware payload. This is done entirely within the set of capabilities provided by the Office suite and Windows environment. Moreover, if this technique were not successful, it would not have been featured in 129 distinct phishing campaigns analyzed by PhishMe Intelligence during the first quarter of 2017 and almost four times that number throughout 2016. Threat actors understand that there’s no need for expensive, complex, and potentially-unreliable exploit content if the victim can be tricked into being a willing, if unwitting, participant in the infection process. This is the goal of content like that featured in Figures 1 and 2 where various threat actors attempt to convince victims that they must enable the macro content in each document.
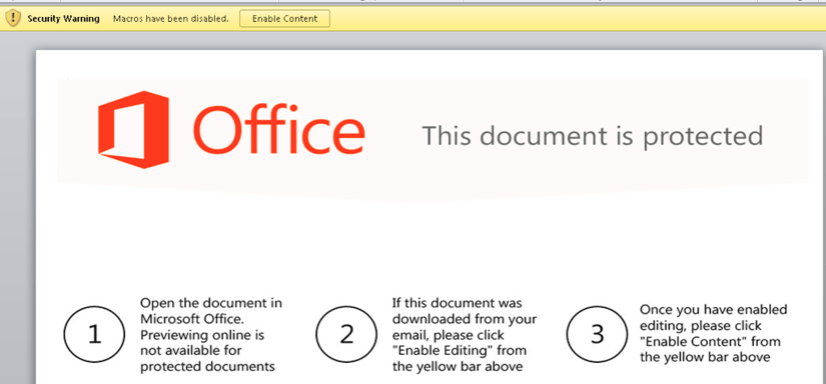
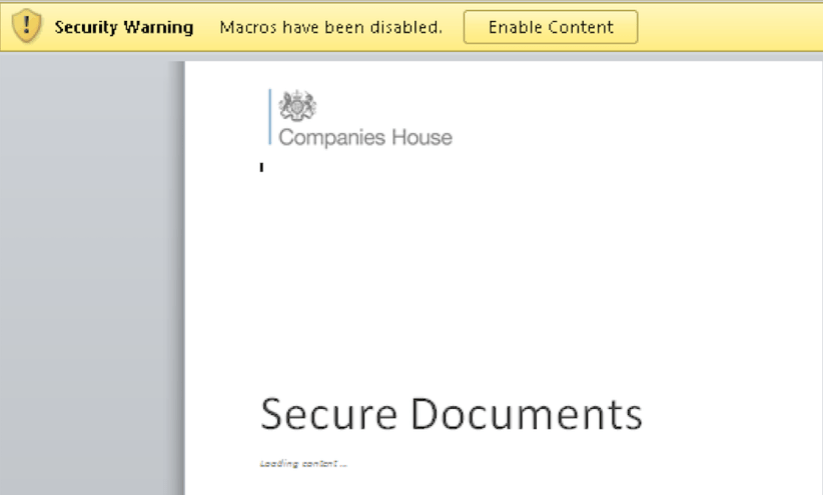
Techniques like these are designed by the threat actor to put enterprises at a disadvantage. Microsoft Office is, for most organizations, the standard suite for creating and transporting documents containing business-critical information. Therefore, heavy-handed solutions like blocking or restricting the transport of these documents inhibits enterprises’ ability to conduct normal business. Threat actors therefore hope to secure the delivery of Office documents so they can leverage their social engineering content to convince potential victims to open the door to the attacker’s tools.
As these macro-based attacks have proliferated, awareness and education for both defenders and users has as well. This has created an increasingly less advantageous environment for threat actors using Office macro documents. This has prompted threat actors to innovate and iterate. Many of these innovations and iterations have focused on defying the expectations created by the increased awareness about Office macro attacks. By changing how these documents are delivered and by altering how they are presented to victims, threat actors hope to defy the expectations for what these attacks look like to improve the probability of success. One example is the flourishing of OLE object abuse like that used to deliver the Ursnif botnet malware. Another is a technique also leveraged by the Dridex threat actors over the past week.
PDF documents attached to various “scan data” templates have been used to distribute the Dridex malware using a relatively simple and straightforward infection process. Upon opening these PDF documents, the recipient is prompted to give permission for the PDF reader application to open a second file. This second file, extracted from within the PDF document, is a Word document with a macro script application used to download a Dridex payload. This adds one more, unexpected step to the infection process and thereby breaks from the common technique used to deliver macro documents. Figures 3 and 4 show the two-steps used by the threat actor to convince victims to engage with the macro document.
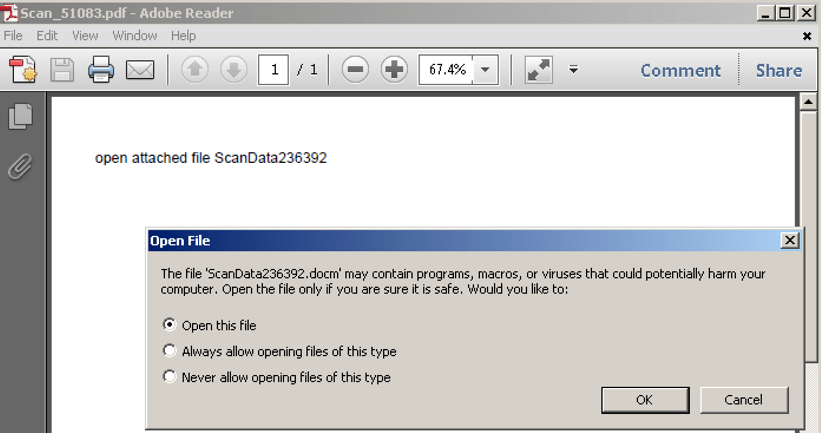
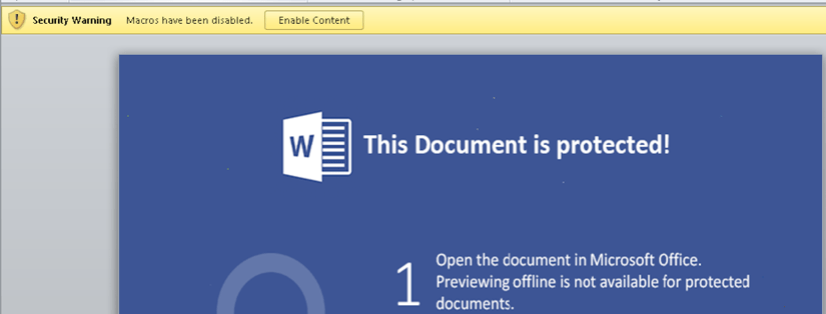
While the allure and drama surrounding un-patched vulnerabilities may make for riveting headlines, threat actors do not need to leverage “zero-day” exploitation to successfully attack enterprises and individuals. That goal can be achieved using much more commonplace and mundane tools that abuse, rather than exploit, the software applications required by computer users to do their jobs. More importantly, however, threat actors seek to abuse the users themselves–the people they hope are vulnerable to their narratives. The Dridex threat actors have not been successful because of their purported exploitation of a previously-unfixed vulnerability. They are successful because of their ability to craft convincing phishing narratives and their agility in reallocating new distribution infrastructure.
Security updates for essential software applications are an important part of a holistic defense posture, but they are by no means a complete defense against phishing threat actors like users of the Dridex malware. Instead, basic best practices must be juxtaposed with the application of actionable and up-to-date threat intelligence that gives an organization’s defenders the edge on how and where phishing attacks are being carried out and the resources used to support them. When combined with robust user education and empowerment, information security professionals can rely on their users to not only avoid falling victim to phishing narratives but also to report them to those tasked with defending an organization. This turns the email users that threat actors hope will be vulnerabilities into intelligence assets. Every user who refuses to be complicit in the threat actor’s plan then becomes a success and victory for the defenders.
Don’t forget to sign up for our FREE PhishMe Threat Alerts service to receive updated information on the latest malware, ransomware and phishing threats, delivered straight to your inbox.


